Refer to the scenario.
A customer has an Aruba ClearPass cluster. The customer has AOS-CX switches that implement 802.1X authentication to ClearPass Policy Manager (CPPM).
Switches are using local port-access policies.
The customer wants to start tunneling wired clients that pass user authentication only to an Aruba gateway cluster. The gateway cluster should assign these clients to the “eth-internet" role. The gateway should also handle assigning clients to their VLAN, which is VLAN 20.
The plan for the enforcement policy and profiles is shown below:

The gateway cluster has two gateways with these IP addresses:
• Gateway 1
o VLAN 4085 (system IP) = 10.20.4.21
o VLAN 20 (users) = 10.20.20.1
o VLAN 4094 (WAN) = 198.51.100.14
• Gateway 2
o VLAN 4085 (system IP) = 10.20.4.22
o VLAN 20 (users) = 10.20.20.2
o VLAN 4094 (WAN) = 198.51.100.12
• VRRP on VLAN 20 = 10.20.20.254
The customer requires high availability for the tunnels between the switches and the gateway cluster. If one gateway falls, the other gateway should take over its tunnels. Also, the switch should be able to discover the gateway cluster regardless of whether one of the gateways is in the cluster.
You are setting up the UBT zone on an AOS-CX switch.
Which IP addresses should you define in the zone?
Refer to the scenario.
A customer is migrating from on-prem AD to Azure AD as its sole domain solution. The customer also manages both wired and wireless devices with Microsoft Endpoint Manager (Intune).
The customer wants to improve security for the network edge. You are helping the customer design a ClearPass deployment for this purpose. Aruba network devices will authenticate wireless and wired clients to an Aruba ClearPass Policy Manager (CPPM) cluster (which uses version 6.10).
The customer has several requirements for authentication. The clients should only pass EAP-TLS authentication if a query to Azure AD shows that they have accounts in Azure AD. To further refine the clients’ privileges, ClearPass also should use information collected by Intune to make access control decisions.
Assume that the Azure AD deployment has the proper prerequisites established.
You are planning the CPPM authentication source that you will reference as the authentication source in 802.1X services.
How should you set up this authentication source?
Several AOS-CX switches are responding to SNMPv2 GET requests for the public community. The customer only permits SNMPv3. You have asked a network admin to fix this problem. The admin says, “I tried to remove the community, but the CLI output an error.â€
What should you recommend to remediate the vulnerability and meet the customer’s requirements?
A company has Aruba gateways that are Implementing gateway IDS/IPS in IDS mode. The customer complains that admins are receiving too frequent of repeat email notifications for the same threat. The threat itself might be one that the admins should investigate, but the customer does not want the email notification to repeat as often.
Which setting should you adjust in Aruba Central?
A customer has an AOS 10-based mobility solution, which authenticates clients to Aruba ClearPass Policy Manager (CPPM). The customer has some wireless devices that support WPA2 in personal mode only.
How can you meet these devices’ needs but improve security?
You want to use Device Insight tags as conditions within CPPM role mapping or enforcement policy rules.
What guidelines should you follow?
Refer to the scenario.
# Introduction to the customer
You are helping a company add Aruba ClearPass to their network, which uses Aruba network infrastructure devices.
The company currently has a Windows domain and Windows CA. The Window CA issues certificates to domain computers, domain users, and servers such as domain controllers. An example of a certificate issued by the Windows CA is shown here.


The company is in the process of adding Microsoft Endpoint Manager (Intune) to manage its mobile clients. The customer is maintaining the on-prem AD for now and uses Azure AD Connect to sync with Azure AD.
# Requirements for issuing certificates to mobile clients
The company wants to use ClearPass Onboard to deploy certificates automatically to mobile clients enrolled in Intune. During this process, Onboard should communicate with Azure AD to validate the clients. High availability should also be provided for this scenario; in other words, clients should be able to get certificates from Subscriber 2 if Subscriber 1 is down.
The Intune admins intend to create certificate profiles that include a UPN SAN with the UPN of the user who enrolled the device.
# Requirements for authenticating clients
The customer requires all types of clients to connect and authenticate on the same corporate SSID.
The company wants CPPM to use these authentication methods:
 EAP-TLS to authenticate users on mobile clients registered in Intune
EAP-TLS to authenticate users on mobile clients registered in Intune
 TEAR, with EAP-TLS as the inner method to authenticate Windows domain computers and the users on them
TEAR, with EAP-TLS as the inner method to authenticate Windows domain computers and the users on them
To succeed, EAP-TLS (standalone or as a TEAP method) clients must meet these requirements:
 Their certificate is valid and is not revoked, as validated by OCSP
Their certificate is valid and is not revoked, as validated by OCSP
 The client’s username matches an account in AD
The client’s username matches an account in AD
# Requirements for assigning clients to roles
After authentication, the customer wants the CPPM to assign clients to ClearPass roles based on the following rules:
 Clients with certificates issued by Onboard are assigned the “mobile-onboarded†role
Clients with certificates issued by Onboard are assigned the “mobile-onboarded†role
 Clients that have passed TEAP Method 1 are assigned the “domain-computer†role
Clients that have passed TEAP Method 1 are assigned the “domain-computer†role
 Clients in the AD group “Medical†are assigned the “medical-staff†role
Clients in the AD group “Medical†are assigned the “medical-staff†role
 Clients in the AD group “Reception†are assigned to the “reception-staff†role
Clients in the AD group “Reception†are assigned to the “reception-staff†role
The customer requires CPPM to assign authenticated clients to AOS firewall roles as follows:
 Assign medical staff on mobile-onboarded clients to the “medical-mobile†firewall role
Assign medical staff on mobile-onboarded clients to the “medical-mobile†firewall role
 Assign other mobile-onboarded clients to the “mobile-other†firewall role
Assign other mobile-onboarded clients to the “mobile-other†firewall role
 Assign medical staff on domain computers to the “medical-domain†firewall role
Assign medical staff on domain computers to the “medical-domain†firewall role
 All reception staff on domain computers to the “reception-domain†firewall role
All reception staff on domain computers to the “reception-domain†firewall role
 All domain computers with no valid user logged in to the “computer-only†firewall role
All domain computers with no valid user logged in to the “computer-only†firewall role
 Deny other clients access
Deny other clients access
# Other requirements
Communications between ClearPass servers and on-prem AD domain controllers must be encrypted.
# Network topology
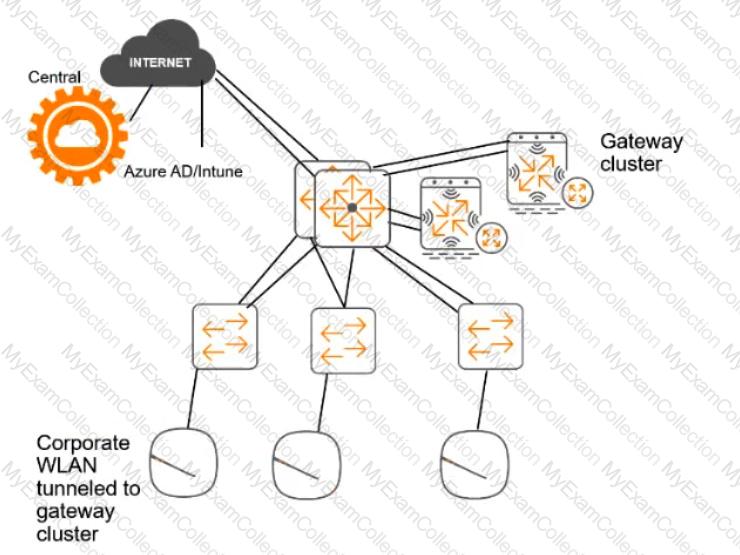
For the network infrastructure, this customer has Aruba APs and Aruba gateways, which are managed by Central. APs use tunneled WLANs, which tunnel traffic to the gateway cluster. The customer also has AOS-CX switches that are not managed by Central at this point.
# ClearPass cluster IP addressing and hostnames
A customer’s ClearPass cluster has these IP addresses:
 Publisher = 10.47.47.5
Publisher = 10.47.47.5
 Subscriber 1 = 10.47.47.6
Subscriber 1 = 10.47.47.6
 Subscriber 2 = 10.47.47.7
Subscriber 2 = 10.47.47.7
 Virtual IP with Subscriber 1 and Subscriber 2 = 10.47.47.8
Virtual IP with Subscriber 1 and Subscriber 2 = 10.47.47.8
The customer’s DNS server has these entries
 cp.acnsxtest.com = 10.47.47.5
cp.acnsxtest.com = 10.47.47.5
 cps1.acnsxtest.com = 10.47.47.6
cps1.acnsxtest.com = 10.47.47.6
 cps2.acnsxtest.com = 10.47.47.7
cps2.acnsxtest.com = 10.47.47.7
 radius.acnsxtest.com = 10.47.47.8
radius.acnsxtest.com = 10.47.47.8
 onboard.acnsxtest.com = 10.47.47.8
onboard.acnsxtest.com = 10.47.47.8
The customer has now decided that it needs CPPM to assign certain mobile-onboarded devices to a “nurse-call†AOS user role. These are mobile-onboarded devices that are communicating with IP address 10.1.18.12 using port 4343.
What are the prerequisites for fulfilling this requirement?
Refer to the scenario.
An organization wants the AOS-CX switch to trigger an alert if its RADIUS server (cp.acnsxtest.local) rejects an unusual number of client authentication requests per hour. After some discussions with other Aruba admins, you are still not sure how many rejections are usual or unusual. You expect that the value could be different on each switch.
You are helping the developer understand how to develop an NAE script for this use case.
You are helping the developer find the right URI for the monitor.
Refer to the exhibit.
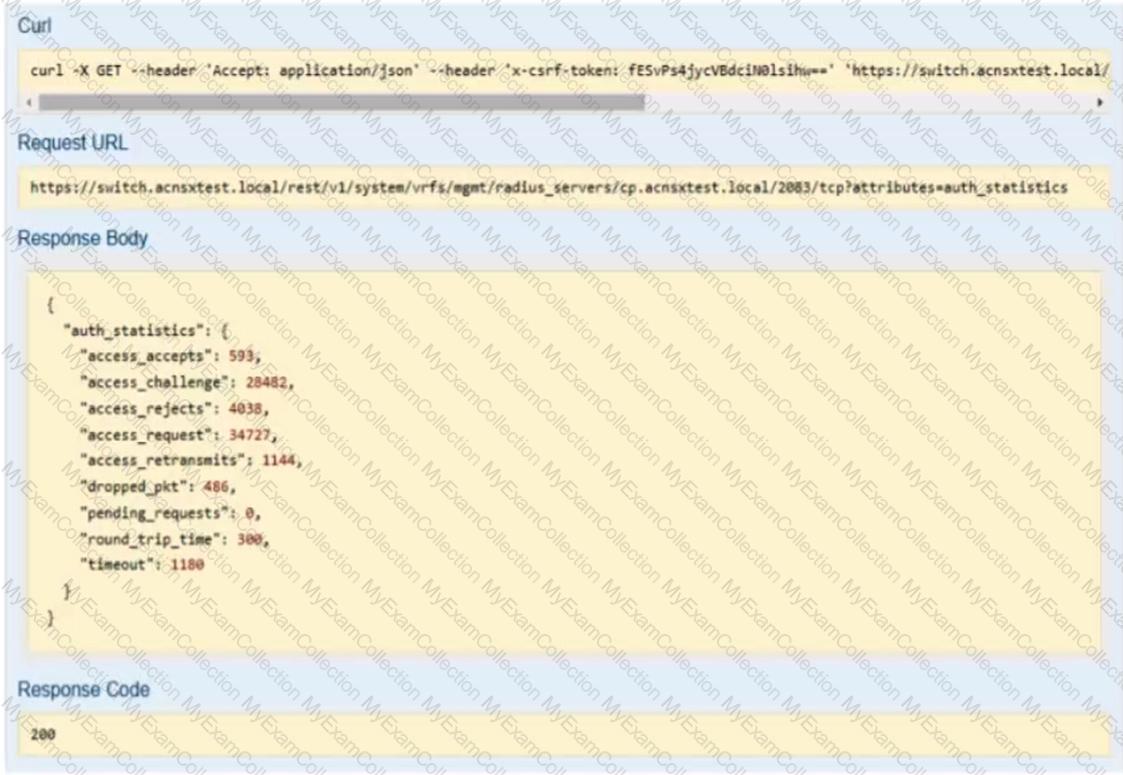
You have used the REST API reference interface to submit a test call. The results are shown in the exhibit.
Which URI should you give to the developer?
A company has an Aruba ClearPass server at 10.47.47.8, FQDN radius.acnsxtest.local. This exhibit shows ClearPass Policy Manager's (CPPM's) settings for an Aruba Mobility Controller (MC).
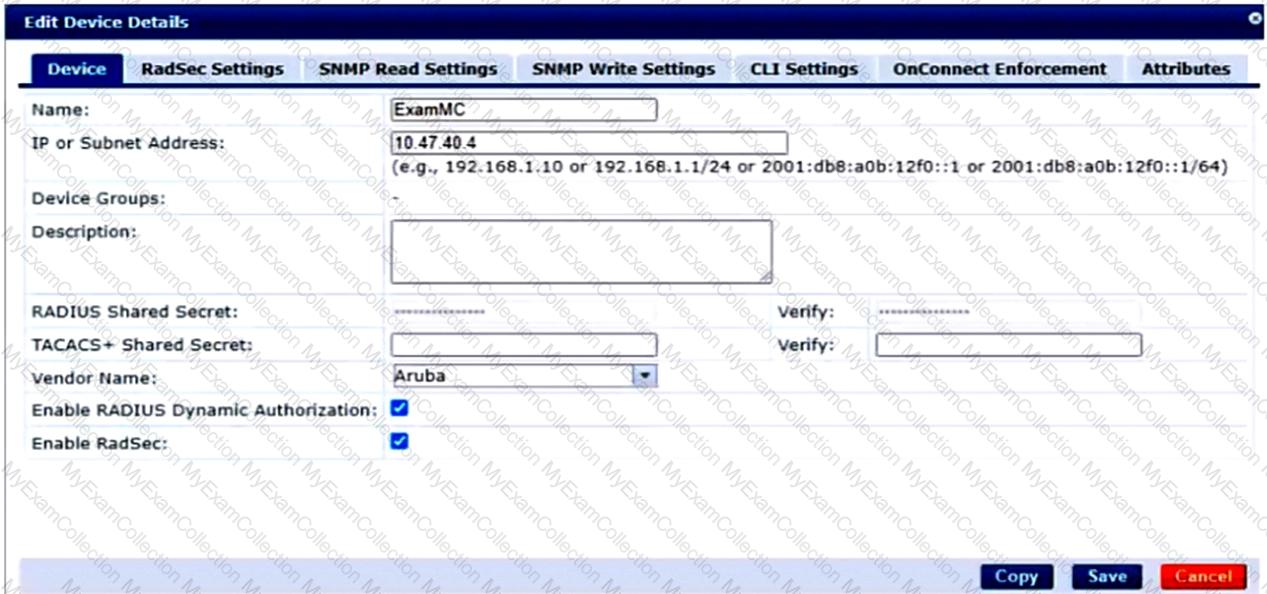
The MC is already configured with RADIUS authentication settings for CPPM, and RADIUS requests between the MC and CPPM are working. A network admin enters and commits this command to enable dynamic authorization on the MC:
aaa rfc-3576-server 10.47.47.8
But when CPPM sends CoA requests to the MC, they are not working. This exhibit shows the RFC 3576 server statistics on the MC:

How could you fix this issue?
Refer to the scenario.
An organization wants the AOS-CX switch to trigger an alert if its RADIUS server (cp.acnsxtest.local) rejects an unusual number of client authentication requests per hour. After some discussions with other Aruba admins, you are still not sure how many rejections are usual or unusual. You expect that the value could be different on each switch.
You are helping the developer understand how to develop an NAE script for this use case.
The developer explains that they plan to define the rule with logic like this:
monitor > value
However, the developer asks you what value to include.
What should you recommend?
Refer to the scenario.
A customer has an AOS10 architecture that is managed by Aruba Central. Aruba infrastructure devices authenticate clients to an Aruba ClearPass cluster.
In Aruba Central, you are examining network traffic flows on a wireless IoT device that is categorized as “Raspberry Pi†clients. You see SSH traffic. You then check several more wireless IoT clients and see that they are sending SSH also.
You want a relatively easy way to communicate the information that an IoT client has used SSH to Aruba CPPM.
What is one prerequisite?
Refer to the scenario.
A customer is using an AOS 10 architecture with Aruba APs and Aruba gateways (two per site). Admins have implemented auto-site clustering for gateways with the default gateway mode disabled. WLANs use tunneled mode to the gateways.
The WLAN security is WPA3-Enterprise with authentication to an Aruba ClearPass Policy Manager (CPPM) cluster VIP. RADIUS communications use RADIUS, not RadSec.
CPPM is using the service shown in the exhibits.

Which step can you take to improve operations during a possible gateway failover event?
Refer to the scenario.
A customer has an AOS10 architecture that is managed by Aruba Central. Aruba infrastructure devices authenticate clients to an Aruba ClearPass cluster.
In Aruba Central, you are examining network traffic flows on a wireless IoT device that is categorized as “Raspberry Pi†clients. You see SSH traffic. You then check several more wireless IoT clients and see that they are sending SSH also.
You want an easy way to communicate the information that an IoT client has used SSH to Aruba ClearPass Policy Manager (CPPM).
What step should you take?
Refer to the scenario.
# Introduction to the customer
You are helping a company add Aruba ClearPass to their network, which uses Aruba network infrastructure devices.
The company currently has a Windows domain and Windows CA. The Window CA issues certificates to domain computers, domain users, and servers such as domain controllers. An example of a certificate issued by the Windows CA is shown here.
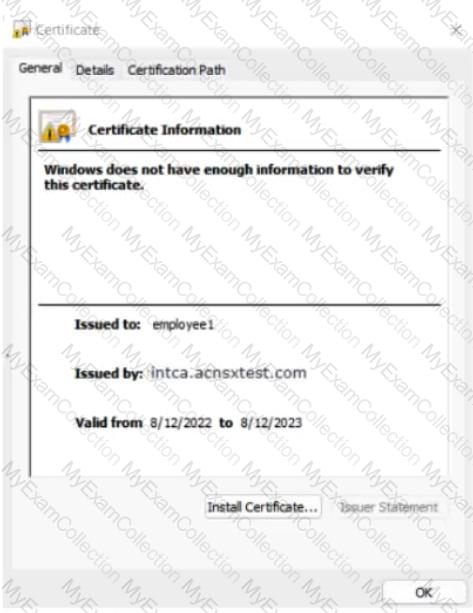
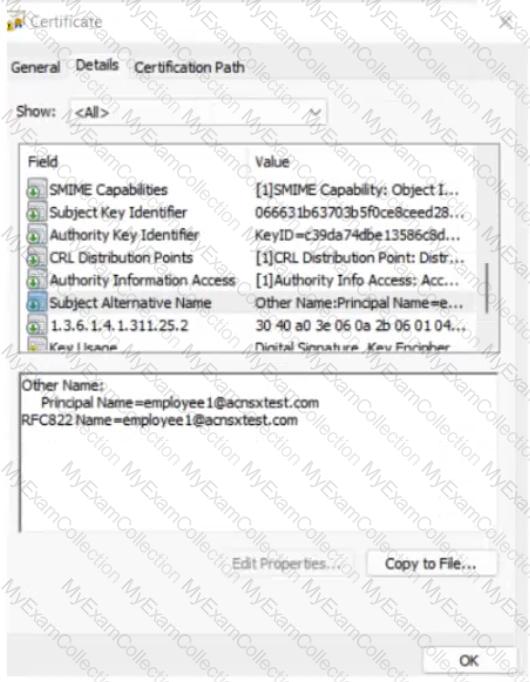
The company is in the process of adding Microsoft Endpoint Manager (Intune) to manage its mobile clients. The customer is maintaining the on-prem AD for now and uses Azure AD Connect to sync with Azure AD.
# Requirements for issuing certificates to mobile clients
The company wants to use ClearPass Onboard to deploy certificates automatically to mobile clients enrolled in Intune. During this process, Onboard should communicate with Azure AD to validate the clients. High availability should also be provided for this scenario; in other words, clients should be able to get certificates from Subscriber 2 if Subscriber 1 is down.
The Intune admins intend to create certificate profiles that include a UPN SAN with the UPN of the user who enrolled the device.
# Requirements for authenticating clients
The customer requires all types of clients to connect and authenticate on the same corporate SSID.
The company wants CPPM to use these authentication methods:
 EAP-TLS to authenticate users on mobile clients registered in Intune
EAP-TLS to authenticate users on mobile clients registered in Intune
 TEAR, with EAP-TLS as the inner method to authenticate Windows domain computers and the users on them
TEAR, with EAP-TLS as the inner method to authenticate Windows domain computers and the users on them
To succeed, EAP-TLS (standalone or as a TEAP method) clients must meet these requirements:
 Their certificate is valid and is not revoked, as validated by OCSP
Their certificate is valid and is not revoked, as validated by OCSP
 The client’s username matches an account in AD
The client’s username matches an account in AD
# Requirements for assigning clients to roles
After authentication, the customer wants the CPPM to assign clients to ClearPass roles based on the following rules:
 Clients with certificates issued by Onboard are assigned the “mobile-onboarded†role
Clients with certificates issued by Onboard are assigned the “mobile-onboarded†role
 Clients that have passed TEAP Method 1 are assigned the “domain-computer†role
Clients that have passed TEAP Method 1 are assigned the “domain-computer†role
 Clients in the AD group “Medical†are assigned the “medical-staff†role
Clients in the AD group “Medical†are assigned the “medical-staff†role
 Clients in the AD group “Reception†are assigned to the “reception-staff†role
Clients in the AD group “Reception†are assigned to the “reception-staff†role
The customer requires CPPM to assign authenticated clients to AOS firewall roles as follows:
 Assign medical staff on mobile-onboarded clients to the “medical-mobile†firewall role
Assign medical staff on mobile-onboarded clients to the “medical-mobile†firewall role
 Assign other mobile-onboarded clients to the “mobile-other†firewall role
Assign other mobile-onboarded clients to the “mobile-other†firewall role
 Assign medical staff on domain computers to the “medical-domain†firewall role
Assign medical staff on domain computers to the “medical-domain†firewall role
 All reception staff on domain computers to the “reception-domain†firewall role
All reception staff on domain computers to the “reception-domain†firewall role
 All domain computers with no valid user logged in to the “computer-only†firewall role
All domain computers with no valid user logged in to the “computer-only†firewall role
 Deny other clients access
Deny other clients access
# Other requirements
Communications between ClearPass servers and on-prem AD domain controllers must be encrypted.
# Network topology
For the network infrastructure, this customer has Aruba APs and Aruba gateways, which are managed by Central. APs use tunneled WLANs, which tunnel traffic to the gateway cluster. The customer also has AOS-CX switches that are not managed by Central at this point.
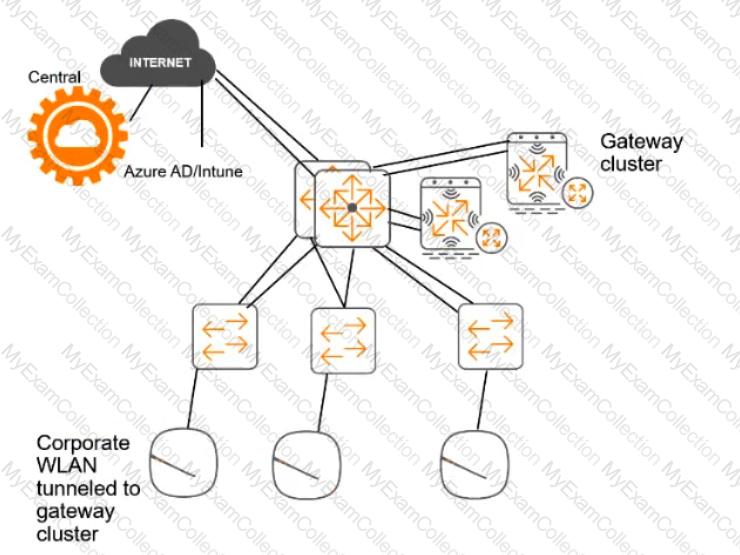
# ClearPass cluster IP addressing and hostnames
A customer’s ClearPass cluster has these IP addresses:
 Publisher = 10.47.47.5
Publisher = 10.47.47.5
 Subscriber 1 = 10.47.47.6
Subscriber 1 = 10.47.47.6
 Subscriber 2 = 10.47.47.7
Subscriber 2 = 10.47.47.7
 Virtual IP with Subscriber 1 and Subscriber 2 = 10.47.47.8
Virtual IP with Subscriber 1 and Subscriber 2 = 10.47.47.8
The customer’s DNS server has these entries
 cp.acnsxtest.com = 10.47.47.5
cp.acnsxtest.com = 10.47.47.5
 cps1.acnsxtest.com = 10.47.47.6
cps1.acnsxtest.com = 10.47.47.6
 cps2.acnsxtest.com = 10.47.47.7
cps2.acnsxtest.com = 10.47.47.7
 radius.acnsxtest.com = 10.47.47.8
radius.acnsxtest.com = 10.47.47.8
 onboard.acnsxtest.com = 10.47.47.8
onboard.acnsxtest.com = 10.47.47.8
You cannot see flow attributes for wireless clients.
What should you check?
Refer to the scenario.
A customer has asked you to review their AOS-CX switches for potential vulnerabilities. The configuration for these switches is shown below:

What is one recommendation to make?

