What is the protocol of the Router Advertisement (RA) packet, which is used in IPv6 stateless address auto-configuration?
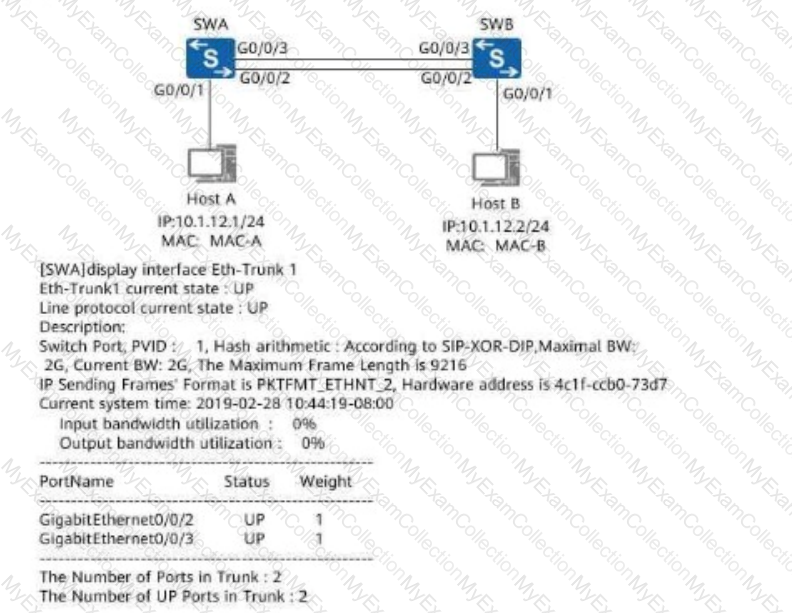
The following figure shows the display interface Eth-Trunk 1 command output on SWA. In the MAC address table of SWA, which of the following interfaces maps the MAC address of SWB?
Which of the following traffic can be filtered by an advanced ACL on a Huawei device?
The router ID of the OSPF-enabled router must be the same as the IP address of an interface on the router.
According to OSI reference model, which layer is responsible for end-to-end error checking and flow control?
Which of the following statements is true about root bridge election in STP?
According to the VTY user interface configuration shown in the following figure, the user level is set to 3.
Which of the following packets is used by network devices running SNMPv1 to proactively send alarm information?
Dynamic routing protocols can automatically adapt to network topology changes.
Following a failure of services in the network, an administrator discovered that the configuration in one of the enterprise routers had been changed. What actions can be taken by the administrator to prevent further changes?
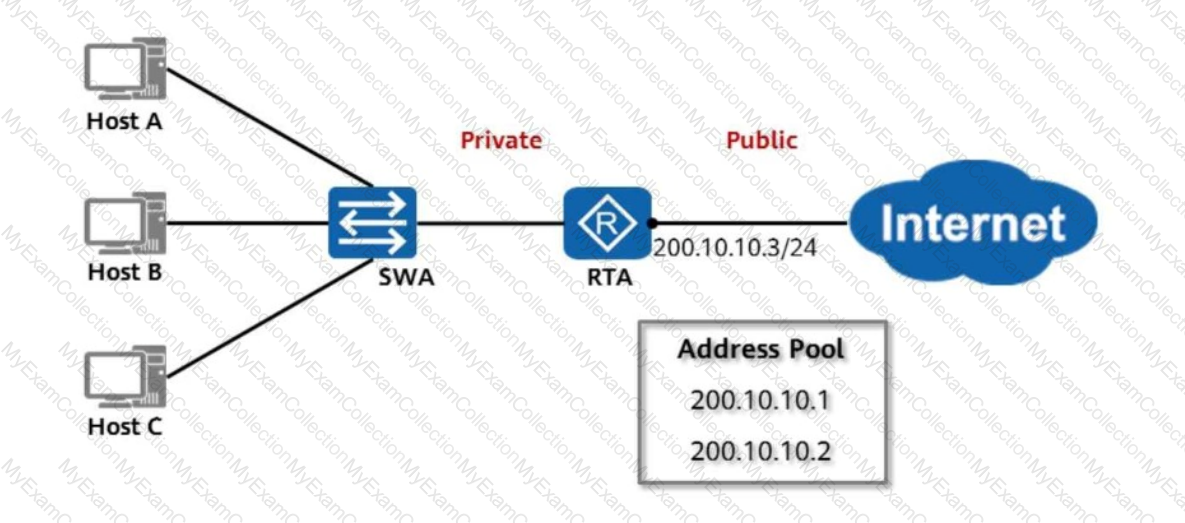
As shown in the figure, RTA uses NAT and has an address pool configured to implement many-to-many non-NAPT address translation, so that hosts on the private network can access the public network. Assume that the address pool has only two public IP addresses, which are translated for Host A and Host B. If Host C wants to access the public network, which of the following statements is true?
Refer to the following configuration of an interface on a switch. For which VLAN does the interface remove VLAN tags before forwarding data frames?
go
CopyEdit
interface GigabitEthernet0/0/1
port link-type trunk
port trunk pvid vlan 10
port trunk allow-pass vlan 10 20 30 40
When a host uses the stateless address autoconfiguration solution to obtain an IPv6 address, the host cannot obtain the DNS server address.
When an Ethernet frame is received by an interface on a Layer 2 Ethernet switch, which field is used to generate an entry in the MAC address table?
Which of the following percentage does the lease time of a DHCP client's IP address reach to trigger the DHCP client to send a lease renewal packet for the first time?
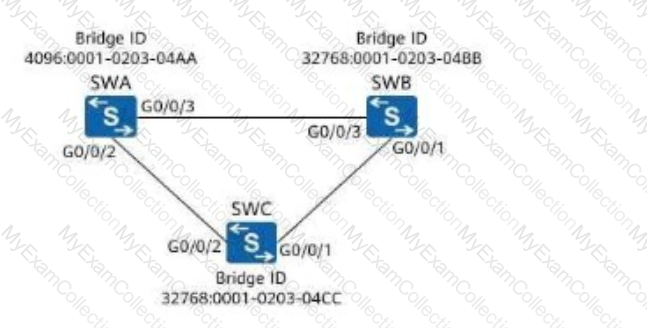
In the figure, bridge IDs of SWA, SWB, SWC, and SWD have been marked. After the stp root secondary command is run on SWD, which switch will be selected as the root bridge?

In which state does OSPF determine the master/slave relationship of DD packets?
Which of the following are true about the Ethernet data frame with the "Length/Type" field being 0x0806?
How many VLANs are created when using the following commands?
vlan batch 10 20
vlan batch 10 to 20
Which of the following commands is used to configure the country code on an AC?
As shown in the figure, the host has ARP cache. Host A sends a data packet to host B. Which of the following are the destination MAC address and destination IP address of the data packet?

Which of the following is the default value of the Router Dead Interval field in OSPF Hello packets on a broadcast network?
Which of the following BIDs cannot be contained in a configuration BPDU sent by a switch?
Refer to the following configuration of a switch interface. Which of the following statements is false?
interface GigabitEthernet0/0/1
port link-type trunk
port trunk pvid vlan 200
port trunk allow-pass vlan 100
By referring to the topology and the configurations of G0/0/1 interfaces on LSW1 and LSW2 shown in the figure, it can be determined that data frames tagged with VLAN 10 can be normally forwarded between LSW1 and LSW2.
Which of the following WLAN security policies support open link authentication?
Which of the following port states are included in Rapid Spanning Tree Protocol (RSTP)?
After an Eth-Trunk in LACP mode is created, devices on both ends send LACPDUs to elect the Actor. Which of the following parameters in LACPDUs determine the Actor election?
What is used as the data link-layer MAC address that identifies each VAP on an AP?
Which of the following statements is true about the Forward Delay timer of STP?
Which of the following commands sets the data forwarding mode on an AC to direct forwarding?
Which of the following statements about the network shown in the figure is true?
Which of the following IEEE 802.11 standards supports the 2.4 GHz frequency band only?
For multiple paths to the same destination network, the router needs to compare the preference values of the paths. If the preference values are the same, the router selects the paths based on the cost value.
On the network shown in the figure, host A logs in to router A through Telnet and obtains the configuration file of router B through FTP on the remote CLI. How many TCP connections exist on router A?
The network administrator has decided to configure link aggregation in the enterprise network. Which of the following represent advantages of link aggregation?
Refer to the graphic, 00e0-fc99-9999 is a specific host MAC address learned by a switch through ARP, and the host changes the IP address three times.
To provide the information about the IP addresses that a user packet traverses along the path to the destination, which of the following does Tracert record in each expired ICMP TTL packet?
What is the default lease time of the IP address allocated by the DHCP server?
While inspecting packets in the network, a network administrator discovers a frame with the destination MAC address of 01-00-5E-A0-B1-C3. What can the administrator determine from this?
Which of the following is not a common network layer in a midsize campus network?
Which of the following advantages is/are provided by inter-VLAN routing in one-arm routing mode?
What is used as the data link-layer MAC address that identifies each VAP on an AP?
If the application-layer protocol is Telnet, what is the value of the "Protocol" field in the IPv4 header?
Which of the following statements are true about the shortcut keys of the Versatile Routing Platform (VRP)?
On Huawei AR G3 Series routers, which authentication modes does AAA support?
In STP, which of the following items may affect the selection of the root switch?
After a switch restarts, static MAC address entries saved on the switch remain in the MAC address table.
Static NAT can only implement one-to-one mapping between private and public addresses.
Which of the following WLAN security policies support open link authentication?
When the header length of an IPv4 data packet is 20B and the total packet length is 1500B, what is the valid payload of the packet?
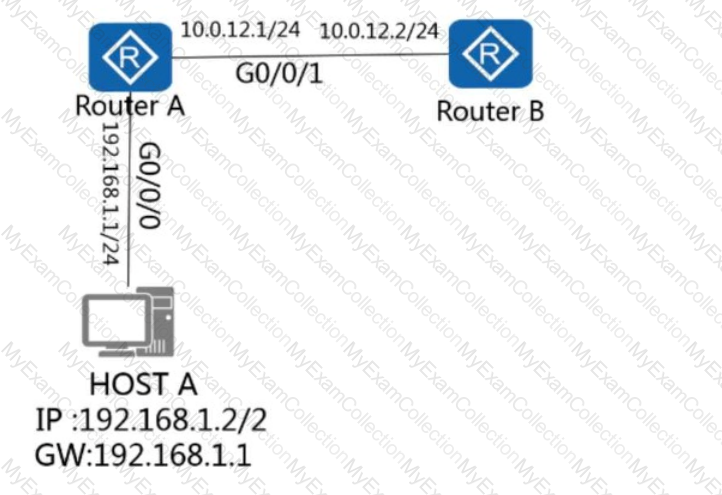
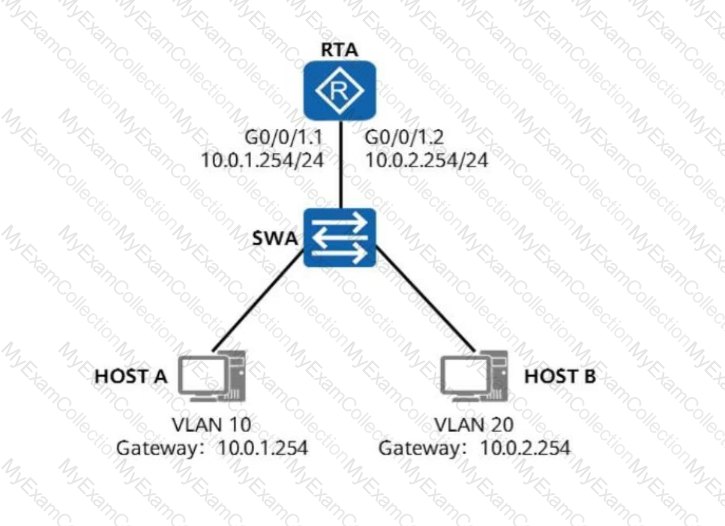
On the network shown in the figure, HOST A and HOST B are required to communicate with each other across VLANs through one-armed routing. To satisfy this requirement, which of the
following commands needs to be performed on G0/0/1.1 of RTA?
What is the length range of an Ethernet_II frame that contains an Ethernet header?
When redundant links exist on a switching network, STP can be used to eliminate loops.
If AAA authentication is used on Huawei devices and the remote server does not respond, the authentication can be performed on network devices.
Which of the following parameters is not contained in STP configuration BPDUs?
If the MAC address of an interface is 00E0-FCEF-0FEC, the corresponding EUI-64 address is ( ).
(Which of the following descriptions regarding the STP forwarding state is incorrect?)
When a router is powered on, the router reads the configuration file saved in the default save directory to get itself initialized. If the configuration file does not exist in the default save directory, what does the router use to initialize itself?
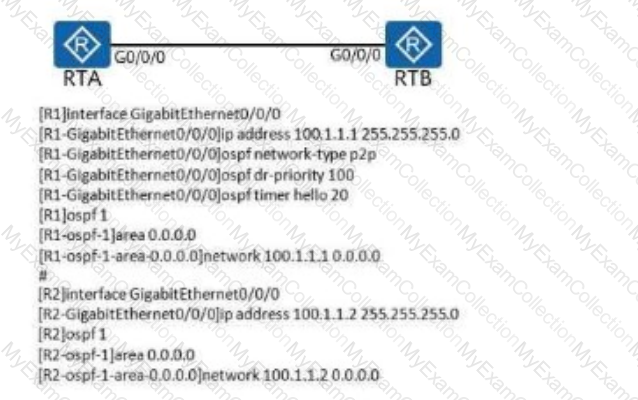
Refer to the graphic, which of the following statements is true about OSPF topology and configuration?
On the network shown in the following figure, assuming that SWA, SWB, and SWC retain factory defaults, which of the following ports will be selected as a designated port?
If the network administrator assigns the IPv4 address 192.168.1.1/28 to a host on the network, how many hosts can be added to the network where the host resides?
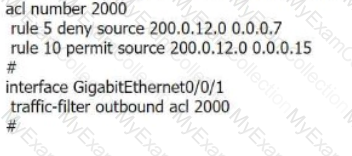
An ACL rule is as follows. Which of the following IP addresses can be matched by the permit rule?
rule 5 permit ip source 10.0.2.0 0.0.254.255
Network Address and Port Translation (NAPT) allows multiple private IP addresses to be mapped to the same public IP address through different port numbers. Which of the following statements about port numbers in NAPT is true?
On an STP-enabled switch, a port in the forwarding state can receive BPDU packets.
NAPT differentiates IP addresses of different users based on protocol ID in TCP, UDP, or IP packets.
On Huawei routers, which of the following is the default preference of static routing?
(If a routing table contains multiple routes to the same destination network, what are these routes called?)
As shown in the figure, the configuration of Router A is as follows. Which of the following statements is/are incorrect?
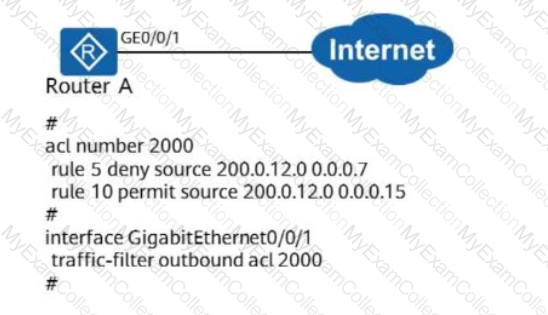
When a host uses the IP address 192.168.1.2 to access the Internet, NAT must be performed.
If Spanning Tree Protocol (STP) is disabled on the network consisting of switches, a Layer 2 loop will definitely occur.
When two switches are connected through link aggregation, what are the requirements for the interfaces on the two switches?
Which of the following are advantages of stacking and CSS (Cluster Switch System) technologies?
With SNMP, an NMS can only display the device running status but cannot deliver configurations.
If the broadcast address of a network is 172.16.1.255, which of the following addresses is the network address?
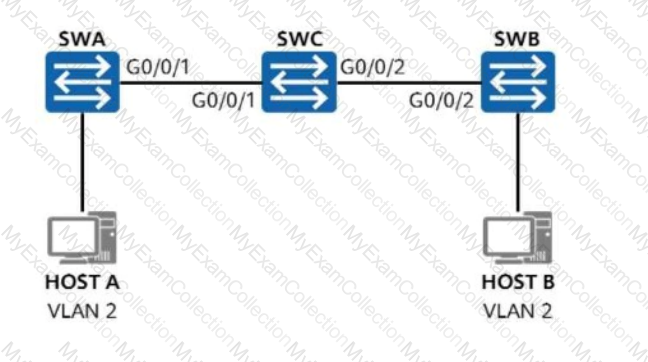
On the network shown in the figure, VLAN 2 is created on SWA and SWB, and interfaces connected to hosts are access ports added to VLAN 2. G0/0/1 on SWA and G0/0/2 on SWB are trunk interfaces allowing all VLANs. What additional configuration is needed on SWC to ensure communication between Host A and Host B?
The router ID of the OSPF process takes effect immediately after being changed.
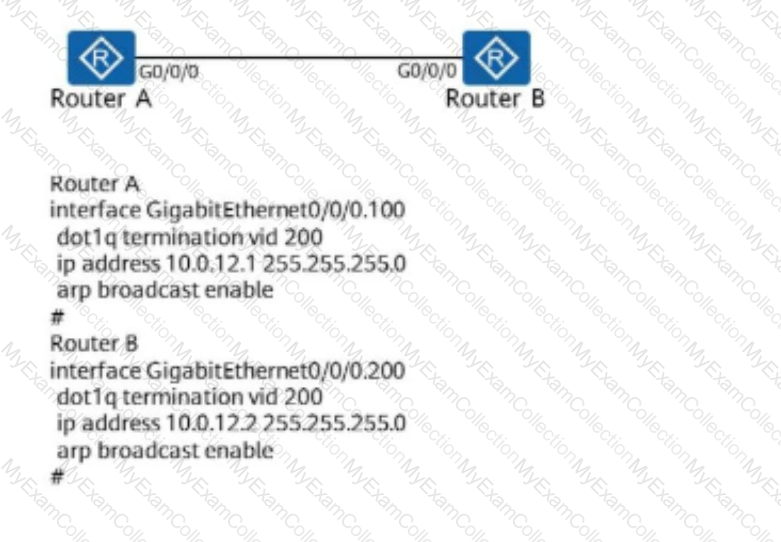
The following figure shows the configuration of a sub-interface on a router. For which VLAN does the sub-interface receive tagged data frames?
The data link layer uses PPP encapsulation. The IP addresses of the two ends of the link can be in different network segments.

