An administrator is configuring ISCSI on an SVM and requires that all network traffic Is encrypted. What must be done to satisfy this requirement?
An administrator runs the vserver nvme namespace convert-from-iun command on a NetApp ASA cluster to increase host performance.
What is modified by the convert command?
Which feature enables simultaneous snapshots of multiple LUNs In different volumes?
What needs to be done to create a consistent Snapshot copy of a LUN without disruptions?
A customer Is setting up a four-node NetApp AFF cluster for use with NVMe/TCP and wants to use automatic host discovery.
Which protocol is used for the discovery of controllers?
When using FCP, what is the minimum number of FC switches needed to redundantly attach three ESXi hosts?
Which two steps must be taken first to restore a LUN from a SnapMirror Synchronous destination? (Choose two.)
A LUN Is displaying 90% used space in the NetApp ONTAP CLI, but a Windows Server shows only 10% used space.
What is the first step to take to address this issue?
Click the Exhibit button.
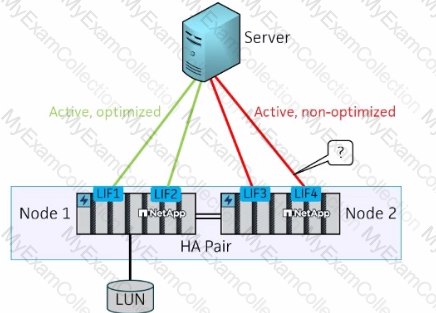
A customer is testing a newly installed NetApp AFF A400 all-flash HA storage system. An SVM for FCP with a LUN on Node 1 has been configured, and a server has been connected as shown in the exhibit. For testing, the engineer plans to do a storage failover of Node 1.
After the failover, what is the expected status of the marked path?
A customer needs to verify if jumbo frames have been configured correctly for an ISCSI workload. Which command should be used?
A customer requires multiple SAN and NAS protocols on a NetApp AFF cluster. The cluster must concurrently serve a namespace over NVMe/FC, a LUN over FCP, a LUN over iSCSI, and an NFS export.
Based on these requirements, what is the minimum data SVM count that is required?
An administrator is setting up a NetApp ONTAP AFF system for both NVMe/TCP and iSCSI. Which task is required for SAN configuration?
A customer Is setting up a two-node cluster to serve (SCSI LUNs. How many interfaces should be created?
A customer wants to enable CHAP authentication on their iSCSI sessions.
Which command should be used to set up the appropriate security policies and passwords?
A storage administrator wants to increase security and optimize performance in a recently implemented SAN deployment.
What should the storage administrator configure to ensure initiator restriction to certain LIFs?

