Exhibit:
Which two statements are correct about the output shown in the exhibit. (Choose Two)
You want to enable transparent mode on your SRX series device.
In this scenario, which three actions should you perform? (Choose three.)
You want to deploy two vSRX instances in different public cloud providers to provide redundant security services for your network. Layer 2 connectivity between the two vSRX instances is not possible.
What would you configure on the vSRX instances to accomplish this task?
A customer wants to be able to initiate a return connection to an internal host from a specific
Server.
Which NAT feature would you use in this scenario?
Which encapsulation type must be configured on the lt-0/0/0 logical units for an interconnect
logical systems VPLS switch?
You are asked to configure tenant systems.
Which two statements are true in this scenario? (Choose two.)
Referring to the exhibit, you have been assigned the user LogicalSYS1 credentials shown in
the configuration.
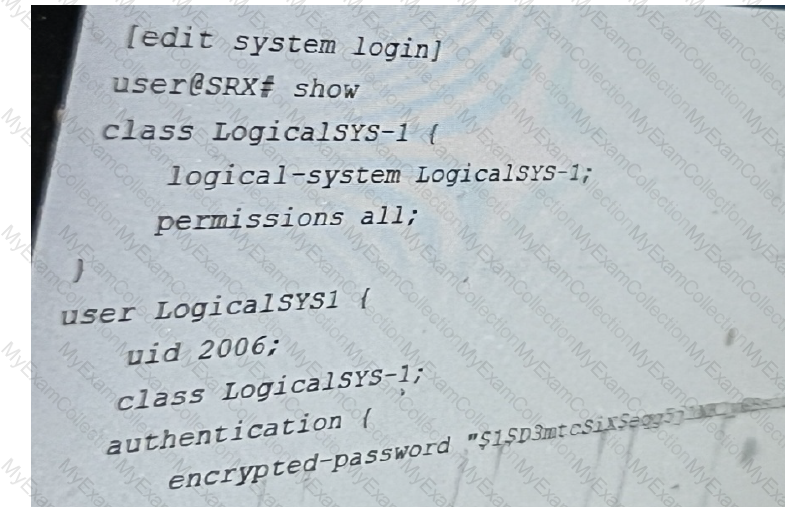
In this scenario, which two statements are correct? (Choose two.)
You want to use a security profile to limit the system resources allocated to user logical systems.
In this scenario, which two statements are true? (Choose two.)
Which two statements are true about the procedures the Junos security device uses when handling traffic destined for the device itself? (Choose two.)
Click the Exhibit button.
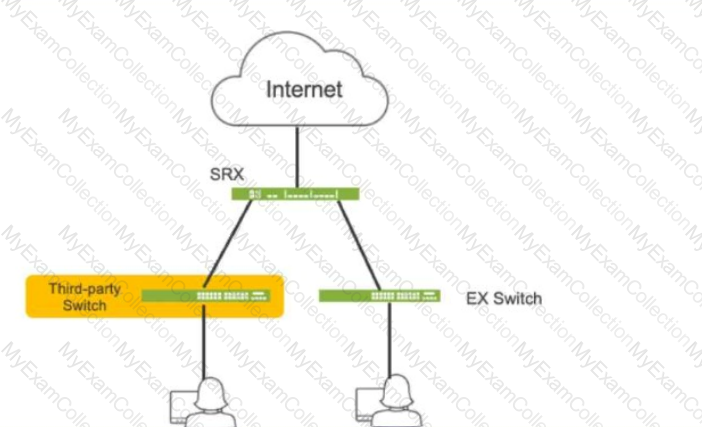
Referring to the exhibit, which three actions do you need to take to isolate the hosts at the switch port level if they become infected with malware? (Choose three.)
Exhibit:
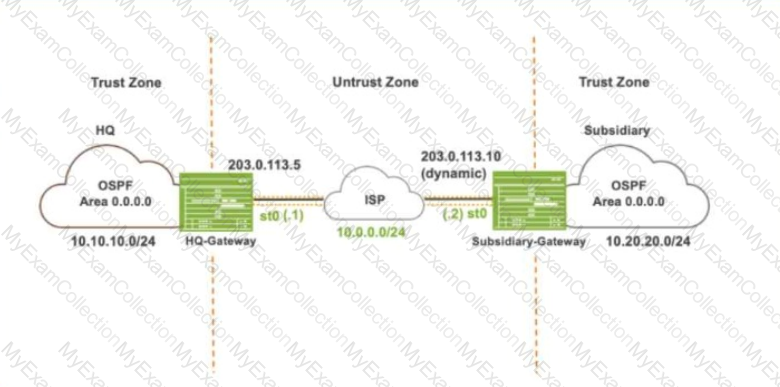
Referring to the exhibit, which IKE mode will be configured on the HQ-Gateway and Subsidiary-Gateway?
You want to test how the device handles a theoretical session without generating traffic on the Junos security device.
Which command is used in this scenario?
You configure two Ethernet interfaces on your SRX Series device as Layer 2 interfaces and add them to the same VLAN. The SRX is using the default L2-learning setting. You do not add the interfaces to a security zone.
Which two statements are true in this scenario? (Choose two.)
You have deployed automated threat mitigation using Security Director with Policy Enforcer, Juniper ATP Cloud, SRX Series devices, and EX Series switches.
In this scenario, which device is responsible for blocking the infected hosts?
You want to bypass IDP for traffic destined to social media sites using APBR, but it is not working and IDP is dropping the session.
What are two reasons for this problem? (Choose two.)
Exhibit:
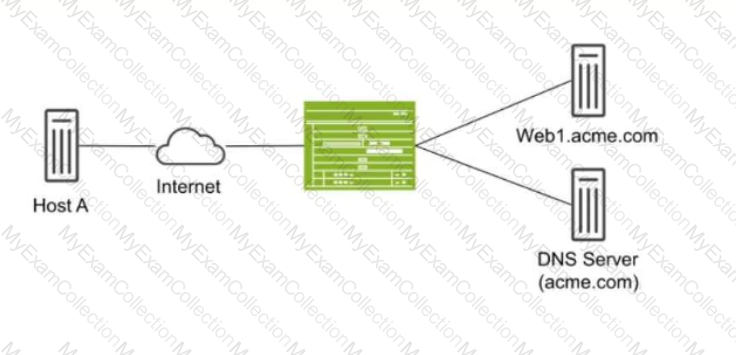
Host A shown in the exhibit is attempting to reach the Web1 webserver, but the connection is failing. Troubleshooting reveals that when Host A attempts to resolve the domain name of the server (web.acme.com), the request is resolved to the private address of the server rather than its public IP.
Which feature would you configure on the SRX Series device to solve this issue?
Â
You are attempting to ping an interface on your SRX Series device, but the ping is unsuccessful.
Â
What are three reasons for this behavior? (Choose three.)
Â
Which two statements about the differences between chassis cluster and multinode HA on
SRX series devices are true? (Choose Two)
Exhibit:
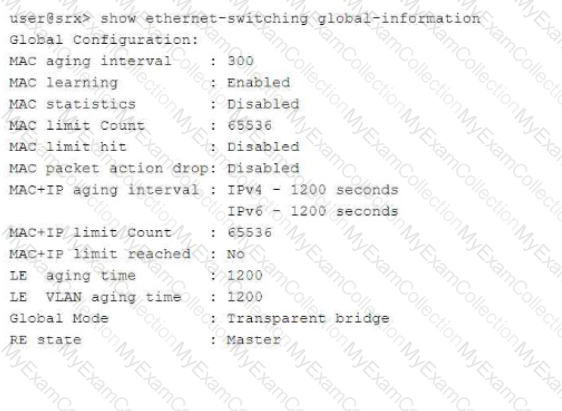
Referring to the exhibit, which two statements are correct? (Choose two.)
Which two statements are correct about automated threat mitigation with Security Director? (Choose two.)
Exhibit:

Your company uses SRX Series devices to establish an IPsec VPN that connects Site-1 and the HQ networks. You want VoIP traffic to receive priority over data traffic when it is forwarded across the VPN.
Which three actions should you perform in this scenario? (Choose three.)
You are deploying IPsec VPNs to securely connect several enterprise sites with ospf for dynamic
routing. Some of these sites are secured by third-party devices not running Junos.
Which two statements are true for this deployment? (Choose two.)
Which two statements are true when setting up an SRX Series device to operate in mixed mode? (Choose two.)
You have deployed two SRX Series devices in an active/passive multimode HA scenario.
In this scenario, which two statements are correct? (Choose two.)
Referring to the exhibit, you are assigned the tenantSYS1 user credentials on an SRX series
device.
In this scenario, which two statements are correct? (Choose two.)
You need to generate a certificate for a PKI-based site-to-site VPN. The peer is expecting to
user your domain name vpn.juniper.net.
Which two configuration elements are required when you generate your certificate request? (Chose two,)
Which two statements about policy enforcer and the forescout integration are true? (Choose two)
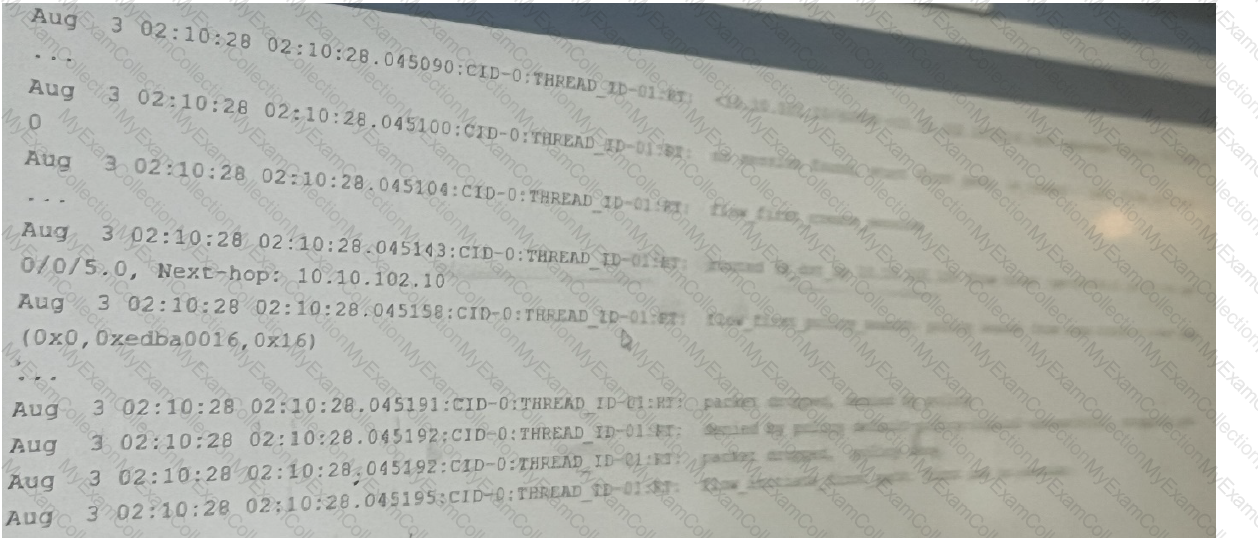
You are using trace options to troubleshoot a security policy on your SRX Series device.
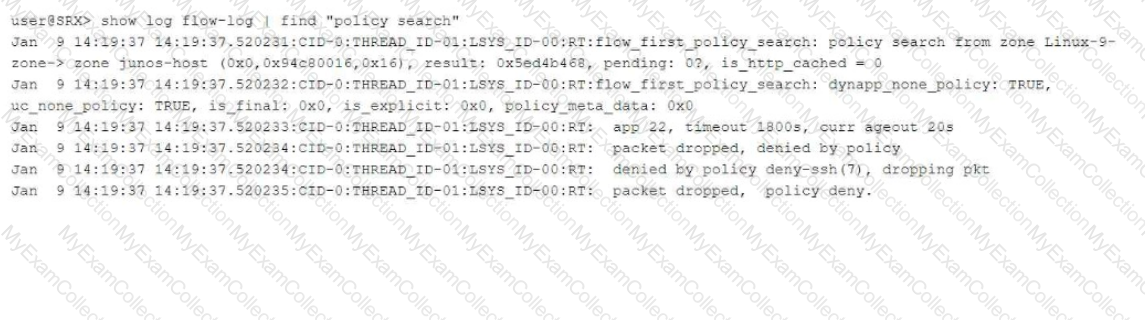
Referring to the exhibit, which two statements are true? (Choose two.)
You want to configure the SRX Series device to map two peer interfaces together and ensure that there is no switching or routing lookup to forward traffic.
Which feature on the SRX Series device is used to accomplish this task?

