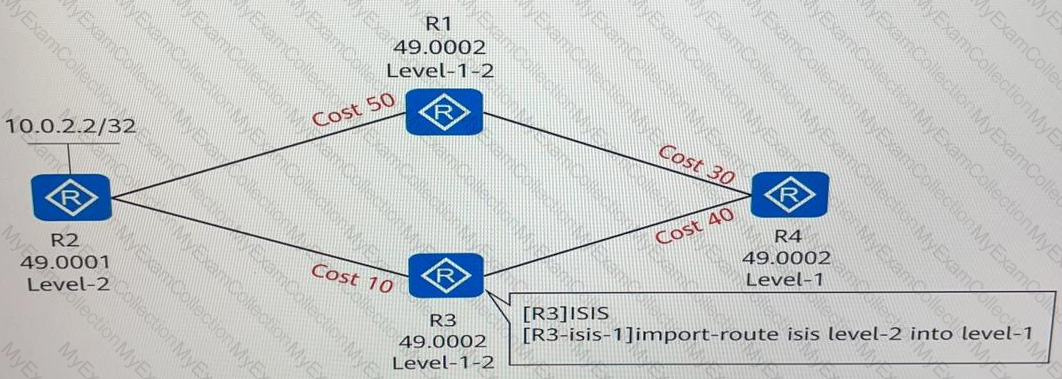
Four routers run ISIS and have established adjacencies. The area IDs and router levels are marked in the following figure. If route leaking is configured on R3, which of the following is the cost of the route from R4 to 10.0.2.2/32?
A monitoring plane usually comprises the monitoring units of main control boards and interface boards. This plane can monitor the system environment independently. Which of the following environment monitoring functions can be provided by the monitoring plane?
IGMPV3 not only supports IGMPv1 General Query and IGMPv2 Group-Specific Query, and also IGMPv3 Source/Group-Specific Query.
The typical characteristics of the AI era are that it focuses on data, explores data value, and improves AI efficiency. Therefore, the core requirement of AI for data center networks is speed, meaning low latency.
On an OSPF network, if two indirectly connected routers with the same router ID run in the same area, Type 1 LSA calculation fails.
After which of the following parameters are modified does an IS-IS neighbor relationship need to re-established?
In BGP, Keepalive messages are used to maintain BGP peer relationships. When a BGP router receives a Keepalive message from a peer, the BGP router sets the state of the peer to Established and periodically sends Keepalive messages to maintain the connection. By default, the device sends Keepalive messages every seconds.
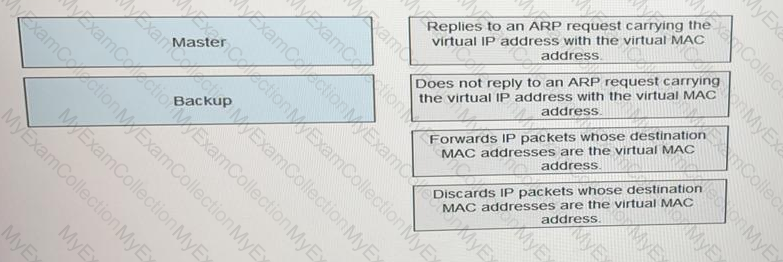
When deploying a VRRP network, an enterprise administrator sets the virtual IP address to 192.168.1.254 and VRID to 1. Which of the following is the virtual MAC address after the network becomes stable?
Which of the following statements regarding the firewall zone security level is false?
IPv6 defines multiple types of addresses. Which of the following statements is false about these addresses?
An IP prefix list is a common matching tool used in routing policies. Which of the following cannot be configured as matching conditions in an IP prefix list on a Huawei router?
A network entity title consists of an area address and a system ID. It is a special NSAP (the SEL has a fixed value of 00) and is mainly used for route calculation.
Which of the following messages are sent when BGP establishes peer relationships?
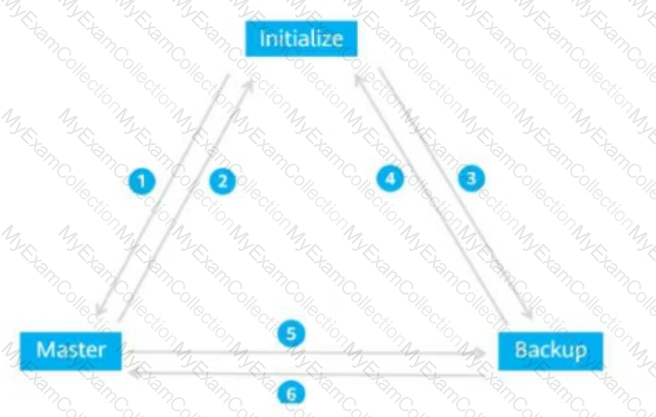
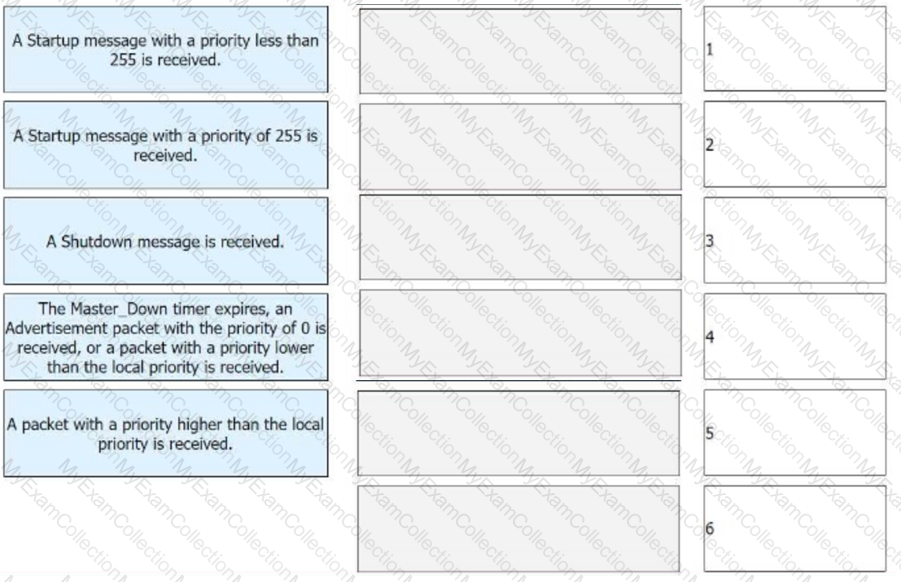
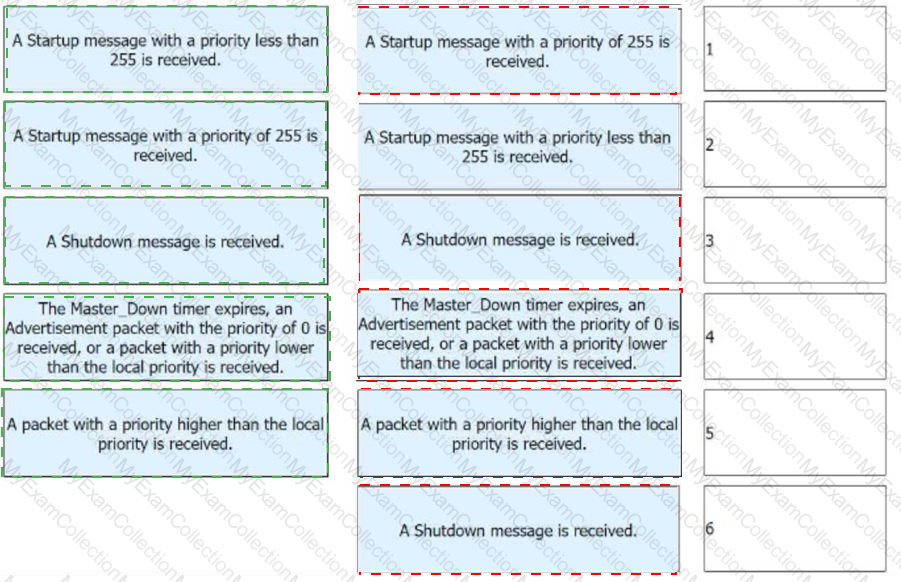
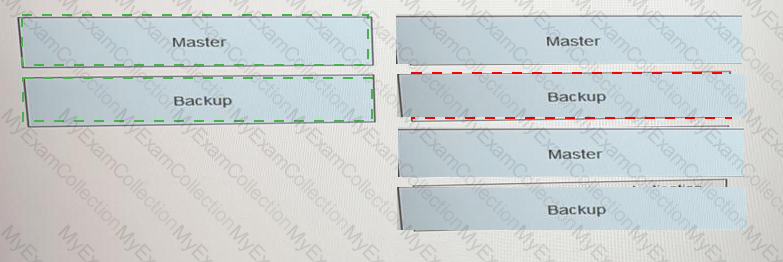
The figure shows the VRRP status switchover events. Match these events with their sequence numbers.
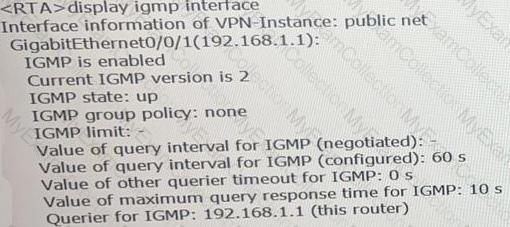
Which of the following statements is false, based on the following IGMP information on an interface of RTA?XC
On an OSPF network, if a router functions as an ABR, the router must also be a BR.
By default, some security zones are created when Huawei firewalls are enabled. Which of the following security zones is created by users?
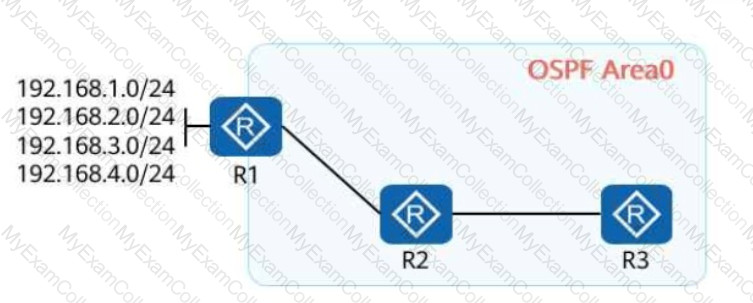
On the OSPF network shown in the figure, R1, R2, and R3 run OSPF, and R1 advertises four VPN routes to OSPF. A filter-policy needs to achieve the following goal: R1's and R3's routing tables contain the routes to 192.168.3.0/24, but R2's routing table does not. Which of the following filter-policies cannot meet this requirement?
On an IS-IS network, areas are divided by router, and a router can belong to only one area. Therefore, an IS-IS router only needs to maintain the LSDB of its area.
On an OSPF network, interfaces are classified into four types based on link layer protocols. Which of the following types can interfaces on an IS-IS network be classified into based on physical links?
There are two types of BGP peer relationships: EBGP and IBGP. When configuring EBGP, ensure that the peer IP address is routable and the UDP connection can be correctly established.
On a network, each router has a local core routing table and protocol routing tables. A routing entry in the local core routing table has multiple key fields. Which of the following are included?
Which of the following statements regarding routing policy and policy-based routing are true?
ON a stateful inspection Firewall where there is no session table, when the status detection mechanism is enabled and the second packet (CYN+ACK) of 3-way hadshakes reaches the firewall. Which of the following statements is true?
STP ensures a loop-free network but has a slow network topology convergence speed, affecting communication quality. RSTP has made some improvements based on STP. Which of the following improvements is not included?
Which of the following TLVs is used by ISIS to describe the IP address of an interface?
A route-policy consists of one or more nodes. What is the maximum number of nodes in a route-policy?
The traffic limiting policy feature only supports the number of connections initiated by the specified IP or the number of connections received.
Which of the following values is the Reserved/Circuit Type field in the IIH packets sent by a Level-1-2 router on an IS-IS network?
After BGP initiates a TCP connection, the ConnectRetry timer is disabled if the TCP connection is successfully established. If the TCP connection fails to be established, the device tries to reestablish the TCP connection when the ConnectRetry timer expires.
Which of the following attributes cannot be directly referenced in an apply clause of a route-policy?
A company has a stack consisting of three switches that are running properly. The master switch restarts due to a fault. Given this, which of the following statements are true?
GRE is a Layer 2 VPN encapsulation technology that encapsulates packets of certain data link layer protocols so that the encapsulated packets can be transmitted over an IP network.
BGP is a distance-vector protocol that implements route reachability between ASs and selects optimal routes. Which of the following statements are true about this protocol?
During routine O&M, the administrator checks the IGMP configuration on a router interface. The configuration is as follows:
Interface information of VPN-Instance: public net
GigabitEthernet0/0/1(192.168.1.1):
IGMP is enabled
Current IGMP version is 2
IGMP state: up
IGMP group policy: none
IGMP limit: -
Value of query interval for IGMP (negotiated): -
Value of query interval for IGMP (configured): 60 s
Value of other querier timeout for IGMP: 0 s
Value of maximum query response time for IGMP: 10 s
Querier for IGMP: 192.168.1.1 (this router)
Given this, which of the following statements are true?
By default, a router interface sends PIM Hello messages at an interval of __________ seconds.
RSTP provides different functions in different scenarios. Which of the following statements Is false?
In IP multicast transmission, packets are transmitted from a source to a group of receivers. Which of the following statements are true about IP multicast technologies?
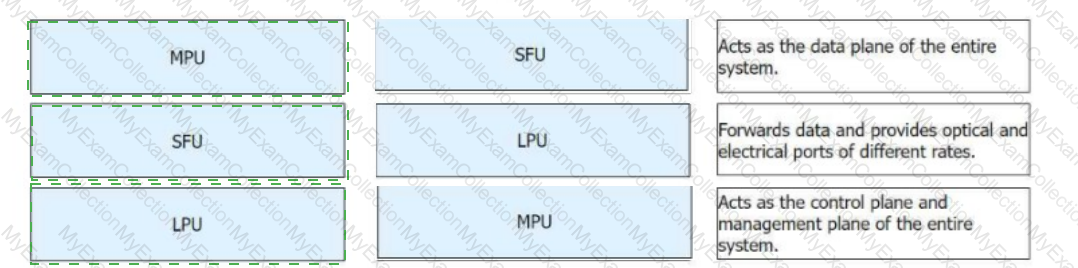
Huawei modular devices have multiple hardware modules that provide different functions. Match the following hardware modules with their functions.

The BFD Echo function checks the connectivity of the forwarding link by looping back packets. Which of the following statements are true about this function?
A session is an entry used to record the connection status of a protocol and is fundamental for the firewall to forward packets. Which of the following protocol packets will the firewall create sessions for?
ASPF enables the firewall to support multi-channel protocols such as FTP and to define security policies for complex applications.
On an IS-IS network, the length and components of a NET are the same as those of an NSAP. Which of the following NET fields is used to uniquely identify a host or router in an area?
See the command output of a router below. Which of the following statements is true?
OSPF Process 1 with Router ID 10.0.2.2
Interface: 10.0.12.2 (GigabitEthernet 0/0/0)
Cost: 1 State: BDR Type: Broadcast MTU: 1500
Priority: 1
Designated Router: 10.0.12.1
Backup Designated Router: 10.0.12.2
Timers: Hello 10 , Dead 40 , Poll 120 , Retransmit 5 , Transmit Delay 1
On the OSPF network shown in the figure, an adjacency has been established between R1 and R2. An engineer configures the commands in the figure on R2. In this case, which of the following routing entries may exist in the routing table of R2?

On an OSPF network, an IR in area 0 must be a BR, but an ASBR may not be an ABR.
If a router ID is configured in both the system via and the BGP view, BGP uses the router ID configured in the BGP view because the BGP view takes precedence over the system view.
On an IS-IS network, each device needs to be configured with a network entity title (NET), which consists of three parts, each containing different fields. Which of the following fields are contained in the Area Address part?
See the network shown in the following figure.
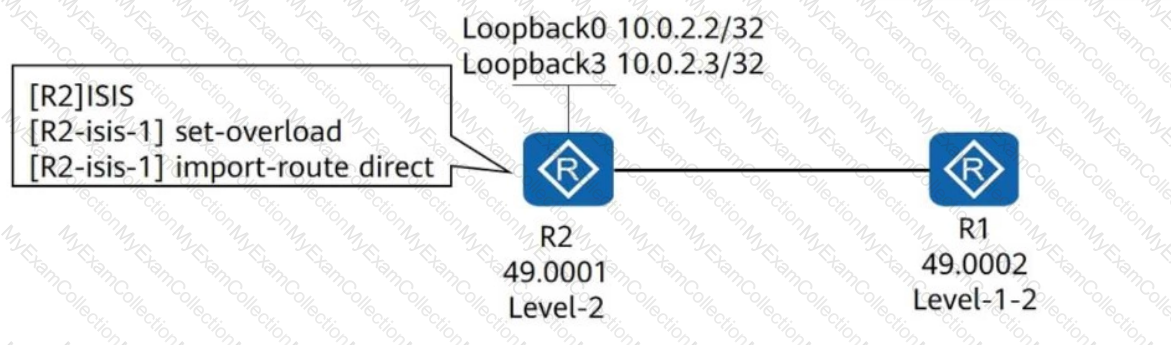
R1 and R2 run IS-IS and establish an adjacency. IS-IS is enabled on Loopback0 of R2 but disabled on Loopback3 of R2. The configurations shown in the figure are performed in the IS-IS process of R2. Which of the following statements are true?
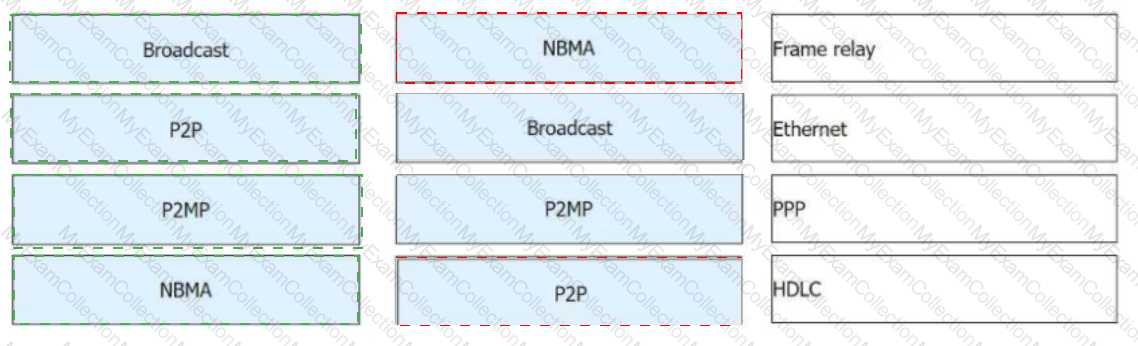
OSPF networks are classified into four types of networks by link layer protocol. Drag the following link layer protocols to the corresponding network types.(Token is reusable)

Compress the 2001:0DBB:B8:0000:C030:0000:0000:09A0:CDEF address.___________(if the answer contains letters, capitalize them.)
During BGP route summarization configuration, the keyword can be used to suppress all specific routes so that only the summary route is advertised. The summary route carries the Atomic-aggregate attribute rather than the community attributes of specific routes.
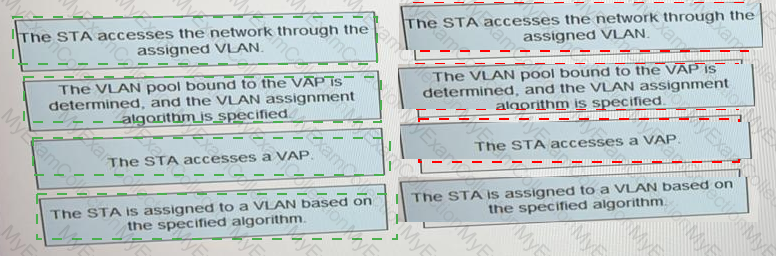
What is the correct procedure for a VLAN pool to assign terminals to VLANs.
A Huawei firewall by default creates security zones named untrust, dmz, _________ and local. (Use Lowercase letters.)
On an enterprise network, the directly connected interfaces of two OSPF routers are on different network segments and have different masks. To establish an OSPF neighbor relationship between the two interfaces, you can change their network types to which of the following?
An enterprise administrator configures route summarization on ASBRs to reduce the number of inter-area Type 3 LSAs, which in turn reduces the routing table size and improves device resource utilization.
On an STP network, only the designated port processes inferior BPDUs. On an RSTP network, a port with any role processes inferior BPDUs.
Which of the following statements regarding the stateful inspection firewall is true?
On an enterprise WLAN where Portal authentication is deployed, an AC functions as an access device and communicates with a Portal server using the Portal protocol. Which of the following statements are true about the Portal protocol?
There are various types of VPNs, which can be applied to different layers. Which of the following network layers does SSL VPN belong to?
Which of the following statements regarding Local-Preference in BGP is true?
Route attributes are specific descriptions of routes. BGP route attributes can be classified into four types. Which of the following are well-known discretionary attributes?
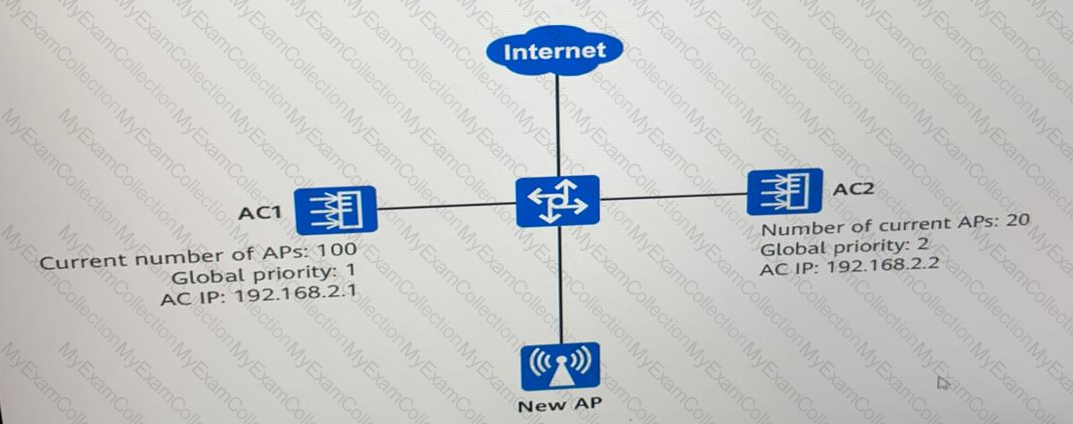
As shown in the following figure, a new AP is deployed In dual link MSB networking (load balancing mode). Which AC will the connect to?
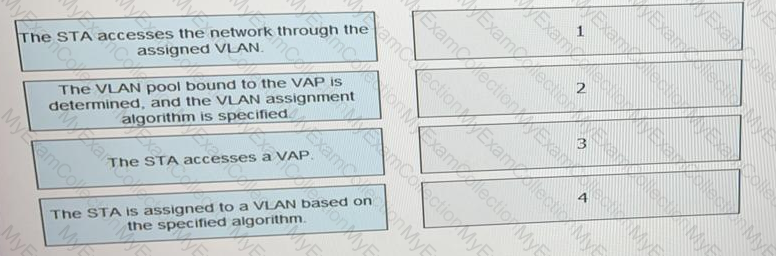
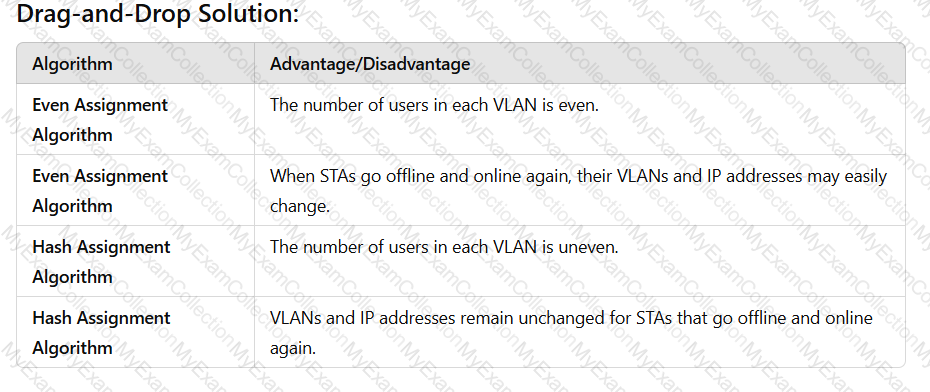
On a WLAN, engineers can use the VLAN pool mechanism to assign access users to different VLANs, which helps reduce the number of broadcast domains and improve network performance. VLAN pools support two VLAN assignment algorithms: even and hash. Drag the advantages and disadvantages to the two algorithms.(Token is reusable)
An engineer sets the CAPWAP heartbeat detection interval to 20 of the active link before an active/standby switchover occurs?
On an IS-IS network, two directly connected routers establish a neighbor relationship through the three-way handshake mechanism by default, regardless of whether the network type is P2P or broadcast.
To overcome the disadvantages of STP, RSTP changes the format of configuration BPDUs. Which of the following fields in STP BPDUs is used to specify the port role?
GRE is a VPN encapsulation technology that is widely used to transmit packets across heterogeneous networks. Which of the following statements is false about GRE?
An enterprise office network runs OSPF and is divided into multiple OSPF areas. Enterprise network engineers can configure route summarization on ASBRs to reduce the number of inter-area Type 3 LSAs, which in turn reduces the routing table size and improves device resource utilization.
An enterprise uses Huawei routers to deploy an IS-IS network for network-wide communication. An engineer wants to change the interface cost to control route selection. By default, which of the following values is the maximum cost that can be configured?
Depending on the type of algorithms used, routing protocols are classified into distance-vector protocols and link-state protocols. Which of the following routing protocols are link-state protocols?
After a BGP peer relationship is established between two ends, changing the router ID of one end resets the BGP peer relationship.
The Next_Hop attribute in BGP records the next hop of a route. Similar to the next hop in an IGP, the Next_Hop attribute in BGP must be the IP address of a peer interface.
Multicast applies to any point-to-multipoint data transmission. Which of the following types of application data can be forwarded in multicast mode?
OSPF neighbors have multiple states, such as Down, Init, 2-way, Loading, or Full. In which of the following states do OSPF routers negotiate the master and slave roles?
 A screenshot of a computer
Description automatically generated
A screenshot of a computer
Description automatically generated
