What configuration on AWS is required in order for VM-Series to forward traffic between its network interfaces?
What is the Palo Alto Networks recommended setting for the Prisma Cloud Training Model Threshold?
Prevention against which type of attack is configurable in Web-Application and API Security (WAAS)?
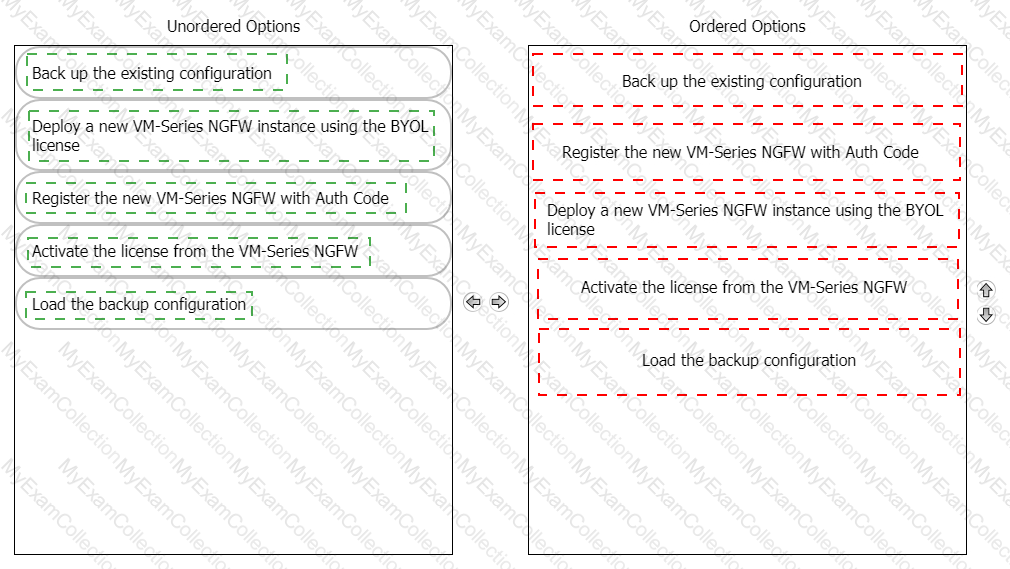
A customer has deployed a VM-Series NGFW on Amazon Web Services using a PAYG license. What is the sequence required by the customer to switch to a BYOL license?
Which type of Resource Query Language (RQL) query is used to create a custom policy that looks for untagged resources?
Which two items are required when a VM-100 BYOL instance is upgraded to a VM-300 BYOL instance? (Choose two.)
What are two ways to enable interface swap when deploying a VM-Series NGFW in Google Cloud Platform? (Choose two.)
The customer has an Amazon Web Services Elastic Computing Cloud that provides a service to the internet directly and needs to secure that cloud with a VM-Series NGFW.
Which component handles address translation?
How can all alerts related to "Amazon RDS" be quickly identified within the Prisma Cloud dashboard?
Amazon Web Services WAF can be enabled on which two resources?(Choose two.)
An image containing medium vulnerabilities that do not have available fixes is being deployed into the sock-shop namespace. Prisma Cloud has been configured for vulnerability management within the organization's continuous integration (CI) tool and registry.
What will occur during the attempt to deploy this image from the CI tool into the sock-shop namespace?
How does a customer that has deployed a VM-Series NGFW on Microsoft Azure using a BYOL license change to a PAYG license structure?
Which two resource types are included in the Prisma Cloud Enterprise licensing count? (Choose two.)
What are two benefits of Cloud Security Posture Management (CSPM) over other solutions? (Choose two.)
Which statement explains the correlation between the block and alert thresholds in a vulnerability management policy?
Which RQL query should be used to quickly identify any events related to an organization's Google Cloud Platform Big Query database the last 24 hours?
Which regulatory framework in Prisma Cloud measures compliance with European Union (EU) data privacy regulations in Amazon Web services (AWS) workloads?
What happens in Prisma Cloud after Training Model Threshold or Alert Disposition is changed?
A customer CSO has asked you to demonstrate how to identify all "Amazon RDS" resources deployed and the region that they are deployed in. What are two ways that Prisma Public Cloud can show the relevant information?(Choose two.)
What are the two options to dynamically register tags used by Dynamic Address Groups that are referenced in policy? (Choose two.)
The following error is received when performing a manual twistcli scan on an image:
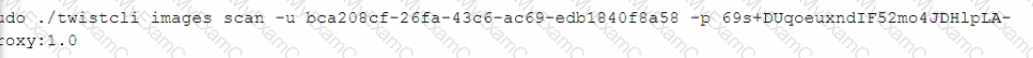
What is missing from the command?
Which two types of Resource Query Language (RQL) queries can be used to create policies? (Choose two.)
Which three services can Google Cloud Security Scanner assess? (Choose three.)