Which statement correctly describes NetAPI polling mode for the FSSO collector agent?
Refer to the exhibits.
Exhibit A shows a topology for a FortiGate HA cluster that performs proxy-based inspection on traffic. Exhibit B shows the HA configuration and the partial output of the get system ha status command.
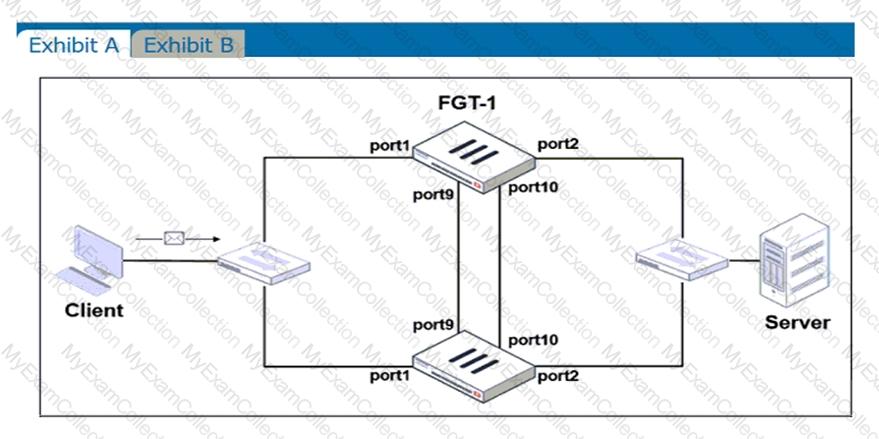
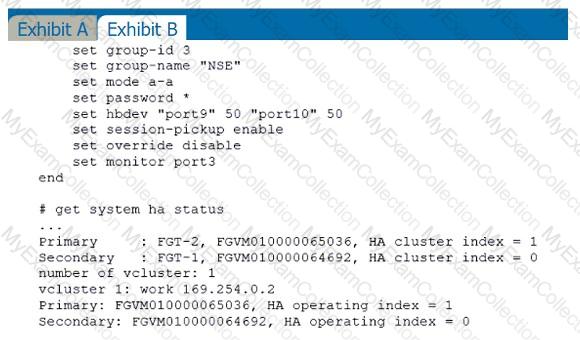
Based on the exhibits, which two statements about the traffic passing through the cluster are true? (Choose two.)
When a firewall policy is created, which attribute is added to the policy to support recording logs to a FortiAnalyzer or a FortiManager and improves functionality when a FortiGate is integrated with these devices?
An administrator is configuring an IPsec VPN between site A and site B. The Remote Gateway setting in both sites has been configured as Static IP Address. For site A, the local quick mode selector is 192. 168. 1.0/24 and the remote quick mode selector is 192. 168.2.0/24.
Which subnet must the administrator configure for the local quick mode selector for site B?
17
In consolidated firewall policies, IPv4 and IPv6 policies are combined in a single consolidated policy. Instead of separate policies. Which three statements are true about consolidated IPv4 and IPv6 policy configuration? (Choose three.)
Refer to the exhibit.
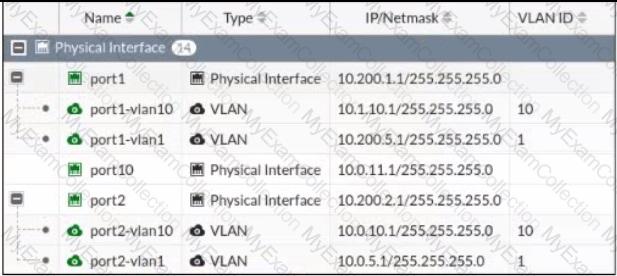
Given the interfaces shown in the exhibit. which two statements are true? (Choose two.)
Refer to the exhibit.

The exhibit contains a network diagram, virtual IP, IP pool, and firewall policies configuration.
The WAN (port1) interface has the IP address 10.200. 1. 1/24.
The LAN (port3) interface has the IP address 10 .0.1.254. /24.
The first firewall policy has NAT enabled using IP Pool.
The second firewall policy is configured with a VIP as the destination address.
Which IP address will be used to source NAT the internet traffic coming from a workstation with the IP address 10.0. 1. 10?
What is the limitation of using a URL list and application control on the same firewall policy, in NGFW policy-based mode?
18
If the Issuer and Subject values are the same in a digital certificate, which type of entity was the certificate issued to?
Which statement about the deployment of the Security Fabric in a multi-VDOM environment is true?
7
Which two settings can be separately configured per VDOM on a FortiGate device? (Choose two.)
27
Which feature in the Security Fabric takes one or more actions based on event triggers?
Refer to the exhibit, which contains a session diagnostic output.

Which statement is true about the session diagnostic output?
93
Which two statements are correct regarding FortiGate HA cluster virtual IP addresses? (Choose two.)
FortiGate is operating in NAT mode and is configured with two virtual LAN (VLAN) subinterfaces added to the same physical interface.
In this scenario, what are two requirements for the VLAN ID? (Choose two.)
Refer to the exhibit.
The exhibit shows a diagram of a FortiGate device connected to the network, the firewall policy and VIP configuration on the FortiGate device, and the routing table on the ISP router.
When the administrator tries to access the web server public address (203.0.113.2) from the internet, the connection times out. At the same time, the administrator runs a sniffer on FortiGate to capture incoming web traffic to the server and does not see any output.

Based on the information shown in the exhibit, what configuration change must the administrator make to fix the connectivity issue?
What is the effect of enabling auto-negotiate on the phase 2 configuration of an IPsec tunnel?
Refer to the exhibit.

Based on the raw log, which two statements are correct? (Choose two.)
Refer to the exhibit to view the application control profile.

Based on the configuration, what will happen to Apple FaceTime?
Refer to the exhibit.

The exhibit shows the IPS sensor configuration.
If traffic matches this IPS sensor, which two actions is the sensor expected to take? (Choose two.)
46
Which two types of traffic are managed only by the management VDOM? (Choose two.)
2
Which two statements are true when FortiGate is in transparent mode? (Choose two.)
106
Which two actions can you perform only from the root FortiGate in a Security Fabric? (Choose two.)
A network administrator has enabled SSL certificate inspection and antivirus on FortiGate. When downloading an EICAR test file through HTTP, FortiGate detects the virus and blocks the file. When downloading the same file through HTTPS, FortiGate does not detect the virus and the file can be downloaded.
What is the reason for the failed virus detection by FortiGate?
Refer to the exhibit.
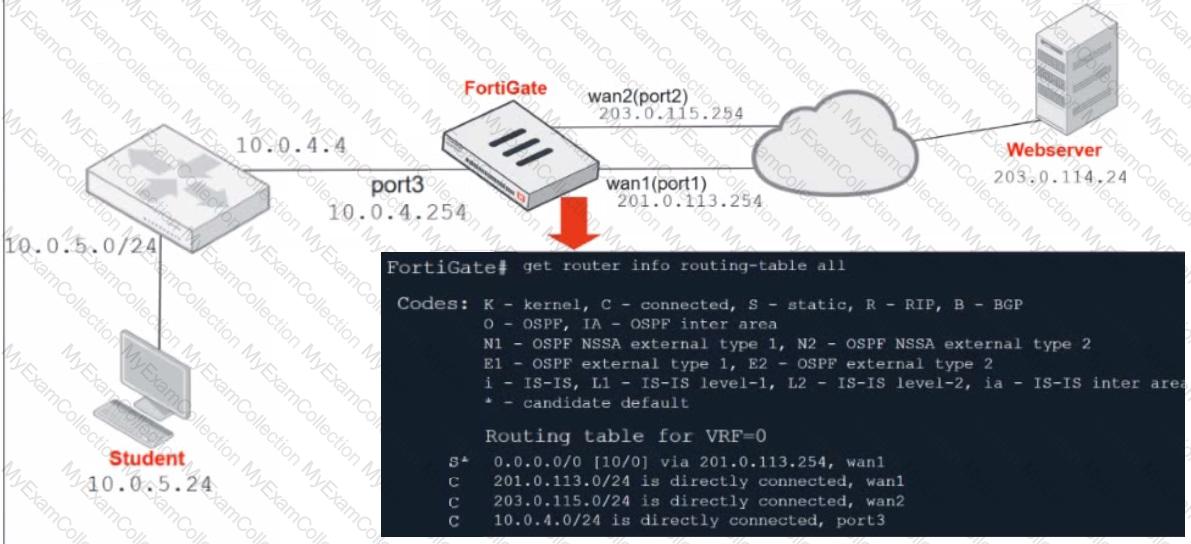
Which contains a network diagram and routing table output.
The Student is unable to access Webserver.
What is the cause of the problem and what is the solution for the problem?
What are two characteristics of FortiGate HA cluster virtual IP addresses? (Choose two.)
Which two settings are required for SSL VPN to function between two FortiGate devices? (Choose two.)
Refer to the exhibit.

Given the routing database shown in the exhibit, which two statements are correct? (Choose two.)
113
What inspection mode does FortiGate use if it is configured as a policy-based next-generation firewall (NGFW)?
68
If the Services field is configured in a Virtual IP (VIP), which statement is true when central NAT is used?
16
FortiGate is configured as a policy-based next-generation firewall (NGFW) and is applying web filtering and application control directly on the security policy. Which two other security profiles can you apply to the security policy? (Choose two.)
87
Which of the following are valid actions for FortiGuard category based filter in a web filter profile ui proxy-based inspection mode? (Choose two.)
Which three security features require the intrusion prevention system (IPS) engine to function? (Choose three.)
An administrator is configuring an Ipsec between site A and siteB. The Remotes Gateway setting in both sites has been configured as Static IP Address. For site A, the local quick mode selector is 192. 16. 1.0/24 and the remote quick mode selector is 192. 16.2.0/24. How must the administrator configure the local quick mode selector for site B?
Refer to the exhibit.
The exhibit shows a diagram of a FortiGate device connected to the network and the firewall policy and IP pool configuration on the FortiGate device.
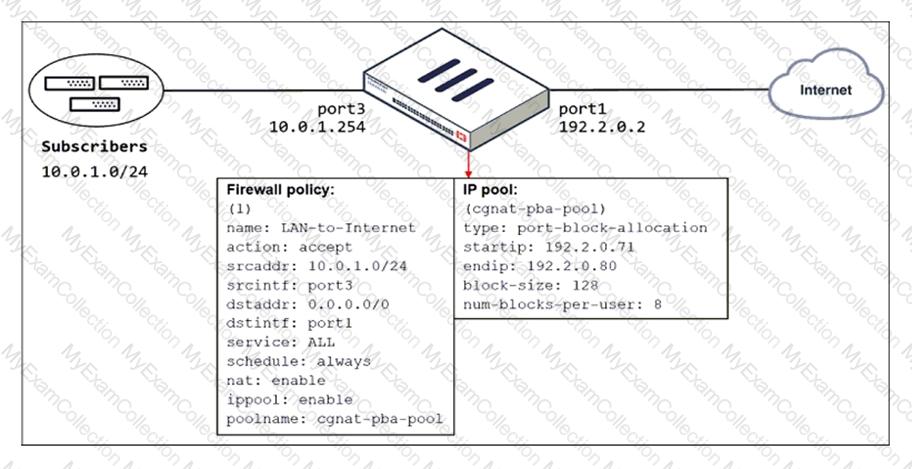
Which two actions does FortiGate take on internet traffic sourced from the subscribers? (Choose two.)
Which three statements explain a flow-based antivirus profile? (Choose three.)
By default, FortiGate is configured to use HTTPS when performing live web filtering with FortiGuard servers.
Which CLI command will cause FortiGate to use an unreliable protocol to communicate with FortiGuard servers for live web filtering?
What is the limitation of using a URL list and application control on the same firewall policy, in NGFW policy-based mode?
An employee needs to connect to the office through a high-latency internet connection.
Which SSL VPN setting should the administrator adjust to prevent SSL VPN negotiation failure?
32
When configuring a firewall virtual wire pair policy, which following statement is true?
95
Examine this output from a debug flow:
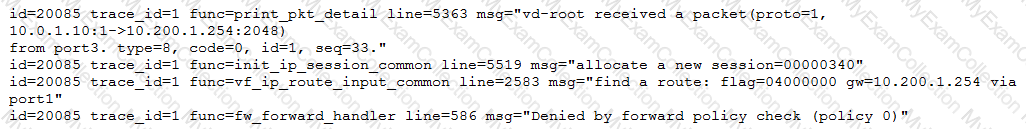
Why did the FortiGate drop the packet?
Refer to the exhibit.
An administrator added a configuration for a new RADIUS server. While configuring, the administrator selected the Include in every user group option.

What is the impact of using the Include in every user group option in a RADIUS configuration?

