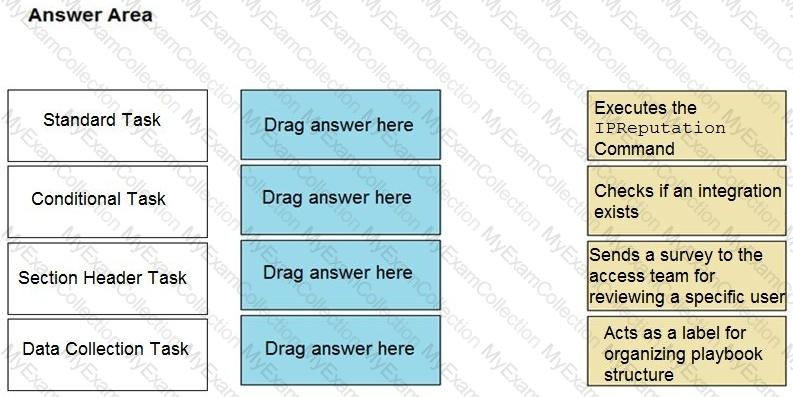
Which of the following is a prerequisite to editing out-of-the-box (OOTB) content?
Newly created subplaybooks do not have any inputs, or outputs. What is necessary to make them functional? (Choose two.)
Which of the following are valid methods to contribute custom content? (Choose three.)
Which two situations would an engineer consider when configuring classification and mapping for an incident type? (Choose two.)
When browsing the Marketplace for new content packs, which details about each pack are you able to view?
What is the most effective way to correlate multiple raw events coming from a SIEM and link them together?
What is used to trigger playbooks automatically based on the classification of an incident?
Which of the following does a XSOAR Admin need to create an integration with a third party cloud application?
Incidents need to be filtered by all of the following criteria:
1.Status – Pending
2.Exclude Category – Job
3.Severity – High
4.Owner – None (No owner assigned)
5.Type – Phishing
6.Email Subject – “You have won a million dollarsâ€
What is the correct query syntax for the above incident search filter?
An engineer’s organization system is registered in the following manner:
What is the most efficient way for the engineer to achieve this?
Which XSOAR architecture would be recommended for Managed Security Service Providers (MSSP)?
For troubleshooting, after a log bundle is created, where do the logs appear on the XCSOAR server?
Which of the following is a basic setting that can be configured in an automation?