Exhibit

Referring to the exhibit, what do you determine about the status of the cluster.
Which two statements about SRX Series device chassis clusters are correct? (Choose two.)
Which solution enables you to create security policies that include user and group information?
You are implementing an SRX Series device at a branch office that has low bandwidth and also uses a cloud-based VoIP solution with an outbound policy that permits all traffic.
Which service would you implement at your edge device to prioritize VoIP traffic in this scenario?
You are asked to find systems running applications that increase the risks on your network. You must ensure these systems are processed through IPS and Juniper ATP Cloud for malware and virus protection.
Which Juniper Networks solution will accomplish this task?
You are preparing a proposal for a new customer who has submitted the following requirements for a vSRX deployment:
-- globally distributed,
-- rapid provisioning,
-- scale based on demand,
-- and low CapEx.
Which solution satisfies these requirements?
Exhibit
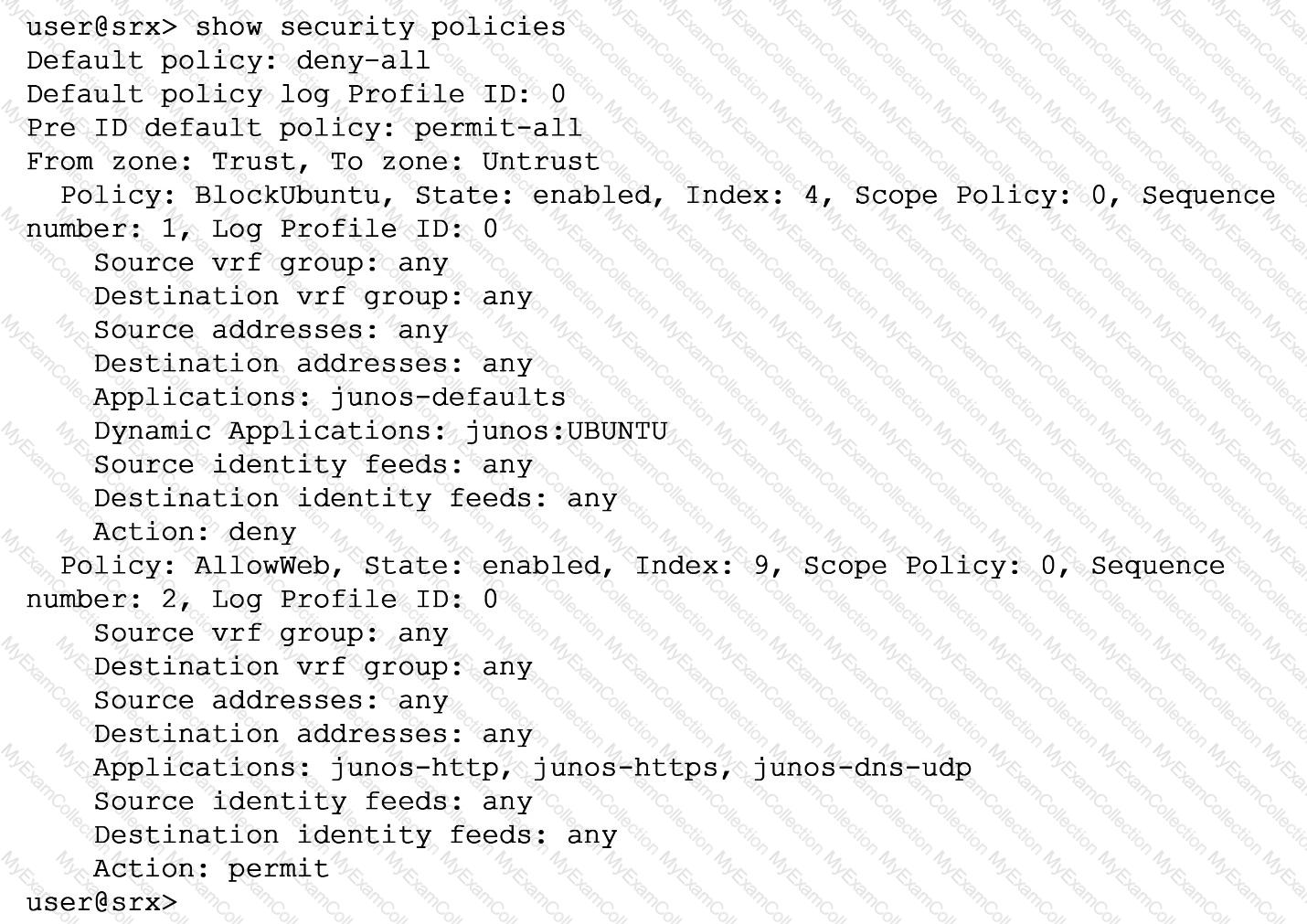
You are asked to ensure that servers running the Ubuntu OS will not be able to update automatically by blocking their access at the SRX firewall. You have configured a unified security policy named Blockuburrtu, but it is not blocking the updates to the OS.
Referring to the exhibit which statement will block the Ubuntu OS updates?
After JSA receives external events and flows, which two steps occur? (Choose two.)
You are asked to implement IPS on your SRX Series device.
In this scenario, which two tasks must be completed before a configuration will work? (Choose two.)
Your company is using the Juniper ATP Cloud free model. The current inspection profile is set at 10 MB You are asked to configure ATP Cloud so that executable files up to 30 MB can be scanned while at the same time minimizing the change in scan time for other file types.
Which configuration should you use in this scenario?
You enable chassis clustering on two devices and assign a cluster ID and a node ID to each device.
In this scenario, what is the correct order for rebooting the devices?
Which two statements about SRX chassis clustering are correct? (Choose two.)
Which two statements are correct about the fab interface in a chassis cluster? (Choose two.)
Exhibit

You just finished setting up your command-and-control (C&C) category with Juniper ATP Cloud. You notice that all of the feeds have zero objects in them.
Which statement is correct in this scenario?
You are configuring logging for a security policy.
In this scenario, in which two situations would log entries be generated? (Choose two.)
Which two statements about SRX Series device chassis clusters are true? (Choose two.)
Which statement regarding Juniper Identity Management Service (JIMS) domain PC probes is true?
Which two sources are used by Juniper Identity Management Service (JIMS) for collecting username and device IP addresses? (Choose two.)
You are asked to ensure that if the session table on your SRX Series device gets close to exhausting its resources, that you enforce a more aggress.ve age-out of existing flows.
In this scenario, which two statements are correct? (Choose two.)
Which statement defines the function of an Application Layer Gateway (ALG)?
Which sequence does an SRX Series device use when implementing stateful session security policies using Layer 3 routes?


