You work as a Network Administrator for XYZ CORP. The company has a Linux-based network. The company needs to provide secure network access. You have configured a firewall to prevent certain ports and applications from forwarding the packets to the company's intranet. What does a firewall check to prevent these ports and applications from forwarding the packets to the intranet?
You work as a Network Administrator for XYZ CORP. The company has a Windows Server 2008 network environment. The network is configured as a Windows Active Directory-based single forest single domain network. You have installed a Windows Server 2008 computer. You have configured auditing on this server. The client computers of the company use the Windows XP Professional operating system. You want to audit each event that is related to a user managing an account in the user database on the computer where the auditing is configured. To accomplish the task, you have enabled the Audit account management option on the server. Which of the following events can be audited by enabling this audit option?
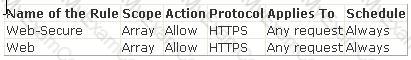
Sam works as a Web Developer for McRobert Inc. He creates a Web site. He wants to include the following table in the Web site:
He writes the following HTML code to create the table:
1.
| 8. | 10. | 12. |
16. | 18. | 20. |
Which of the following tags will Sam place at lines 3 and 4 to create the table?
George works as an office assistant in Soft Well Inc. The company uses the Windows Vista operating system. He wants to disable a program running on a computer. Which of the following Windows Defender tools will he use to accomplish the task?
Which of the following allows the use of multiple virtual servers using different DNS names resolved by the same IP address?
You are responsible for a large network that has its own DNS servers. You periodically check the log to see if there are any problems. Which of the following are likely errors you might encounter in the log? (Choose three)
You have recently joined as a Network Auditor in XYZ CORP. The company has a Windows-based network. You have been assigned the task to determine whether or not the company's goal is being achieved. As an auditor, which of the following tasks should you perform before conducting the data center review? Each correct answer represents a complete solution. Choose three.
Which of the following statements about a perimeter network are true? (Choose three)
You work as a professional Ethical Hacker. You are assigned a project to test the security of www.we-are-secure.com. You are working on the Windows Server 2003 operating system. You suspect that your friend has installed the keyghost keylogger onto your computer. Which of the following countermeasures would you employ in such a situation?
Which of the following is an attempt to give false information or to deny that a real event or transaction should have occurred?
Samantha works as a Web Developer for XYZ CORP. She develops a Web application using Visual InterDev. She wants to group a series of HTML elements together so that an action can be performed collectively on them. Which of the following tags will Samantha use to accomplish this?
Brutus is a password cracking tool that can be used to crack the following authentications: HTTP (Basic Authentication) HTTP (HTML Form/CGI) POP3 (Post Office Protocol v3) FTP (File Transfer Protocol) SMB (Server Message Block) Telnet Which of the following attacks can be performed by Brutus for password cracking?
In an IT organization, some specific tasks require additional detailed controls to ensure that the workers perform their job correctly. What do these detailed controls specify? (Choose three)
Many organizations create network maps of their network system to visualize the network and understand the relationship between the end devices and the transport layer that provide services. Which of the following are the techniques used for network mapping by large organizations? Each correct answer represents a complete solution. Choose three.
You work as a Network Administrator for XYZ CORP. The company has a Windows Server 2008 network environment. The network is configured as a Windows Active Directory-based single forest single domain network. You have installed a Windows Server 2008 computer as the domain controller. The client computers of the company use the Windows XP Professional operating system. When a user logs on to a client computer, it gets authenticated by the domain controller. You want to audit the logon events that would be generated on the domain controller. Which of the following audit settings do you need to configure to accomplish the task?
Which of the following types of servers are dedicated to provide resources to hosts on the network? (Choose three)
Which of the following wireless security standards supported by Windows Vista provides the highest level of security?
You are tasked with configuring your routers with a minimum security standard that includes the following: A local Username and Password configured on the router A strong privilege mode password Encryption of user passwords Configuring telnet and ssh to authenticate against the router user database Choose the configuration that best meets these requirements.
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to set the hard disk geometry parameters, cylinders, heads, and sectors. Which of the following Unix commands can you use to accomplish the task?
Every network device contains a unique built in Media Access Control (MAC) address, which is used to identify the authentic device to limit the network access. Which of the following addresses is a valid MAC address?
Which of the following is a prevention-driven activity to reduce errors in the project and to help the project meet its requirements?
John works as a Network Auditor for XYZ CORP. The company has a Windows-based network. John wants to conduct risk analysis for the company. Which of the following can be the purpose of this analysis? (Choose three)
You are concerned about rogue wireless access points being connected to your network. What is the best way to detect and prevent these?
In the DNS Zone transfer enumeration, an attacker attempts to retrieve a copy of the entire zone file for a domain from a DNS server. The information provided by the DNS zone can help an attacker gather user names, passwords, and other valuable information. To attempt a zone transfer, an attacker must be connected to a DNS server that is the authoritative server for that zone. Besides this, an attacker can launch a Denial of Service attack against the zone's DNS servers by flooding them with a lot of requests. Which of the following tools can an attacker use to perform a DNS zone transfer?
John works as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. John is working as a root user on the Linux operating system. He has a data.txt file in which each column is separated by the TAB character. Now, he wants to use this file as input for a data mining software he has created. The problem preventing him from accomplishing his task is that with his data mining software, he has used TAB as a delimiter to distinguish between columns. Hence, he is unable to use this file as input for the software. However, if he somehow replaces the TAB characters of the file with SPACE characters, he can use this file as an input file for his data mining software. Which of the following commands will John use to replace the TAB characters of the file with SPACE characters?
What is the purpose of Cellpadding attribute of