HTML5 Gateway can be installed on which supported UNIX OS versions? (Choose two.)
Which file must you edit to ensure the PSM for SSH server is not hardened automatically after installation?
What is a valid combination of primary and secondary layers of authentication to a company's two-factor authentication policy?
What is a prerequisite step before CyberArk can be configured to support RADIUS authentication?
A customer has five PVWA servers. Three are located at the primary data center and the remaining two are at a satellite data center.
What is important to consider about the load balancer? (Choose two.)
Which of the following are supported authentication methods for CyberArk? Check all that apply
When integrating a Vault with HSM, which file is uploaded to the HSM device?
Which parameter must be identical for both the Identity Provider (IdP) and the PVWA?
When performing “In Domain†hardening of a PSM server, which steps must be performed? (Choose two.)
You are installing the HTML5 gateway on a Linux host using the RPM provided.
After installing the Tomcat webapp, what is the next step in the installation process?
Which component should be installed on the Vault if Distributed Vaults are used with PSM?
CyberArk User Neil is trying to connect to the Target Linux server 192.168.1.164 using a domain account ACME/linuxuser01 on domain acme.corp using PSM for SSH server 192.168.65.145.
What is the correct syntax?
In a SIEM integration it is possible to use the fully-qualified domain name (FQDN) when specifying the SIEM server address(es)
What authentication methods can be implemented to enforce Two-Factor Authentication (2FA) for users authenticating to CyberArk using both the PVWA (through the browser) and the PrivateArk Client?
When a DR vault server becomes an active vault, it will automatically fail back to the original state once the primary vault comes back online.
A customer asked you to help scope the company's PSM deployment.
What should be included in the scoping conversation?
As a member of a PAM Level-2 support team, you are troubleshooting an issue related to load balancing four PVWA servers at two data centers. You received a note from your Level-1 support team stating “When testing PVWA website from a workstation, we noticed that the “Source IP of last sign-in†was shown as the VIP (Virtual IP address) assigned to the four PVWA servers instead of the workstation IP where the PVWA site was launched from.â€
Which step should you take?
You want to change the name of the PVWAappuser of the second PVWA server.
Which steps are part of the process? (Choose two.)
-
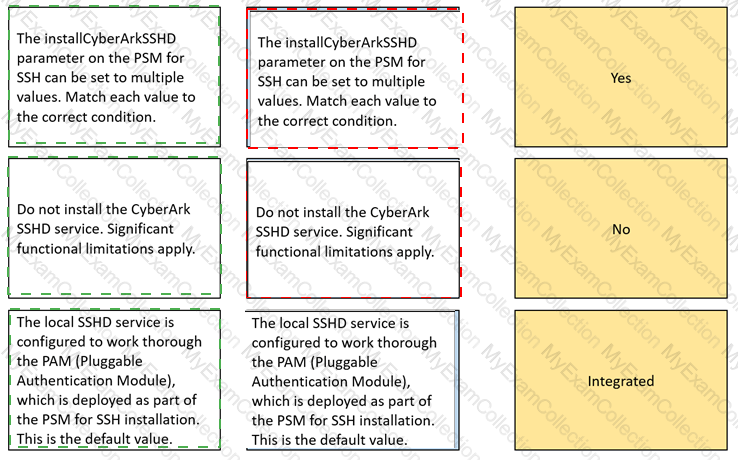
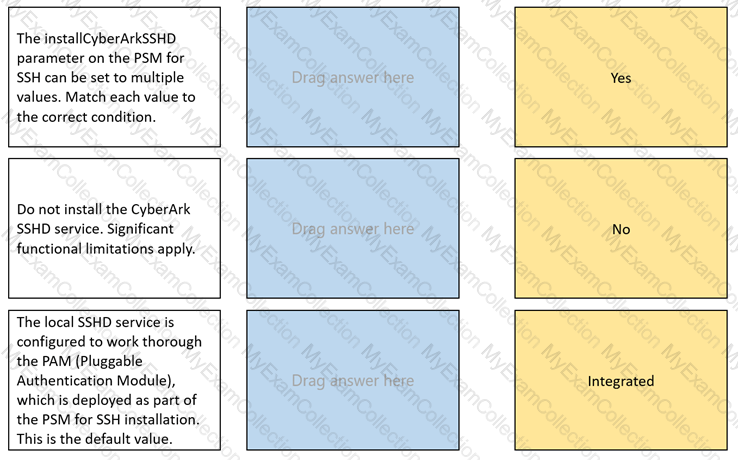
The installCyberArkSSHD parameter on the PSM for SSH can be set to multiple values.
Match each value to the correct condition.
Which statement is correct about CPM behavior in a distributed Vault environment?
You are installing multiple PVWAs behind a load balancer.
Which statement is correct?
The PrivateArk clients allows a user to view the contents of the vault like a filesystem.
The account used to install a PVWA must have ownership of which safes? (Choose two.)
In addition to bit rate and estimated total duration of recordings per day, what is needed to determine the amount of storage required for PSM recordings?
What are the operating system prerequisites for installing CPM? Select all that apply.
You need to add a new PSM server to an existing CyberArk environment.
What is the best way to determine the sizing of this server?
Which utility should be used to register the Vault in Amazon Web Services?
If a customer has one data center and requires fault tolerance, how many PVWAs should be deployed?
In order to avoid conflicts with the hardening process, third party applications like Antivirus and Backup Agents should be installed on the Vault server before installing the Vault.
You are designing the number of PVWAs a customer must deploy. The customer has three data centers with a distributed Vault in each, requires high availability, and wants to use all Vaults at all times.
How many PVWAs does the customer need?