Which of the following statements about impact of DevOps on testing is CORRECT?
Which of the following statements best describe Behavior-Driven Development (BDD)?
Which ONE of the following options corresponds to an activity in the testing process in which testable features are identified?
Which of the following can be considered a VALID exit criterion?
I Estimates of defect density or reliability measures.
II. The completion and publication of an exhaustive Test Report.
III. Accuracy measures, such as code, functionality or risk coverage.
IV Residual risks such as lack of code coverage in certain areas.
A test manager decided to skip static testing since he believes bugs can be found easily by doing dynamic testing. Was this decision right or wrong?
Which of the following BEST matches the descriptions with the different categories of test techniques?
1.Test cases are based on the test basis which may include the requirements, use cases and user stories
2.Test cases are based on the test basis which may include the software architecture or code
3.Test cases can show deviations from the requirements
4.These test techniques are applicable to both functional and non-functional testing
5.Tests are based on knowledge of developers, users and other stakeholders
Black - Black-box test techniques
White * White-box test techniques
Experience - Experience-based test techniques
The following state diagram is given as basis for state transition testing and contains only valid transitions:
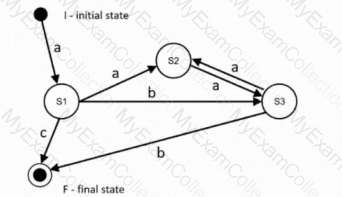
Explanation of the state diagram: States are depicted as nodes. The initial state is I, the final state is F. A state transition is depicted as a directed arrow with the initiating event as a label, e. g. from I to S1 with event a, and is also written as a triple (I,a,S1). Note: A test case is a sequence of events that initiates the corresponding sequence of state transitions.
The state diagram contains the following 7 state transitions:
(I, a, S1)
(S1, a, S2), (S1, b, S3), (S1, c, F)
(S2, a, S3)
(S3, a, S2), (S3, b, F)
What is the minimum number of test cases to achieve 100% coverage of all valid state transitions in the diagram?
Which of the following is a factor that contributes to a successful review?
Which of the following statements refers to good testing practice to be applied regardless of the chosen software development model?
The following state transition diagram describes the functionality involved in a system using fingerprint and password authentication to log onto a system.
How many distinct states of the system are visible in the above diagram?
Which of the following is the most important task of a typical test leader?
The ISTOB glossary defines Quality Assurance as: "Pail or quality management focused on providing confidence that quality requirements will be fulfilled. Which of the following Is not one of the Quality Assurance activity?
In which of the following test documents would you expect to find test exit criteria described9
Which one of the following statements correctly describes the term 'debugging'?
A software module to be used in a mission critical application incorporates an algorithm for secure transmission of data.
Which review type is most appropriate to ensure high quality and technical correctness of the algorithm?
Your organization's test strategy states that it is desirable to use more than one method for estimating test effort. You are responsible for estimating test effort for the next project. Based on historical data, the development-to-test effort ratio is 5:3.
The initial estimate for the development effort is 450 person-days.
Which ONE of the following options corresponds to the estimated test effort using the ratio-based method?
Consider a given test plan which, among others, contains the following three sections: "Test Scope", "Testing Communication", and "Stakeholders". The features of the test object to be tested and those excluded from the testing represent information that is:
Given the following statements:
1.It can prevent defects by manual examination of the functional specification
2.It is effective since it can be performed very early in the software development life cycle
3.It can detect the failures in the running application
4.It can help eliminate defects in user stories
5.It can verify externally visible behaviors
Which set of statements represent values ONLY for static testing?
Which of the following statements best describes an advantage of the whole team approach?
A test manager defined the following test levels in her test plan; Component, System and Acceptance.
Which Software Development lifecycle is the Test Manager most likely following?
Which of the following statements are true?
1. Early and frequent feedback helps to avoid requirements misunderstanding.
2. Early feedback allows teams to do more with less.
3. Early feedback allows the team to focus on the most Important features.
4. Early and frequent feedback clarifies customer feedback by applying static testing techniques
Select the correct answer:
For a given set of test-cases, which of the following is a benefit of running these tests with a test automation tool?
Which of the following statements best describes the difference between product risk and project risk in software testing?
Given some statements about independence of testing
i. Independence is a replacement for familiarity with the code
ii. Independence helps remove the biases produced because of own work
iii. Similar kind of failures can be detected by anyone
iv Assumptions by different people are different revealing weaknesses
Which of the following CORRECTLY represents the benefits?
Which ONE of the following roles is responsible for mediating, managing time, and generating a safe review environment in which everyone can speak freely?
The following rules determine the annual bonus to be paid to a salesman of a company based on the total annual amount of the sales made (referred to as TAS).
If the TAS is between 50k€ and 80k€, the bonus is 10%. If the TAS exceeds 80k€ by a value not greater than 40k€, the bonus is 15%. Finally, if the TAS
exceeds the maximum threshold which entitles to a 15% bonus, the bonus is 22%.
Consider applying equivalence partitioning to the TAS (Note: 1k€ = 1000 euros).
Which one of the following answers contain only test cases that belong to the same equivalence partition?
During which main group of test activity are the following tasks performed?
•Checking test results and logs against specified coverage criteria.
•Assessing the level of component or system quality based on test results and logs.
•Determining whether more tests are needed.
Select the correct answer:
An agile software development organization has recently hired a senior tester. The organization has distributed teams spread across time zones. They need to share test status with various stakeholders including upper management and customers at a regular interval. Which of the following statements seems to be correct with regards to the communication?
The following open incident report provided:
Date: 01.01.01
Description: When pressing the stop button the application status remain in "Attention" instead of "Ready'.
Severity: High
Life Cycle: Integration
Which of the following details are missing in the giving incident report?
I. Identification or configuration of the application
II. The name of the developer
III. Recommendation of the developer
IV The actions and/or conditions that came before the pressing of the button
In branch testing, what is the significance of a conditional branch in a software program?
Which of the following project scenario gives the BEST example where maintenance testing should be triggered?
Which ONE of the following elements is TYPICALLY NOT part of a test progress report?
During component testing of a program if 100% decision coverage is achieved, which of the following coverage criteria is also guaranteed to be 100%?
Your manager asked you when testing will be complete. In order to answer this question, you'll most likely use:
Which of the following statements about test activities that form the overall test process is correct?
Which of the following statements regarding the test-first approach (principle of early testing) is true?
Which of the following statements describes regression testing?
I. Retesting of a fixed defect
II. Testing of an already tested program
III. Testing of new functionality in a program
IV. Regression testing applies only to functional testing
V Tests that do not nave to be repeatable, because They are only used once
You are testing the download process of a mobile phone application.
For which to the following capabilities to the system you need to design a nonfunctional test?
In Agile teams, testers closely collaborate with all other team members. This close collaboration could be problematic and result in testing-related organizational risks.
Which TWO of the following organization risks could be encountered?
I.Testers lose motivation and fail at their core tasks.
ii.Close interaction with developers causes a loss of the appropriate tester mindset.
iii.Testers are not able to keep pace with incoming changes in time-constrained iterations.
iv.Testers, once they have acquired technical development or business skills, leave the testing team.
Which of the following statements best describes the value of maintaining traceability in software testing?
A new web app aims at offering a rich user experience. As a functional tester, you have run some functional tests to verify that, before releasing the app, such app works correctly on several mobile devices, all of which are listed as supported devices within the requirements specification. These tests were performed on stable and isolated test environments where you were the only user interacting with the application. All tests passed, but in some of those tests you observed the following issue: on some mobile devices only, the response time for two web pages containing images was extremely slow.
Based only on the given information, which of the following recommendation would you follow?
Which of the following statements about re-testing and regression testing are TRUE?
I Re-testing should be performed after a defect is fixed.
II Regression testing should always be performed after a defect is fixed.
III. Re-testing and regression testing may be performed at any test level.
IV Regression testing may include functional, non-functional and structural testing.
V. Re-testing should be included in the debugging activity.
Which of the following statements refers to a good testing practice that applies to all software development lifecycles?
A mid-size software product development company has analyzed data related to defects detected in its product and found out that detects fixed in earlier builds are getting re-opened after a few months.
The company management now seeks your advice in order to reverse this trend and prevent re-opening of defects fixed earlier.
What would be your FIRST recommendation to the company?
Which ONE of the following options BEST describes the purpose of confirmation testing versus regression testing?
Which ONE of the following options BEST describes black-box test techniques?
Which statement is true regarding confirmation testing and regression testing?
Consider the following iteration planning tasks where a tester can provide value:
Break down user stories into tasks (particularly testing tasks)
Estimate test effort for all testing tasks
Identify and refine functional and non-functional aspects of the test object
Which ONE of the following tasks should be ADDED to the above list?
Use Scenario 1 “Happy Tomatoes†(from the previous question).
When running test case TC_59, the actual result for t = 35 degrees Celsius is OUTPUT = X instead of the expected output.
Which information should NOT be included in the defect report?
A Static analysis tool analyzes a given program's CONTROL FLOW among other things. Which of the following options represents the most likely outcome of the control flow analysis:
Consider the following examples of risks identified in different software development projects
[1]. It may not be possible to generate the expected workloads to run performance tests, due to the poor hardware equipment of the machines (load injectors) that should generate these workloads.
[ii]. A user's session on a web application is not invalidated after a certain period of inactivity (configured by the system administrator) of the user,
[iii]. The test team will not have an adequate requirements specification (since many requirements will still be missing) by the time test design and analysis activities should begin according to the test plan.
[IV]. Following a failure, the system is unable to continue to maintain its pre-failure operation and some data becomes corrupted.
Which of the following statements is TRUE?
The following table shows six test cases TC01 to TC06 with their priorities and dependencies.
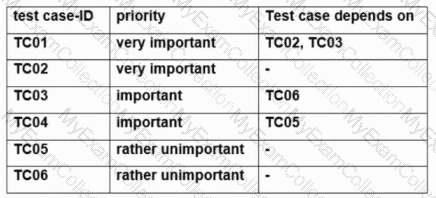
Schedule the test execution of the specified test case set according to the priorities and dependencies. Since the test time is very tight, the number of test cases should be minimized as much as possible, but all very important test cases must be included.
Which of the following statements is correct?
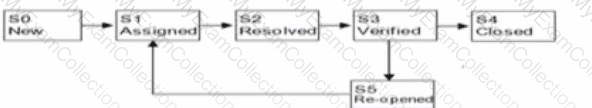
Which sequence of stated in the answer choices is correct in accordance with the following figure depicting the life-cycle of a defect?
Consider a review for a high-level architectural document written by a software architect. The architect does most of the review preparation work, including distributing the document to reviewers before the review meeting. However, reviewers are not required to analyze the document in advance, and during the review meeting the software architect explains the document step by step. The only goal of this review is to establish a common understanding of the software architecture that will be used in a software development project.
Which of the following review types does this review refer to?
Given the following User Story: "As an online customer, I would like to be able to cancel the purchase of an individual item from a shopping list so that it only displays the relevant items, in less than 1 second", which of the following can be considered as applicable acceptance test cases?
I.Click on my online shopping list, select the unwanted Item, delete the unwanted item, the unwanted Item is deleted from the shopping list in less than 1 second.
ii.Click on my online shopping list, select all the items, delete all the items, the unwanted items are deleted from the shopping list in less than 1 second.
iii.Tab to the online shopping list and press enter, select the unwanted item, delete the unwanted item, the unwanted item is deleted from the shopping list In less than 1 second.
Iv. Click on the checkout button, select the payment method, make payment, confirmation received of payment and shipping date.
v. Click on my shopping list, select the unwanted Item, delete the unwanted item, the unwanted item is deleted from the shopping list.
Select the correct answer:
Which of the following is the main difference between quality assurance (QA) and quality control
Which of the statements correctly describes when a whole team approach may NOT be suitable?
Which of the following tasks is MOST LIKELY to be performed by the tester?
You are responsible for applying the correct technique for a review of the requirements document for a project to develop a new software application. You identify the reviewers and the required roles, including the meeting leader, who is the requirements document author, and a separate role for a scribe. Additionally, you decide to take a relatively informal approach to the requirements review. The goal of the review is to find defects in the requirements document, such as omissions, Inconsistencies, and duplications. Another goal of the review is to improve the software application's usability and accessibility by considering the various stakeholders' viewpoints.
Which of the following statements BEST describes this scenario?
Consider an estimation session in which a six-member Agile team (Memb1..... Memb6) uses the planning poker technique to estimate a user story (in story points). The team members will use a set of cards with the following values: 1,2, 3,5, 8,13,21. Below is the outcome of the first round of estimation for this session:
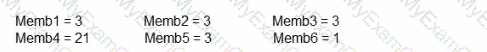
Which of the following answers BEST describes how the estimation session should proceed?
Which of the following statements about decision tables are TRUE?
I. Generally, decision tables are generated for low risk test items.
II. Test cases derived from decision tables can be used for component tests.
III. Several test cases can be selected for each column of the decision table.
IV. The conditions in the decision table represent negative tests generally.
Which of the following statements about testing in the context of an agile (iterative-incremental) development model is correct?
As a tester, as part of a V-model project, you are currently executing some tests aimed at verifying if a mobile app asks the user to grant the proper access permissions during the installation process and after the installation process. The requirements specification states that in both cases the app shall ask the user to grant access permissions only to the camera and photos stored on the device. However, you observe that the app also asks the user to grant access permission to all contacts on the device. Consider the following items:
[I]. Test environment
[ii]. Expected result
[iii]. Actual result.
[IV] Test level.
[V]. Root cause.
Based on only the given information, which of the items listed above, are you able to CORRECTLY specify in a defect report?
Which of the following statements is an example of testing contributing to higher quality?
Which of the following statements does NOT describe good testing practice, regardless of the SDLC chosen?
A team's test strategy was to invest equal effort in testing each of a system's modules. After running one test cycle, it turned out that most of the critical bugs were detected in one of the system's modules.
Which testing principal suggests a change to the current test strategy for the next test cycle?
Which of the following activities are part of test planning?
I) Setting the entry and exit criteria
II) Determining the validity of bug reports
III) Determining the number of resources required
IV) Determining the expected result for test cases
For withdrawing money tram an Automated Teller Machine (ATM), the following conditions are required:
- The bank card is valid
- The PIN code is correct
- Money is available in the user's account
The following are some possible interactions between the user and the ATM:
- The entered card is invalid The card is rejected
- The PIN code is wrong The ATM asks for another PIN code
- The requested amount is more than available in the user's account: The ATM asks for another amount
- The requested amount is available in the user's account The ATM dispenses the money
Which test design technique should be used to cover all possible combinations of the in put conditions?
Which of the following statements best describes the way in which decision coverage is measured?
Determining the schedule for each testing activity and test milestones for a test project, using activity estimates, available resources, and other constraints is a typical task performed during
Which of the following is a CORRECT statement about how a tester should communicate about defects, test results, and other test information?
Which of the following is not an example of a typical generic skill required for testing?
Which of the following metrics relates to the number of defects per unit size of a work product?
To be able to define testable acceptance criteria, specific topics need to be addressed. In the table below are the topics matched to an incorrect description. Match the topics (the left column) with the correct description (the right column)
TopicDescription
Which of the following options should NOT be used for writing acceptance criteria?
Which one of the following statements IS NOT a valid objective of testing?
Which of the following BEST describes a test summary report for executive-level employees
You are testing an e-commerce system that sporadically fails to properly manage customers' shopping carts. You have stressed the urgency of this situation to the development manager and development team and they recognize the priority of resolving the underlying defect. The development team is waiting for more information, which you will include in your defect report. Given the following items of information they are included in a typical defect report:
1. The expected results
2. The actual results
3. The urgency and priority to fix this
4. The date and author of the defect report
5. A description of the defect in order to reproduce, including screenshots and database dumps
Which of these items will be MOST useful to the developers to help them identify and remove the defect causing this failure?
Which ONE of the following options identifies the perspectives through which a collective authorship process generates a shared vision of user stories?
Which of the following best describes the relationship between a test progress report and a test summary report?
Testing Quadrants, as a model, is effective in aligning stakeholders within Agile teams.
Which of the following examples demonstrates this?
Which of the following is not an example of a typical content of a test completion report for a test project?
While repotting a defect, which attribute indicates the degree of impact that the defect has on the system?
Which of the following would be the LEAST likely to be used as the basis for a test exit criteria?
Which of the following is the BEST reason for selecting a particular type of software development lifecycle model?
For each of the test cases to be executed, the following table specifies the priority order and dependencies on other test cases
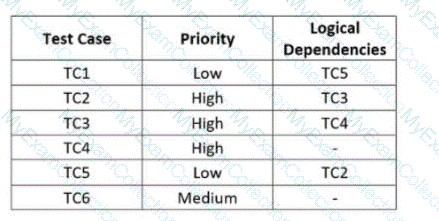
Which of the following test execution schedules is compatible with the logical dependencies and allows executing the test cases in priority order?
Given the following state model of sales order software:
PLACED -> IN PRODUCTION
IN PRODUCTION -> CANCELLED
IN PRODUCTION -> SHIPPED
SHIPPED -> INVOICED
INVOICED -> CANCELLED
CANCELLED -> PLACED
Which of the following sequences of tran-sitions provides the highest level of tran-sition coverage for the model (assuming you can start in any state)?
Which of the statements on confirmation testing and regression testing is correct?
Which of the following types of bugs are more likely to be found by static testing then by dynamic testing?
A program is used to control a manufacturing line (turn machines on and off. start and stop conveyer belts, add raw materials to the flow. etc.). Not all actions are possible at all times. For example, there are certain manufacturing stages that cannot be stopped - unless there is an emergency. A tester attempts to evaluate if all such cases (where a specific action is not allowed) are covered by the tests.
Which coverage metric will provide the needed information for this analysis?
Given the following review process main activities and specific review activities:
a.Planning
b.Initiate review
c.Issue communication and analysis
d.Fixing and reporting
1.Creating defect reports
2.Estimating effort and timeframe
3.Recording updated status of defects
4.Selecting the people to participate
5.Distributing the work product and other material
6.Evaluating the review findings
Which of the following BEST matches the review process main activities with the appropriate specific review activities?


