Using the "normal" schedule, and assuming you are billing on the last day of the month for previous month and for appropriate partial months, how many invoices will you have for this project?
The addition of which of the following relationships would cause a logic loop?
Who will receive the most benefit from a master schedule of the Spring Highway project?
When resource leveling craft labor for a critical path schedule, the scheduler
The sum of all budgets for work scheduled to be accomplished within a given time period is the ____________.
Which letter of the alphabet best approximates the graphical shape of a project's cumulative cost baseline, or budgeted cost of work scheduled?
When reconstructing a CPM schedule electronically from a hardcopy, which of the following is NOT required to determine the critical path?
Using the normal schedule, given Activity 3001 and the relationship with Activity 4001. what is indicated?
Due to the delayed completion of Product Testing, the Release for Manufacture milestone was delayed by 5 workdays which thus delayed starting the Draft Product Manual activity. If the Print Product Manual activity is also delayed by 10 workdays, what is the delay to completing the Product Available milestone?
The expected remaining cost needed to complete an activity, group of activities or the project is the____________.
What is the actual duration as of the status date or data date of Activity B?
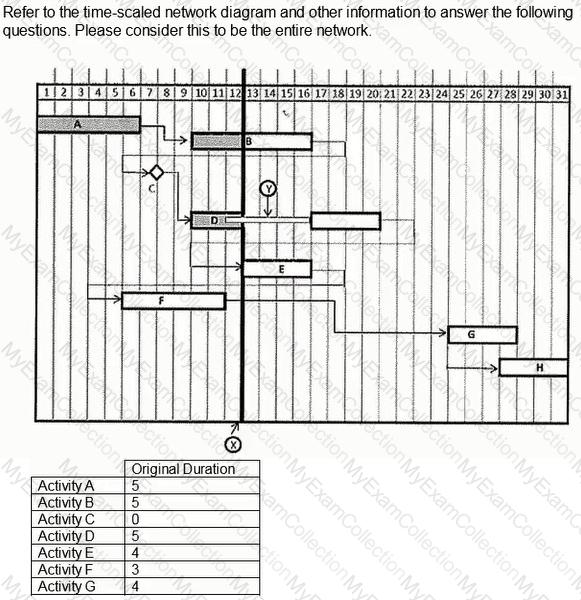
Using the normal schedule, theoretically construct a hammock for activities 6001-6003. What is the duration of the hammock?
Scenario: You are providing construction management services for a small office building project. Your duties include reviewing and approving the contractor's baseline schedule. The contractor has submitted the first baseline schedule for the project.
The contractor's baseline schedule submittal includes a bar chart, but no CPM diagram. Which of the following is the most significant shortcoming to using a bar chart to review the baseline?
Which of these letters, symbols or words best approximates the graphical shape of a project's cumulative BCWS?
What method offers the best chance of the schedule being used effectively to implement the project in the field?
You are developing a detailed critical path schedule for a proposed petrochemical plant. The schedule will become a part of the project baseline document, which will be sent to the company's board of directors for its consideration. What document or resource is likely to be MOST valuable in determining the schedule's work activity durations?
When using a detailed estimate as the basis for work package/activity durations, which element does NOT need to be identified before the activity durations can be calculated?
Under which circumstance should one perform resource-leveling calculations?
Scenario:
The entire network consists of the following activities and relationships. Activity A is twenty days long and is tied to Activity B, a ten-day activity, with a finish-to-finish tie with a lag value of five Activity B is tied to Activity C, a twenty-day activity, with a start-to-start relationship with a lag value of five.
PSP Activities Table
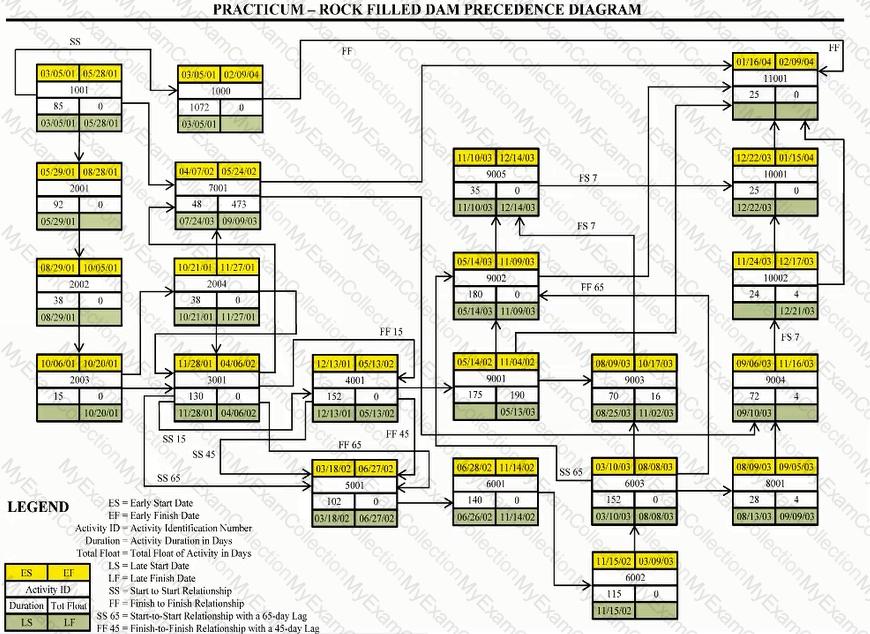
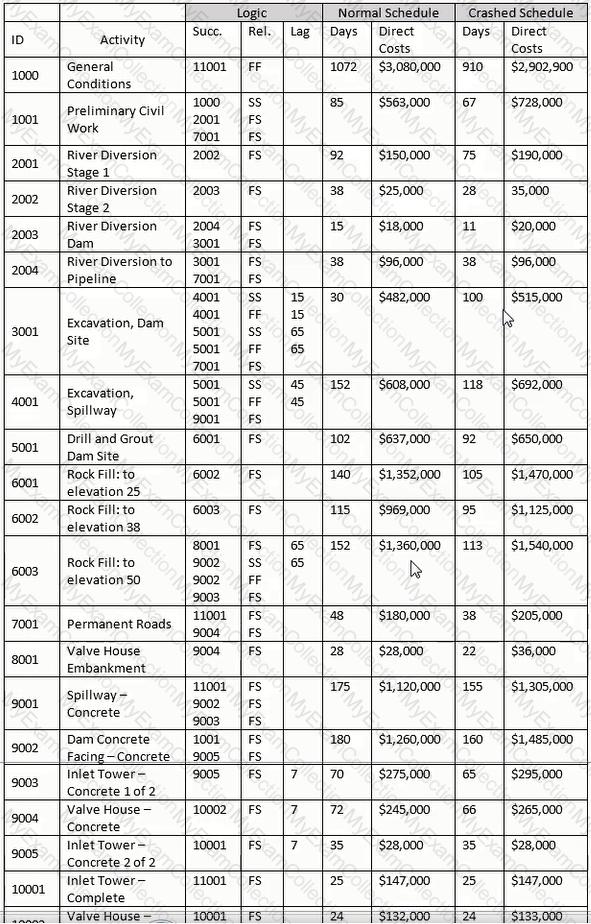
Scope Known about Rock-Filled Dam Project:
The dam requires river diversion and work over two or more rainy seasons. The contract is lump sum, competitively bid, and will be self-performed. The owner has attempted to shift all risk to the contractor by employing "no differing sit conditions" and "no damage for delay" clauses. There is a bonus/penalty provision of $2,500 per calendar day for early or late delivery. The early completion bonus is capped at $500,000, with no cap for late delivery penalty.
Liquidated damages end at the finish of demobilization. Indirect costs per calendar day are $2,800 for the "normal" schedule and $3,200 for the "crashed" schedule. The winter/wet weather season is 151 days between October 15 and March 25 of each year, reduces the efficiency of the contractor's operations by 20% and costs the contractor $10,000 per day. Assume a start date of March 5, 2001 and use a 7-day work week.
The following table lists work activities as planned by the contractor.

Theoretically construct a summary activity for only those activities with a finish-to-start relationship for Activities 8001 through 10001. Using the "normal" schedule, what is the cost of this hammock?
As the project plan is developed a mechanism is developed to communicate the projects organic structures that will facilitate reporting against the baseline schedule and cost estimate or budget Which of the following is NOT used for reporting?
Which is NOT an industry-recognized methodology for quantifying critical delay?
Scenario: You are providing construction management services for a small office building project. Your duties include reviewing and approving the contractor's baseline schedule. The contractor has submitted the first baseline schedule for the project.
The contractor subsequently submits a CPM schedule for its baseline schedule submittal. As part of your review, you look at the durations for each activity in the schedule. How do you determine if a duration of 10 work days for drywall installation is accurate?
Which of the following will NOT affect the total float calculation of a non-resource leveled schedule?
In analyzing a logical chain of activities in a critical path method (CPM) schedule, what do differing total float values within that chain typically indicate?
Activity 1001 started on the scheduled date but has slipped 10 days. Activity 10002 will slip 35 days. All remaining activities retain their original duration. What is the revised completion date?
In its simplest form, what is the main drawback of critical path method scheduling?
The Scope of Work divides the major deliverables into smaller more manageable components for all of the following EXCEPT to:
By subtracting a measured unit productivity rate during an impacted period from the unit productivity rate during an unimpacted period, the resulting value represents:
Which of the following options is NOT a feasible method to reduce the overall completion time of the toll road program?
Which of the following procedures is generally recognized as acceptable when updating a schedule?
Determine the correct formula and date for the late finish for Activity 2001.
Which of the following is NOT a tool or technique used to perform scope planning?
Based on the available scope information and required accuracy, different cost estimated models or methodologies are utilized Which of the following statements is NOT true?
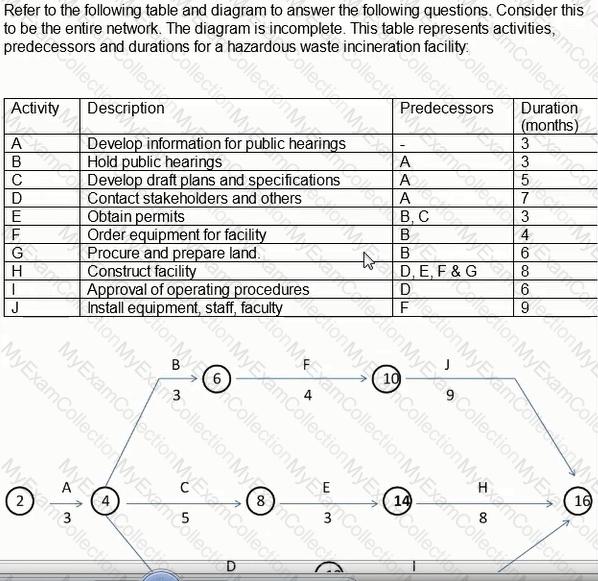
If Activity E's duration changes to 4 months, what is the overall duration of the project.
In order for a claimant to be entitled to an extension of contract time for a delay event (and further to be considered compensable):
Considering the information provided for the project, what is the factor that most influences the successful crashing of the schedule?
Determine the correct formula and date for the late finish for Activity 2002.

Using one crane capable of 30 lifts per day. for 3 column pours requiring 28 lifts each, plus assorted work in the area requiring an additional 150 lifts, what are the lowest planned workdays for this work?
The schedule or budget at completion less the estimate at completion is___________.
Which of the following risks CANNOT be estimated by BILCO with only a resource-loaded schedule?





