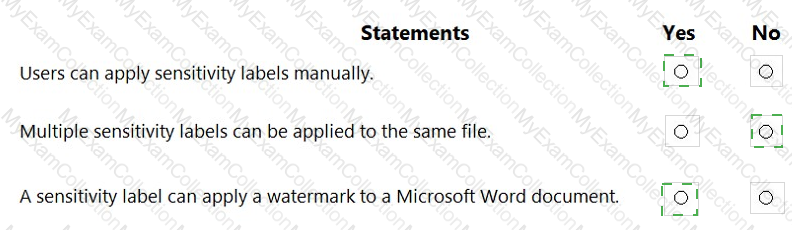
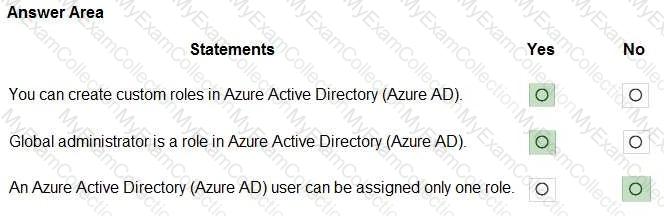
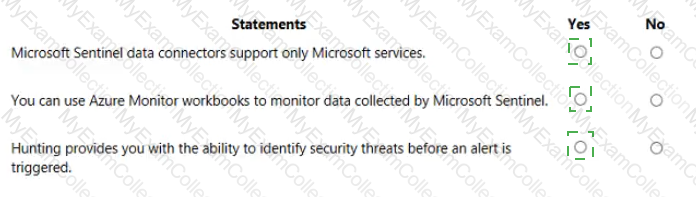
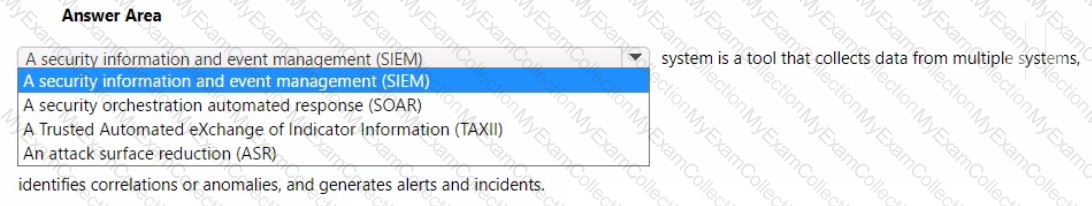
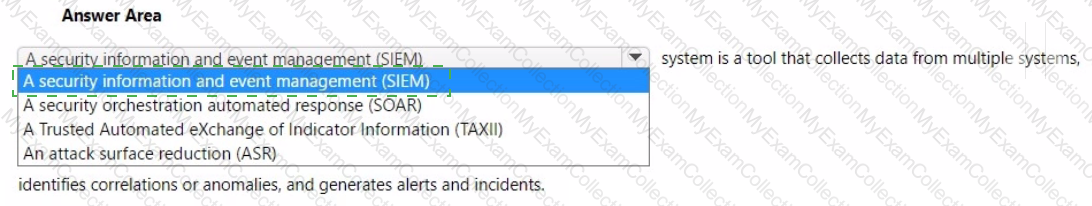
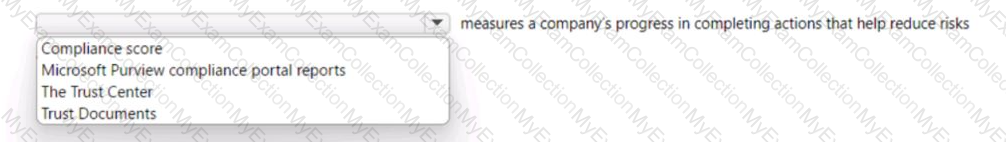
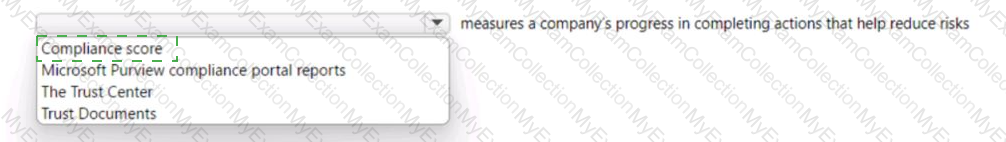
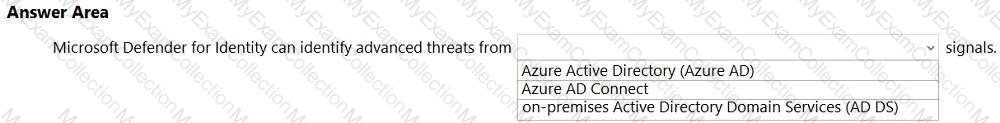
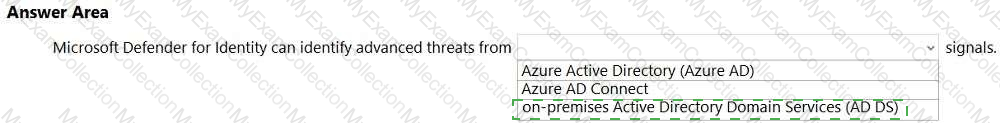
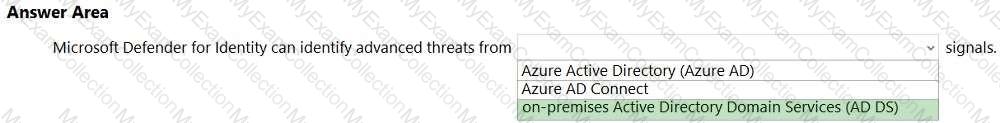
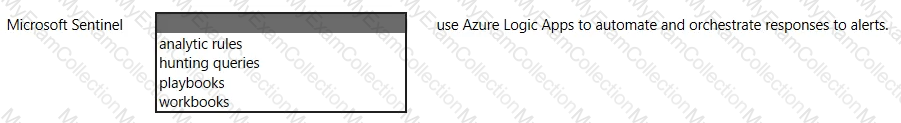
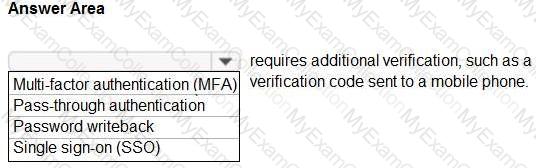
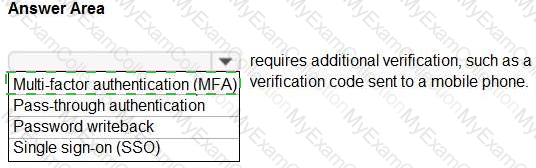
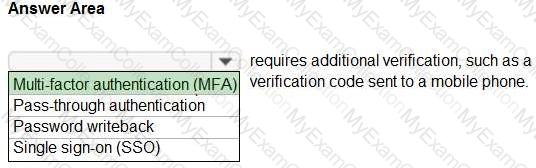
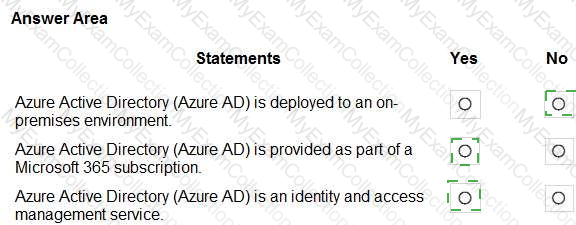
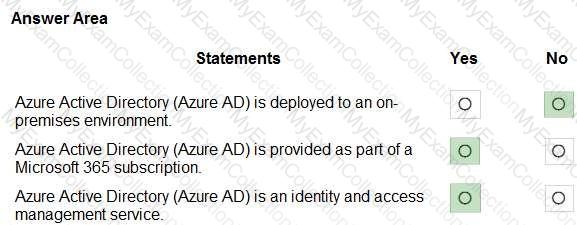
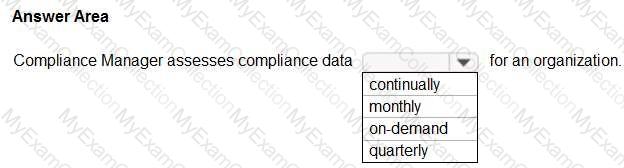
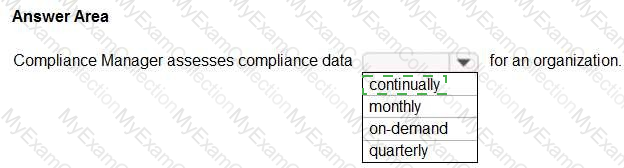
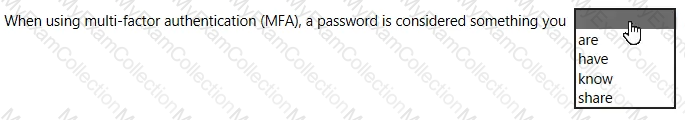
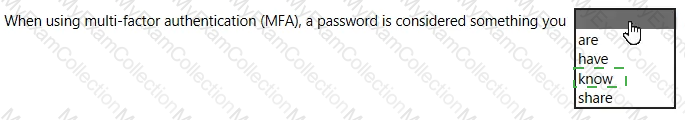
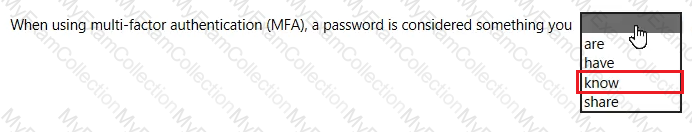
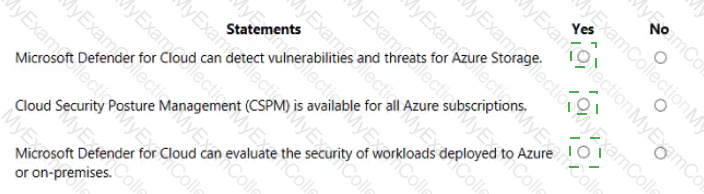
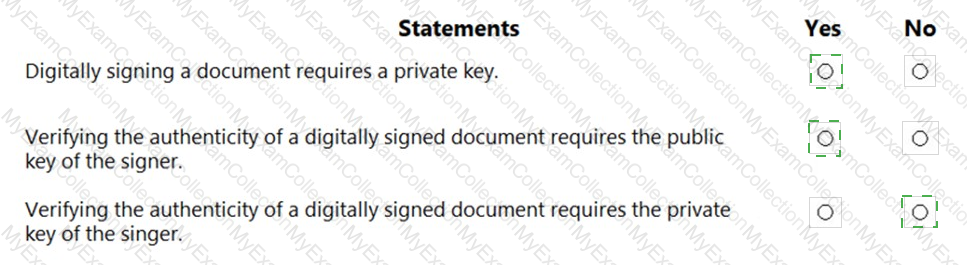
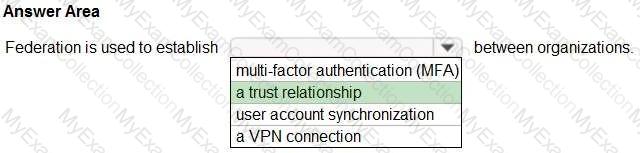
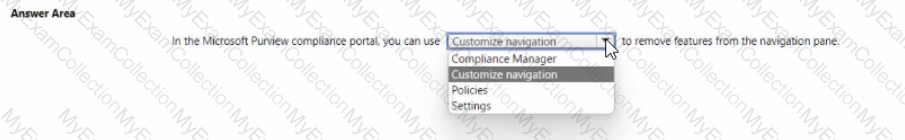
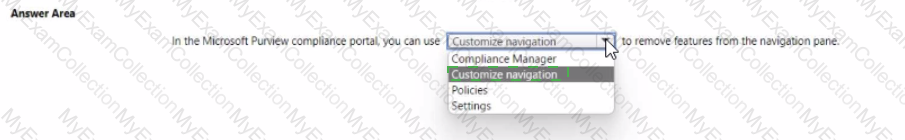
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
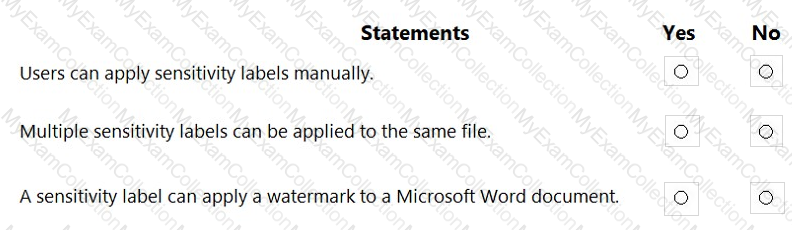
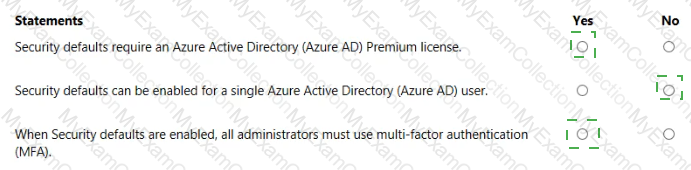
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
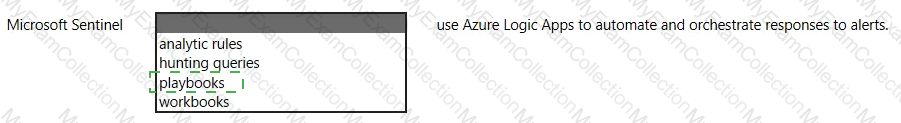
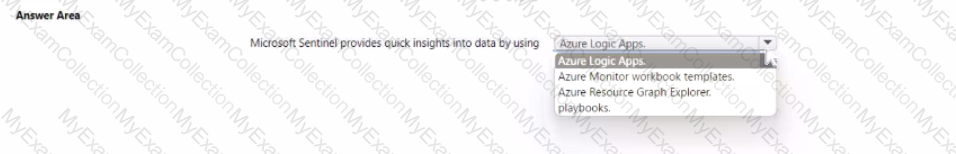
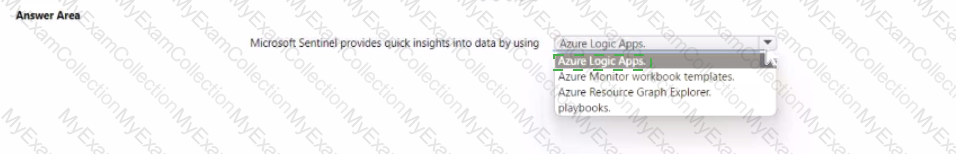
Which feature provides the extended detection and response (XDR) capability of Azure Sentinel?
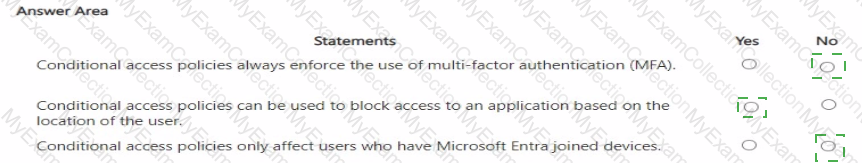
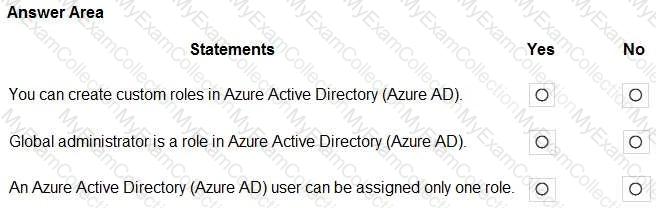
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point
Which Microsoft 365 feature can you use to restrict users from sending email messages that contain lists of customers and their associated credit card numbers?
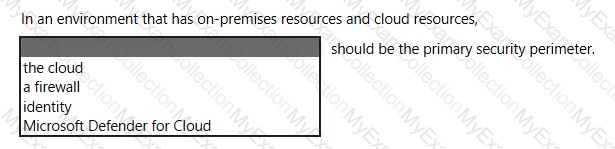
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
You have an Azure subscription.
You need to implement approval-based, tiProme-bound role activation.
What should you use?
Which Microsoft 365 feature can you use to restrict communication and the sharing of information between members of two departments at your organization?
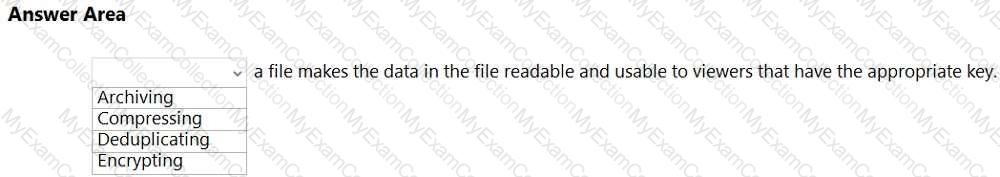
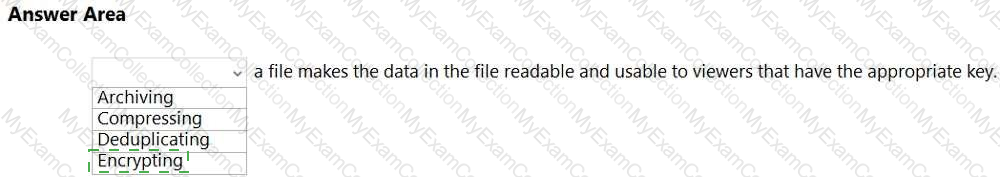
What Microsoft Purview feature can use machine learning algorithms to detect and automatically protect sensitive items?
Which Azure Active Directory (Azure AD) feature can you use to restrict Microsoft Intune-managed devices from accessing corporate resources?
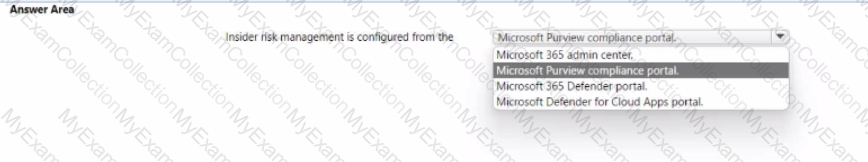
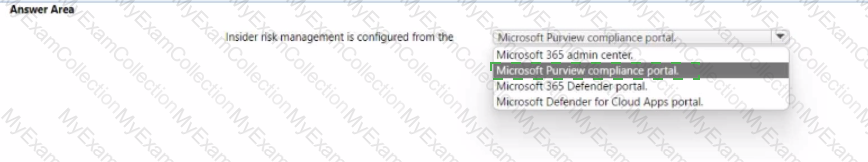
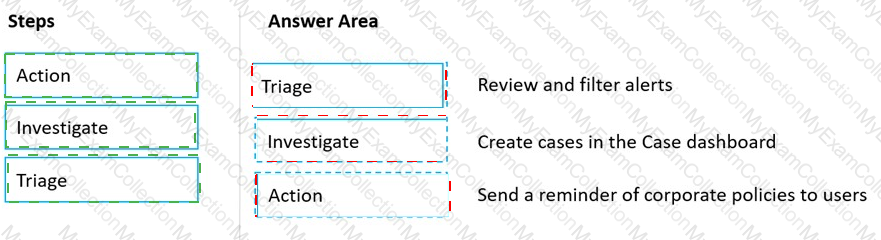
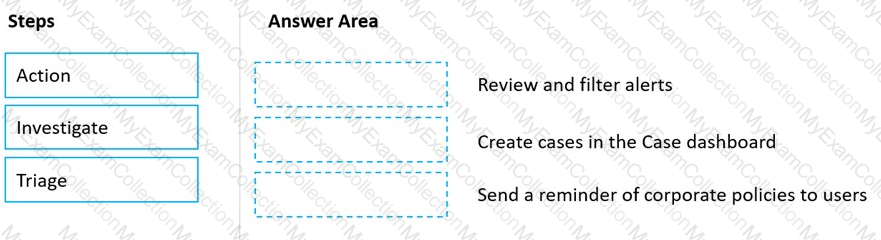
Match the Microsoft 365 insider risk management workflow step to the appropriate task.
To answer, drag the appropriate step from the column on the left to its task on the right. Each step may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.
What can you use to provision Azure resources across multiple subscriptions in a consistent manner?
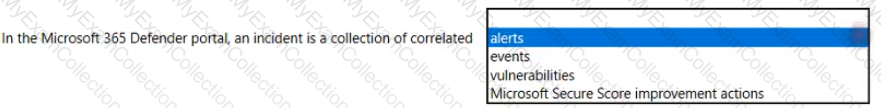
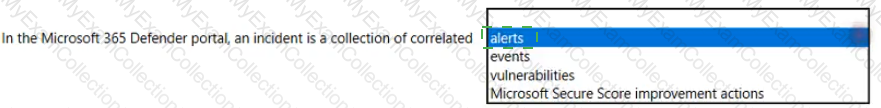
Which two cards are available in the Microsoft 365 Defender portal? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
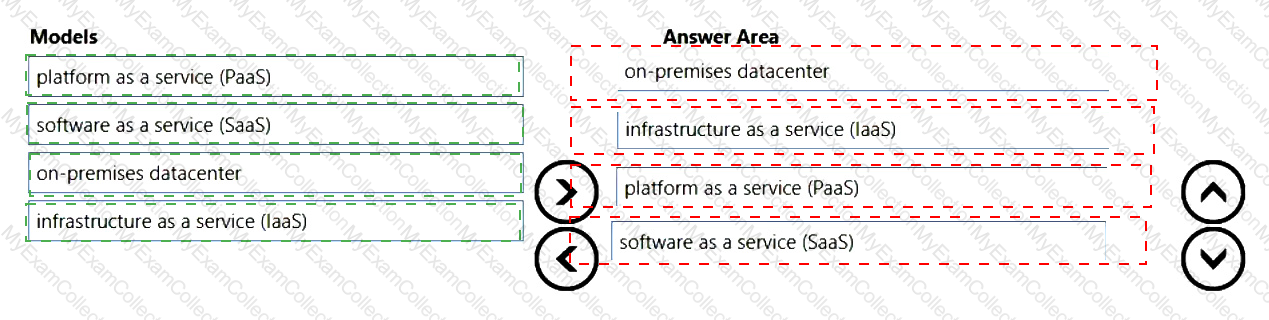
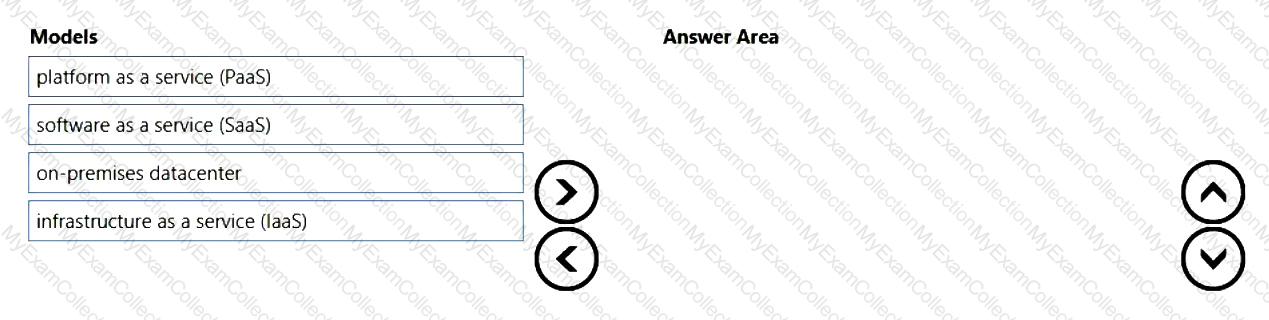
You need to identify which cloud service models place the most responsibility on the customer in a shared responsibility model.
in which order should you list the service models from the most customer responsibility (on the top) to the least customer responsibility (on the bottom)? To answer, move all models from the list of models to the answer area and arrange them in the correct order.
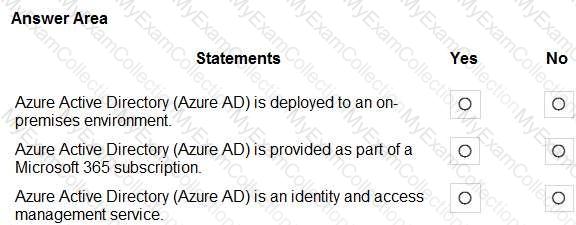
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
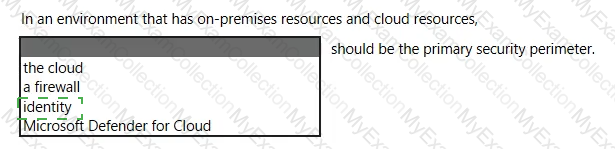
Which pillar of identity relates to tracking the resources accessed by a user?
What should you create to search and export content preserved in an eDiscovery hold?
What are three uses of Microsoft Cloud App Security? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
You have an Azure subscription.
You need to implement approval-based time-bound role activation.
What should you use?
Which Azure Active Directory (Azure AD) feature can you use to evaluate group membership and automatically remove users that no longer require membership in a group?
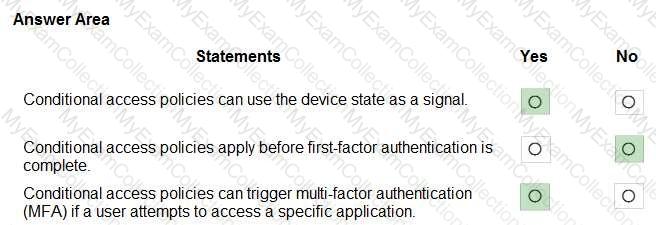
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

In the Microsoft Cloud Adoption Framework for Azure, which two phases are addressed before the Ready phase? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
What can you use to provide a user with a two-hour window to complete an administrative task in Azure?
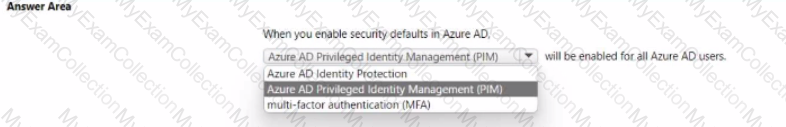
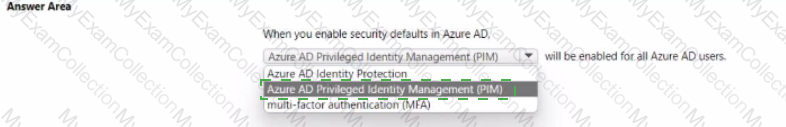
When security defaults are enabled for an Azure Active Directory (Azure AD) tenant, which two requirements are enforced? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
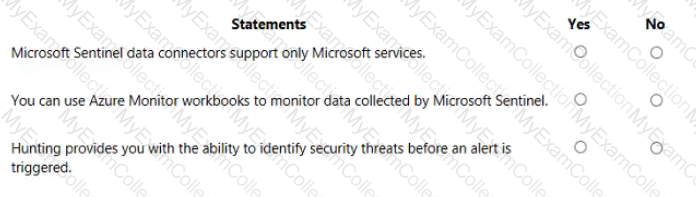
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point
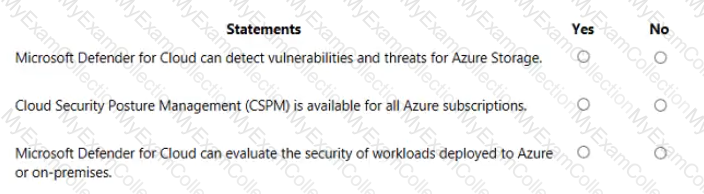
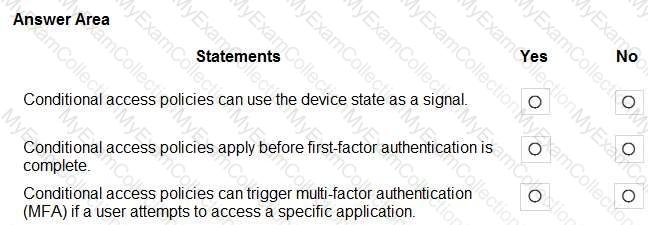
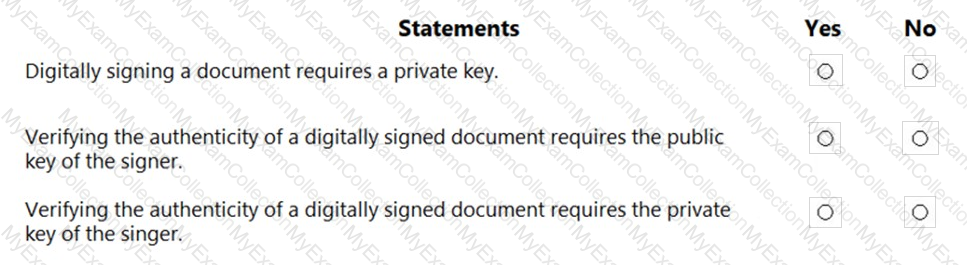
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Which three authentication methods can Microsoft Entra users use to reset their password? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
What is a use case for implementing information barrier policies in Microsoft 365?
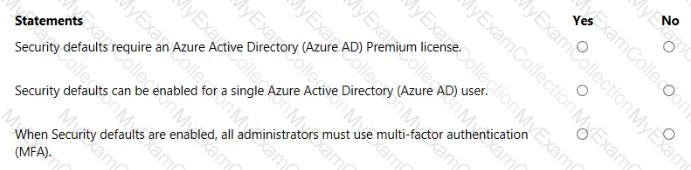
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
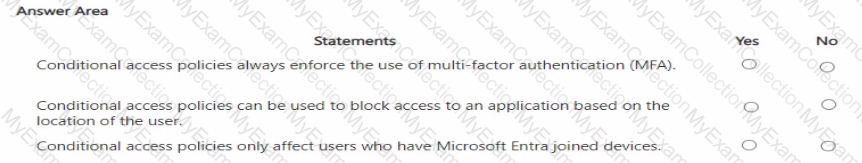
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

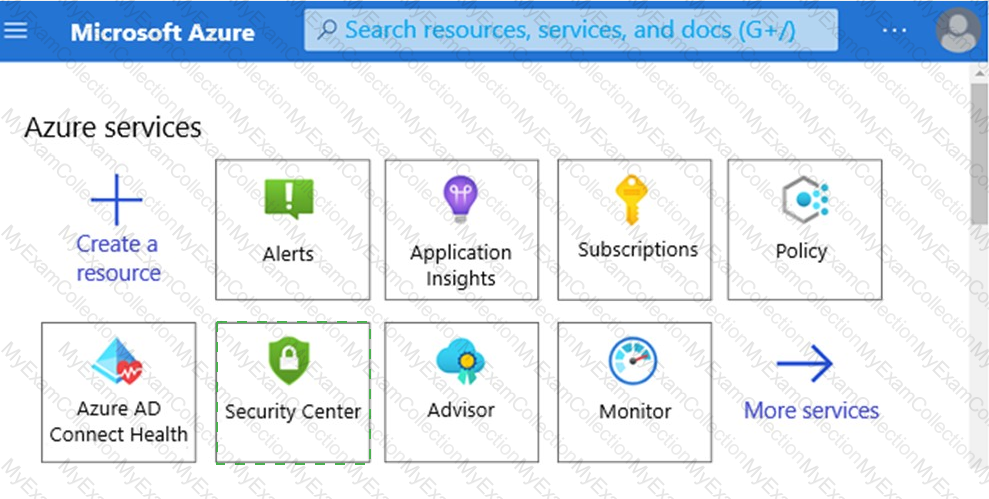
Which service should you use to view your Azure secure score? To answer, select the appropriate service in the answer area.