Match each PoE power class to Its corresponding 802.3 standard. (Options may he used more than once or not at all)

What are two advantages of splitting a larger OSPF area into a number of smaller areas? (Select two )
Which Aruba AP mode is sending captured RF data to Aruba Central for waterfall plot?
How do you allow a new VLAN 100 between VSX pair inter-switch-link 256 for port 1/45 and 2/45?
You need to have different routing-table requirements with Aruba CX 6300 VSF configuration
Assuming the correct layer-2 VLAN already exists how would you create a new OSPF configuration for a separate routing table?
A large retail client is looking to generate a rich set of contextual data based on the location information of wireless clients in their stores Which standard uses Round Trip Time (RTT) and Fine Time Measurements (FTM) to calculate the distance a client is from an AP?
Which statements are true regarding a VXLAN implementation on Aruba Switches? (Select two.)
You are proposing new CX 8360 VSX switches to replace a customer's existing core switches. The customer is concerned about the possibility of a split-brain scenario between the VSX pair.
How is the VSX pair affected when the ISL is down and keepalive is up?
A company recently upgraded its campus switching infrastructure with Aruba 6300 CX switches. They have implemented 802.1X authentication on edge ports where laptop and loT devices typically connect An administrator has noticed that for PoE devices the pons are delivering the maximum wattage instead of what the device actually needs Upon connecting the loT devices, the devices request their specific required wattage through information exchange
You are deploying Aruba CX 6300's with the customers requirement to only allow one (1) VoIP phone and one (1) device.
The following local role gets assigned to the phone
port-access rote VoIP device-traffic-class voice
What set of commands best fits this requirement?
A customer wants to enable wired authentication across all their CX switches One of the requirements is that the switch must be able to authenticate a single computer connected through a VoIP phone.
Which feature should be enabled to support this requirement?
A customer is looking Tor a wireless authentication solution for all of their loT devices that meet the following requirements
- The wireless traffic between the IoT devices and the Access Points must be encrypted
- Unique passphrase per device
- Use fingerprint information to perform role-based access
Which solutions will address the customer's requirements? (Select two.)
Your manufacturing client is deploying two hundred wireless IP cameras and fifty headless scanners in their warehouse. These new devices do not support 802.1X authentication.
How can HPE Aruba enhance security for these new IP cameras in this environment?
How is Dynamic Multicast Optimization (DMO) implemented in an HPE Aruba wireless network?
You are setting up a customer's 15 headless loT devices that do not support 802.1X. What should you use?
A customer just upgraded aggregation layer switches and noticed traffic dropping for 120 seconds after the aggregation layer came online again. What is the best way to avoid having this traffic dropped given the topology below?
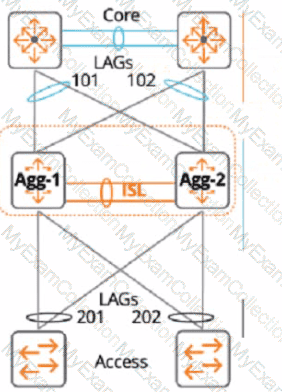
A customer is using a legacy application that communicates at layer-2. The customer would like to keep this application working across the campus which is connected via layer-3. The legacy devices are connected to Aruba CX 6300 switches throughout the campus.
Which technology minimizes flooding so the legacy application can work efficiently?
You must ensure the HPEAruba network you are configuring for a client is capable of plug-and-play provisioning of access points. What enables this capability?
You are working on a network where the customer has a dedicated router with redundant Internet connections Tor outbound high-importance real-time audio streams from their datacenter All of this traffic.
• originates from a single subnet
• uses a unique range of UDP ports
• is required to be routed to the dedicated router
All other traffic should route normally The SVI for the subnet containing the servers originating the traffic is located on the core routing switch in the datacenter What should be configured?
With the Aruba CX 6200 24G switch with uplinks or 1/1/25 and 1/1/26, how do you protect client ports from forming layer-2 loops?
Your manufacturing client is having installers deploy seventy headless scanners and fifty IP cameras in their warehouse These new devices do not support 802 1X authentication.
How can HPE Aruba reduce the IT administration overhead associated with this deployment while maintaining a secure environment using MPSK?
What is the order of operations tor Key Management service for a wireless client roaming from AP1 to AP2?
Which statements regarding 0SPFv2 route redistribution are true for Aruba OS CX switches? (Select two.)
What is the best practice for handling voice traffic with dynamic segmentation on AOS-CX switches?
For the Aruba CX 6400 switch, what does virtual output queueing (VOQ) implement that is different from most typical campus switches?
Your customer is having issues with Wi-Fi 6 clients staying connected to poor-performing APs when a higher throughput APs are closer. Which technology should you implement?
With the Aruba CX 6000 24G switch with uplinks of 1/1/25 and what does the switch do when a client port detects a loop and the do-not-disabie parameter is used?
What steps are part of the Key Management workflow when a wireless device is roaming from AP1 to AP2? (Select two.)
A customer wants to provide wired security as close to the source as possible The wired security must meet the following requirements:
-allow ping from the IT management VLAN to the user VLAN
-deny ping sourcing from the user VLAN to the IT management VLAN
The customer is using Aruba CX 6300s
What is the correct way to implement these requirements?
Your customer currently has Iwo (2) 5406 modular switches with MSTP configured as their core switches. You are proposing a new solution. What would you explain regarding the Aruba CX VSX switch pair when the Primary VSX node is replaced and the system MAC is replaced?
With Aruba CX 6300. how do you configure ip address 10 10 10 1 for the interface in default state for interface 1/1/1?
You are troubleshooting an issue with a pair of Aruba CX 8360 switches configured with VSX Each switch has multiple VRFs. You need to find the IP address of a particular client device with a known MAC address You run the "show arp" command on the primary switch in the pair but do not find a matching entry for the client MAC address.
The client device is connected to an Aruba CX 6100 switch by VSX LAG.
Which action can be used to find the IP address successfully?
A)

B)

C)

D)

Which standard supported by some Aruba APs can enable a customer to accurately locate wireless client devices within a few meters?
You are helping an onsite network technician bring up an Aruba 9004 gateway with ZTP for a branch office The technician was to plug in any port for the ZTP process to start Thirty minutes after the gateway was plugged in new users started to complain they were no longer able to get to the internet. One user who reported the issue stated their IP address is 172.16 0.81 However, the branch office network is supposed to be on 10.231 81.0/24.
What should the technician do to alleviate the issue and get the ZTP process started correctly?
you need to have different routing-table requirements With Aruba CX 6300 VSF configuration.
Assuming the correct layer-2 VLAN already exists, how would you create a new SVI for a separate routing table?




