Which of the following intelligent traffic steering policies can be used to fully utilize link bandwidth and implement link bandwidth-based load balancing on an enterprise network with multiple links?
On a campus network, which of the following problems may occur when you manually create a static VXLAN tunnel?
HTTP is an application layer protocol for distributed, collaborative, and hypermedia information systems.
K company has two types of network services: UDP-based real-time video streaming services and TCP-based FTP download services. The company's network administrator often receives complaints that the FTP download speed is slow or unstable. What are the possible causes?
An SRLB is a set of user-specified local labels reserved for SR-MPLS. These labels are locally configured and have only local significance. Therefore, they are not advertised through the IGP.
Before connecting an SSH client to an SSH server in public key authentication mode, a client needs to create a key pair. Which of the following commands is used to create a DSS key pair on the client using Git Bash?
In thefirewall hot standby scenario, in which of the following conditions will the local deviceproactively send VGMP packets?
Which of the following statements about 802.1X authentication are correct?
In a scenario where a VXLAN tunnel is dynamically established through BGP EVPN, which of the following statements about symmetric IRB forwarding are correct?
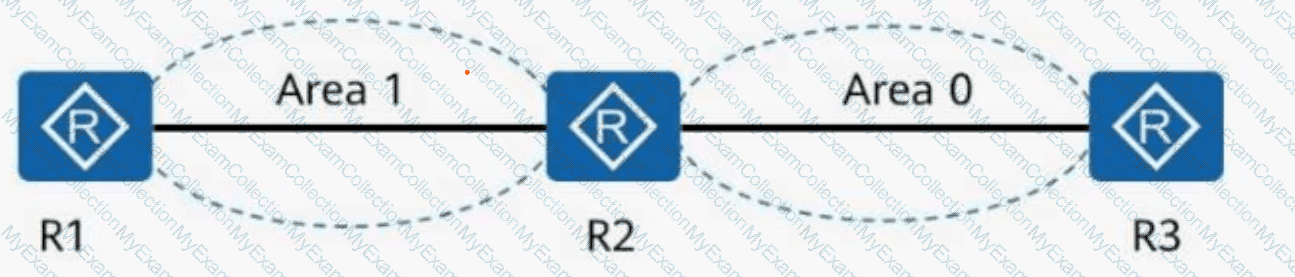
In the following figure, all routers are running OSPF. Given this, which of the following statements is correct?
Huawei Open Programmability System (OPS) uses HTTP methods to access managed objects to manage network devices. To facilitate script compilation, Huawei OPS provides the Python script template. In the Python script template, what are the contents of the Content-type and Accept fields in the header of an HTTP request packet?
Which of the following fields is added to BGP4+ Update packets to advertise IPv6 routes?
NETCONF provides a set of mechanisms for managing network devices. What layers can NETCONF be conceptually partitioned into?
Which of the following parameters is not included in an IPsec security association (SA)?
Which of the following functions can be provided by iMaster NCE-Campus when it functions as a relay agent for authentication?
In addition to indicating priority, the DSCP value can also indicate the drop probability. Which of the following DSCP values is set with the highest drop probability?
On the network shown in the figure, OSPF-based SR-MPLS TE is enabled on all routers. Which of the following adjacency labels are allocated by P3?
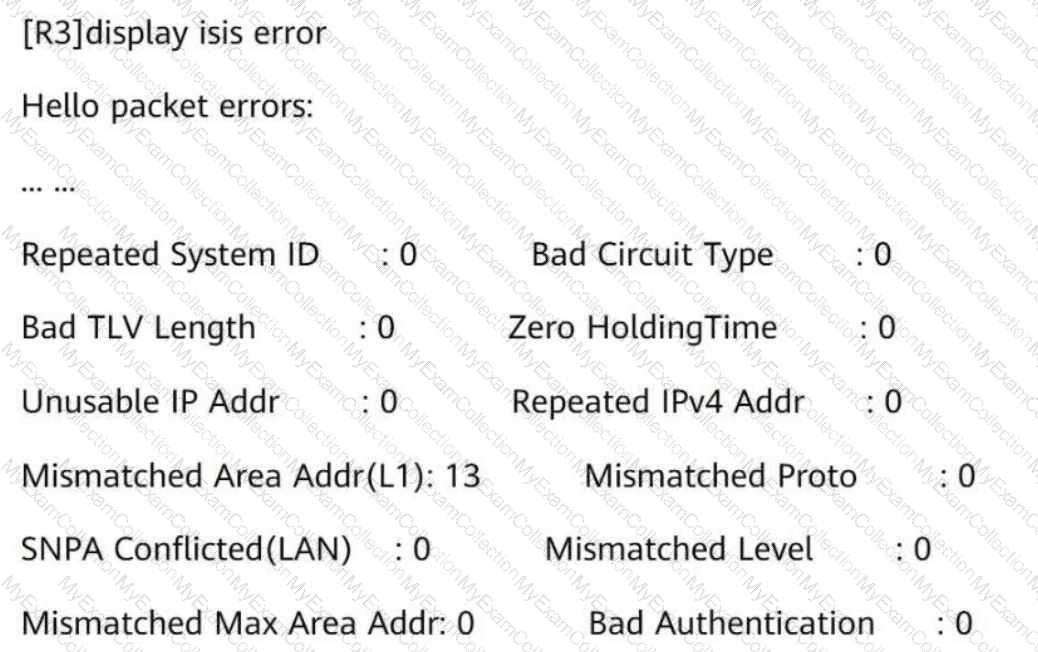
According to the following information displayed on a router, which of the following are the causes of the failure in establishing an OSPF adjacency relationship?
OSPF error statistics:
1: Hello timer mismatch
0: Netmask mismatch
0: Bad checksum
0: Bad authentication type
0: Unknown neighbor
0: Extern option mismatch
If ISIS is used to transmit SIDs on an SR network, the node SIDs advertised by a Level-2 router are transmitted only within the same area.
What can be determined from the following figure?
Total Number of Routes: 2
*>i Network : 3002::3
NextHop : 3000:FDEA::3
MED : 0
Path/Orgn : i
*>i Network : 3002::4
NextHop : 3000:FDEA::3
MED : 0
PrefixLen : 128
LocPrf : 100
PrefVal : 0
Path/Orgn : 65001 i
On a virtualized network deployed using iMaster NCE-Campus, after creating VNs, you need to configure inter-VN communication. Which of the following configurations is used to achieve VN communication?
Whenstatic IPsec VPNis used for WAN interconnection in theHuawei CloudCampus Solution, theAP, Router, and ____can be used as egress devices.
Which of the following statements isincorrectabout adding devices on a virtualized network deployed using iMaster NCE-Campus?
iMaster NCE-Campus restricts RESTful APIs. If a client sends aGET requestthat invokes a RESTful API to obtain site information from iMaster NCE-Campus, which of the following fields should be included in the request header?
On acampus network,iMaster NCE-Campusis used to deploy twoVNs (Virtual Networks):R&D VNandMarketing VN. Users in these two VNs belong to twoseparate security groups.
The campus network requiresR&D personnel and sales personnel to communicate with each other. To meet this requirement, which of the following tasks does a network administrator need to perform?
To enhance reliability, you can deploy Huawei iMaster NCE-WAN controllers in active/standby mode. Which of the following IP addresses must be configured to be the same for the active and standby controllers so that the controllers can be accessed properly? (Select All that Apply)
Collecting information before a cutover helps you determine whether services are normal before and after the cutover.
When designing IGP routes for an enterprise bearer WAN, ensure that the metric of aggregation-layer links is smaller than that of access-layer links, so that data can be preferentially forwarded over aggregation-layer links.
The channelized sub-interface and FlexE technologies both can be used to implement network slicing, but the application scenarios of the two technologies are slightly different. Which of the following statements about the two technologies are correct?
Which of the following statements aboutSR-MPLS Policy path planningare correct?
Refer to the output information of a device below. According to the information, which of the following MPLS labels is carried in a data packet forwarded by the device to 10.0.1.1?
Which of the following are application optimization functions in the Huawei SD-WAN Solution?
Flavors are additional behaviors defined to enhance theEnd series instructionsinSRv6. Which of the followingEnd instructionscan thePSP flavorbe attached to?
When you configure avirtualized campus networkoniMaster NCE-Campus, Fit APs can immediately go online after you add them toiMaster NCE-Campus.
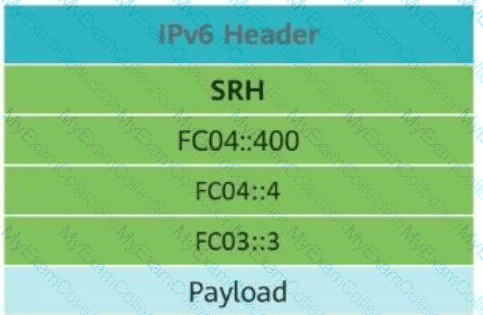
This figure shows anSRv6 (Segment Routing over IPv6)packet. If theDestination Addressfield in the IPv6 basic header isFC04::4, the value of theSL (Segment Left)field in the SRv6 header should be____.(Enter only digits.)
In Huawei SD-WAN Solution, which of the following tunneling technologies is used to establish data channels?
In the figure,SR-MPLSis enabled onR1, R2, and R3. TheSRGB (Segment Routing Global Block) rangeonR3is from20000 to 21000, and theprefix SID indexconfigured on theloopback1 interface of R3 is 30.
In this case, theMPLS label corresponding to the loopback1 interface of R3 is _____.
(Enter anArabic numeralwithout symbols.)
TheNETCONF content layercontainsdevice configuration data.
Which of the following statements are correct about the followingNETCONF configuration?
To obtain thetoken IDofiMaster NCE, you need to send anHTTP requestusing the followingPython codeto invoke aniMaster NCE RESTful API:
Which of the following statements isincorrect?
The following figure shows the inter-AS MPLS L3VPN Option C (Solution 2). ASBR-PE2 is connected to CE3 and runs eBGP.
To enable all CEs to communicate with each other, which of the following address families must peer relationships be enabled in the BGP process of ASBR-PE2?
Flavors can be used to enhance SRv6 instructions to meet more diversified service requirements. Which of the following are flavors? (Select all that apply)
An engineer needs todownload the configuration file vrpcfg.cfgto a local device throughSFTP, rename the configuration file to backup.cfg, and upload it to thedefault directory of the device.
The configuration file is located at /vrpcfg.cfg (default directory of the remote device), and the local directory is C:\.
Which of the followingPython Paramikocode lines can implement the required operations?
MPLS supports forwarding equivalence class (FEC). Which of the following cannot be used as an FEC allocation standard?
In the Huawei SD-WAN Solution, which of the following routing protocols is used to advertise VPN routes between CPEs?
The IS-IS Level-1 neighbor relationship is not established betweenR3andR4. Referring to the following information, what is the possible cause?
On a router,SRv6is enabled, and the configurations shown below are performed. Which of the following statements about the configurations are correct?
[Router-segment-routing-ipv6] locator srv6_locator1 ipv6-prefix 2001:DB8:ABCD::/64 static 32
If an engineer wants to remotely log in to a Huawei device, the engineer uses the Paramiko library to compile the following code when compiling the SSH Python script:
cli = ssh.invoke_shell()
cli.send("screen-length 0 temporary\n")
What is the function of screen-length 0 temporary?
Which of the following is the drop probability of packets exceeding the upper threshold in WRED?
SSH connections are usually established based on TCP/IP connections. In specific cases, SSH connections can be established based on UDP connections.
O&M personnel for a large-scale event center receive feedback about Wi-Fi access failures. iMaster NCE-CampusInsight provides the function for personnel to view packet exchange processes and locate the root cause. It is found that IP addresses in the DHCP address pool are exhausted, preventing IP addresses from being assigned to mobile terminals. Which of the following functions is used by O&M personnel in this scenario?
An LSR supports various label retention modes. Which of the following statements regarding the liberal mode are correct?
Based on the figure, which of the following statements are correct?
1 10.1.12.2 40 ms 10 ms 10 ms
2 10.1.24.2 30 ms 20 ms 20 ms
3 10.1.34.1 20 ms 20 ms 20 ms
4 10.1.13.1 20 ms 20 ms 10 ms
5 10.1.12.2 20 ms 30 ms 20 ms
6 10.1.24.2 30 ms 30 ms 30 ms
7 10.1.34.1 50 ms 40 ms 40 ms
8 10.1.13.1 20 ms 30 ms 30 ms
When configuring a static VXLAN tunnel, you need to manually configure the _____, VTEP IP address, and ingress replication list. (Enter only uppercase letters.)
Which of the following community attributes ensure that BGP routes are transmitted only within an AS?
Which of the following statements about the multicast address used by OSPFv3 are correct?
Which of the following is the type ofnorthbound APIused byiMaster NCE-WAN?
SR-MPLS uses IGP extensions to advertise labels and reserve bandwidth to support high-bandwidth services.
Network Quality Analysis (NQA) is a real-time network performance detection and measurement technology. It monitors the performance of multiple protocols running on a network. Which of the following protocols can be monitored by NQA?
Which of the following can be used to transmit traffic to a VXLAN network and implement intra-subnet communication on the same VXLAN network?
During telemetry static subscription, the NMS delivers subscription configuration to devices for data sampling. Which of the following statements is incorrect about the sampling path huawei-debug:debug/cpu-infos/cpu-info?
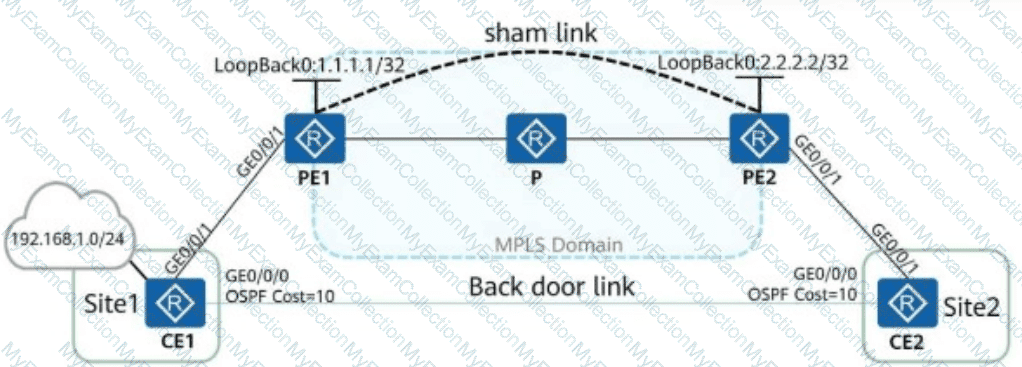
As shown in the figure, a sham link is established between PE1 and PE2 through the loopback interfaces. CE2 can learn the 192.168.1.0/24 route (directed route on CE1) through the sham link and backdoor link. If other parameters use their default settings, the cost of the 192.168.1.0/24 route on CE2 should be ______. (Enter an Arabic numeral without symbols.)
Huawei Open Programmability System (OPS) provides openness and programmability capabilities for network devices and enables users to perform secondary development. To facilitate script completion, Huawei OPS provides the Python script template in which the OPSConnection class is created. The member function for creating device resources is def post(self, uri, req_data).
NAFTIR policing can only be applied to the inbound direction. Its purpose is to monitor the traffic entering the device and ensure that the upstream device does not unnecessarily consume network resources.
Huawei Open Programmability System (OPS)usesstandard HTTP methodsto accessmanaged objectsand manage network devices.
Which of the followingHTTP methodsis used toconfigure the value of a network device’s managed object?
Which of the following items are included in static information collection and analysis?
As shown in the figure, when PE1 receives an ARP request packet, it forwards the packet to PE4. The packet then carries two labels. The label value 201 is carried by the EVPN Type ____ route. (Enter only digits.)
Telemetry data must be encoded in GPB binary format. This format reduces the number of bytes in telemetry messages and improves the transmission efficiency compared with messages encoded in JSON format.
InSRv6, each time a packet passes through anSRv6 endpoint node, theSegments Leftfield valuedecrements by 1, and theIPv6 DA changes.
Which of the following statements aboutSR-MPLS Policy candidate pathsare correct?
MPLS supports Forwarding Equivalence Class (FEC). Which of the following cannot be used as a FEC allocation standard?
In theHuawei CloudCampus Solution, which of the following devices can go online through theregistration query center?
During WLAN planning and design, channels 1, 6, and 11 are recommended on the 2.4 GHz frequency band, and channels 1, 5, 9, and 13 are recommended in high-density scenarios. On the 5 GHz frequency band, it is recommended thathigh-frequency and low-frequency channels of adjacent APs be staggered to prevent overlapping.
In a VXLAN scenario, which of the following features can be enabled to reduce ARP packet flooding between VTEPs?
Telemetry is a technology that remotely collects data from physical or virtual devices at high speed, and has a layered protocol stack. Which of the following layers isnotincluded in the telemetry protocol stack?
Drag the IPsec functions on the left to the corresponding function description on the right.
When an SSH client logs in to an SSH server that is configured only with username and password authentication in SSH mode, the key exchange phase is not involved (no key is generated).
When an NVE encapsulates a data frame into a VXLAN packet, information of which of the following protocols is encapsulated between the outer IP header and the VXLAN header?
A network administrator needs to retrieve atoken IDfromiMaster NCEusing the following Python code:
import requests
nbi_name = "demol3@north.com"
nbi_pwd = "qqcOVcVel@"
host = "139.9.213.72"
port = "18002"
URI = "/controller/v2/tokens"
post_token_url = "https:// " + host + ":" + port + URI
headers_post = {'Content-Type': 'application/json', 'Accept': 'application/json'}
r = requests.post(post_token_url, headers=headers_post, json={"userName": nbi_name, "password": nbi_pwd}, verify=incorrect)
Which of the following statements is incorrect?
Which of the following statements aboutOPS (Open Programmability System) application scenariosisincorrect?
In the firewall hot standby scenario, which of the following status information can be backed up between the active and standby firewalls?
In OSPF, an ABR translates all Type 7 LSAs in a Not-So-Stubby Area (NSSA) into Type 5 LSAs.
The Ingress VTEP performs both Layer 2 and Layer 3 table lookup for packet forwarding. The forwarding mode is _____ IRB forwarding. (Capitalize the first letter.)
On a CloudCampus virtualized campus network, service data enters different VNs from physical networks through edge nodes, and the VN that the data will enter is determined by the VLANs to which users belong. Which of the following statements about dynamic VLAN authorization is incorrect?
Which of the following channels are involved in the Huawei SD-WAN Solution?
 A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect.
