A company is attempting to steer traffic to Netskope using GRE tunnels. They notice that after the initial configuration, users cannot access external websites from their browsers.
What are three probable causes for this issue? (Choose three.)
Which two cloud security and infrastructure enablement technologies does Secure Access Service Edge (SASE) combine into its unified platform? (Choose two.)
A customer changes CCI scoring from the default objective score to another score. In this scenario, what would be a valid reason for making this change?
How does a cloud security solution achieve visibility into TLS/SSL-protected Web traffic?
You just deployed the Netskope client in Web mode and several users mention that their messenger application is no longer working. Although you have a specific real-time policy that allows this application, upon further investigation you discover that it is using proprietary encryption. You need to permit access to all the users and maintain some visibility.
In this scenario, which configuration change would accomplish this task?
You want to take into account some recent adjustments to CCI scoring that were made in your Netskope tenant.
In this scenario, which two CCI attributes in the Ul would be used in a Real-time Protection policy? (Choose two.)
You investigate a suspected malware incident and confirm that it was a false alarm.
You want to see the actual data that caused the policy violation within a DLP Incident view.
In this scenario, which profile must be set up?
Click the Exhibit button.
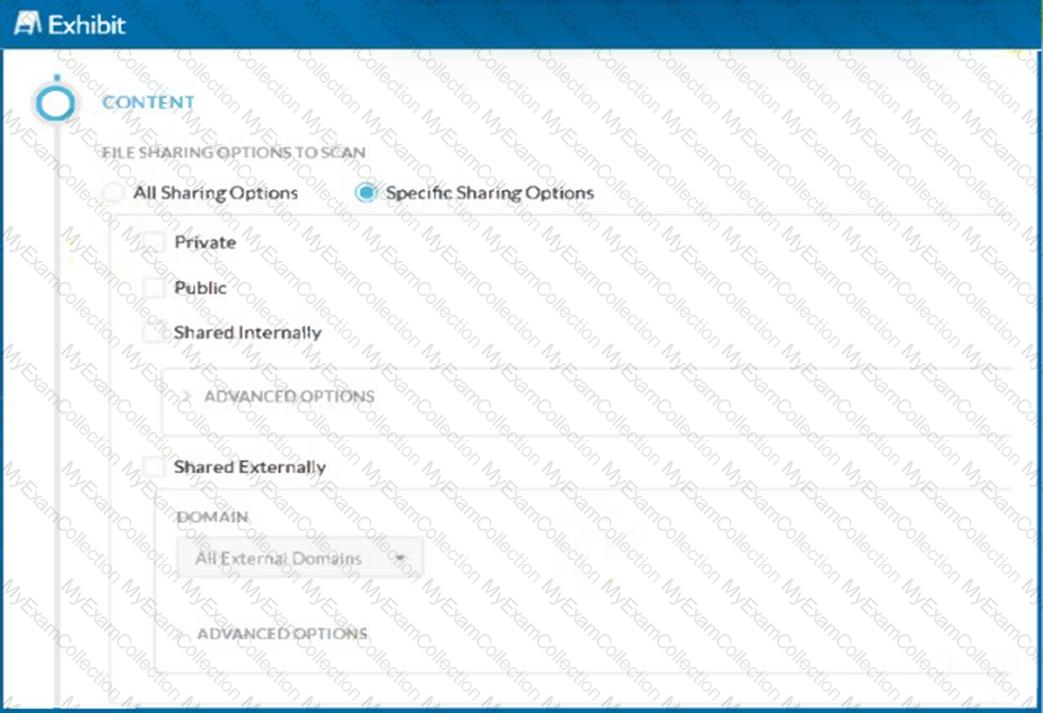
A customer has created a CASB API-enabled Protection policy to detect files containing sensitive data that are shared outside of their organization.
Referring to the exhibit, which statement is correct?
How do you provision users to your customer's Netskope tenant? (Choose two.)
What are two uses for deploying a Netskope Virtual Appliance? (Choose two.)
A new customer is concerned about performance, especially with respect to Microsoft 365. They have offices in 20 countries around the world and their workforce is mostly mobile.
In this scenario, which two statements about NewEdge would align with the customer's requirements? (Choose two.)
What are two primary advantages of Netskope's Secure Access Service Edge (SASE) architecture? (Choose two.
When comparing data in motion with data at rest, which statement is correct?
Your company started deploying the latest version of the Netskope Client and you want to track the progress and device count using Netskope.
Which two statements are correct in this scenario? (Choose two.)
When using an out-of-band API connection with your sanctioned cloud service, what are two capabilities available to the administrator? (Choose two.)
You need to create a service request ticket for a client-related issue using the Netskope client Ul. In this scenario, you generate the client logs by right-clicking on the system tray icon and choosing
Click the Exhibit button.
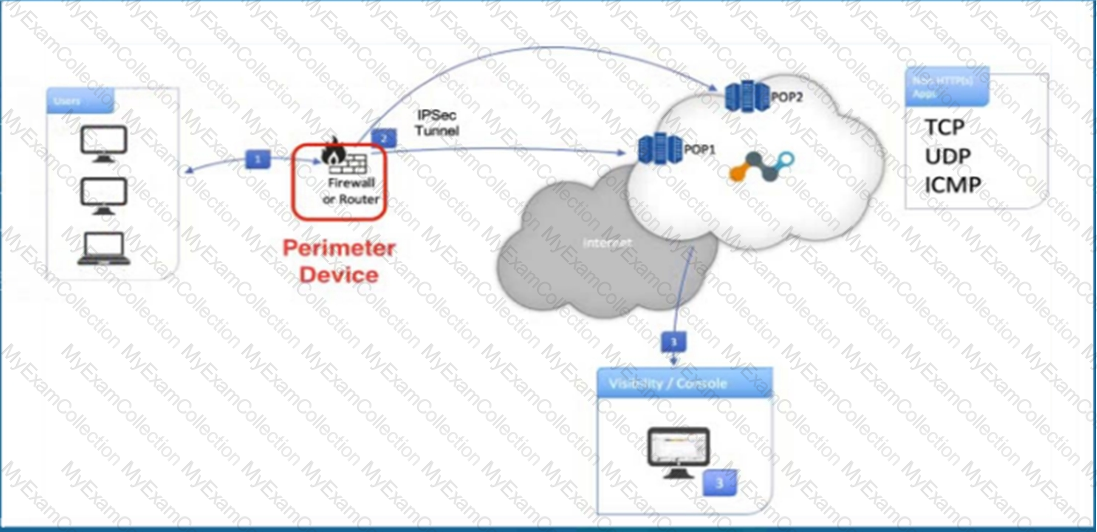
Referring to the exhibit, what are two recommended steps to be set on the perimeter device to monitor IPsec tunnels to a Netskope data plane? (Choose two.)
Which Netskope component would an administrator use to see an overview of private application usage and performance?
You want to prevent Man-in-the-Middle (MITM) attacks on an encrypted website or application. In this scenario, which method would you use?
Which two statements are correct about DLP Incidents in the Netskope platform? (Choose two.)
What information is displayed in an application's Cloud Confidence Index (CCI) page? (Choose two.)
A company user cannot open a sports news site. You want to review the category of the website and see how the rules are applied even though this category is allowed. In this scenario, which action will accomplish this task?
There is a DLP violation on a file in your sanctioned Google Drive instance. The file is in a deleted state. You need to locate information pertaining to this DLP violation using Netskope. In this scenario, which statement is correct?
Which three status indicators does the NPA Troubleshooter Tool provide when run? (Choose three)
Click the Exhibit button.
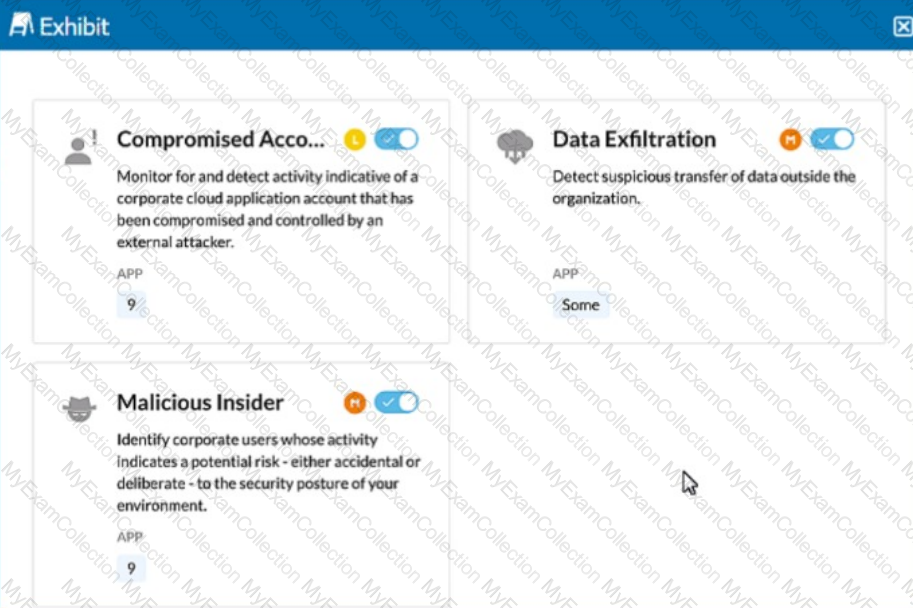
The exhibit shows security rules that are part of which component of the Netskope platform?
Which two capabilities are part of Netskope's Adaptive Zero Trust Data Protection? (Choose two.)
Users are connecting to sanctioned cloud applications from public computers, such as from a hotel business center.
Which traffic steering method would work in this scenario?
You are asked to review files affected by malware in your organization. In this scenario, which two actions are possible and would be accessible from the Netskope UI -> Incidents --> Malware? (Choose two)
Click the Exhibit button.
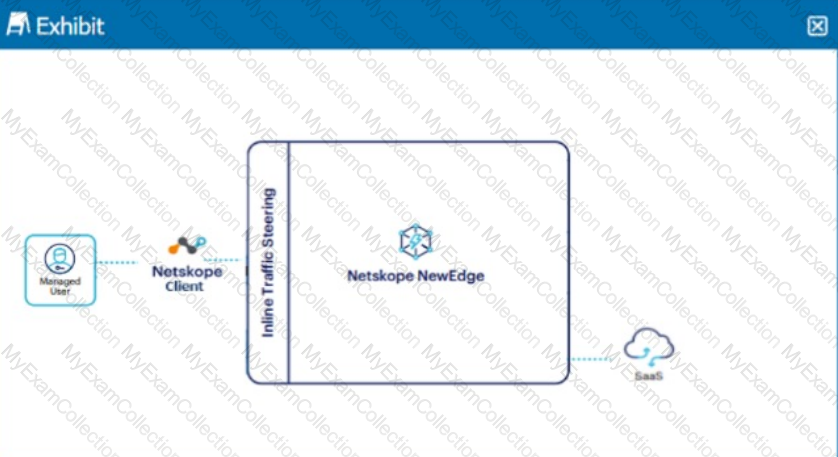
A user is connected to a SaaS application through Netskope's Next Gen SWG with SSL inspection enabled. In this scenario, what information is available in SkopeIT? (Choose three.)
You are working with a large retail chain and have concerns about their customer data. You want to protect customer credit card data so that it is never exposed in transit or at rest. In this scenario, which regulatory compliance standard should be used to govern this data?
An administrator wants to determine to which data plane a user is traversing. In this scenario, what are two ways to accomplish this task? (Choose two.)

