Which two statements are true regarding certificate-based authentication for ZTNA deployment? (Choose two.)
FortiGate signs the client certificate submitted by FortiClient.
The default action for empty certificates is block
Certificate actions can be configured only on the FortiGate CLI
Client certificate configuration is a mandatory component for ZTNA
Answer:
Explanation:
 Certificate-based authentication is a method of verifying the identity of a device or user by using a digital certificate issued by a trusted authority. For ZTNA deployment, certificate-based authentication is used to ensure that only authorized devices and users can access the protected applications or resources.
B. The default action for empty certificates is block. This is true because ZTNA requires both device and user verification before granting access. If a device does not have a valid certificate issued by the ZTNA CA, it will be blocked by the ZTNA gateway. This prevents unauthorized or compromised devices from accessing the network.
D. Client certificate configuration is a mandatory component for ZTNA. This is true because ZTNA relies on client certificates to identify and authenticate devices. Client certificates are generated by the ZTNA CA and contain the device ID, ZTNA tags, and other information. Client certificates are distributed to devices by the ZTNA management server (such as EMS) and are used to establish a secure connection with the ZTNA gateway.
A. FortiGate signs the client certificate submitted by FortiClient. This is false because FortiGate does not sign the client certificates. The client certificates are signed by the ZTNA CA, which is a separate entity from FortiGate. FortiGate only verifies the client certificates and performs certificate actions based on the ZTNA tags.
C. Certificate actions can be configured only on the FortiGate CLI. This is false because certificate actions can be configured on both the FortiGate GUI and CLI. Certificate actions are the actions that FortiGate takes based on the ZTNA tags in the client certificates. For example, FortiGate can allow, block, or redirect traffic based on the ZTNA tags.
References :=
- 1: Technical Tip: ZTNA for Corporate hosts with SAML authentication and FortiAuthenticator as IDP
- 2: Zero Trust Network Access - Fortinet
Which method is used to install passive agent on an endpoint?
Deployed by using a login/logout script
Agent is downloaded from Playstore
Agent is downloaded and run from captive portal
Installed by user or deployment tools
Answer:
Explanation:
The method used to install a passive agent on an endpoint is:
- D. Installed by user or deployment tools: Passive agents are typically installed on endpoints either manually by users or automatically through deployment tools used by the organization.
The other options do not accurately describe the installation of passive agents:
- A. Deployed by using a login/logout script: This is not the standard method for deploying passive agents.
- B. Agent is downloaded from Playstore: This is more relevant for mobile devices and does not represent the general method for passive agent installation.
- C. Agent is downloaded and run from captive portal: This method is not typically used for installing passive agents.
References:
- FortiNAC Agent Deployment Guide.
- Installation Methods for Passive Agents in FortiNAC.
Exhibit.
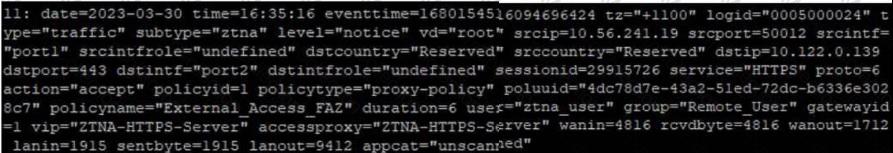
Based on the ZTNA logs provided, which statement is true?
The Remote_user ZTNA tag has matched the ZTNA rule
An authentication scheme is configured
The external IP for ZTNA server is 10 122 0 139.
Traffic is allowed by firewall policy 1
Answer:
Explanation:
Based on the ZTNA logs provided, the true statement is:
- A. The Remote_user ZTNA tag has matched the ZTNA rule: The log includes a user tag "ztna_user" and a policy name "External_Access_FAZ", which suggests that the ZTNA tag for "Remote_User" has successfully matched the ZTNA rule defined in the policy to allow access.
The other options are not supported by the information in the log:
- B. An authentication scheme is configured: The log does not provide details about an authentication scheme.
- C. The external IP for ZTNA server is 10.122.0.139: The log entry indicates "dstip=10.122.0.139" which suggests that this is the destination IP address for the traffic, not necessarily the external IP of the ZTNA server.
- D. Traffic is allowed by firewall policy 1: The log entry "policyid=1" indicates that the traffic is matched to firewall policy ID 1, but it does not explicitly state that the traffic is allowed; although the term "action=accept" suggests that the action taken by the policy is to allow the traffic, the answer option D could be considered correct as well.
References:
- Interpretation of FortiGate ZTNA Log Files.
- Analyzing Traffic Logs for Zero Trust Network Access.
Which factor is a prerequisite on FortiNAC to add a Layer 3 router to its inventory?
Allow HTTPS access from the router to the FortiNAC ethO IP address
Allow FTP access to the FortiNAC database from the router
The router responding to ping requests from the FortiNAC eth1 IP address
SNMP or CLI access to the router to carry out remote tasks
Answer:
Explanation:
 FortiNAC uses SNMP or CLI to communicate with network devices such as routers and switches. To add a Layer 3 router to its inventory, FortiNAC needs to have SNMP or CLI access to the router to perform remote tasks such as polling, VLAN assignment, and port shutdown. Without SNMP or CLI access, FortiNAC cannot manage the router or its ports. Therefore, SNMP or CLI access is a prerequisite for adding a Layer 3 router to FortiNAC’s inventory. References := https://docs.fortinet.com/document/fortinac/9.4.0/administration-guide/105927/inventory
https://docs.fortinet.com/document/fortinac/9.4.0/administration-guide/344098/l3-polling
What are two functions of NGFW in a ZTA deployment? (Choose two.)
Acts as segmentation gateway
Endpoint vulnerability management
Device discovery and profiling
Packet Inspection
Answer:
Explanation:
NGFW stands for Next-Generation Firewall, which is a network security device that provides advanced features beyond the traditional firewall, such as application awareness, identity awareness, threat prevention, and integration with other security tools. ZTA stands for Zero Trust Architecture, which is a security model that requires strict verification of the identity and context of every request before granting access to network resources. ZTA assumes that no device or user can be trusted by default, even if they are connected to a corporate network or have been previously verified.
In a ZTA deployment, NGFW can perform two functions:
- Acts as segmentation gateway: NGFW can act as a segmentation gateway, which is a device that separates different segments of the network based on security policies and rules. Segmentation can help isolate and protect sensitive data and applications from unauthorized or malicious access, as well as reduce the attack surface and contain the impact of a breach. NGFW can enforce granular segmentation policies based on the identity and context of the devices and users, as well as the applications and services they are accessing. NGFW can also integrate with other segmentation tools, such as software-defined networking (SDN) and microsegmentation, to provide a consistent and dynamic segmentation across the network.
- Device discovery and profiling: NGFW can also perform device discovery and profiling, which are processes that identify and classify the devices that are connected to the network, as well as their attributes and behaviors. Device discovery and profiling can help NGFW to apply the appropriate security policies and rules based on the device type, role, location, health, and activity. Device discovery and profiling can also help NGFW to detect and respond to anomalous or malicious devices that may pose a threat to the network.
References: =
Some possible references for the answer and explanation are:
What is a Next-Generation Firewall (NGFW)? | Fortinet : What is Zero Trust Network Access (ZTNA)? | Fortinet : Zero Trust Architecture Explained: A Step-by-Step Approach : The Most Common NGFW Deployment Scenarios : Sample Configuration for Post vWAN Deployment
What happens when FortiClient EMS is configured as an MDM connector on FortiNAC?
FortiNAC sends the hostdata to FortiClient EMS to update its host database
FortiClient EMS verifies with FortiNAC that the device is registered
FortiNAC polls FortiClient EMS periodically to update already registered hosts in FortiNAC
FortiNAC checks for device vulnerabilities and compliance with FortiClient
Answer:
Explanation:
When FortiClient EMS is configured as an MDM connector on FortiNAC, it allows FortiNAC to obtain host information from FortiClient EMS and use it for network access control. FortiNAC polls FortiClient EMS periodically (every 5 minutes by default) to update already registered hosts in FortiNAC. This ensures that FortiNAC has the latest host data from FortiClient EMS, such as device type, OS, IP address, MAC address, hostname, and FortiClient version. FortiNAC can also use FortiClient EMS as an authentication source for devices that have FortiClient installed. FortiNAC does not send any data to FortiClient EMS or check for device vulnerabilities and compliance with FortiClient123. References := 1: MDM Service Connectors | FortiClient EMS Integration 2: FortiClient EMS Device Integration|FortiNAC 9.4.0 - Fortinet Documentation 3: Technical Tip: Integration with FortiClient EMS

