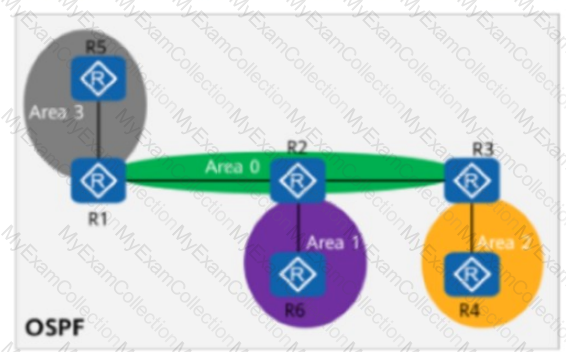
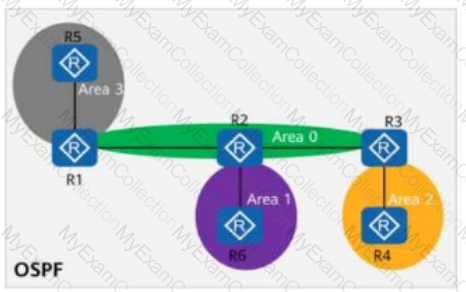
On the OSPF network shown in the figure, area 1 is a common area, area 2 is a stub area, and area 3 is an NSSA. R5 imports an external route 10.0.5.5/32. Given this, which of the following routers does not have the route 10.0.5.5/32 in its routing table?
I-SPF and PRC can speed up ISIS route convergence. PRC does not calculate nodes. Instead, it updates routes based on the shortest path tree (SPT) calculated using the SPF algorithm.
OSPFv3 packets are encapsulated in IPv6 packets. Which of the following is the value of the Next Header field in the IPv6 packet header?
Options:
In the hub-spoke networking shown in the figure, to ensure correct route transmission, an administrator must manually configure the peer 10.1.2.1 _____ command in the IPv4 address family view of the BGP-VPN_out instance on the Hub-PE.

(Enter the answer in lowercase letters only.)
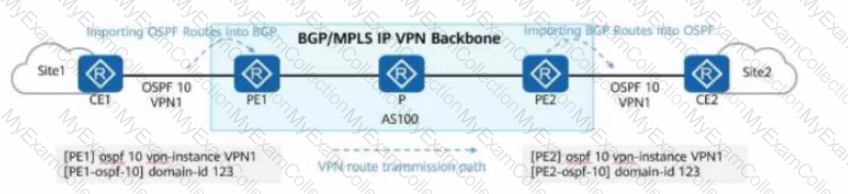
The figure shows information about VPN1 on a PE (Provider Edge) router in a BGP/MPLS IP VPN network.
When the VPNv4 route corresponding to VPN1 is advertised to the remote PE, which VPNs of the remote PE will accept the route?
VPN1 Configuration:
ip vpn-instance VPN1
ipv4-family
route-distinguisher 100:1
vpn-target 100:1 200:1 300:1 export-extcommunity
VPN Import Policies on the Remote PE:
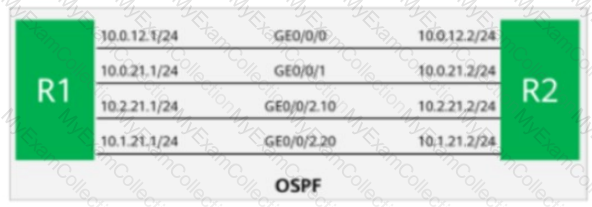
On the OSPF network shown in the figure, R1 and R2 are connected through four links. OSPF is enabled on Loopback0 of R2, and the maximum load-balancing 1 command is run in the OSPF process of R1. Which of the following is the outbound interface from R1 to Loopback0 of R2?
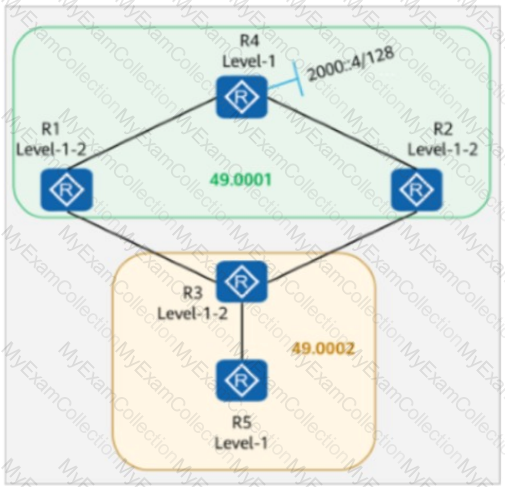
On the IS-IS IPv6 network shown in the figure, multi-topology is enabled on all routers. The IPv6 address of Loopback0 on R4 is 2000::/128. The IPv6 summary 2000::/64 level-1-2 command is configured in the IS-IS processes of R2 and R1. Which of the following statements is false?
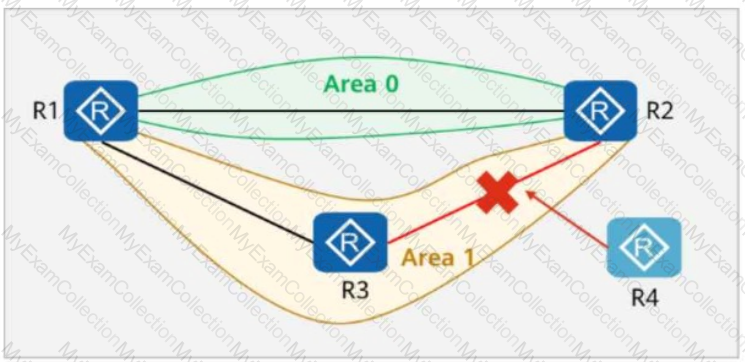
The figure shows the logical network architecture of a migration project. The purpose of the migration is to add network device R4 between R2 and R3.
OSPF runs between network devices.
After the physical network is connected, a network engineer incorrectly imports the backup configuration of R3 to R4 during the migration.
Given this, which of the following statements are true?
Options:
On the OSPFv3 network shown in the figure, area 1 is a common area. Which of the following statements are true?
On a PIM-SM multicast network, a network engineer finds that multicast clients cannot receive multicast data. Which of the following is not a possible cause of this problem?
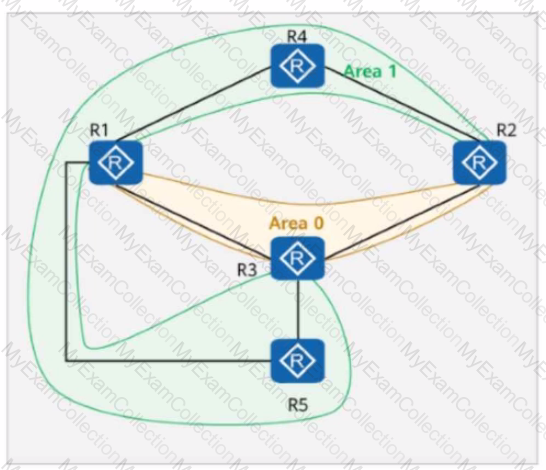
On the OSPF network shown in the figure:
Area 1 is a common area.
Area 2 is a totally NSSA (Not-So-Stubby Area).
Area 3 is an NSSA.
R5 imports the external route 10.0.5.5/32 into OSPF.
Which of the following routers have the route 10.0.5.5/32 in their routing tables?
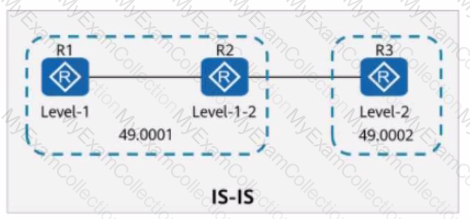
On the ISIS network shown in the figure, R1 imports a default route using the default-route-advertise always level-1 command. In this case, R3 can learn this default route through IS-IS.
If end-to-end QoS is configured on an MPLS network, the penultimate hop device on the MPLS network can pop MPLS labels from packets based on penultimate hop popping (PHP), so that the egress node can process packets based on the QoS priority in inner packets.
MPLS supports nesting of multiple labels. After receiving an MPLS packet, a device first processes the label next to the Layer 2 header, that is, the top MPLS label.
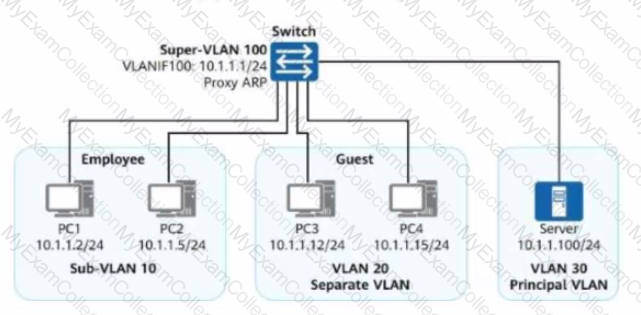
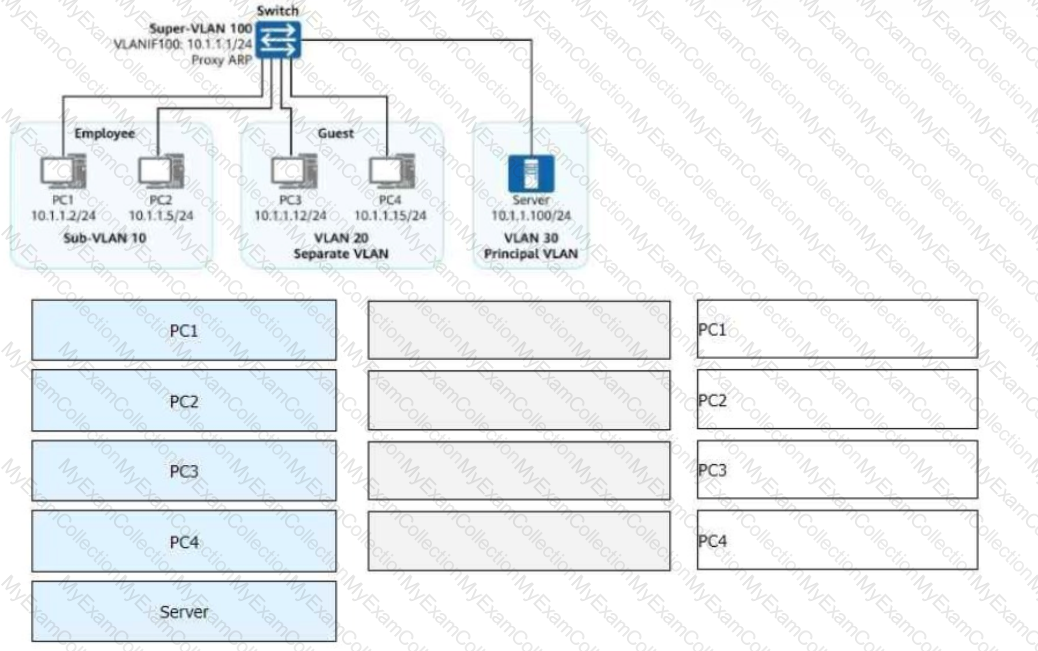
Both VLAN aggregation and MUX VLAN are deployed on the enterprise network shown in the figure, and all switch interfaces connected to terminals are access interfaces. Given this, match PCI to PC4 with the hosts or servers that they can access on the network. (Note: A host cannot be matched with itself. For example, PCI cannot match PCI.) (Tokens can be reused.)

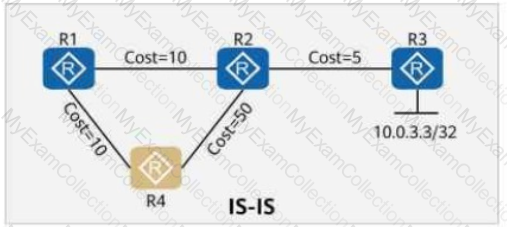
On the OSPF network shown in the figure, the cost values of links are marked. IS-IS Auto FRR is enabled on R1. The primary path from R1 to 10.0.3.3/32 is R1 → R2 → R3, and the backup path is R1 → R4 → R2 → R3.
Is this statement TRUE or FALSE?
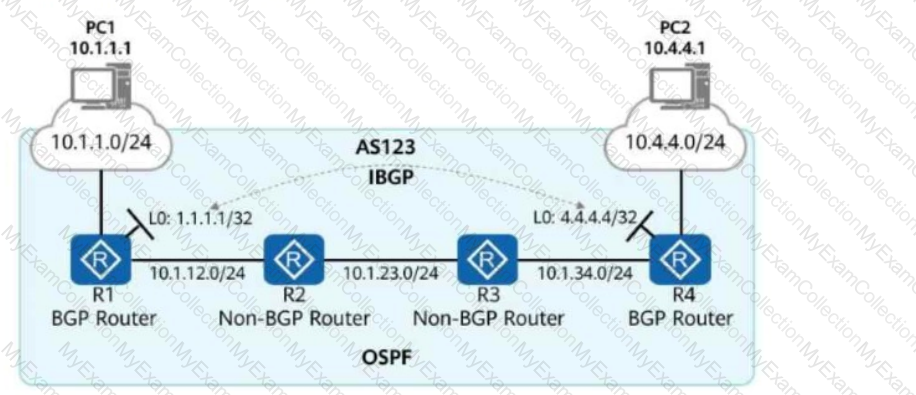
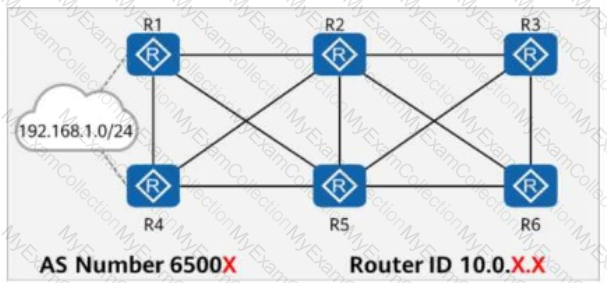
As shown in the figure, R1 to R4 are four routers in AS123. They all run OSPF to implement route reachability within the AS.
Network segments 10.1.1.0/24 and 10.4.4.0/24 are not advertised into OSPF.
R1 and R4 establish an IBGP peer relationship using Loopback0 and advertise network segments 10.1.1.0/24 and 10.4.4.0/24 into BGP.
Which of the following methods can be used to implement communication between PC1 and PC2?
Options:
MPLS can carry multiple network protocol services, including unicast IPv4 services, multicast IPv4 services, unicast IPv6 services, and multicast IPv6 services.
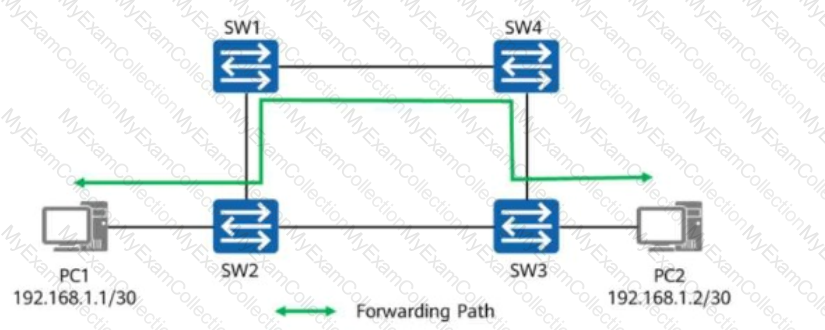
On the network shown in the figure, a network engineer finds that the path between PC1 and PC2 is not the optimal path, and all links along the path have the same cost.
Given this, which of the following routers may be the root bridges of the Layer 2 network?
Options:
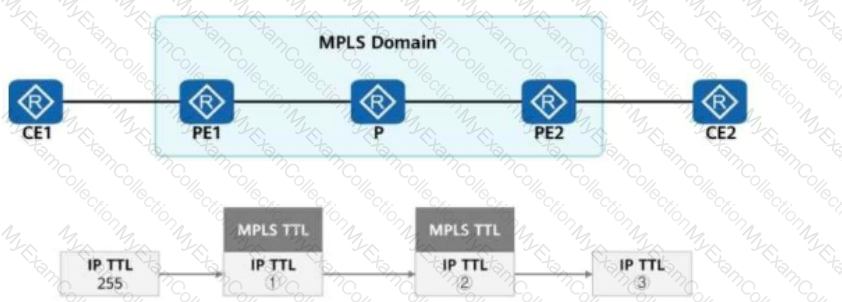
When an IP packet passes through an MPLS network, an MPLS device processes the TTL value in the packet.
If the pipe mode is used in the topology shown in the figure, which of the following is the TTL value in the IP packet?
Options:
Service routes of an enterprise are transmitted on the network. Some configurations of PE1 and PE2 are shown in the figure. Which of the following LSAs may CE2 receive?
On the network shown in the figure, SW3 is the user gateway and DHCP relay agent.
The administrator plans to configure DHCP snooping on SW3 to prevent DHCP attacks.
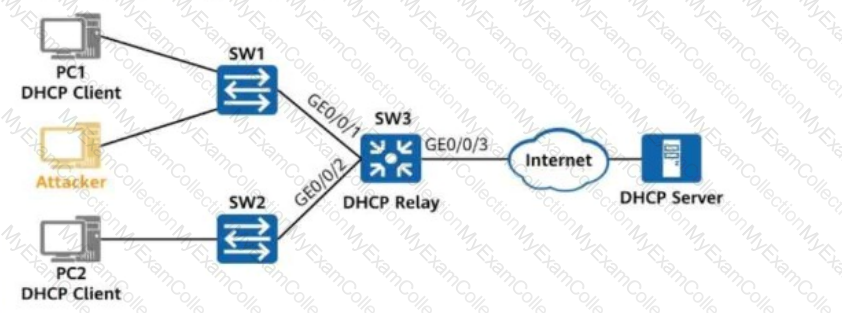
Which of the following commands does not need to be configured on SW3?
On an enterprise network shown in the figure, if CE2 is dual-homed to PE2 and PE3, a routing loop may occur during the exchange of Type 5 LSAs (External LSAs in OSPF).
To prevent the loop, the route-tag command can be run on PE2 and PE3.
In this way, if the route tag of the route received by PE3 is the same as that configured locally, the route is ignored.
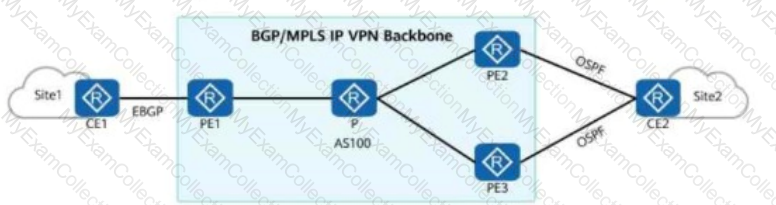
Is this statement True or False?
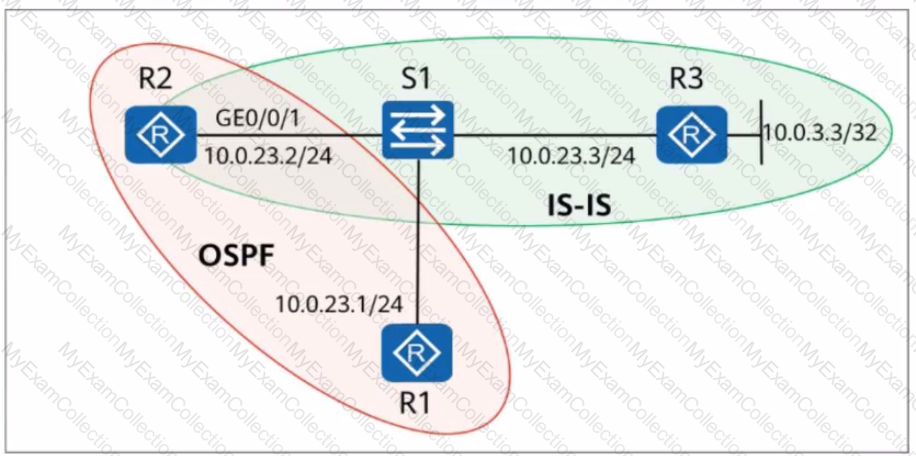
On the network shown in the figure, OSPF is deployed on R1 and R2. IS-IS is deployed on R2 and R3. To enable R1 to obtain the route to 10.0.3.3/32, ISIS routes are imported into OSPF on R2. In this case, the next hop address to 10.0.3.3/32 in the routing table of R1 is_____.
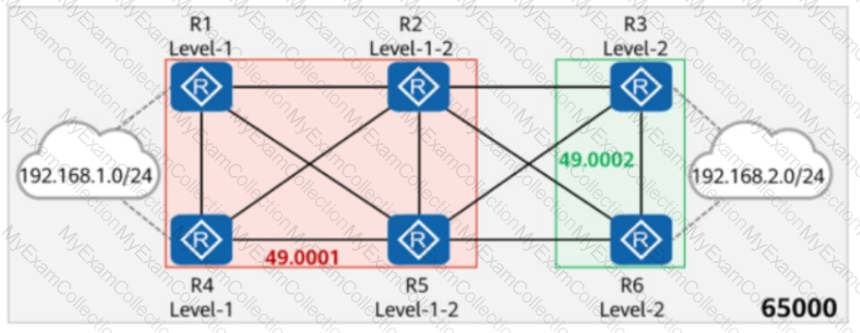
On the network shown in the figure, IS-IS runs on R1, R2, R4, and R5, and the area ID is 49.0001. IS-IS runs on R3 and R6, and the area ID is 49.0002. The import-route isis level-2 into level-1 command is configured on R2 and R5. In AS 65000, R1, R3, R4, and R6 each establish iBGP peer relationships with R2 and R5. R2 and R5 are RR (Route Reflectors), and R1, R4, R3, and R6 are the iBGP peer relationship clients. The iBGP peer relationship ID is 10.0.0.X/32, where X is the number of the iBGP router. R1 and R4 import the external route 192.168.1.0/24 to BGP through the import-route command, and R3 and R6 import the external route 192.168.2.0/24 to BGP through the import-route command. Which of the following statements are true?
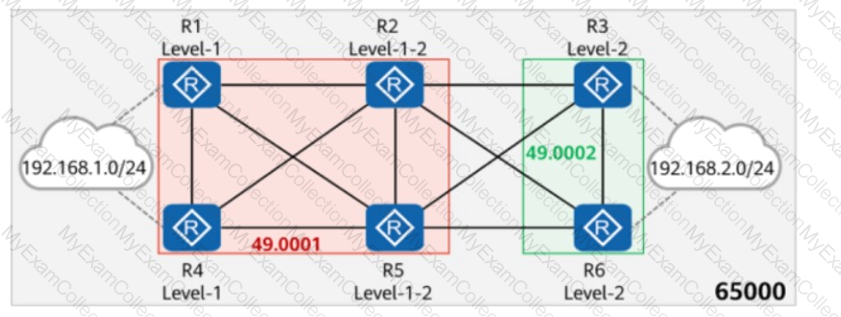
On the network shown in the figure, EBGP peer relationships are established between neighboring routers through directly connected interfaces.
The router ID of each router is 10.0.X.X, and the AS number is 6500X, where X is the number of the router.
Both R1 and R4 have static routes to 192.168.1.0/24, which are imported to BGP through the import-route command.
The aggregate 192.168.1.0/16 detail-suppressed command is configured on R2.
Which of the following is the path for traffic from R3 to 192.168.1.0/24?
IS-IS LSP fragments are identified by the LSP Number field in their LSP IDs. This field is 4 bits long. Therefore, an IS-IS process can generate a maximum of 256 LSP fragments, which means only a limited amount of information can be carried. By adding additional system IDs, you can enable the IS-IS process to generate more LSP fragments.
Options:
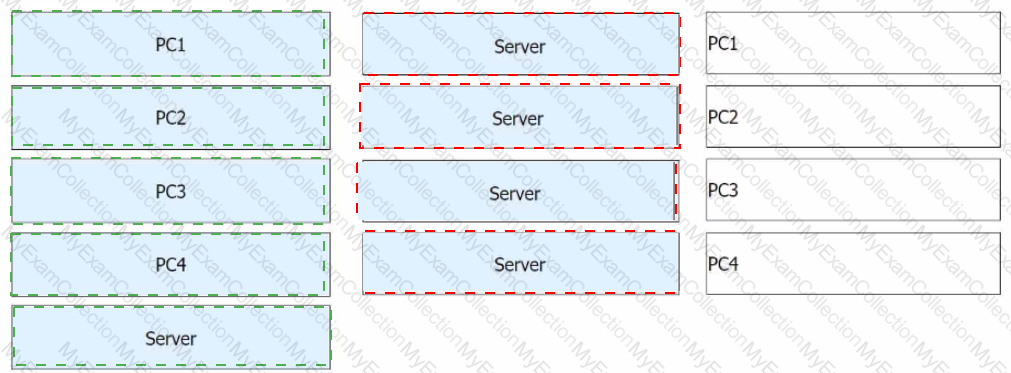
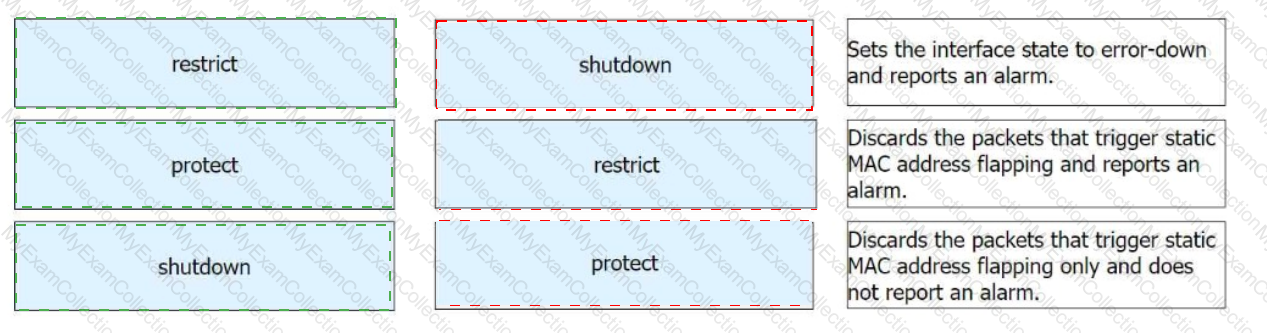
When configuring port security on a switch, the administrator also enables static MAC address flapping detection. If static MAC address flapping occurs, the switch takes the configured action to protect the interface.
Match the names of interface security protection actions with corresponding operations.

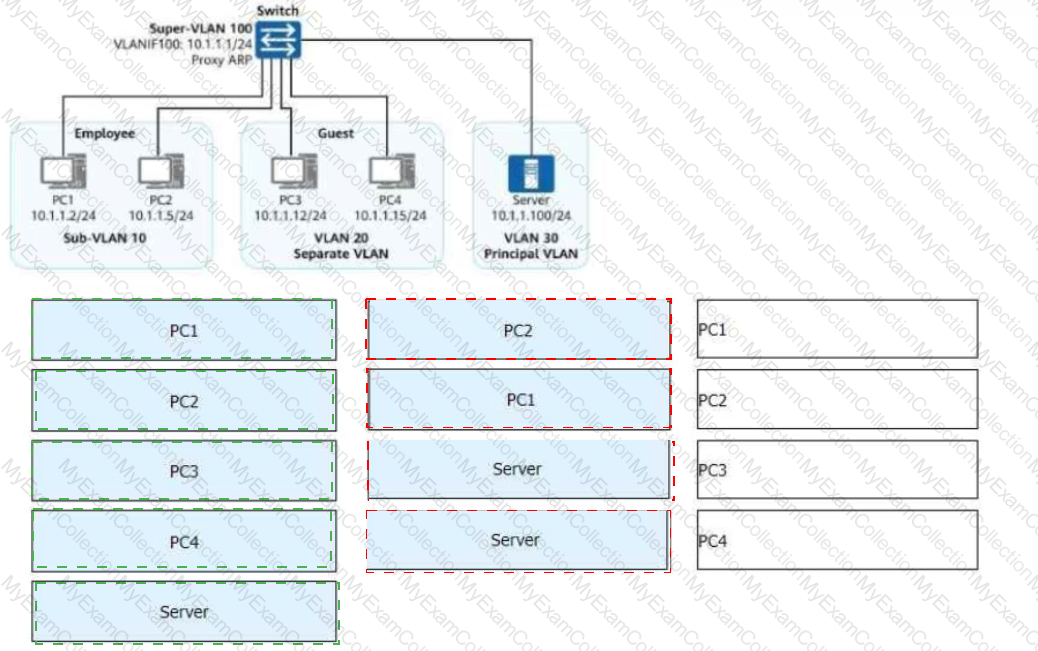
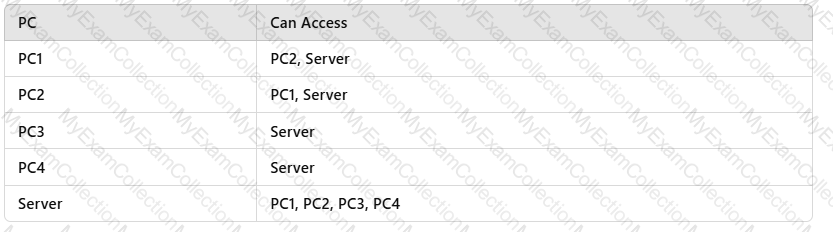
Both VLAN aggregation and MUX VLAN are deployed on the enterprise network shown in the figure.
All switch interfaces connected to terminals are access interfaces.
Given this, match PC1 to PC4 with the hosts or servers they can access on the network.
(Note: A host cannot be matched with itself. For example, PC1 cannot match PC1. Tokens can be reused.)
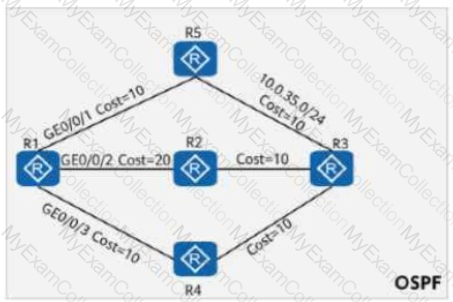
On the OSPF network shown in the figure, the cost values of links are marked. OSPF IP FRR is enabled on R1, and the maximum load-balancing 8 command is configured in the OSPF process. Which of the following is the cost value of the route 10.0.35.0/24 in the routing table of R1?
The figure shows information about an LSP (Link-State PDU) generated by an IS-IS router.
From the LSP, you can infer that the router is not the DIS (Designated Intermediate System) of the local link.
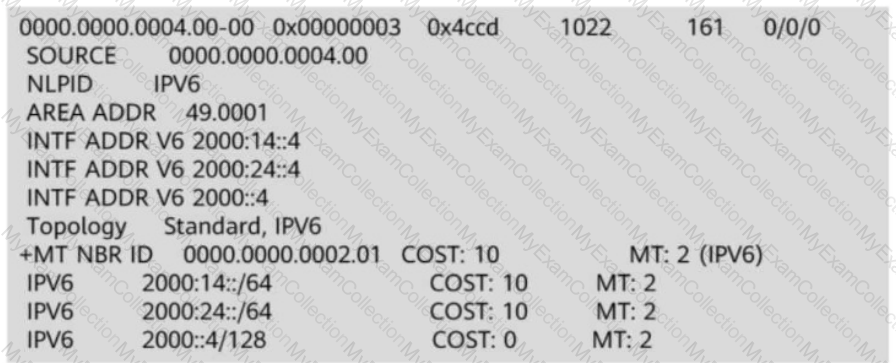
Options:
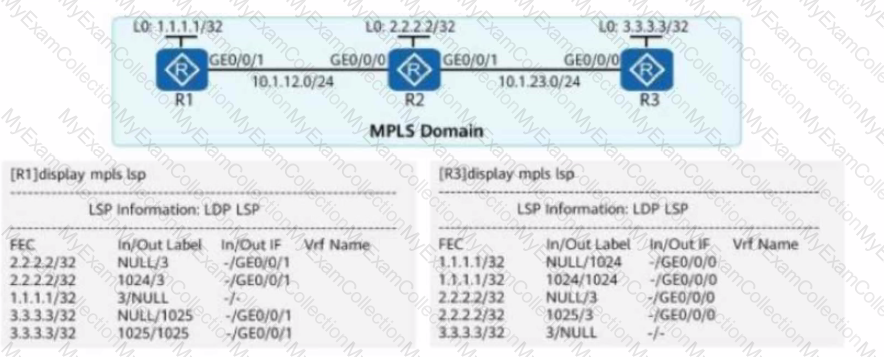
The figure shows the LSP information of R1 and R3 on an MPLS network. An administrator runs the ping -a 1.1.1.1 3.3.3.3 command on R1. Given this, which of the following statements is true?
On the OSPF network shown in the figure, R1 and R2 use OSPF to communicate with each other through Loopback0. In addition:
MPLS LDP is enabled on R1 and R2.
The LDP transport address is the IP address of Loopback0.
A network engineer finds that an LDP session cannot be established between R1 and R2 and runs diagnostic commands (shown in the figure) to locate the fault.
Given this, which of the following are possible causes of the fault?
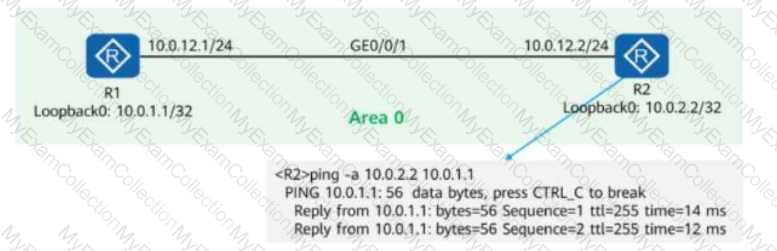
Options:
On the IS-IS IPv6 network shown in the figure:
Multi-topology is enabled on all routers.
The IPv6 address of Loopback0 on R4 is 2000::4/128.
The command ipv6 summary 2000::/64 level-2 is configured in the IS-IS processes of R2 and R1.
The command ipv6 import-route isis level-2 into level-1 is configured in the IS-IS processes of R1, R2, and R3.
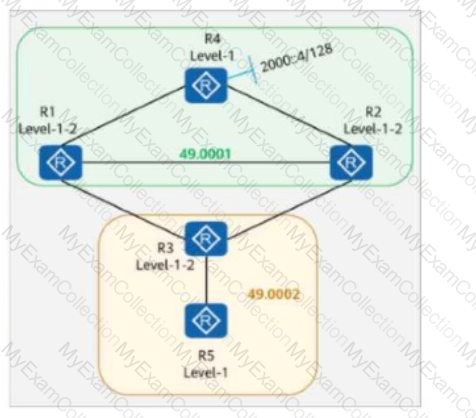
Which of the following routers have the route 2000::/64 in their routing tables?
On the network shown in the figure, IS-IS runs on R1, R2, R4, and R5, and the area ID is 49.0001. IS-IS runs on R3 and R6, and the area ID is 49.0002. In AS 65000, R1, R3, R4, and R6 each establish iBGP peer relationships with R2 and R5. R2 and R5 are RRs (Route Reflectors), and R1, R4, R3, and R6 are clients. The iBGP peer relationships are established using Loopback0 on each router, and the router ID is 10.0.0.X/32, where X is the number of the router. R1 and R4 import the external route 192.168.1.0/24 to BGP through the import-route command, and R3 and R6 import the external route 192.168.2.0/24 to BGP through the import-route command. Which of the following statements are true?
In the figure, a network administrator configures a static LSP to implement MPLS data forwarding. The lower part of the topology shows the packet header information obtained from a device.
Which of the following statements are true?

Options:
Network administrators can run the clock timezone command to set the time zone of a device. If two network devices have different time zone settings, they cannot establish a neighbor relationship using a dynamic routing protocol.
Options:
In the figure, packets are forwarded based on MPLS on the network.
When PE2 receives a packet from P2, what is the label value carried in the packet?
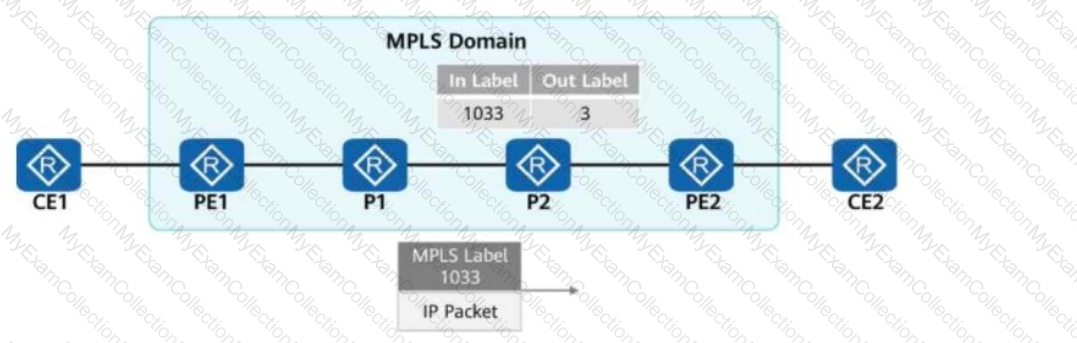
Options:
On the OSPFv3 network shown in the figure, area 1 is a stub area, area 2 is a common area, and area 3 is an NSSA. Which of the following LSAs is displayed only in area 2?
The path that IP packets pass through on an MPLS network is called a label switched path (LSP). An LSP is a bidirectional path that specifies the transmission direction of data flows.
In the hub-spoke networking shown in the figure, the Hub-PE can be configured to allow repetitive local AS numbers for correct route transmission.
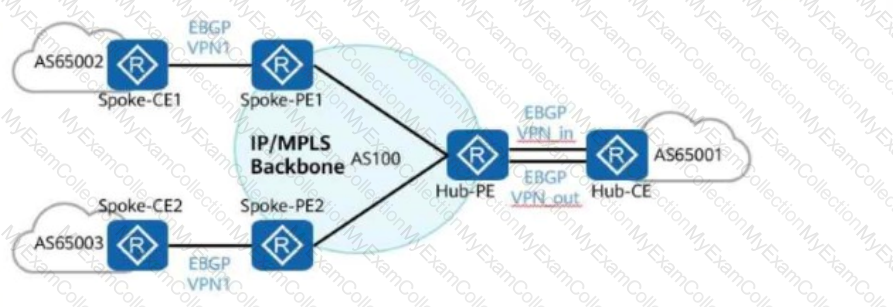
Is this statement TRUE or FALSE?
Options: