What information is exchanged during a TCP three-way handshake? (Choose two)
Which protocol would you configure to synchronize the time and date on a Junos device?
You want to find out the chassis serial number of a Junos device.
Which command would display this information?
You have just increased the MTU size of interface ge-0/0/0 and committed the configuration.
Which command would help you identify the applied MTU change?
You are asked to convert the number 7 from decimal to binary.
Which number is correct in this scenario?
Click the Exhibit button.
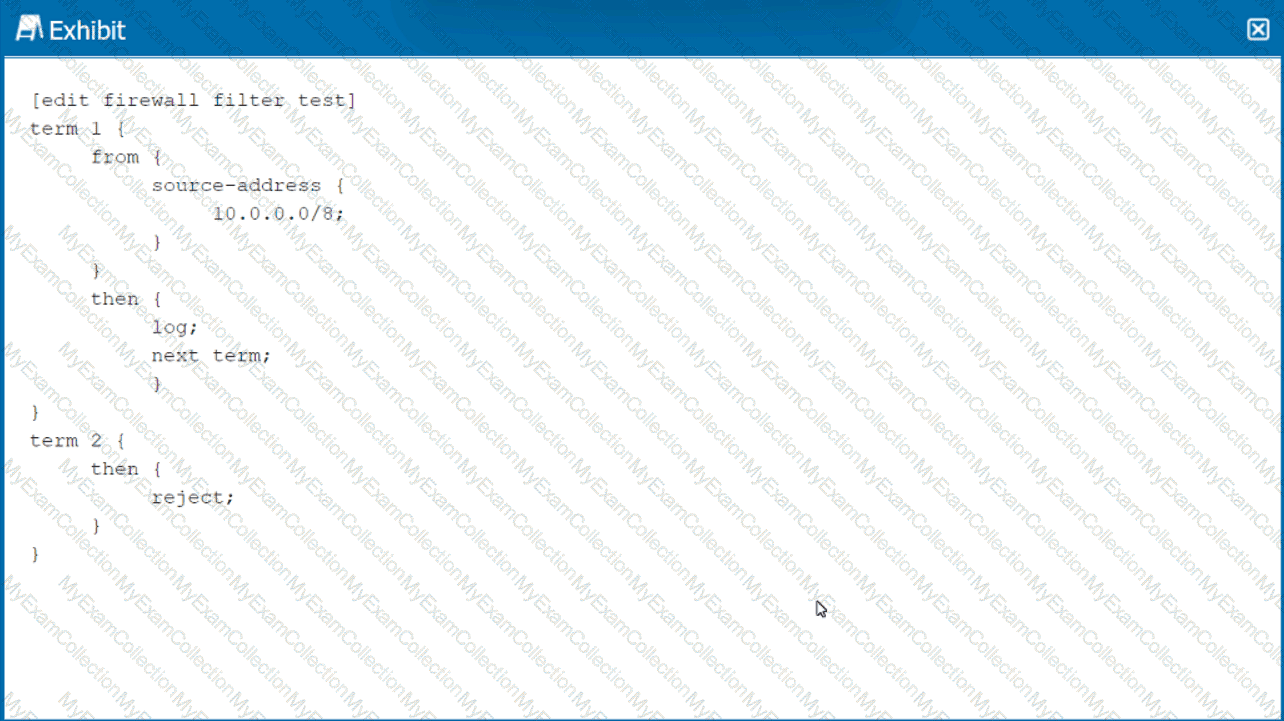
How is traffic, sourced from 10.0.0.0/8, treated by the firewall filter shown in the exhibit?
Which Junos feature limits the amount of exception traffic that is sent from the PFE to the RE?
You have completed the initial configuration of your new Junos device. You want to be able to load this configuration at a later time.
Which action enables you to perform this task?
Which two actions does the configure exclusive command perform? (Choose two.)
Which two statements are correct regarding Layer 2 network switches? (Choose two.)
What are two functions of the routing protocol daemon (rpd)? (Choose two.)
Which two external authentication methods does Junos support for administrative access? (Choose two.)
What is the maximum number of rollback configuration files that the Junos OS will store?
Which Junos OS component is responsible for maintaining the forwarding table?
What are two methods for navigating to configuration mode from an operational mode prompt? (Choose two.)
Which three benefits occur when operating an interior gateway protocol (IGP) in an autonomous system (AS)? (Choose three.)
Which two fields are you required to enter when you create a new user account? (Choose two.)
Which statement is correct when multiple users are configuring a Junos device using the configure private command?
Click the Exhibit button.
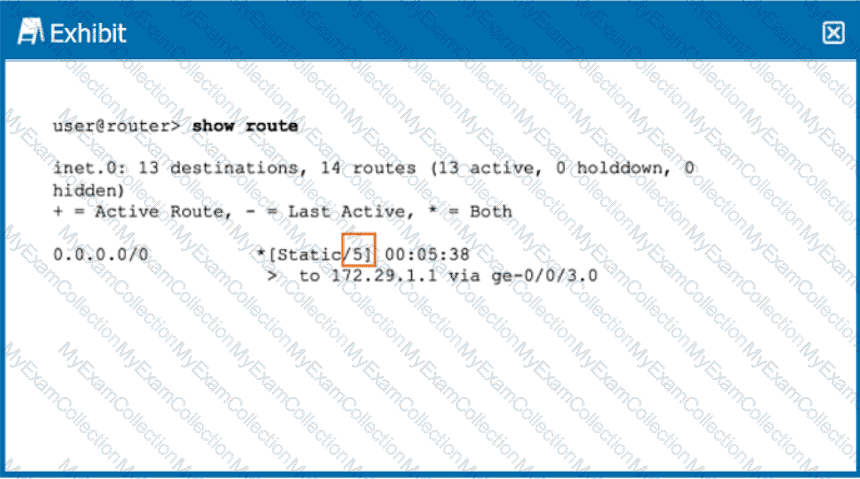
Referring the exhibit, what does the highlighted number indicate?
After the factory default configuration is loaded, which configuration object must be created prior to the first commit?
You are trying to diagnose packet loss at interface ge-0/0/3.
In this scenario, which command would help you view error statistics in real time?
Which two statements describe the result when you enter? at the command-line prompt? (Choose two.)
What are two ways that the carrier-sense multiple access with collision detection (CSMA/CD) MAC protocol helps devices “talk†with each other in an Ethernet network? (Choose two.)

