How are HTTP Event Collector (HEC) tokens configured in a managed Splunk Cloud environment?
A Splunk Cloud administrator is looking to allow a new group of Splunk users in the marketing department to access the Splunk environment and view a dashboard with relevant data. These users need to access marketing data (stored in the marketing_data index), but shouldn't be able to access other data, such as events related to security or operations.
Which approach would be the best way to accomplish these requirements?
A log file is being ingested into Splunk, and a few events have no date stamp. How would Splunk first try to determine the missing date of the events?
What information is identified during the input phase of the ingestion process?
Windows Input types are collected in Splunk via a script which is configurable using the GUI. What is this type of input called?
When creating a new index, which of the following is true about archiving expired events?
By default, which of the following capabilities are granted to the sc_admin role?
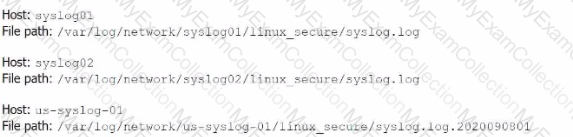
Li was asked to create a Splunk configuration to monitor syslog files stored on Linux servers at their organization. This configuration will be pushed out to multiple systems via a Splunk app using the on-prem deployment server.
The system administrators have provided Li with a directory listing for the logging locations on three syslog hosts, which are representative of the file structure for all systems collecting this data. An example from each system is shown below:
A)
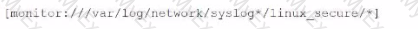
B)
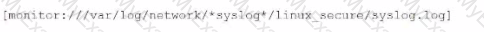
C)
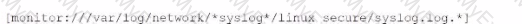
D)
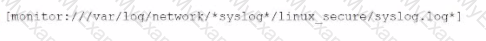
Which of the following is a valid method to test if a forwarder can successfully send data to Splunk Cloud?
What is the name of the Splunk index that contains the most valuable information for troubleshooting a Splunk issue?
What is the default port for sending data via HTTP Event Collector to Splunk Cloud?
Which of the following tasks is not managed by the Splunk Cloud administrator?

