You want to enroll an SRX Series device with Juniper ATP Appliance. There is a firewall device in the path between the devices. In this scenario, which port should be opened in the firewall device?
You are asked to detect domain generation algorithms
Which two steps will accomplish this goal on an SRX Series firewall? (Choose two.)
You are asked to deploy Juniper atp appliance in your network. You must ensure that incidents and
alerts are sent to your SIEM.
In this scenario, which logging output format is supported?
You are required to deploy a security policy on an SRX Series device that blocks all known Tor network IP addresses. Which two steps will fulfill this requirement? (Choose two.)
You are asked to deploy filter-based forwarding on your SRX Series device for incoming traffic sourced from the 10.10 100 0/24 network in this scenario, which three statements are correct? (Choose three.)
Your company uses non-Juniper firewalls and you are asked to provide a Juniper solution for zero-day malware protection. Which solution would work in this scenario?
You want to configure a threat prevention policy.
Which three profiles are configurable in this scenario? (Choose three.)
Exhibit

Referring to the exhibit, which two statements are true about the CAK status for the CAK named "FFFP"? (Choose two.)
You are not able to activate the SSH honeypot on the all-in-one Juniper ATP appliance.
What would be a cause of this problem?
Exhibit
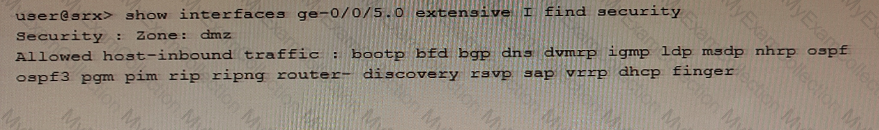
Referring to the exhibit, which three protocols will be allowed on the ge-0/0/5.0 interface? (Choose three.)
You must setup a Ddos solution for your ISP. The solution must be agile and not block legitimate traffic.
Which two products will accomplish this task? (Choose two.)
Exhibit

You configure a traceoptions file called radius on your returns the output shown in the exhibit
What is the source of the problem?
Exhibit
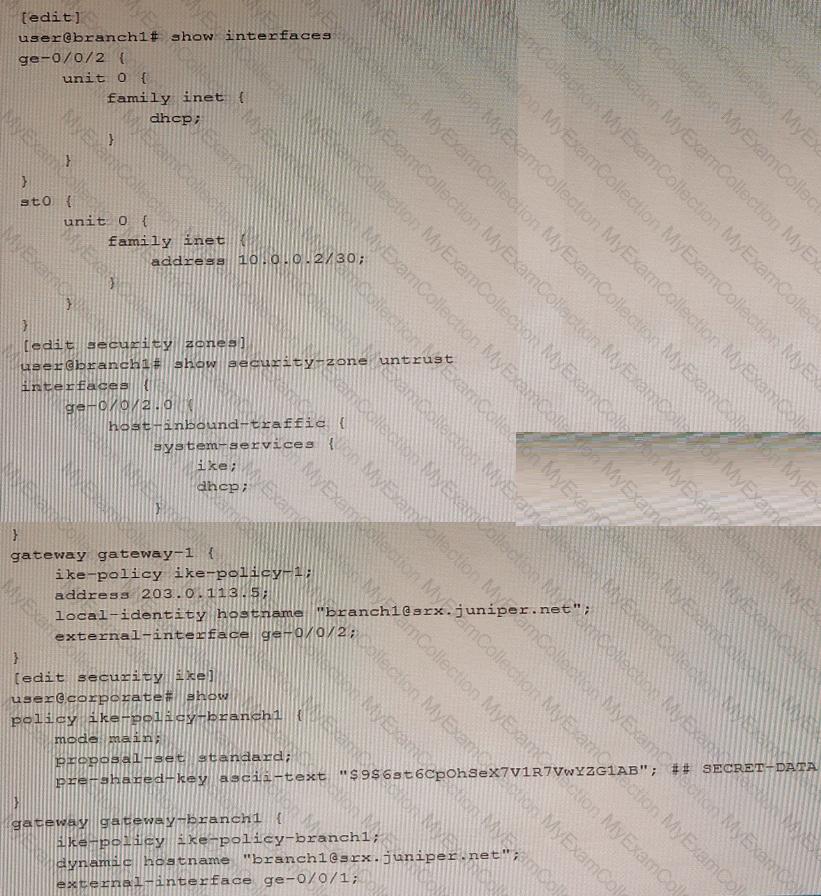
You are trying to configure an IPsec tunnel between SRX Series devices in the corporate office and branch1. You have committed the configuration shown in the exhibit, but the IPsec tunnel is not establishing.
In this scenario, what would solve this problem.
You are configuring transparent mode on an SRX Series device. You must permit IP-based traffic only, and BPDUs must be restricted to the VLANs from which they originate.
Which configuration accomplishes these objectives?
A)

B)

C)

D)
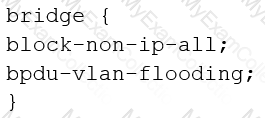
You want traffic to avoid the flow daemon for administrative task.
In this scenario which two stateless service are available with selective stateless packet based service. (Choose Two)
your company wants to take your juniper ATP appliance into private mode. You must give them a list
of impacted features for this request.
Which two features are impacted in this scenario? (Choose two)
Exhibit

You configure Source NAT using a pool of addresses that are in the same subnet range as the external ge-0/0/0 interface on your vSRX device. Traffic that is exiting the internal network can reach external destinations, but the return traffic is being dropped by the service provider router.
Referring to the exhibit, what must be enabled on the vSRX device to solve this problem?
You are required to secure a network against malware. You must ensure that in the event that a
compromised host is identified within the network. In this scenario after a threat has been
identified, which two components are responsible for enforcing MAC-level infected host ?
You have noticed a high number of TCP-based attacks directed toward your primary edge device. You are asked to
configure the IDP feature on your SRX Series device to block this attack.
Which two IDP attack objects would you configure to solve this problem? (Choose two.)
Click the Exhibit button.

When attempting to enroll an SRX Series device to JATP, you receive the error shown in the exhibit. What is the cause of the error?
Exhibit

Referring to the exhibit, which two statements are true? (Choose two.)
Which two additional configuration actions are necessary for the third-party feed shown in the exhibit to work properly? (Choose two.)
What are two important function of the Juniper Networks ATP appliance solution? (Choose two.).
Exhibit

You are not able to ping the default gateway of 192.168 100 1 (or your network that is located on your SRX Series firewall.
Referring to the exhibit, which two commands would correct the configuration of your SRX Series device? (Choose two.)
A)

B)
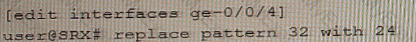
C)

D)

Exhibit
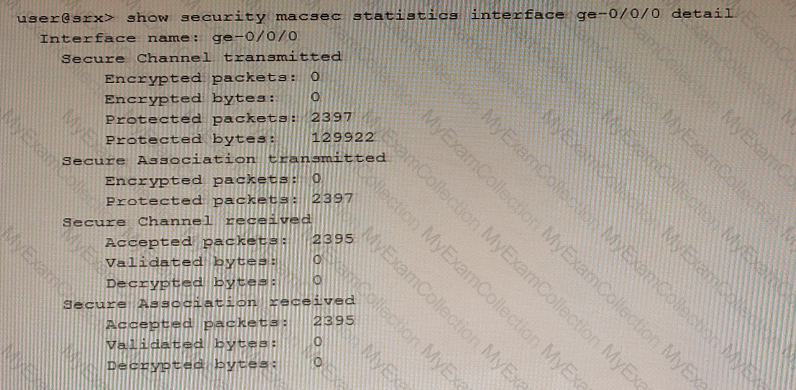
Referring to the exhibit, which two statements are true? (Choose two.)
You want to enable inter-tenant communica􀆟on with tenant system.
In this Scenario, Which two solutions will accomplish this task?
Refer to the exhibit,

which two potential violations will generate alarm ? (Choose Two)
Click the Exhibit button.
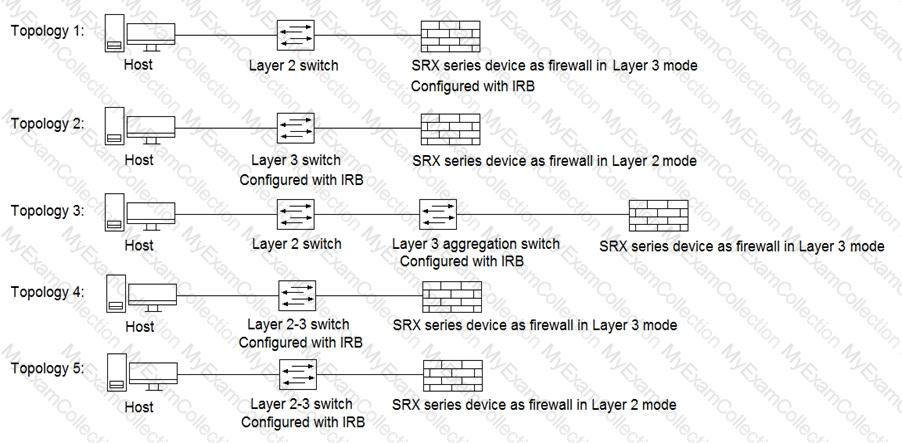
Referring to the exhibit, which three topologies are supported by Policy Enforcer? (Choose three.)


