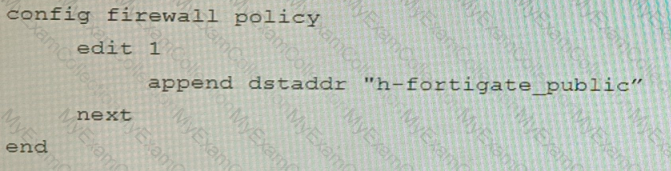
Refer to the exhibit.

A customer is trying to setup a Playbook automation using a FortiAnalyzer, FortiWeb and FortiGate. The intention is to have the FortiGate quarantine any source of SQL Injection detected by the FortiWeb. They got the automation stitch to trigger on the FortiGate when simulating an attack to their website, but the quarantine object was created with the IP 0.0.0.0. Referring to the configuration and logs in the exhibits, which two statements are true? (Choose two.)
Refer to the exhibit.
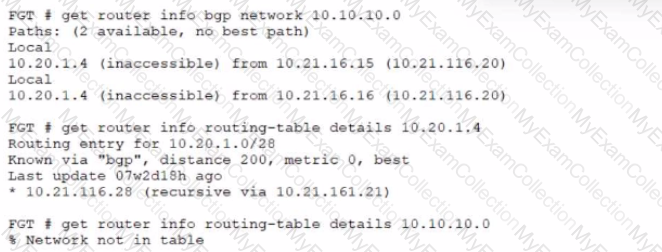
A customer reports that they are not able to reach subnet 10.10.10.0/24 from their FortiGate device.
Based on the exhibit, what should you do to correct the situation?
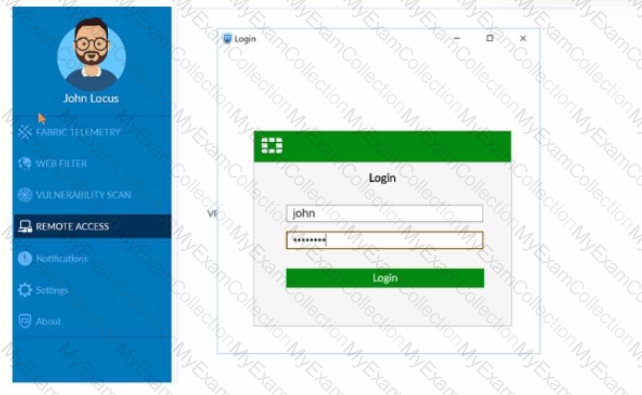
Refer to the exhibit containing the configuration snippets from the FortiGate. Customer requirements:

• SSLVPN Portal must be accessible on standard HTTPS port (TCP/443)
• Public IP address (129.11.1.100) is assigned to portl
• Datacenter.acmecorp.com resolves to the public IP address assigned to portl
The customer has a Let's Encrypt certificate that is going to expire soon and it reports that subsequent attempts to renew that certificate are failing.
Reviewing the requirement and the exhibit, which configuration change below will resolve this issue?
A)
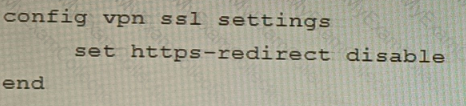
B)
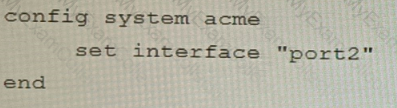
C)
D)
You have configured a Site-to-Site IPsec VPN tunnel between a FortiGate and a third-party device but notice that one of the error counters on the tunnel interface keeps increasing.

Which two configuration options can resolve this problem? (Choose two.)
A customer has FortiAP devices in three branch offices managed from a FortiGate in the HQ. Each FortiAP is connected to a dedicated management VLAN.
The customer wants the users connected to the FortiAP SSIDs to use the branch local internet connection, but each branch uses a different VLAN ID for the bridge. HQ users travel to different branches and connect to the same SSID.
Which configuration option will solve this requirement?
A customer is operating a FortiWeb cluster in a high volume active-active HA group consisting of eight FortiWeb appliances. One of the secondary members is handling traffic for one specific VIP.
What will happen with the traffic if that secondary FortiWeb appliance fails?
Refer to The exhibit showing a FortiEDR configuration.
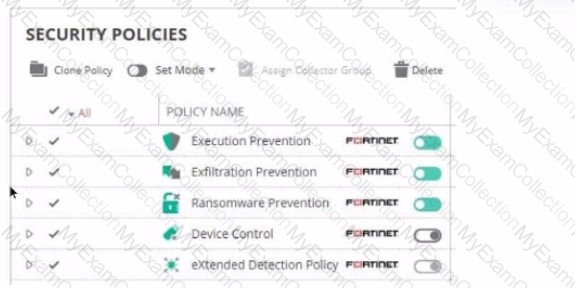
Based on the exhibit, which statement is correct?
Refer to the exhibit.
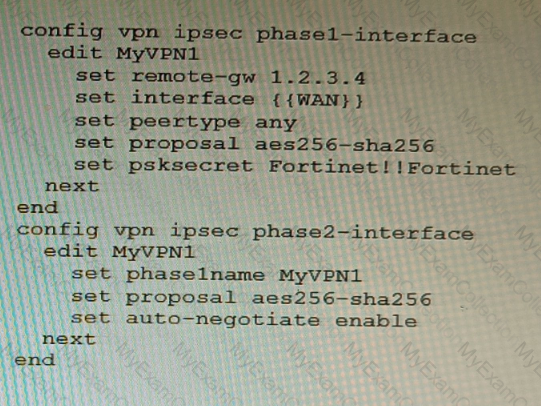
FortiManager is configured with the Jinja Script under CLI Templates shown in the exhibit.
Which two statements correctly describe the expected behavior when running this template? (Choose two.)
A FortiGate is configured to perform outbound firewall authentication with Azure AD as a SAML IdP.
What are two valid interactions that occur when the client attempts to access the internet? (Choose two.)
You must configure an environment with dual-homed servers connected to a pair of FortiSwitch units using an MCLAG.
Multicast traffic is expected in this environment, and you should ensure unnecessary traffic is pruned from links that do not have a multicast listener.
In which two ways must you configure the igmps-f lood-traffic and igmps-flood-report settings? (Choose two.)
An administrator has configured a FortiGate device to authenticate SSL VPN users using digital certificates. A FortiAuthenticator is the certificate authority (CA) and the OCSP server.
Part of the FortiGate configuration is shown below:
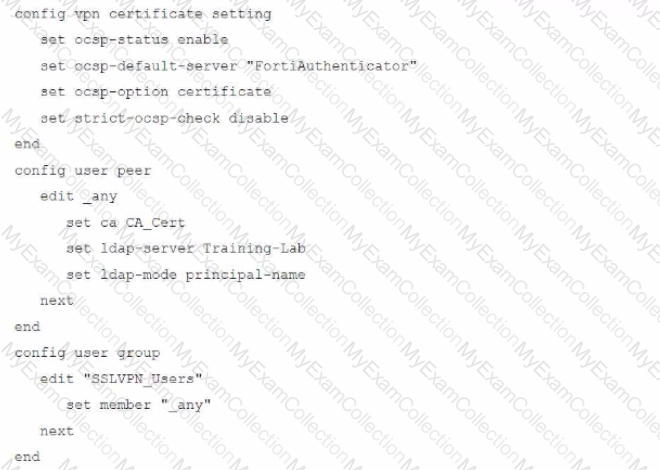
Based on this configuration, which authentication scenario will FortiGate deny?
Which feature must you enable on the BGP neighbors to accomplish this goal?
A Hub FortiGate is connecting multiple branch FortiGate devices separating the traffic centrally in unique VRFs. Routing information is exchanged using BGP between the Hub and the Branch FortiGate devices.
You want to efficiently enable route leaking of specific routes between the VRFs.
Which two steps are required to achieve this requirement? (Choose two.)
Refer to the exhibit that shows VPN debugging output.
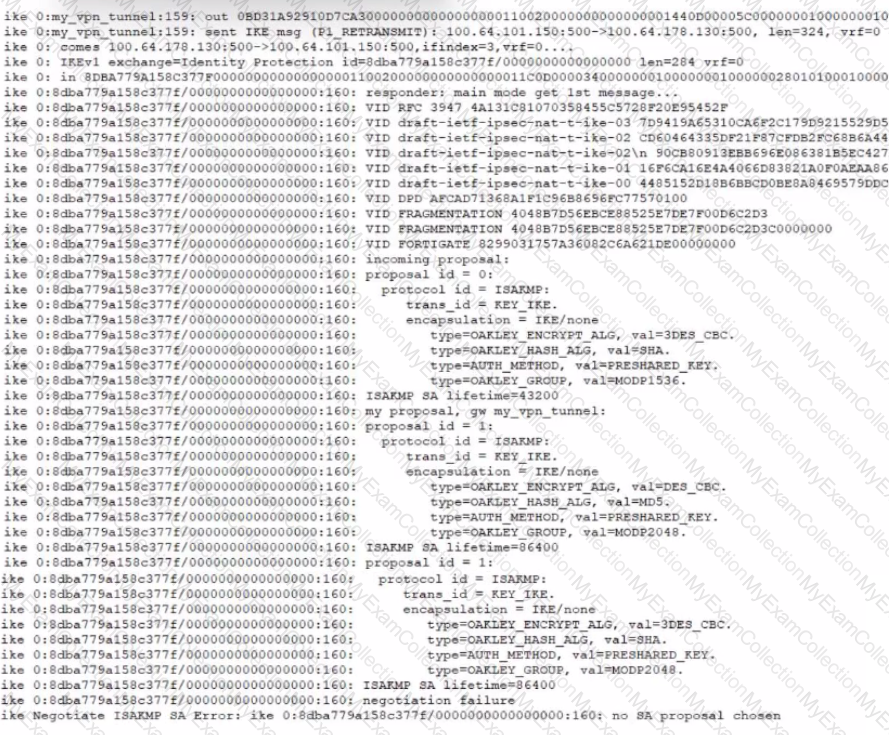
The VPN tunnel between headquarters and the branch office is not being established.
What is causing the problem?
An automation stitch was configured using an incoming webhook as the trigger named 'my_incoming_webhook'. The action is configured to execute the CLI Script shown:
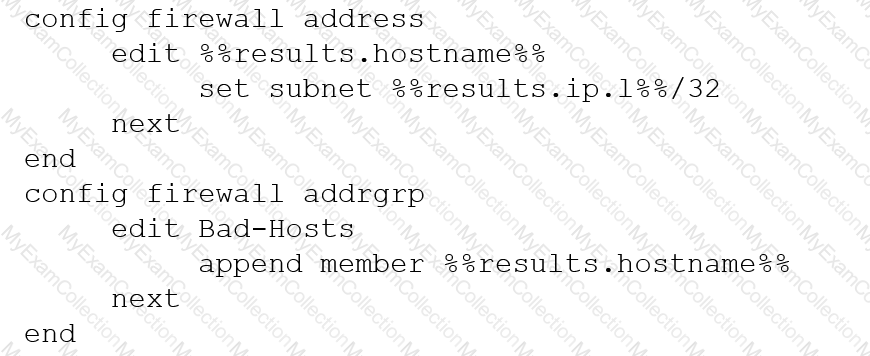
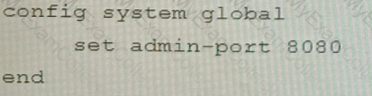
A FortiGate running FortiOS 7.2.0 GA is configured in multi-vdom mode with a vdom set to vdom type Admin and another vdom set to vdom type Traffic.
Which two GUI sections are available on both VDOM types? (Choose two.)
Refer to the exhibit.
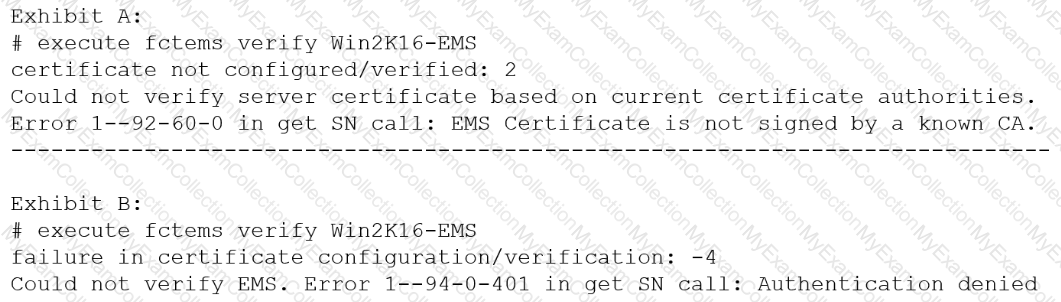
The exhibit shows two error messages from a FortiGate root Security Fabric device when you try to configure a new connection to a FortiClient EMS Server.
Referring to the exhibit, which two actions will fix these errors? (Choose two.)
Refer to the exhibit showing an SD-WAN configuration.
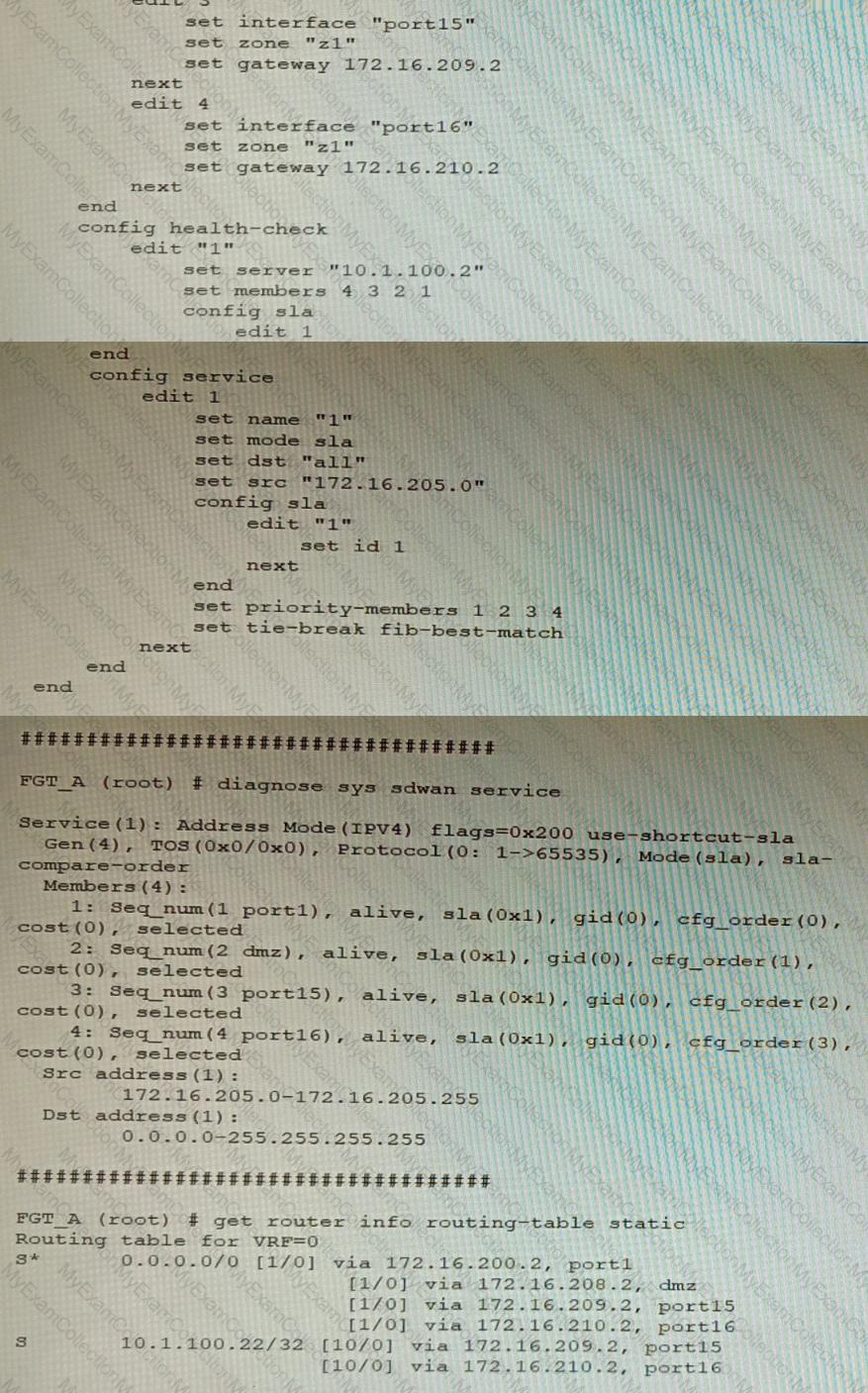
According to the exhibit, if an internal user pings 10.1.100.2 and 10.1.100.22 from subnet 172.16.205.0/24, which outgoing interfaces will be used?
You must analyze an event that happened at 20:37 UTC. One log relevant to the event is extracted from FortiGate logs:
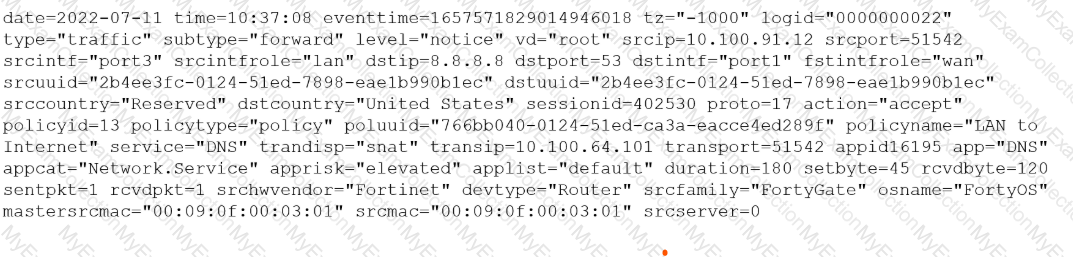
The devices and the administrator are all located in different time zones Daylight savings time (DST) is disabled
• The FortiGate is at GMT-1000.
• The FortiAnalyzer is at GMT-0800
• Your browser local time zone is at GMT-03.00
You want to review this log on FortiAnalyzer GUI, what time should you use as a filter?
Refer to the exhibit.
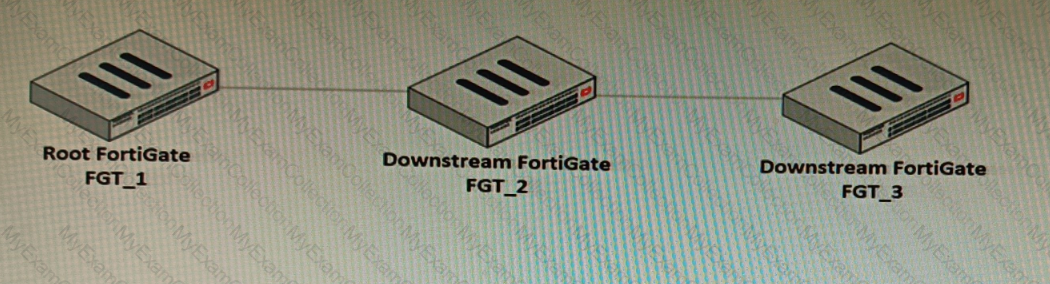
You have deployed a security fabric with three FortiGate devices as shown in the exhibit. FGT_2 has the following configuration:
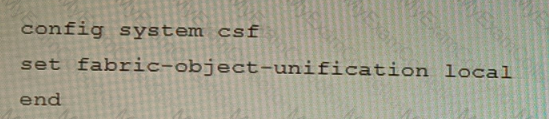
FGT_1 and FGT_3 are configured with the default setting. Which statement is true for the synchronization of fabric-objects?
Refer to the exhibits.
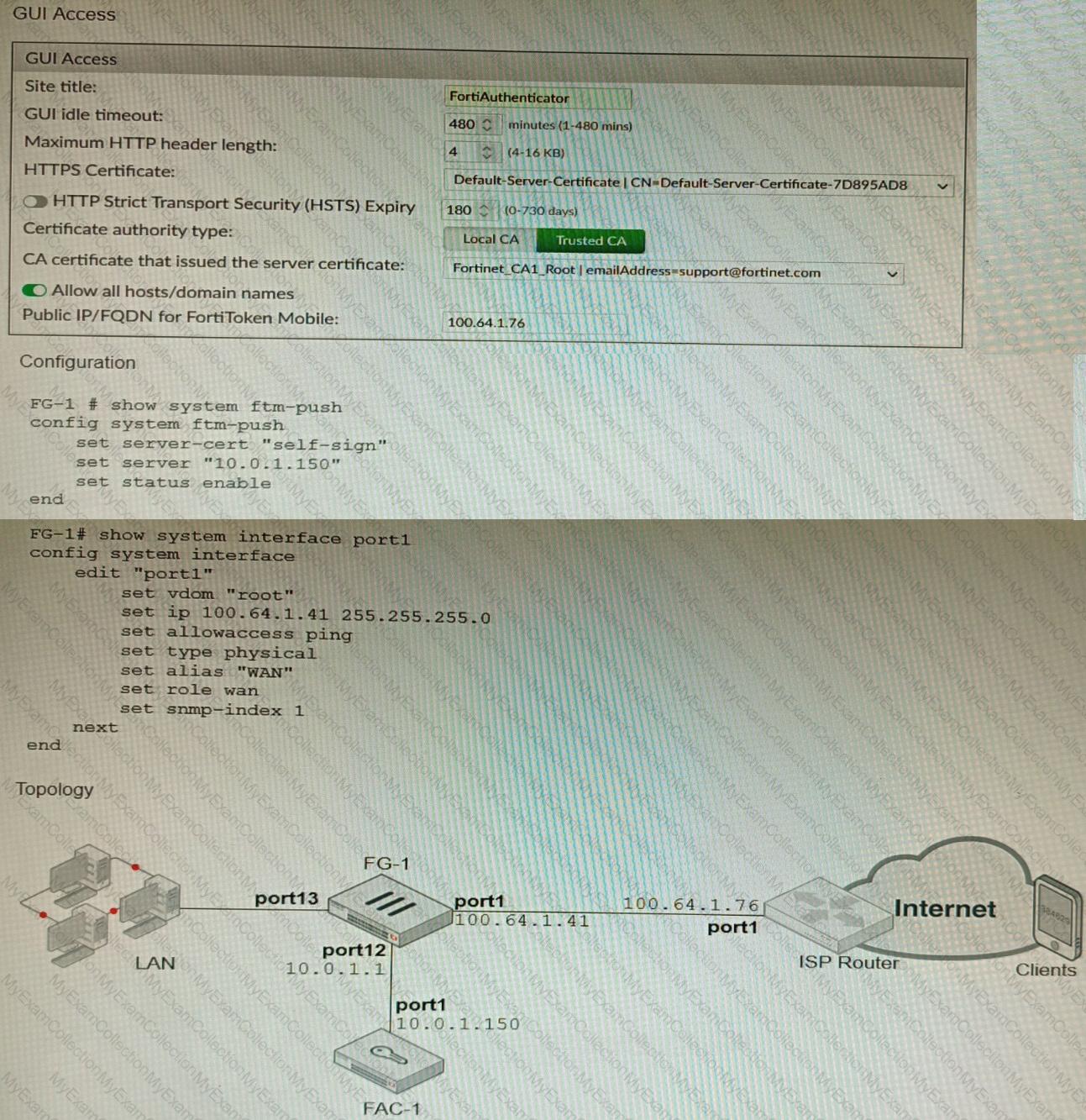
An administrator has configured a FortiGate and Forti Authenticator for two-factor authentication with FortiToken push notifications for their SSL VPN login. Upon initial review of the setup, the administrator has discovered that the customers can manually type in their two-factor code and authenticate but push notifications do not work
Based on the information given in the exhibits, what must be done to fix this?
A retail customer with a FortiADC HA cluster load balancing five webservers in L7 Full NAT mode is receiving reports of users not able to access their website during a sale event. But for clients that were able to connect, the website works fine.
CPU usage on the FortiADC and the web servers is low, application and database servers are still able to handle more traffic, and the bandwidth utilization is under 30%.
Which two options can resolve this situation? (Choose two.)
Refer to the CLI output:
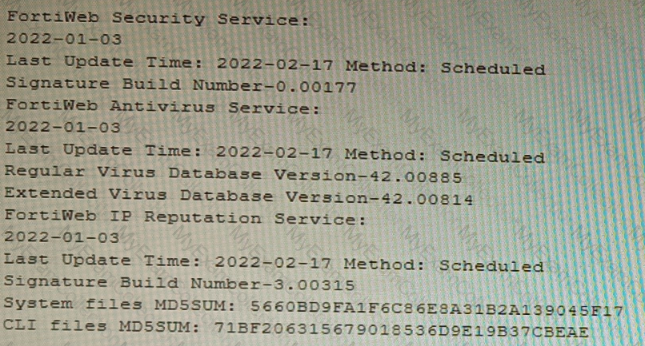
Given the information shown in the output, which two statements are correct? (Choose two.)
Review the following FortiGate-6000 configuration excerpt:
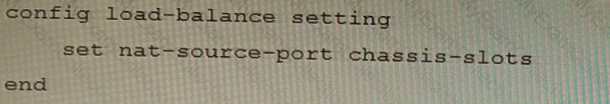
Based on the configuration, which statement is correct regarding SNAT source port partitioning behavior?
Refer to the exhibits.
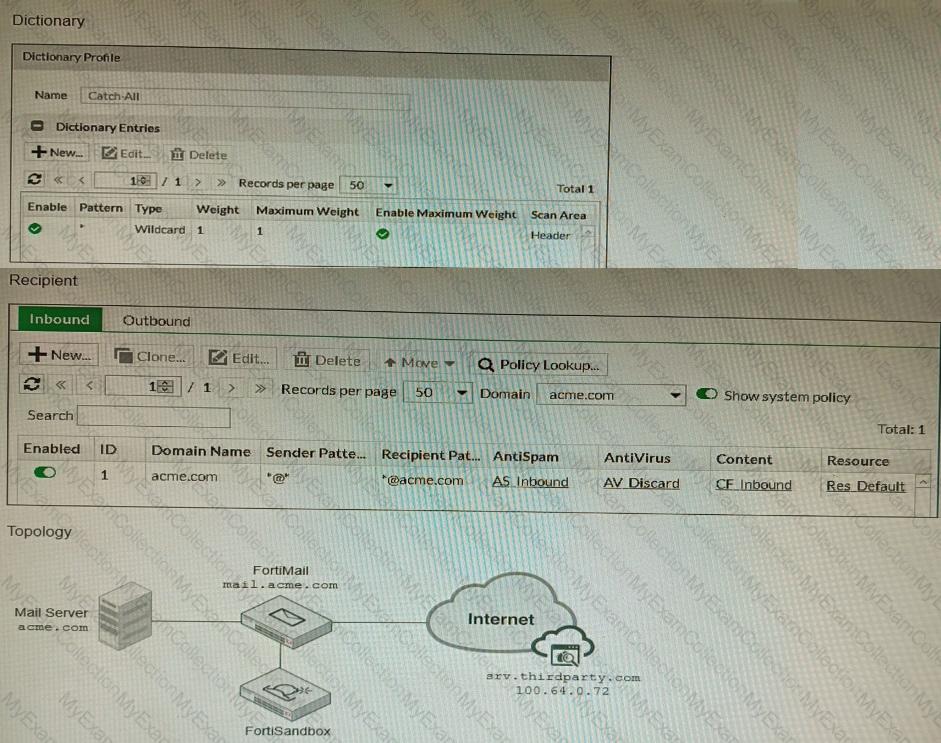
The exhibits show a FortiMail network topology, Inbound configuration settings, and a Dictionary Profile.
You are required to integrate a third-party's host service (srv.thirdparty.com) into the e-mail processing path.
All inbound e-mails must be processed by FortiMail antispam and antivirus with FortiSandbox integration. If the email is clean, FortiMail must forward it to the third-party service, which will send the email back to FortiMail for final delivery, FortiMail must not scan the e-mail again.
Which three configuration tasks must be performed to meet these requirements? (Choose three.)
You are performing a packet capture on a FortiGate 2600F with the hyperscale licensing installed. You need to display on screen all egress/ingress packets from the port16 interface that have been offloaded to the NP7.
Which three commands need to be run? (Choose three.)