A Mule application includes a subflow containing a Scatter.Gather scope. Within each log of the Scatter.Gatter. an HTTP connector calls a PUT endpoint to modify records in different upstream system. The subflow is called inside an Unit successful scope to retry if a transitory exception is raised.
A technical spike is being performed to increase reliability of the Mule application.
Which steps should be performed within the Mule flow above the ensure idempontent behavior?
Mule application A is deployed to CloudHub and is using Object Store v2. Mute application B is also deployed to CloudHub.
Which approach can Mule application B use to remove values from Mule application A’S Object Store?
When registering a client application with an existing API instance or API Group instance, what is required to manually approve or reject request access?
Which statement is true when using XML SDK for creating custom message processors?
In a Mule project, Flow-1 contains a flow-ref to Flow-2 depends on data from Flow-1 to execute successfully.
Which action ensures the test suites and test cases written for Flow-1 and Flow-2 will execute successfully?
A Mule application contain two policies Policy A and Policy A has order1, and Policy B has order 2. Policy A Policy B, and a flow are defined by he configuration below.
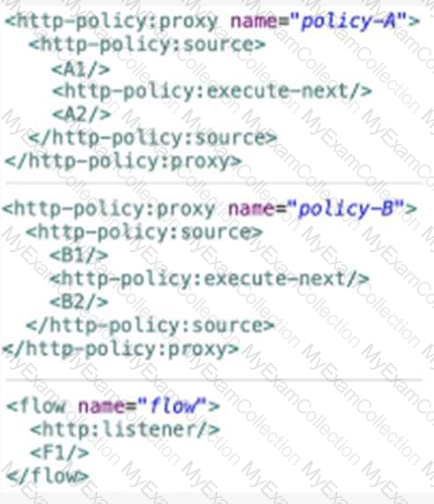
When a HTTP request arrives at the Mule application’s endpoint, what will be the execution order?
Which type of cache invalidation does the Cache scope support without having to write any additional code?
An API has been developed and deployed to CloudHub Among the policies applied to this API is an allowlist of IP addresses. A developer wants to run a test in Anypoint Studio and does not want any policies applied because their workstation is not included in the allowlist.
What must the developer do in order to run this test locally without the policies applied?
Refer to the exhibit.
What is the result of the Mule Maven Plugin configuration of the value of property its,keystorePassoword in CloudHub 2.0?

Which pattern can a web API use to notify its client of state changes as soon as they occur?
A custom policy needs to be developed to intercept all cutbound HTTP requests made by Mule applications.
Which XML element must be used to intercept outbound HTTP requests?
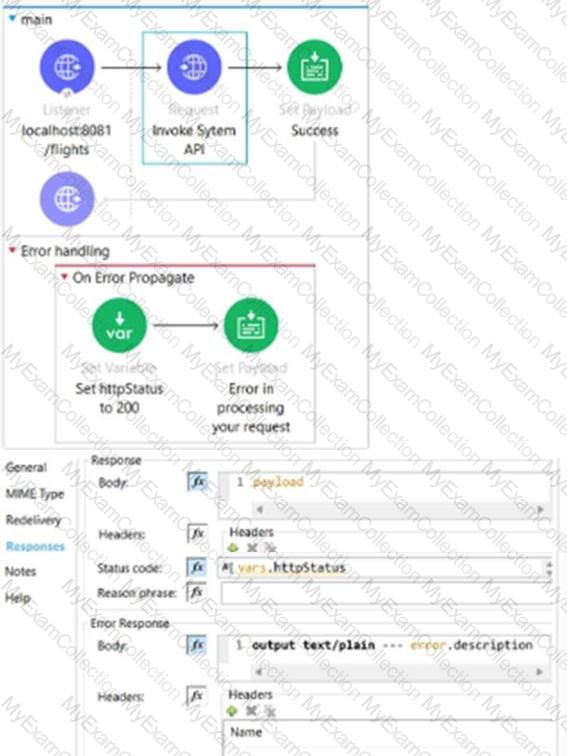
The HTTP Request operation raises an HTTP CONNECTIVITY error.
Which HTTP status code and body are returned to the web client?