You want to provision users and groups to a Netskope tenant. You have Microsoft Active Directory servers hosted in two different forests. Which statement is true about this scenario?
You want to provide malware protection for all cloud storage applications.
In this scenario, which action would accomplish this task?
Review the exhibit.
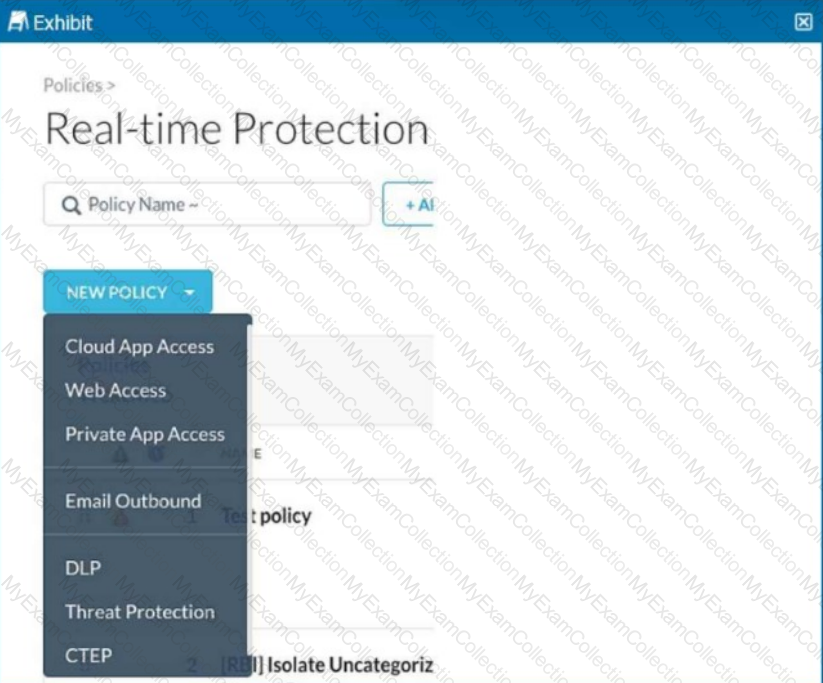
You are asked to create a new Real-time Protection policy to scan SMTP emails using data loss prevention (DLP) for personal health information (PHI). The scope is limited to only emails being sent from Microsoft Exchange Online to outside recipients.
You want to reduce false positives by only triggering policies when contents of your customer database are uploaded to Dropbox. Your maximum database size is 2 MB. In this scenario, what are two ways to accomplish this task? (Choose two.)
You want to allow both the user identities and groups to be imported in the Netskope platform. Which two methods would satisfy this requirement? (Choose two.)
Your small company of 10 people wants to deploy the Netskope client to all company users without requiring users to be imported using Active Directory, LDAP, or an IdP.
Your company asks you to use Netskope to integrate with Endpoint Detection and Response (EDR) vendors such as CrowdStrike. In this scenario, what is a requirement for a successful Integration and sharing of threat data?
You are given an MD5 hash of a file suspected to be malware by your security incident response team. They ask you to offer insight into who has encountered this file and from where was the threat initiated. In which two Skope IT events tables would you search to find the answers to these questions? (Choose two.)
You want to prevent a document stored in Google Drive from being shared externally with a public link. What would you configure in Netskope to satisfy this requirement?
Your company asks you to use Netskope to integrate with Endpoint Detection and Response (EDR) vendors such as Crowdstrike.
Which two requirements are needed for a successful integration and sharing of threat data? (Choose two.)
Your team is asked to investigate ten Netskope DLP incidents. You want to assign these incidents among different team members.
To which three event types does Netskope's REST API v2 provide access? (Choose three.)
Your customer implements Netskope Secure Web Gateway to secure all Web traffic. While they have created policies to block certain categories, there are many new sites available dally that are not yet categorized. The customer's users need quick access and cannot wait to put in a request to gain access requiring a policy change or have the site's category changed.
To solve this problem, which Netskope feature would provide quick, safe access to these types of sites?
Your company wants to deploy Netskope using a tunnel because you have a mixture of device operating systems. You also do not want to enable encryption because you want to maximize bandwidth.
Your learn is asked to Investigate which of the Netskope DLP policies are creating the most incidents. In this scenario, which two statements are true? (Choose two.)
Review the exhibit.
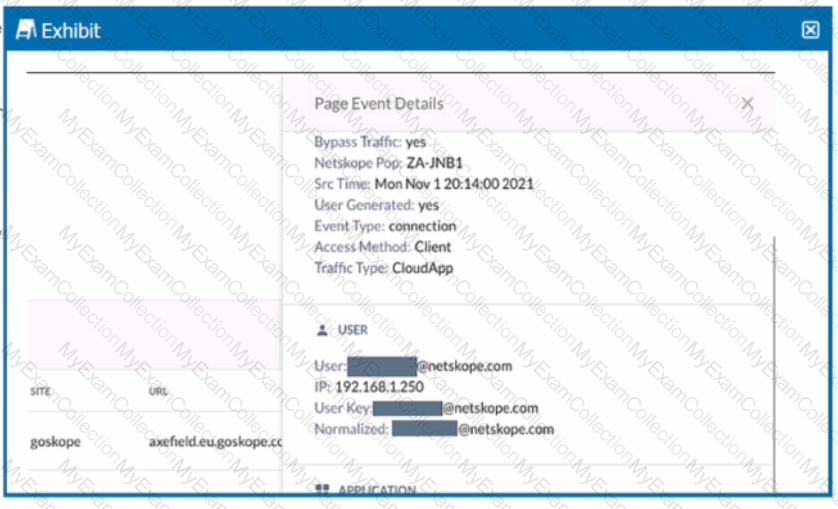
You are asked to restrict users from accessing YouTube content tagged as Sport. You created the required real-time policy; however, users can still access the content
Referring to the exhibit, what is the problem?
Your customer has some managed Windows-based endpoints where they cannot add any clients or agents. For their users to have secure access to their SaaS application, you suggest that the customer use Netskope's Explicit Proxy.
Which two configurations are supported for this use case? (Choose two.)
You are asked to grant access for a group of users to an application using NPA. So far, you have created and deployed the publisher and created a private application using the Netskope console.
Which two steps must also be completed to enable your users access to the application? (Choose two.)
Your company has many users that are remote and travel often. You want to provide the greatest visibility into their activities, even while traveling. Using Netskope. which deployment method would be used in this scenario?
A customer wants to deploy the Netskope client on all their employee laptops to protect all Web traffic when users are working from home. However, users are required to work from their local offices at least one day per week. Management requests that users returning to the office be able to transparently leverage the local security stack without any user intervention.
Which two statements are correct in this scenario? (Choose two.)
You created the Netskope application in your IdP for user provisioning and validated that the API Integration settings are correct and functional. However, you are not able to push the user groups from the IdP into your Netskope tenant.
A company allows their users to access OneDrive on their managed laptops. It is against corporate policy to upload any documents to their personal OneDrive. The company needs to enforce this policy to protect their customer’s sensitive data.
What are two ways to enforce this policy? (Choose two.)

