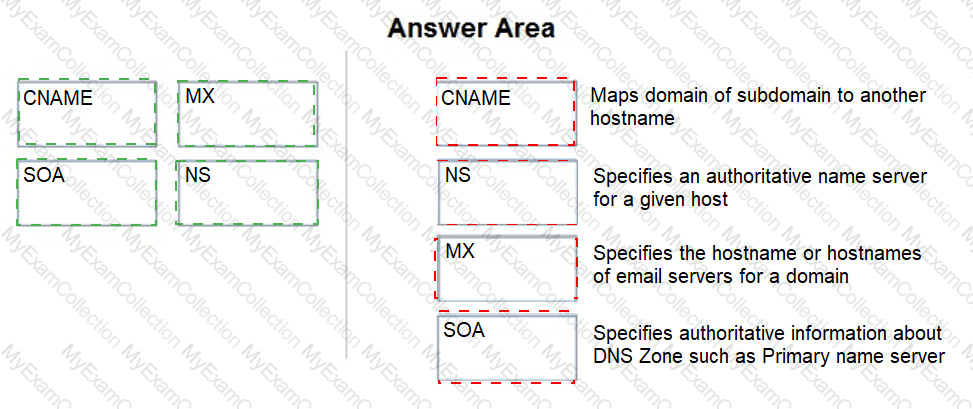
Which action must Secunty Operations take when dealing with a known attack?
Which type of IDS/IPS uses a baseline of normal network activity to identify unusual patterns or levels of network activity that may be indicative of an intrusion attempt?
Routing Information Protocol (RIP), uses what metric to determine how network traffic should flow?
Which product from Palo Alto Networks enables organizations to prevent successful cyberattacks as well as simplify and strengthen security processes?
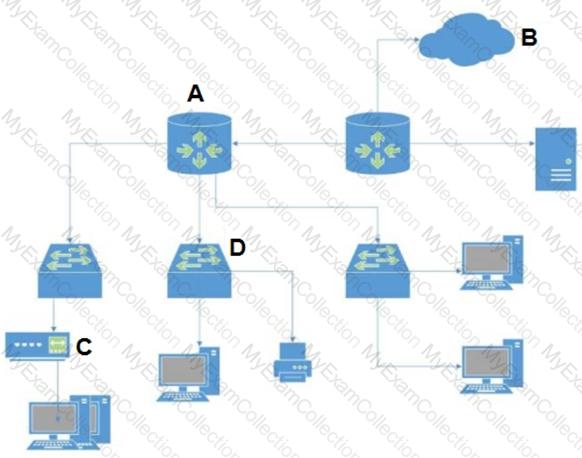
If an endpoint does not know how to reach its destination, what path will it take to get there?
An Administrator wants to maximize the use of a network address. The network is 192.168.6.0/24 and there are three subnets that need to be created that can not overlap. Which subnet would you use for the network with 120 hosts?
Requirements for the three subnets: Subnet 1: 3 host addresses
Subnet 2: 25 host addresses
Subnet 3: 120 host addresses
With regard to cloud-native security in layers, what is the correct order of the four C's from the top (surface) layer to the bottom (base) layer?
Which three layers of the OSI model correspond to the Application Layer (L4) of the TCP/IP model?
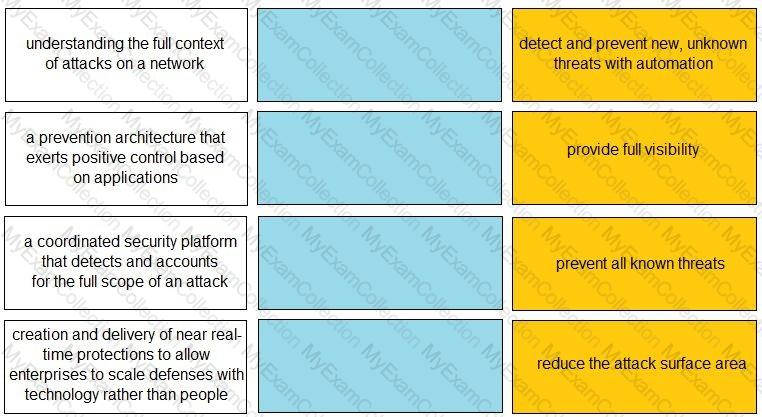
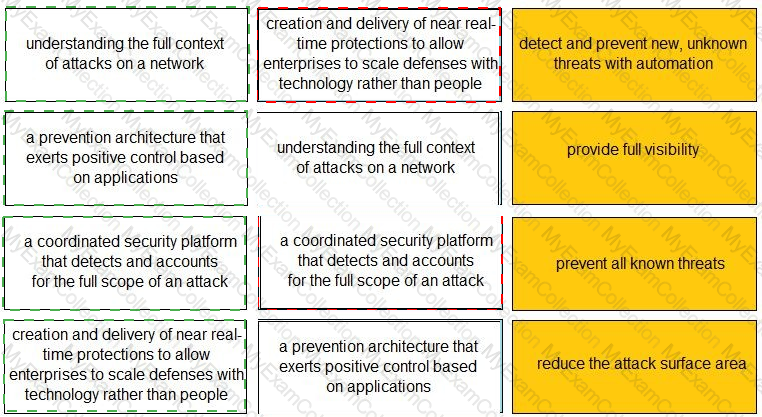
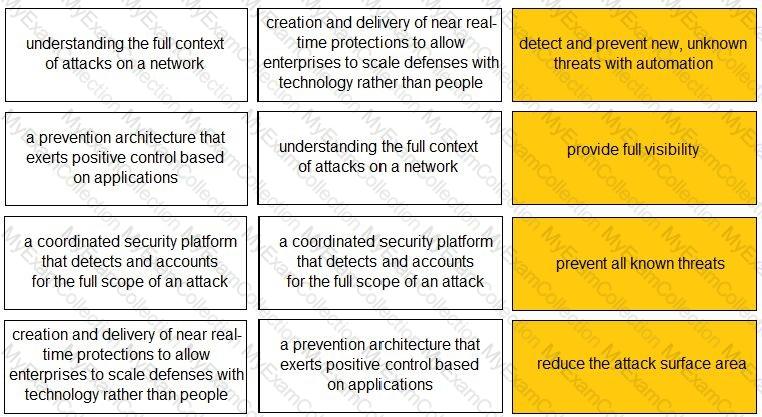
What are three benefits of the cloud native security platform? (Choose three.)
Which native Windows application can be used to inspect actions taken at a specific time?
Which pillar of Prisma Cloud application security does vulnerability management fall under?
Which Palo Alto Networks product provides playbooks with 300+ multivendor integrations that help solve any security use case?
Which method is used to exploit vulnerabilities, services, and applications?
What is the recommended method for collecting security logs from multiple endpoints?
Which type of Software as a Service (SaaS) application provides business benefits, is fast to deploy, requires minimal cost and is infinitely scalable?
In an IDS/IPS, which type of alarm occurs when legitimate traffic is improperly identified as malicious traffic?
Which Palo Alto subscription service identifies unknown malware, zero-day exploits, and advanced persistent threats (APTs) through static and dynamic analysis in a scalable, virtual environment?
Which analysis detonates previously unknown submissions in a custom-built, evasion-resistant virtual environment to determine real-world effects and behavior?
Which type of malware replicates itself to spread rapidly through a computer network?
During the OSI layer 3 step of the encapsulation process, what is the Protocol Data Unit (PDU) called when the IP stack adds source (sender) and destination (receiver) IP addresses?
SecOps consists of interfaces, visibility, technology, and which other three elements? (Choose three.)
What should a security operations engineer do if they are presented with an encoded string during an incident investigation?
Which internet of things (loT) connectivity technology operates on the 2.4GHz and 5GHz bands, as well as all bands between 1 and 6GHz when they become available for 802.11 use. at ranges up to 11 Gbit/s?
In which situation would a dynamic routing protocol be the quickest way to configure routes on a router?
Which feature of the VM-Series firewalls allows them to fully integrate into the DevOps workflows and CI/CD pipelines without slowing the pace of business?
Anthem server breaches disclosed Personally Identifiable Information (PII) from a number of its servers. The infiltration by hackers was attributed to which type of vulnerability?
Based on how much is managed by the vendor, where can CaaS be situated in the spread of cloud computing services?