A Linux administrator copied a Git repository locally, created a feature branch, and committed some changes to the feature branch. Which of the following Git actions should the Linux administrator use to publish the changes to the main branch of the remote repository?
NO: 11:
Users report that they cannot access some files located in the /opt/finapp directory after a power outage caused an unexpected server restart. A Linux administrator examines the following filesystem details and system logs:
# mount | grep finapp
/dev/mapper/rhel-opt_finapp on /opt/finapp type xfs (rw,relatime,seclabel,attr2,inode64,logbufs=8,logbsize=32k,noquota)
# lsblk
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT
sda 8:0 0 931.5G 0 disk
|-sda1 8:1 0 1G 0 part /boot
|-sda2 8:2 0 930.5G 0 part
|-rhel-root 253:0 0 30.5G 0 lvm /
|-rhel-opt_finapp 253:1 0 900G 0 lvm /opt/finapp
# grep opt_finapp /var/log/messages
XFS (opt_finapp): Corruption detected in inode 3645, extent tree
Which of the following commands should the administrator run in an attempt to fix the filesystem?
A systems administrator is tasked with setting up key-based SSH authentication. In which of the following locations should the administrator place the public keys for the server?
A systems administrator created a web server for the company and is required to add a tag for the API so end users can connect. Which of the following would the administrator do to complete this requirement?
A Linux systems administrator is configuring a new filesystem that needs the capability to be mounted persistently across reboots. Which of the following commands will accomplish this task? (Choose two.)
A junior administrator updated the PostgreSQL service unit file per the data-base administrator's recommendation. The service has been restarted, but changes have not been applied. Which of the following should the administrator run for the changes to take effect?
After installing a new version of a package, a systems administrator notices a new version of the corresponding, service file was Installed In order to use the new version of the, service file, which of the following commands must be Issued FIRST?
A Linux administrator was notified that a virtual server has an I/O bottleneck. The Linux administrator analyzes the following output:
Given there is a single CPU in the sever, which of the following is causing the slowness?
During a security scan, the password of an SSH key file appeared to be too weak and was cracked. Which of the following commands would allow a user to choose a stronger password and set it on the existing SSH key file?
A Linux administrator reviews a set of log output files and needs to identify files that contain any occurrence of the word denied. All log files containing entries in uppercase or lowercase letters should be included in the list. Which of the following commands should the administrator use to accomplish this task?
A systems administrator configured firewall rules using firewalld. However, after the system is rebooted, the firewall rules are not present:
The systems administrator makes additional checks:
Which of the following is the reason the firewall rules are not active?
A systems administrator is troubleshooting a connectivity issue pertaining to access to a system named db.example.com. The system IP address should be 192.168.20.88. The administrator issues the dig command and receives the following output:
The administrator runs grep db.example.com /etc/hosts and receives the following output:
Given this scenario, which of the following should the administrator do to address this issue?
A systems administrator is receiving tickets from users who cannot reach the application app that should be listening on port 9443/tcp on a Linux server.
To troubleshoot the issue, the systems administrator runs netstat and receives the following output:
Based on the information above, which of the following is causing the issue?
A systems administrator is notified that the mysqld process stopped unexpectedly. The systems administrator issues the following command:
sudo grep –i -r ‘out of memory’ /var/log
The output of the command shows the following:
kernel: Out of memory: Kill process 9112 (mysqld) score 511 or sacrifice child.
Which of the following commands should the systems administrator execute NEXT to troubleshoot this issue? (Select two).
A Linux administrator is scheduling a system job that runs a script to check available disk space every hour. The Linux administrator does not want users to be able to start the job. Given the following:
The Linux administrator attempts to start the timer service but receives the following error message:

Which of the following is MOST likely the reason the timer will not start?
A senior Linux administrator has created several scripts that will be used to install common system applications. These scripts are published to a reposito-ry to share with the systems team. A junior Linux administrator needs to re-trieve the scripts and make them available on a local workstation. Which of the following Git commands should the junior Linux administrator use to accom-plish this task?
A systems administrator is investigating a service that is not starting up. Given the following information:
Which of the following systemd commands should the administrator use in order to obtain more details about the failing service?
A Linux administrator is alerted to a storage capacity issue on a server without a specific mount point or directory. Which of the following commands would be MOST helpful for troubleshooting? (Choose two.)
A cloud engineer is asked to copy the file deployment.yaml from a container to the host where the container is running. Which of the following commands can accomplish this task?
A systems administrator wants to delete app . conf from a Git repository. Which of the following commands will delete the file?
A systems administrator has been unable to terminate a process. Which of the following should the administrator use to forcibly stop the process?
An administrator added the port 2222 for the SSH server on myhost and restarted the SSH server. The administrator noticed issues during the startup of the service. Given the following outputs:
Which of the following commands will fix the issue?
A Linux administrator has set up a new DNS forwarder and is configuring all internal servers to use the new forwarder to look up external DNS requests. The administrator needs to modify the firewall on the server for the DNS forwarder to allow the internal servers to communicate to it and make the changes persistent between server reboots. Which of the following commands should be run on the DNS forwarder server to accomplish this task?
A Linux administrator is troubleshooting a memory-related issue. Based on the output of the commands:
Which of the following commands would address the issue?
A Linux system is failing to boot with the following error:
Which of the following actions will resolve this issue? (Choose two.)
After installing some RPM packages, a systems administrator discovers the last package that was installed was not needed. Which of the following commands can be used to remove the package?
A new file was added to a main Git repository. An administrator wants to synchronize a local copy with the contents of the main repository. Which of the following commands should the administrator use for this task?
A systems administrator pressed Ctrl+Z after starting a program using the command line, and the shell prompt was presented. In order to go back to the program, which of the following commands can the administrator use?
A systems administrator is configuring a Linux system so that network traffic from the internal network 172.17.0.0/16 going out through the eth0 interface would appear as if it was sent directly from this interface. Which of the following commands will accomplish this task?
A Linux administrator needs to rebuild a container with the httpd service in order to change some default parameters. Which of the following should be the first command line in the Dockerfile?
A systems administrator is gathering information about a file type and the contents of a file. Which of the following commands should the administrator use to accomplish this task?
A systems administrator made some unapproved changes prior to leaving the company. The newly hired administrator has been tasked with revealing the system to a compliant state. Which of the following commands will list and remove the correspondent packages?
Junior system administrator had trouble installing and running an Apache web server on a Linux server. You have been tasked with installing the Apache web server on the Linux server and resolving the issue that prevented the junior administrator from running Apache.
INSTRUCTIONS
Install Apache and start the service. Verify that the Apache service is running with the defaults.
Typing “help†in the terminal will show a list of relevant event commands.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A systems administrator wants to be sure the sudo rules just added to /etc/sudoers are valid. Which of the following commands can be used for this task?
Users report that connections to a MariaDB service are being closed unexpectedly. A systems administrator troubleshoots the issue and finds the following message in /var/log/messages:
Which of the following is causing the connection issue?
A Linux administrator wants to find out whether files from the wget package have been altered since they were installed. Which of the following commands will provide the correct information?
A database administrator requested the installation of a custom database on one of the servers. Which of the following should the Linux administrator configure so the requested packages can be installed?
Developers have requested implementation of a persistent, static route on the application server. Packets sent over the interface eth0 to 10.0.213.5/32 should be routed via 10.0.5.1. Which of the following commands should the administrator run to achieve this goal?
A systems administrator wants to leverage their password-protected SSH key to connect to multiple servers without entering their password every time. Which of the following commands should the administrator use?
After starting an Apache web server, the administrator receives the following error:
Apr 23 localhost.localdomain httpd 4618] : (98) Address already in use: AH00072: make_sock: could not bind to address [: :]80
Which of the following commands should the administrator use to further trou-bleshoot this issue?
A Linux administrator needs to correct the permissions of a log file on the server. Which of the following commands should be used to set filename.log permissions to -rwxr—r--. ?
A systems administrator wants to list all local account names and their respective UIDs. Which of the following commands will provide output containing this information?
A systems administrator frequently connects to a remote host via SSH and a non-standard port. The systems administrator would like to avoid passing the port parameter on the command line every time. Which of the following files can be used to set a different port value for that host?
A new application container was built with an incorrect version number. Which of the following commands should be used to rename the image to match the correct version 2.1.2?
A Linux administrator changed a systemd configuration. However, the change was not applied after the system was restarted. Which of the following commands is required to apply the change?
An administrator needs to get network information from a group of statically assigned workstations before they are reconnected to the network. Which of the following should the administrator use to obtain this information?
A systems administrator is tasked with mounting a USB drive on a system. The USB drive has a single partition, and it has been mapped by the system to the device /dev/sdb. Which of the following commands will mount the USB to /media/usb?
A Linux administrator is configuring a log collector agent to monitor logs in /var/log/collector. The agent is reporting that it cannot write to the directory. The agent runs as the logger user account. The administrator runs a few commands and reviews the following output:
Output 1:
drwxr-xr-x. 1 root root 0 Oct 20:13 collector
Output 2:
file: /var/log/collector
owner: root
group: root
user::rwx
group::r-x
mask::rwx
other::r-x
Output 3:
uid=1010(logger) gid=1010(monitor) groups=1010(monitor)
Which of the following is the best way to resolve the issue?
Due to performance issues on a server, a Linux administrator needs to termi-nate an unresponsive process. Which of the following commands should the
administrator use to terminate the process immediately without waiting for a graceful shutdown?
Users are reporting that a Linux server is responding slowly. A systems administrator troubleshooting the server issue sees the following iostat output, with %iowait at 50.38. Which of the following is most likely the issue?
Users report that they are unable to reach the company website https://www.comptia.org. A systems administrator confirms the issue with the following command:
# curl https://www.comptia.org
curl: (7) Failed to connect to www.comptia.org port 443: No route to host
The administrator logs in to the company’s web server to check its configuration and sees the following output:
root@comptia.org:-># firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: dummy0 eth0
sources:
services: cockpit dhcpv6-client http ssh
ports: 3001/tcp
protocols:
forward: no
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
rule family="ipv4" source address="61.177.173.6" port port="ssh" protocol="tcp" reject type="icmp-port-unreachable"
rule family="ipv4" source address="185.143.45.164" port port="ssh" protocol="tcp" reject type="icmp-port-unreachable"
rule family="ipv4" source address="143.198.60.41" port port="ssh" protocol="tcp" reject type="icmp-port-unreachable"
root@comptia.org:-># ip route
default via 172.31.1.1 dev eth0 proto dhcp src 65.21.187.65 metric 100
10.0.6.0/24 dev dummy0 proto kernel scope link src 10.0.6.65 metric 550
172.17.0.0/16 dev docker0 proto kernel scope link src 172.17.0.1
172.18.0.0/16 dev br-28ac2eaeeca1 proto kernel scope link src 172.18.0.1
172.19.0.0/16 dev br-fb3897555ca3 proto kernel scope link src 172.19.0.1 linkdown
172.31.1.1 dev eth0 proto dhcp scope link src 65.21.187.65 metric 100
192.168.224.0/20 dev br-e949ab177d79 proto kernel scope link src 192.168.224.1 linkdown
192.168.240.0/20 dev br-6adf72ac0ae3 proto kernel scope link src 192.168.240.1 linkdown
Which of the following is causing the issue?
An application developer received a file with the following content:
##This is a sample Image ##
FROM ubuntu:18.04
MAINTAINER demohut@gtmail.com.hac
COPY . /app
RUN make /app
CMD python /app/app.py
RUN apt-get update
RUN apt-get install -y nginx
CMD ["echo","Image created"]
The developer must use this information to create a test bed environment and identify the image (myimage) as the first version for testing a new
application before moving it to production. Which of the following commands will accomplish this task?
An administrator added a new disk to expand the current storage. Which of the following commands should the administrator run first to add the new disk to the LVM?
A cloud engineer wants to delete all unused networks that are not referenced by any container. Which of the following commands will achieve this goal?
A Linux systems administrator is resolving a privileged access issue for users who are members of an admin group. Which of the following configuration files should the administrator update so the users in the admin group will have root privileged access to the Linux system?
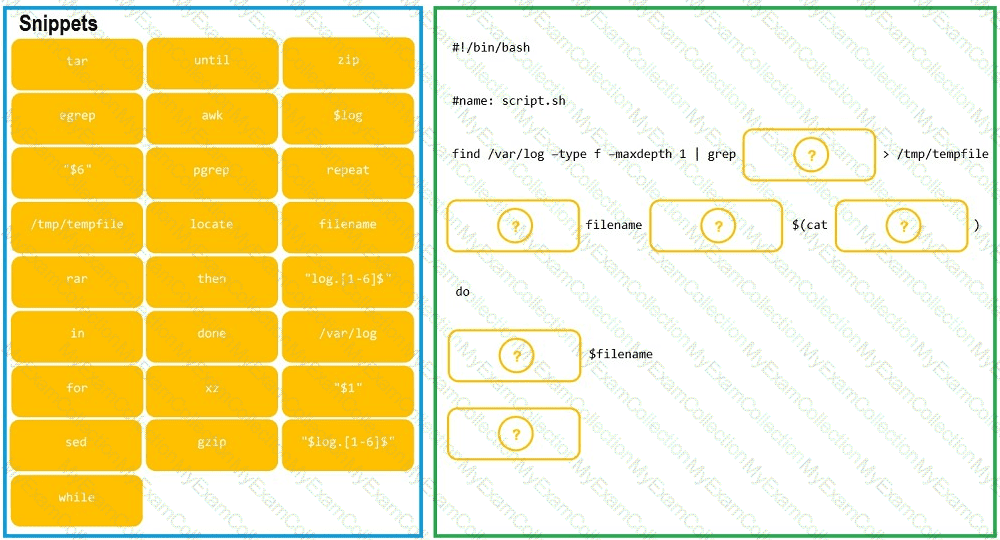
As a Systems Administrator, to reduce disk space, you were tasked to create a shell script that does the following:
Add relevant content to /tmp/script.sh, so that it finds and compresses rotated files in /var/log without recursion.
INSTRUCTIONS
Fill the blanks to build a script that performs the actual compression of rotated log files.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A Linux administrator was asked to run a container with the httpd server inside. This container should be exposed at port 443 of a Linux host machine while it internally listens on port 8443. Which of the following commands will accomplish this task?
Which of the following enables administrators to configure and enforce MFA on a Linux system?
An administrator would like to list all current containers, regardless of their running state. Which of the following commands would allow the administrator to accomplish this task?
Which of the following can be used as a secure way to access a remote termi-nal?
A Linux user would like the shell changed to /bin/bash. Which of the following commands will accomplish this task?
A developer needs to launch an Nginx image container, name it Web001, and ex-pose port 8080 externally while mapping to port 80 inside the container. Which of the following commands will accomplish this task?
A Linux administrator has been tasked with installing the most recent versions of packages on a RPM-based OS. Which of the following commands will accomplish this task?
A cloud engineer needs to check the link status of a network interface named eth1 in a Linux server. Which of the following commands can help to achieve the goal?
A junior systems administrator has just generated public and private authentication keys for passwordless login. Which of the following files will be moved to the remote servers?
A Linux administrator created a new file system. Which of the following files must be updated to ensure the filesystem mounts at boot time?
Several users reported that they were unable to write data to the /oracle1 directory. The following output has been provided:
Which of the following commands should the administrator use to diagnose the issue?
A Linux administrator is trying to remove the ACL from the file /home/user/data. txt but receives the following error message:
Given the following analysis:
Which of the following is causing the error message?
A Linux administrator booted up the server and was presented with a non-GUI terminal. The administrator ran the command systemct1 isolate graphical.target and rebooted the system by running systemct1 reboot, which fixed the issue. However, the next day the administrator was presented again with a non-GUI terminal. Which of the following is the issue?
A systems administrator is installing various software packages using a pack-age manager. Which of the following commands would the administrator use on the Linux server to install the package?
Which of the following is a way to enable a production web server's communications with strong encryption and identity verification?
A systems administrator is compiling a report containing information about processes that are listening on the network ports of a Linux server. Which of the following commands will allow the administrator to obtain the needed information?
A Linux administrator is providing a new Nginx image from the registry to local cache. Which of the following commands would allow this to happen?
A cloud engineer needs to change the secure remote login port from 22 to 49000. Which of the following files should the engineer modify to change the port number to the desired value?
A junior administrator is setting up a new Linux server that is intended to be used as a router at a remote site. Which of the following parameters will accomplish this goal?
A Linux administrator recently downloaded a software package that is currently in a compressed file. Which of the following commands will extract the files?
After connecting to a remote host via SSH, an administrator attempts to run an application but receives the following error:
arduino
Error: cannot open display:
Which of the following should the administrator do to resolve this error?
Which of the following command sequences is used to install Linux software directly from source code?
A Linux administrator is creating a user that can run the FTP service but cannot log in to the system. The administrator sets /bin/false as a login shell for the user. When the user tries to run the FTP service, it is rejected with an "invalid shell: /bin/false" message. Which of the following is the best way to resolve the issue?
Joe, a user, is unable to log in to the Linux system. Given the following output:
Which of the following commands would resolve the issue?
A Linux system is getting an error indicating the root filesystem is full. Which of the following commands should be used by the systems administrator to resolve this issue? (Choose three.)
A systems administrator is investigating why one of the servers has stopped connecting to the internet.
Which of the following is causing the issue?
A Linux systems administrator needs to persistently enable IPv4 forwarding in one of the Linux systems. Which of the following commands can be used together to accomplish this task? (Choose two.)
A junior Linux administrator is tasked with installing an application. The installation guide states the application should only be installed in a run level 5 environment.
Which of the following commands would ensure the server is set to runlevel 5?
Based on an organization’s new cybersecurity policies, an administrator has been instructed to ensure that, by default, all new users and groups that are created fall within the specified values below.
To which of the following configuration files will the required changes need to be made?
Which of the following technologies can be used as a central repository of Linux users and groups?
Some servers in an organization have been compromised. Users are unable to access to the organization’s web page and other services. While reviewing the system log, a systems administrator notices messages from the kernel regarding firewall rules:
Which of the following commands will remediate and help resolve the issue?
A DevOps engineer wants to allow the same Kubernetes container configurations to be deployed in development, testing, and production environments. A key requirement is that the containers should be configured so that developers do not have to statically configure custom, environment-specific locations. Which of the following should the engineer use to meet this requirement?
A cloud engineer needs to launch a container named web-01 in background mode. Which of the following commands will accomplish this task''
Which of the following actions are considered good security practices when hardening a Linux server? (Select two).
Users have been unable to save documents to /home/tmp/temp and have been receiving the following error:
Path not found
A junior technician checks the locations and sees that /home/tmp/tempa was accidentally created instead of /home/tmp/temp. Which of the following commands should the technician use to fix this issue?
A Linux engineer needs to create a custom script, cleanup.sh, to run at boot as part of the system services. Which of the following processes would accomplish this task?
A Linux administrator needs to obtain a list of all volumes that are part of a volume group. Which of the following commands should the administrator use to accomplish this task?
An administrator recently updated the BIND software package and would like to review the default configuration that shipped with this version. Which of the following files should the administrator review?
Which of the following commands is used to configure the default permissions for new files?
A Linux administrator needs to expand a volume group using a new disk. Which of the following options presents the correct sequence of commands to accomplish the task?
A systems administrator wants to list all local accounts in which the UID is greater than 500. Which of the following commands will give the correct
output?
A Linux administrator rebooted a server. Users then reported some of their files were missing. After doing some troubleshooting, the administrator found one of the filesystems was missing. The filesystem was not listed in /etc/f stab and might have been mounted manually by someone prior to reboot. Which of the following would prevent this issue from reoccurring in the future?
A Linux administrator has logged in to a server for the first time and needs to know which services are allowed through the firewall. Which of the following options will return the results for which the administrator is looking?
User1 is a member of the accounting group. Members of this group need to be able to execute but not make changes to a script maintained by User2. The script should not be accessible to other users or groups. Which of the following will give proper access to the script?
A systems administrator is reconfiguring existing user accounts in a Linux system. Which of the following commands should the administrator use to include "myuser" in the finance group?
A systems administrator received a request to change a user's credentials. Which of the following commands will grant the request?
A systems administrator needs to install the file installer_0.17-41.2_amd64.deb. Which of the following commands should the administrator use?
A Linux administrator is troubleshooting an SSHD issue on a server. Users are receiving error messages stating the connection is refused. Which of the following commands should be used to verify whether the service is listening?
A systems administrator is reviewing the following output on the text editor that is being used to update the company's internal database records:
Which of the following extensions should the systems administrator use when saving the file?
A User on a Linux workstation needs to remotely start an application on a Linux server and then forward the graphical display of that application back to the Linux workstation. Which of the following would enable the user to perform this action?
User1 reports "access denied" errors while trying to execute app. Given the following outputs:
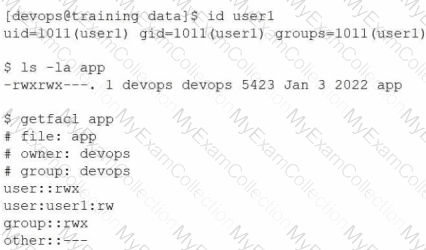
Which of the following options will remediate this issue?
While troubleshooting server issues, a Linux systems administrator obtains the following output:
yaml
total used free shared buff/cache available
Mem: 3736 3538 33 2 48 25
Swap: 2047 1824 223
Which of the following best describes the state of the system?
A Linux administrator needs to replace the content of the test1.sh file with the content of the test2.sh file. Which of the following commands will help accomplish this task?
An administrator would like to securely connect to a server and forward port 8080 on a local machine to port 80 on the server. Which of the following commands should the administrator use to satisfy both requirements?
A systems administrator is creating new user accounts on several Linux machines and wants to automate the process from a Linux system used for operations. In this operations system, the list of servers is located in the /home/user/serverslist file and the list of user accounts is located in the /home/user/userslist file. Which of the following scripts will help accomplish this task?
An administrator is troubleshooting a database service outage that was reported by a monitoring system. Given the following output:
$ systemctl status mariadb
Oct 20 16:40:45 comptia systemd[1]: mariadb.service: Main process exited, code=killed, status=9/KILL
Oct 20 16:40:45 comptia systemd[1]: mariadb.service: Failed with result 'signal'.
Oct 20 16:40:50 comptia systemd[1]: Stopped MariaDB 10.3 database server.
$ dmesg
[ 1061.491433] oom-kill:constraint=CONSTRAINT_NONE,nodemask=(null),cpuset=/,mems_allowed=0,global_oom, task_memcg=/system.slice/mariadb.service, task=mysqld,pid=1981,uid=27
[ 1061.491453] Out of memory: Killed process 1981 (mysqld) total-vm:330668kB, anon-rss:31316kB, file-rss:OkB, shmem-rss:OkB, UID:27 pgtables:324kB oom_score_adj:0
Which of the following is the reason for the outage?
A Linux engineer needs to block an incoming connection from the IP address 2.2.2.2 to a secure shell server and ensure the originating IP address receives a response that a firewall is blocking the connection. Which of the following commands can be used to accomplish this task?
When trying to connect from the bastion host to the remote server, a Linux user always forgets to add some required options in the SSH command line. Which of the following is the best way to permanently solve the user's issue?
After listing the properties of a system account, a systems administrator wants to remove the expiration date of a user account. Which of the following commands will accomplish this task?
A systems administrator needs to remove a disk from a Linux server. The disk size is 500G, and it is the only one that size on that machine. Which of the following commands can the
administrator use to find the corresponding device name?
An administrator is provisioning an Apache web server. When the administrator visits the server website, the browser displays a message indicating the website cannot be reached. Which of the following commands should the administrator use to verify whether the service Is running?
A Linux administrator wants to prevent the httpd web service from being started both manually and automatically on a server. Which of the following should the administrator use to accomplish this task?
Ann, a security administrator, is performing home directory audits on a Linux server. Ann issues the su Joe command and then issues the Is command. The
output displays files that reside in Ann's home directory instead of Joe's. Which of the following represents the command Ann should have issued in order to list Joe's files?
NO: 20:
A hardened physical Linux system allows regular, unprivileged users to remotely connect to the server using SSH only. No sudo tool has been installed. Which of the following should the Linux administrator use to perform administrative tasks on this host? (Select two).
A Linux administrator is enabling root log-in over SSH on a server. Which of the following combinations of files and parameters should the administrator modify to accomplish this task?
Which of the following commands should a technician use to create an administrative account for the username Joe?
A network administrator issues the dig www.foo.com command and receives an NXDOMAIN response. Which of the following files should the administrator check first?
Following the migration from a disaster recovery site, a systems administrator wants a server to require a user to change credentials at initial login. Which of the following commands should
be used to ensure the aging attribute?
A Linux administrator needs to deploy an Apache web server in a container. In addition, the container needs to run in the background, and the web server needs to be exposed on port 8080 of the host machine. Which of the following commands will satisfy these requirements?
A systems administrator is checking the system logs. The administrator wants to look at the last 20 lines of a log. Which of the following will execute the command?
A Linux administrator is troubleshooting an issue in which an application service failed to start on a Linux server. The administrator runs a few commands and gets the following outputs:
Based on the above outputs, which of the following is the MOST likely action the administrator should take to resolve this issue?
A systems administrator wants to test the route between IP address 10.0.2.15 and IP address 192.168.1.40. Which of the following commands will accomplish this task?
A systems administrator is tasked with installing GRUB on the legacy MBR of the SATA hard drive. Which of the following commands will help the administrator accomplish this task?
A junior administrator is trying to set up a passwordless SSH connection to one of the servers. The administrator follows the instructions and puts the key in the authorized_key file at the server, but the administrator is still asked to provide a password during the connection.
Given the following output:
Which of the following commands would resolve the issue and allow an SSH connection to be established without a password?
A systems administrator wants to back up the directory /data and all its contents to /backup/data on a remote server named remote. Which of the following commands will achieve the desired effect?
A systems administrator has been tasked with disabling the nginx service from the environment to prevent it from being automatically and manually started. Which of the following commands will accomplish this task?
A Linux administrator is tasked with adding users to the system. However, the administrator wants to ensure the users’ access will be disabled once the project is over. The expiration date should be 2021-09-30. Which of the following commands will accomplish this task?
An administrator installed an application from source into /opt/operations1/ and has received numerous reports that users are not able to access the application without having to use the full path /opt/operations1/bin/*. Which of the following commands should be used to resolve this issue?
A systems administrator needs to check if the service systemd-resolved.service is running without any errors. Which of the following commands will show this information?
A Linux administrator was tasked with deleting all files and directories with names that are contained in the sobelete.txt file. Which of the following commands will accomplish this task?
A Linux engineer has been notified about the possible deletion of logs from the file /opt/app/logs. The engineer needs to ensure the log file can only be written into without removing previous entries.
Which of the following commands would be BEST to use to accomplish this task?
A systems administrator requires that all files that are created by the user named web have read-only permissions by the owner. Which of the following commands will satisfy this requirement?
A Linux administrator is troubleshooting SSH connection issues from one of the workstations.
When users attempt to log in from the workstation to a server with the IP address 104.21.75.76, they receive the following message:
The administrator reviews the information below:
Which of the following is causing the connectivity issue?
A Linux administrator is troubleshooting the root cause of a high CPU load and average.
Which of the following commands will permanently resolve the issue?
An administrator is unable to sync servers to the new NTP server IP address given by the service provider despite several attempts. Looking at the below output

Which of the following commands will help resolve the issue?







