Refer to the exhibit.
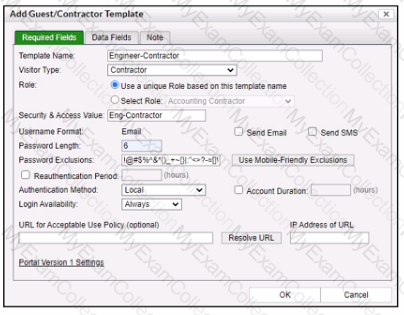
When a contractor account is created using this template, what value will be set in the accounts Rote field?
In a wireless integration, what method does FortiNAC use to obtain connecting MAC address information?
Refer to the exhibit.
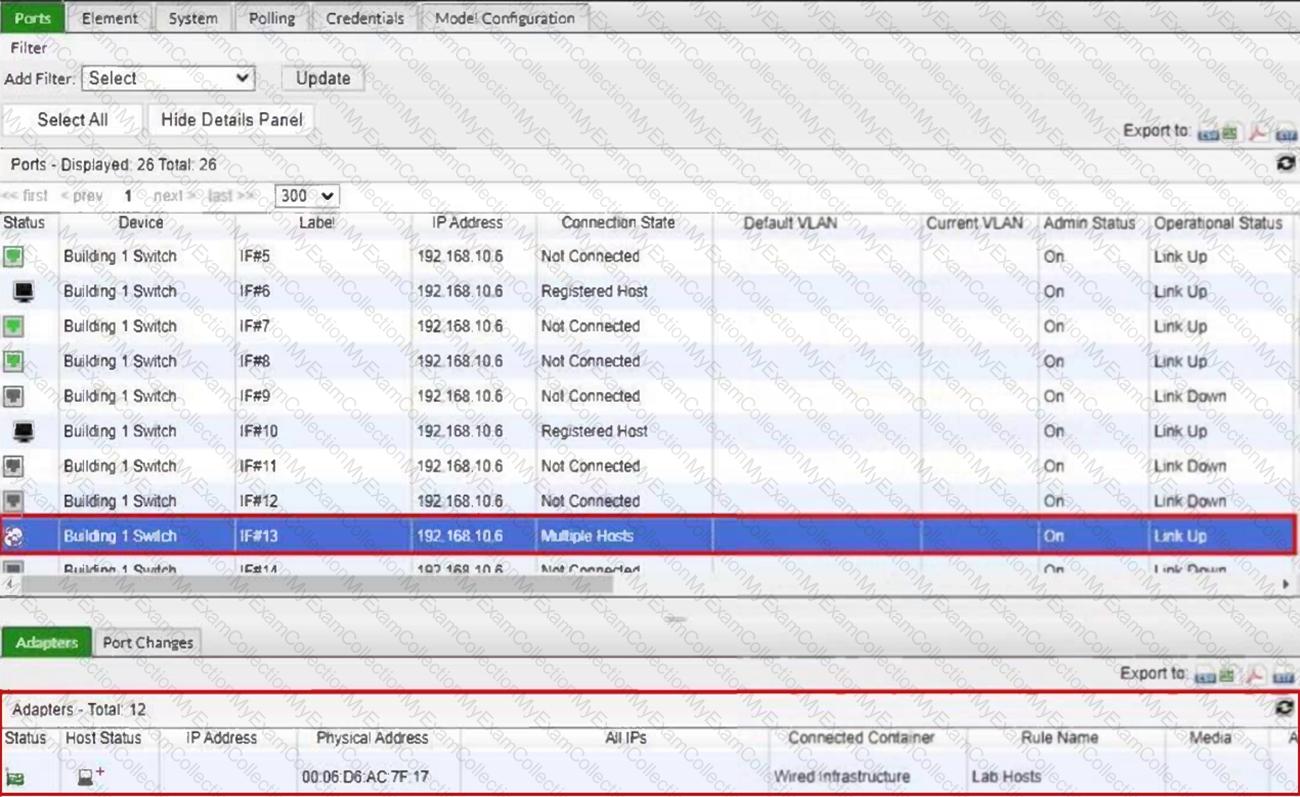
What would happen if the highlighted port with connected hosts was placed in both the Forced Registration and Forced Remediation port groups?
Which three communication methods are used by FortiNAC to gather information from and control, infrastructure devices? (Choose three.)
Refer to the exhibit.
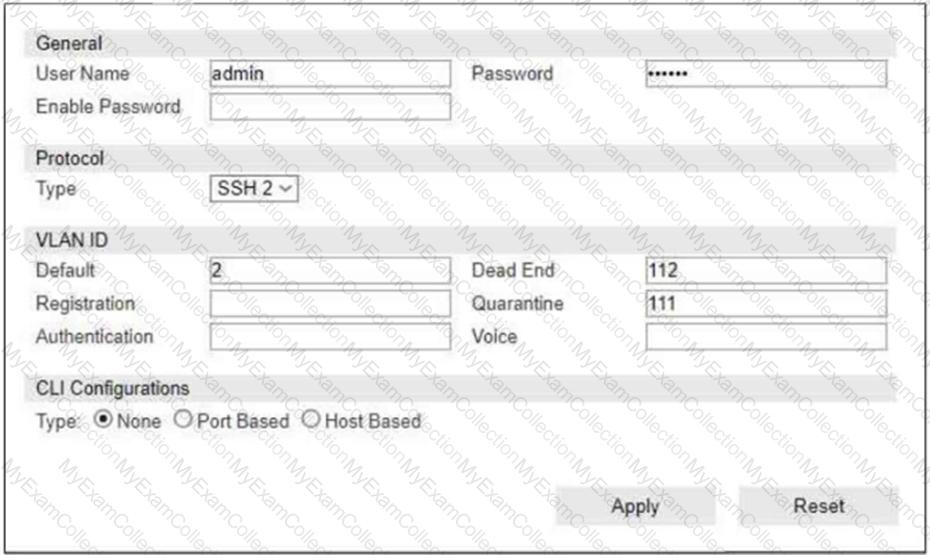
If you are forcing the registration of unknown (rogue) hosts, and an unknown (rogue) host connects to a port on the switch, what occurs?
Which two device classification options can register a device automatically and transparently to the end user? (Choose two.)
When FortiNAC is managing FortiGate VPN users, why is an endpoint compliance policy necessary?
When configuring isolation networks in the configuration wizard, why does a Layer 3 network type allow for more than one DHCP scope for each isolation network type?

