A server technician is installing application updates on a Linux server. When the technician tries to install a MySQL update, the GUI displays the following error message: AVC denial. Which of the following should the technician do for the MySQL update to install?
Which of the following backup types only backs up files that have changed since the last full backup?
Which of the following documents would explain the consequences of server downtime?
A senior administrator was notified that a junior administrator installed software on a server that should not have new software installed on it. The senior administrator decides to restrict the server via a Group Policy. Which of the following can be used to elevate the permissions?
An administrator is upgrading a group of legacy blade servers to the latest version of the hypervisor. After restarting the server, the upgrade is interrupted. The hypervisor is not available, and the update is not successful. Which of the following should the administrator do next to accomplish this upgrade?
A technician is installing an OS on ten servers. Which of the following media installation types would allow for the fastest installation time?
A virtual host has four NICs and eight VMs. Which of the following should the technician configure to enable uplink redundancy?
Which of the following backup types is used to capture all data regardless of any changes from the previous backup jobs?
Which of the following benefits of virtualization is most important during a data center migration?
A server recently started sending error messages about running out of memory while in use. After a maintenance period during which more memory was added, the server is still unable to consistently remain powered on. Which of the following should the technician check first?
An administrator is installing a new server and OS. After installing the OS, the administrator logs in and wants to quickly check the network configuration. Which of the following is the best command to use to
accomplish this task?
An administrator connects a server to an external gigabit switch, but the server can only get a speed of 100Mbps. Which of the following is the most likely cause of this issue?
A server is only able to connect to a gigabit switch at 100Mb. Other devices are able to access the network port at full gigabit speeds, and when the server is brought to another location, it is able to connect at full gigabit speed. Which of the following should an administrator check first?
A technician is installing a large number of servers in a data center with limited rack space. Which of the following would accomplish this goal while using the least amount of space?
A server administrator is connecting a new storage array to a server. The administrator has obtained multiple IP addresses for the array. Which of the following connection types is the server most likely using to connect to the array?
An administrator notices high traffic on a certain subnet and would like to identify the source of the traffic. Which of the following tools should the administrator utilize?
A systems administrator notices a newly added server cannot see any of the LUNs on the SAN. The SAN switch and the local HBA do not display any link lights. Which of the following is most likely the issue?
A systems administrator is installing Windows on an 8TB drive and would like to create a single 8TB partition on the disk. Which of the following options should the administrator use?
Which of the following authentication types defines credentials as "something you have"?
A server administrator is taking advantage of all the available bandwidth of the four NICs on the server. Which of the following NIC-teaming technologies should the server administrator utilize?
A server technician notices several of the servers in a data center are making loud noises. The servers are still working correctly, and no indicator lights show any issues. Which of the following should the technician do first to ensure the issues are corrected and the servers remain online?
An administrator is configuring the storage for a new database server, which will host databases that are mainly used for archival lookups. Which of the following storage types will yield the fastest database read performance?
A security team must ensure that unauthorized individuals are unable to tailgate through the data center's entrance. Which of the following should be implemented to stop this type of breach from happening?
A systems administrator is setting up a second VLAN for end users. Which of the following should be provisioned for a DHCP server to be able to receive client requests from a different subnet?
A technician notices a server that contains four fans is now louder than normal even though the temperature in the room has not changed and the load on the server has not increased. Which of the following is most likely the cause of the noise?
A new company policy requires that any data loss in excess of one hour is unacceptable in the event of a disaster. Which of the following concepts is being referred to in this policy?
Hackers recently targeted a company with an attack that resulted in a system breach, which compromised the organization's data. Because of the system breach, the administrator had to bypass normal change management procedures. Which of the following change management activities was necessary?
A server administrator deployed a new product that uses a non-standard port for web access on port 8443. However, users are unable to access the new
application. The server administrator checks firewall rules and determines 8443 is allowed. Which of the following is most likely the cause of the issue?
Which of the following attacks is the most difficult to mitigate with technology?
Two developers are working together on a project, and they have built out a set of snared servers that both developers can access over the internet. Which of the following cloud models is this an example of?
A site is considered a warm site when it:
has basic technical facilities connected to it.
has faulty air conditioning that is awaiting service.
is almost ready to take over all operations from the primary site.
The internal IT department policy for monitoring server health requires that evidence of server reboots be collected and reviewed on a regular basis. Which of the following should be monitored to best provide this evidence?
A server administrator notices drive C on a critical server does not have any available space, but plenty of unallocated space is left on the disk. Which of the following should the administrator perform to address the availability issue while minimizing downtime?
A server in the data center reportedly has a BSOD and is not responding. The server needs to be rebooted. Which of the following is the best method to reboot the server remotely?
A startup is migrating a stand-alone application that stores Pll to the cloud. Which of the following should be encrypted?
A server administrator is currently working on an incident. Which of the following steps should the administrator perform before resolving the issue?
Following a recent power outage, a server on a server farm has been running slowly. A technician receives a ticket with a request to check for anything out of the ordinary. The technician sees an orange light on the front console of the server, indicating an error. Which of the following should the technician check next?
A systems administrator notices the fans are running at full speed in a newly upgraded server. Which of the following should be done to address this issue?
An administrator is patching a file and print server After rebooting the server, it begins acting strangely. The administrator tries to open Print Management, but it will not open Upon inspection, the spooler service has been disabled. The administrator then notices the server has services that should be enabled but are disabled. Which of the following actions should the administrator take next to resolve the issue as quickly as possible?
An administrator is troubleshooting an application performance issue on a virtual server with two vCPUs. The application performance logs indicate CPU contention. The administrator adds more vCPU cores to the VM, yet the issue persists. Which of the following is the most likely reason for this issue?
After installing a new file server, a technician notices the read times for accessing the same file are slower than the read times for other file servers.
Which of the following is the first step the technician should take?
A systems administrator is performing a routine update to a server. The administrator applies the update, restarts the server, and then conducts routine testing that reveals the critical functionality provided by the server is unavailable. Event logs indicate a core service is failing to start. The service is configured to start automatically, and rolling back the update does not correct the issue. Which of the following is most likely causing the service failure?
Which of the following backup types copies changed data from a server and then combines the backups on the backup target?
An administrator is investigating several unexpected documents and video files that recently appeared in a network share. The administrator checks the properties of the files and sees the author's name on the documents is not a company employee. The administrator questions the other users, but no one knows anything about the files. The administrator then checks the log files and discovers the FTP protocol was used to copy the files to the server. Which of the following needs to be done to prevent this from happening again?
A server administrator purchased a single license key to use for all the new servers that will be imaged this year. Which of the following MOST likely refers to the licensing type that will be used?
A server administrator is creating a script that will move files only if they were created before a date input by the user. Which of the following constructs will allow the script to apply this test until all available files are assessed?
A company needs to increase the security controls on its servers. An administrator is implementing MFA on all servers using cost effective techniques. Which of the following should the administrator use to satisfy the MFA requirement?
A staff memberwho a monitoring a data center reports one rack is experiencing higher temperatures than the racks next to it, despite the hardware in each rack being the same. Which of the following actions would MOST likely remediate the heal issue?
An organization is donating its outdated server equipment to a local charity. Which of the following describes what the organization should do BEFORE donating the equipment?
The Chief Information Officer of a data center is concerned that transmissions from the building can be detected from the outside. Which of the
following would resolve this concern? (Select TWO).
Which of the following is a system that scans outgoing email for account numbers, sensitive phrases, and other forms of Pll?
Which of the following is the MOST secure method to access servers located in remote branch offices?
A developer is creating a web application that will contain five web nodes. The developer's main goal is to ensure the application is always available to the end users. Which ofthefollowing should the developer use when designing the web application?
A server administrator just installed a new physical server and needs to harden the applications on the server. Which of the following best describes a method of application hardening?
Which of the following commands would MOST likely be used to register a new service on a Windows OS?
A systems administrator is trying to determine why users in the human resources department cannot access an application server. The systems administrator reviews the application logs but does not see any attempts by the users to access the application. Which of the following is preventing the users from accessing the application server?
Which of the following concepts refers to prioritizing a connection that had previously worked successfully?
A server administrator receives the following output when trying to ping a local host:
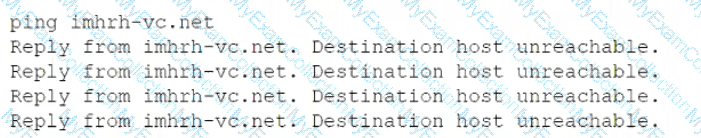
Which of the following is MOST likely the issue?
A server administrator has received calls regarding latency and performance issues with a file server. After reviewing all logs and server features the administrator discovers the server came with four Ethernet ports, out only one port is currently in use. Which of the following features will enable the use of all available ports using a single IP address?
An administrator is working locally in a data center with multiple server racks. Which of the following is the best low-cost option to connect to any server while on site?
A security analyst completed a port scan of the corporate production-server network. Results of the scan were then provided to a systems administrator for immediate action. The following table represents the requested changes:
The systems administrator created local firewall rules to block the ports indicated above. Immediately, the service desk began receiving calls about the internet being down. The systems administrator then reversed the changes, and the internet became available again. Which of the following ports on DNSSrv must remain open when the firewall rules are reapplied?
A server administrator noticesthe/var/log/audit/audit.logfileon a Linux server is rotating loo frequently. The administrator would like to decrease the number of times the leg rotates without losing any of the information in the logs. Which of the following should the administrator configure?
Which of the following BEST describes overprovisioning in a virtual server environment?
A backup application is copying only changed files each time it runs. During a restore, however, only a single file is used. Which of the following backup methods does this describe?
Which of the following BEST measures how much downtime an organization can tolerate during an unplanned outage?
A systems administrator is setting up a server farm for a new company. The company has a public range of IP addresses and uses the addresses internally. Which of the following IP addresses best fits this scenario?
A technician learns users are unable to tog in to a Linux server with known-working LDAP credentials. The technician logs in to the server with a local account and confirms the system is functional can communicate over the network, and is configured correctly However, the server log has entries regarding Kerberos errors. Which of the following is the MOST likely source of the issue?
A user logs in to a Linux server and attempts to run the following command:
sudo emacs /root/file
However the user gets the following message:
User userid is not allowed to execute Temacs' on this server. Which of the following would BEST allow the user to find out which commands can be used?
Users report they ate unable to access an application after a recent third-party patch update. The physical server that is hosting the application keeps crashing on reboot. Although the update was installed directly from the manufacturer's support website as recommended it has now been recalled and removed from the website as the update unintentionally installed unauthorized software after a reboot. Which of the following steps should the administrator perform to restore access to the application while minimizing downtime? (Select TWO)
Which of the following commands should a systems administrator use to create a batch script to map multiple shares'?
Joe. a user m the IT department cannot save changes to a sensitive file on a Linux server. An 1s -1& snows the following listing;
Which of the following commands would BEST enable the server technician to allow Joe tohaveaccess without granting excessive access to others?
Which of the following backup types resets the archive bit each time it is run?
An administrator is troubleshooting a failed NIC in an application server. The server uses DHCP to get all IP configurations, and the server must use a
specific IP address. The administrator replaces the NIC, but then the server begins to receive a different and incorrect IP address. Which of the following will enable the server to get the proper IP address?
A hardware technician is installing 19 1U servers in a 42 the following unit sizes should be allocated per server?
A server administrator needs to ensure all Window-based servers within a data center have RDP disabled. There are thousands of servers performing various roles. Which of the following is the best way to meet this requirement?
A technician is troubleshooting a server issue. The technician has determined several possible causes of the issue and has identified various solutions. Which of the following should the technician do next?
A VLAN needs to be configured within a virtual environment for a new VM. Which of the following will ensure the VM receives a correct IP address?
An administrator is only able to log on to a server with a local account. The server has been successfully joined to the domain and can ping other servers by IP address. Which of the following locally defined settings is MOST likely misconfigured?
Which of the following often-overlooked parts of the asset life cycle can cause the greatest number of issues in relation to Pll exposure?
A server administrator is building a pair of new storage servers. The servers will replicate; therefore, no redundancy is required, but usable capacity
must be maximized. Which of the following RAID levels should the server administrator implement?
A storage engineer responds to an alarm on a storage array and finds the battery on the RAID controller needs to be replaced. However, the
replacement part will not be available for 14 days. The engineer needs to identify the impact of the failed battery on the system. Which of the following best describes the impact?
A security technician generated a public/private key pair on a server. The technician needs to copy the key pair to another server on a different subnet. Which of the following is the most secure method to copy the keys?
HTTP
Which of the following asset management documents is used to identify the location of a serves within a data center?
Which of the following testing exercises for disaster recovery is primarily used to discuss incident response strategies for critical systems without affecting production data?
Which of the following refers to the requirements that dictate when to delete data backups?
A company's security team has noticed employees seem to be blocking the door in the main data center when they are working on equipment to avoid having to gain access each time. Which of the following should be implemented to force the employees to enter the data center properly?
A user has been unable to authenticate to the company's external, web-based database after clicking a link in an email that required the user to change the account password. Which of the following steps should the company take next?
A server administrator is completing an OS installation for a new server. The administrator patches the server with the latest vendor-suggested software, configures DHCP, and verifies all network cables are properly connected in the IDF, but there is no network connectivity. Which of the following is the MOST likely reason for the lack of connectivity?
A company uses a hot-site, disaster-recovery model. Which of the following types of data replication is required?
A datacenter technician is attempting to troubleshoot a server that keeps crashing. The server runs normally for approximately five minutes, but then it crashes. After restoring the server to operation, the same cycle repeats. The technician confirms none of the configurations have changed, and the load on the server is steady from power-on until the crash. Which of the following will MOST likely resolve the issue?
Which of the following is the MOST appropriate scripting language to use for a logon script for a Linux box?
A server administrator is deploying a new server that has two hard drives on which to install the OS. Which of the following RAID configurations should be used to provide redundancy for the OS?
An administrator is troubleshooting a RAID issue in a failed server. The server reported a drive failure, and then it crashed and would no longer boot. There are two arrays on the failed server: a two-drive RAIO 0 set tor the OS, and an eight-drive RAID 10 set for data. Which of the following failure scenarios MOST likely occurred?
When configuring networking on a VM, which of the following methods would allow multiple VMs to share the same host IP address?
A server administrator is exporting Windows system files before patching and saving them to the following location:
\\server1\ITDept\
Which of the following is a storage protocol that the administrator is MOST likely using to save this data?
A company is running an application on a file server. A security scan reports the application has a known vulnerability. Which of the following would be the company’s BEST course of action?
Which of the following encryption methodologies would MOST likely be used to ensure encrypted data cannot be retrieved if a device is stolen?
A server administrator needs to check remotely for unnecessary running services across 12 servers. Which of the following tools should the administrator use?
A technician needs to deploy an operating system that would optimize server resources. Which of the following server installation methods would BEST meet this requirement?
A server administrator added a new drive to a server. However, the drive is not showing up as available. Which of the following does the administrator need to do to make the drive available?
A server has experienced several component failures. To minimize downtime, the server administrator wants to replace the components while the server is running. Which of the following can MOST likely be swapped out while the server is still running? (Select TWO).
A technician has several possible solutions to a reported server issue. Which of the following BEST represents how the technician should proceed with troubleshooting?
A systems administrator is investigating a server with a RAID array that will not boot into the OS. The administrator notices all the hard drives are reporting to be offline. The administrator checks the RAID controller and verifies the configuration is correct. The administrator then replaces one of the drives with a known-good drive, but it appears to be unavailable as well. Next, the administrator takes a drive out of the server and places it in a spare server, and the drive is available and functional. Which of the following is MOST likely causing the issue?
A technician has received multiple reports of issues with a server. The server occasionally has a BSOD, powers off unexpectedly, and has fans that run continuously. Which of the following BEST represents what the technician should investigate during troubleshooting?
Which of the following policies would be BEST to deter a brute-force login attack?
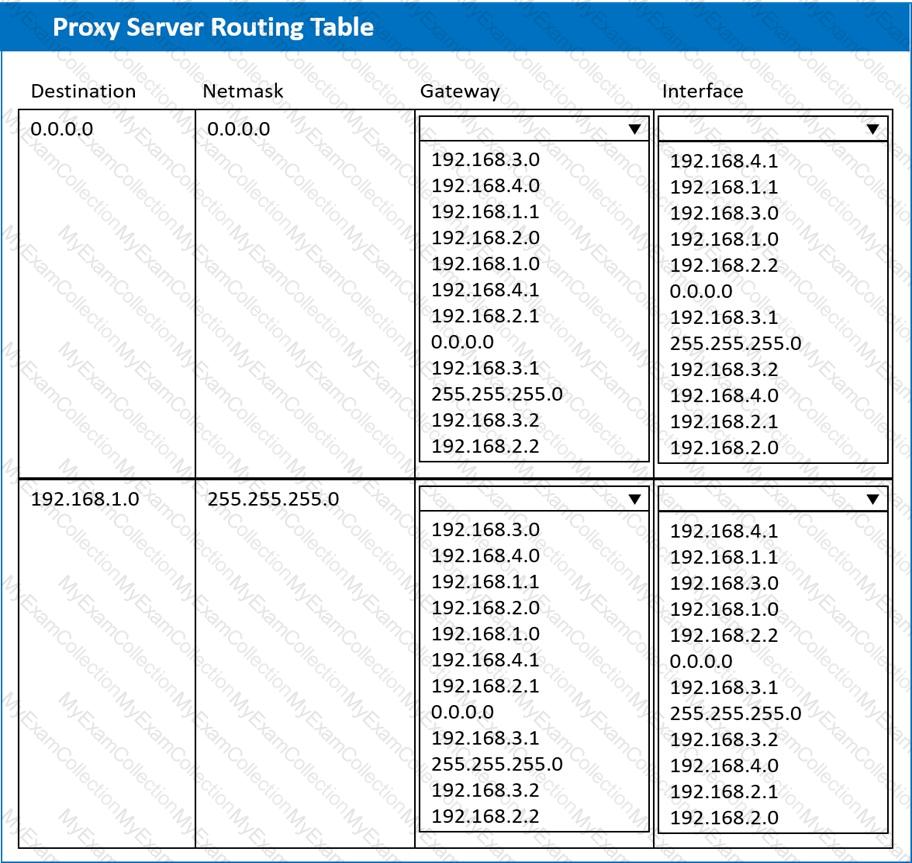
A systems administrator deployed a new web proxy server onto the network. The proxy server has two interfaces: the first is connected to an internal corporate firewall, and the second is connected to an internet-facing firewall. Many users at the company are reporting they are unable to access the Internet since the new proxy was introduced. Analyze the network diagram and the proxy server’s host routing table to resolve the Internet connectivity issues.
INSTRUCTIONS
Perform the following steps:
1. Click on the proxy server to display its routing table.
2. Modify the appropriate route entries to resolve the Internet connectivity issue.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A server technician is installing a new server OS on legacy server hardware. Which of the following should the technician do FIRST to ensure the OS will work as intended?
Hosting data in different regional locations but not moving it for long periods of time describes:
Which of the following steps in the troubleshooting theory should be performed after a solution has been implemented? (Choose two.)
Network connectivity to a server was lost when it was pulled from the rack during maintenance. Which of the following should the server administrator use to prevent this situation in the future?
An administrator is configuring a host-based firewall tor a server. The server needs to allow SSH, FTP, and LDAP traffic. Which of the following ports must be configured so this traffic will be allowed? (Select THREE).
A technician is checking a server rack. Upon entering the room, the technician notices the tans on a particular server in the rack are running at high speeds. This is the only server in the rack that is experiencing this behavior. The ambient temperature in the room appears to be normal. Which of the following is the MOST likely reason why the fans in that server are operating at full speed?
A server administrator needs to harden a server by only allowing secure traffic and DNS inquiries. A port scan reports the following ports are open:
An administrator needs to perform bare-metal maintenance on a server in a remote datacenter. Which of the following should the administrator use to access the server’s console?
A server administrator is testing a disaster recovery plan. The test involves creating a downtime scenario and taking the necessary steps. Which of the following testing methods is the administrator MOST likely performing?
A technician is unable to access a server’s package repository internally or externally. Which of the following are the MOST likely reasons? (Choose two.)
A technician is installing a variety of servers in a rack. Which of the following is the BEST course of action for the technician to take while loading the rack?
A server administrator is experiencing difficulty configuring MySQL on a Linux server. The administrator issues the getenforce command and receives the following output:
># Enforcing
Which of the following commands should the administrator issue to configure MySQL successfully?
The Chief Information Officer (CIO) of a datacenter is concerned that transmissions from the building can be detected from the outside. Which of the following would resolve this concern? (Choose two.)
A technician is connecting a Linux server to a share on a NAS. Which of the following is the MOST appropriate native protocol to use for this task?
A company deploys antivirus, anti-malware, and firewalls that can be assumed to be functioning properly. Which of the following is the MOST likely system vulnerability?
A security analyst suspects a remote server is running vulnerable network applications. The analyst does not have administrative credentials for the server. Which of the following would MOST likely help the analyst determine if the applications are running?
Users have noticed a server is performing below Baseline expectations. While diagnosing me server, an administrator discovers disk drive performance has degraded. The administrator checks the diagnostics on the RAID controller and sees the battery on me controller has gone bad. Which of the following is causing the poor performance on the RAID array?
A company is reviewing options for its current disaster recovery plan and potential changes to it. The security team will not allow customer data to egress to non-company equipment, and the company has requested recovery in the shortest possible time. Which of the following will BEST meet these goals?
A technician is working on a Linux server. The customer has reported that files in the home directory are missing. The /etc/ f stab file has the following entry:
nfsserver:/home /home nfs defaults 0 0
However, a df -h /home command returns the following information:
/dev/sda2 10G 1G 9G 10% /home
Which of the following should the technician attempt FIRST to resolve the issue?
A datacenter in a remote location lost power. The power has since been restored, but one ol the servers has not come back online. After some investigation, the server is found to still be powered off. Which of the following is the BEST method to power on the server remotely?
Which of the following can be used to map a network drive to a user profile?
A server administrator has noticed that the storage utilization on a file server is growing faster than planned. The administrator wants to ensure that, in the future, there is a more direct relationship between the number of users using the server and the amount of space that might be used. Which of the following would BEST enable this correlation?
Which of the following allows for a connection of devices to both sides inside of a blade enclosure?
Users at a company work with highly sensitive data. The security department implemented an administrative and technical control to enforce least-privilege access assigned to files. However, the security department has discovered unauthorized data exfiltration. Which of the following is the BEST way to protect the data from leaking?
A server in a remote datacenter is no longer responsive. Which of the following is the BEST solution to investigate this failure?
Users cannot access a new server by name, but the server does respond to a ping request using its IP address. All the user workstations receive their IP information from a DHCP server. Which of the following would be the best step to perform NEXT?
Which of the following can be BEST described as the amount of time a company can afford to be down during recovery from an outage?
A server administrator is installing an OS on a new server. Company policy states no one is to log in directly to the server. Which of the following Installation methods is BEST suited to meet the company policy?
Which of the following should an administrator use to transfer log files from a Linux server to a Windows workstation?
Which of the following should a server administrator use when writing a script with a function that needs to be run ten times?
A technician is investigating a server's configuration to secure it from physical threats. The technician checks the BIOS and sees the following boot order:
USB Drive CDROM Drive Network Adapter RAID Controller
Additionally, the server's host OS is stored on mirrored drives. Which of the following should the technician do to secure the server?
Multiple users have reported an issue accessing files on a specific server. Which of the following should be the first step in troubleshooting this issue?
A software developer is unable to reach an internal website. The developer's attempt to ping the FQDN returns the following IP address: 104.18.17.32. Which of the following is the most likely reason for this result?
An administrator reviews a new server that was received from a vendor and notes the OS has been installed to a two-drive array configured with RAID 0. Which of the following best describes what will happen if a drive in that array fails?


