John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He finds that the We-are-secure server is vulnerable to attacks. As a countermeasure, he suggests that the Network Administrator should remove the IPP printing capability from the server. He is suggesting this as a countermeasure against __________.
Which of the following statements about Digest authentication are true?
Each correct answer represents a complete solution. Choose two.
The Project Scope Management knowledge area focuses on which of the following processes?
Each correct answer represents a complete solution. Choose all that apply.
A Web developer with your company wants to have wireless access for contractors that come in to work on various projects. The process of getting this approved takes time. So rather than wait, he has put his own wireless router attached to one of the network ports in his department. What security risk does this present?
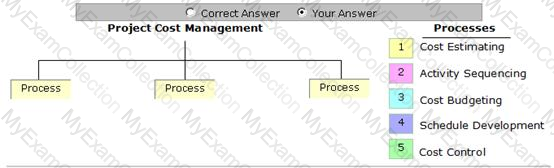
Place the processes that are grouped under the Project Cost Management Knowledge Area in the image below.

Which of the following security protocols can be used to support MS-CHAPv2 for wireless client authentication?
Each correct answer represents a complete solution. Choose two.
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He writes the following snort rule:
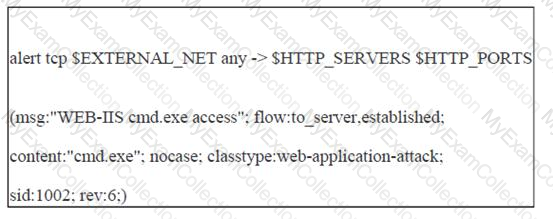
This rule can help him protect the We-are-secure server from the __________.
Which of the following are the types of access controls?
Each correct answer represents a complete solution. Choose three.
Which of the following is used to translate domain names into the numerical (binary) identifiers associated with networking equipment for the purpose of locating and addressing these devices worldwide?
Which of the following is a read-only copy of a zone and obtains its resource records from other name servers?
Which of the following blocks unwanted advertisements and small windows that pop up suddenly in IE, without user's initiation?
You work as a Network Administrator in a company. The NIDS is implemented on the network. You want to monitor network traffic. Which of the following modes will you configure on the network interface card to accomplish the task?
Mark works as a Network Administrator for We-are-secure Inc. He finds that the We-are-secure server has been infected with a virus. He presents to the company a report that describes the symptoms of the virus. A summary of the report is given below:
This virus has a dual payload, as the first payload of the virus changes the first megabyte of the hard drive to zero. Due to this, the contents of the partition tables are deleted and the computer hangs.
The second payload replaces the code of the flash BIOS with garbage values. This virus spreads under the Portable Executable File Format under Windows 95, Windows 98, and Windows ME.
Which of the following viruses has the symptoms as the one described above?
Which of the following is used to detect malicious activity such as port scans or even attempts for cracking into computers by monitoring network traffic?
Which of the following is the best encryption algorithm to encrypt and decrypt messages?
A honey pot is a computer trap that is used to attract potential intruders or attackers. Which of the following are some advantages of honey pots?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following encrypts its code differently with each infection or generation of infections?
Fill in the blank with the appropriate type of router.
A _________ router performs packet-filtering and is used as a firewall.
Which of the following is used to provide the service of exchanging data directly between two hosts on the same network?
John works as a professional Ethical Hacker. He has been assigned the task of testing the security of www.we-are-secure.com. He installs a sniffer on the We-are-secure server thinking that the following protocols of the We-are-secure server are being used in the network:
• HTTP
• SSL
• SSH
• IPSec
Considering the above factors, which of the following types of packets can he expect to see captured in encrypted form when he checks the sniffer's log file?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following generates MD5 hashes to check the MD5 value for each file processed and compares it with other MD5 strings?
Which of the following statements are true about WPA?
Each correct answer represents a complete solution. Choose all that apply.
You are the project manager of the HQQ Project for your company. You are working with your project stakeholders to discuss the risks in the project that can adversely affect the project objectives. You are discussing the possibilities of causes for an identified risk event in your project. Your stakeholder is confused on the difference between causes and risk events. Which of the following is NOT an example of a cause for a project risk?
You are the Network Administrator for a bank. In addition to the usual security issues, you are concerned that your customers could be the victim of phishing attacks that use fake bank Web sites.
Which of the following would protect against this?
Which of the following wireless security standards supported by Windows Vista provides the highest level of security?
You are concerned about possible hackers doing penetration testing on your network as a prelude to an attack. What would be most helpful to you in finding out if this is occurring?
Which of the following terms related to risk management represents the estimated frequency at which a threat is expected to occur?
A user is sending a large number of protocol packets to a network in order to saturate its resources and to disrupt connections to prevent communications between services. Which type of attack is this?
Which of the following tools can be used to read NetStumbler's collected data files and present street maps showing the logged WAPs as icons, whose color and shape indicates WEP mode and signal strength?
Dawn is the project manager of the HQQ Project and she believes the project work is done. She has prepared the final project report, which includes information on the financial performance, schedule performance, and project team performance in the project. All of the following documents are used to measure the completeness of the project scope except for which one?
Which of the following statements about a certification authority (CA) is true?
Holly is the project manager of the GHQ Project for her organization. The project is using the AAA IT Integrators Corporation as a vendor to do a portion of the project work. Mitch Smith, the IT Directors for the AAA IT Integrators Corporation, reports that his team has completed the project work. Holly and her team review the deliverables and she confirms that Mitch's team has indeed completed the work according to the statement of work. What document should Holly refer to now to determine the next course of action with the AAA IT Integrators Corporation?
Which of the following is used to identify a particular 802.11 wireless LAN?
You work as a Network Administrator for PassGuide Inc. Adam, your assistant, wants to perform a backup of the server. Which of the following authentication methods will you assign to Adam?
You work as a Network Administrator for Tech Perfect Inc. The company has a Windows Active Directory-based single domain single forest network. The functional level of the forest is Windows Server 2003. You install access points for enabling a wireless network. The sales team members and the managers in the company will be using laptops to connect to the LAN through wireless connections. Therefore, you install WLAN network interface adapters on their laptops. However, you want to restrict the sales team members and managers from communicating directly to each other. Instead, they should communicate through the access points on the network. Which of the following topologies will you use to accomplish the task?
You are the project manager of the NJJ project. Your enterprise environmental factors require that you establish certain risk management rules regarding low risks within your project. What is the best policy for risks with low probability and low impact in the project management?
Andrew works as a Software Developer for Mansoft Inc. The company's network has a Web server that hosts the company's Web site. Andrew wants to enhance the security of the Web site by implementing Secure Sockets Layer (SSL). Which of the following types of encryption does SSL use?
Each correct answer represents a complete solution. Choose two.
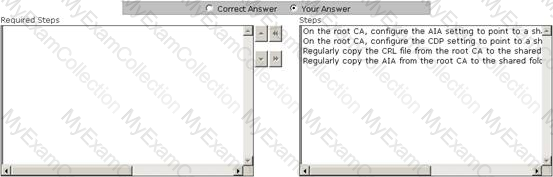
You work as a Network Administrator for Infonet Inc. The company has a Windows Server 2008 Active Directory-based single domain single forest network. The functional level of the forest is Windows Server 2003. All client computers on the network run Windows XP Professional. You configure a public key infrastructure (PKI) on the network. You configure a root CA and a subordinate CA on the network. For security reasons, you want to take the root CA offline. You are required to configure the CA servers to support for certificate revocation. Choose the steps you will require to accomplish the task.
You work as a project manager for TYU project. You are planning for risk mitigation. You need to identify the risks that will need a more in-depth analysis. Which of the following activities will help you in this?
Olive is the program manager for her organization. She has created a request for proposal for a large portion of her program. In this work to be procured she has set several requirements for the vendors to participate. The chief among these requirements is a vendor must have at least four licensed electricians in his team. This requirement for four licensed electricians is an example of which one of the following terms?
In which of the following attacks does an attacker create the IP packets with a forged (spoofed) source IP address with the purpose of concealing the identity of the sender or impersonating another computing system?
You have installed Windows Vista Home Premium on your home computer. The computer is connected to the Internet through an ADSL connection. You want to protect yourself from the traps of fraudulent sites. Which of the following features of Internet Explorer 7+ will you use?
You are a Network Administrator in an enterprise. You have been assigned the task of installing Windows 2000 and some other applications, on each computer on the network. But in the enterprise environment, it is not cost effective to install Windows 2000 and other applications, using the standard interactive setup on each computer. You plan to perform automated installation on multiple computers. Which of the following installation tasks can be automated?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Network Administrator for Blue Well Inc. The company has a Windows Server 2008 domain-based network. All client computers on the network run Windows Vista Ultimate. Andy, a Finance Manager, uses Windows Mail to download his e-mails to his inbox. He complains that every now and then he gets mails asking for revealing personal or financial information. He wants that such mails are not shown to him. Which of the following steps will you take to accomplish the task?
John works as a professional Ethical Hacker. He is assigned a project to test the security of www.weare-secure.com. He installs a rootkit on the Linux server of the We-are-secure network. Which of the following statements are true about rootkits?
Each correct answer represents a complete solution. Choose all that apply.
You are the program manager for your organization. You have proposed a program that will cost $750,000 and will last for four years. Management is concerned with the cost of the program in relation to the return your program will bring. If the rate of return is six percent what is the minimum value your project should return in four years based on the investment of the program?
Which of the following statements about Encapsulating Security Payload (ESP) are true?
Each correct answer represents a complete solution. Choose two.
You work as a Network Administrator for Infosec Inc. The company has a Windows 2003-based server. You have installed McAfee antivirus as well as anti-spyware software on the server. One day, you come to know that not only have the security applications running on the server (including software firewalls, anti-virus, and anti-spyware) been disabled, but the anti-virus and anti-spyware definitions have also been deleted. You suspect that this is due to malware infection. Which of the following types of malware is the most likely cause of the issue?
An organization has a standardized change management plan that all project managers must adhere to. A project manager has worked with the Change Control Board in his organization to approve a change to project scope. What should the standardized change management plan require the project manager to do with the approved scope change?
Which of the following password authentication schemes enables a user with a domain account to log on to a network once, using a password or smart card, and to gain access to multiple computers in the domain without being prompted to log in again?
What is the term used to describe the cost of the solution after the solution has been implemented in production by a vendor?
Which of the following layers of TCP/IP model is used to move packets between the Internet Layer interfaces of two different hosts on the same link?
Consider the following diagram:
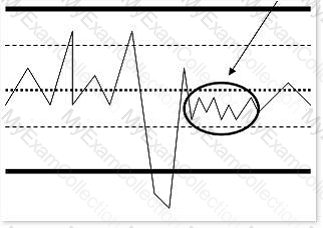
What is the highlighted area of the diagram known as?
Maria works as a professional Ethical Hacker. She has been assigned the project of testing the security of www.gentech.com. She is using dumpster diving to gather information about Gentech Inc. In which of the following steps of malicious hacking does dumpster diving come under?
Which of the following activities result in change requests?
Each correct answer represents a complete solution. Choose all that apply.
You are the program manager for your organization. Management has asked that you determine when resources, such as leased equipment, are no longer needed so that you may release the resources to save time, money, and utilization of resources within your program. What program management process is management asking you to perform?
Mark works as a Network Administrator for Infonet Inc. The company has a Windows 2000 Active Directory domain-based network. The domain contains one hundred Windows XP Professional client computers. Mark is deploying an 802.11 wireless LAN on the network. The wireless LAN will use Wired Equivalent Privacy (WEP) for all the connections. According to the company's security policy, the client computers must be able to automatically connect to the wireless LAN. However, the unauthorized computers must not be allowed to connect to the wireless LAN and view the wireless network. Mark wants to configure all the wireless access points and client computers to act in accordance with the company's security policy. What will he do to accomplish this?
Each correct answer represents a part of the solution. Choose three.
You are a project manager of a construction project. You are documenting project purchasing decisions, specifying the approach, and identifying potential sellers. You are in which of the following processes?
Which of the following tools works both as an encryption-cracking tool and as a keylogger?
A sequence number is a 32-bit number ranging from 1 to 4,294,967,295. When data is sent over the network, it is broken into fragments (packets) at the source and reassembled at the destination system. Each packet contains a sequence number that is used by the destination system to reassemble the data packets in the correct order. The Initial Sequence Number of your computer is 24171311 at login time. You connect your computer to a computer having the IP address 210.213.23.21. This whole process takes three seconds. What will the value of the Initial Sequence Number be at this moment?
Mark works as a Network Administrator for Technet Inc. The company has a Windows 2003 domainbased network. The network has a file server that uses a RAID-5 volume. The RAID-5 volume is configured with five hard disk drives. Over the weekend, a drive in the RAID-5 volume fails. What will Mark do to restore the RAID-5 volume?
Which of the following tools is a Windows-based commercial wireless LAN analyzer for IEEE 802.11b and supports all high level protocols such as TCP/IP, NetBEUI, and IPX?
You are concerned about rogue wireless access points being connected to your network. What is the best way to detect and prevent these?
Maria works as a professional Ethical Hacker. She recently has been assigned a project to test the security of www.we-are-secure.com. The company has provided the following information about the infrastructure of its network:
• Network diagrams of the we-are-secure infrastructure
• Source code of the security tools
• IP addressing information of the we-are-secure network
Which of the following testing methodologies is we-are-secure.com using to test the security of its network?
Which of the following types of security will be the cause of concern if the server has been stolen from the organization's premises?
Which of the following terms describes the statement given below?
"It is a service on a computer system (usually a server) that delays incoming connections for as long as possible. The technique was developed as a defense against a computer worm, and the idea is that network abuses, such as spamming or broad scanning, are less effective if they take too long."
Part of your change management plan details what should happen in the change control system for your project. Theresa, a junior project manager, asks what the configuration management activities are for scope changes. You tell her that all of the following are valid configuration management activities except for which one?
You are the project manager of the GYG Project. A new scope change is being considered for your project. You are concerned, however, that the scope change may add costs, risks, and adversely affect the project schedule. What project management process is responsible for evaluating the full effect of a proposed scope change on your project?
Which of the following are based on malicious code?
Each correct answer represents a complete solution. Choose two.
Which of the following types of attacks cannot be prevented by technical measures only?
You work as a Network Administrator for McNeil Inc. The company has a Windows Server 2008 network environment. The network is configured as a Windows Active Directory-based single forest domain-based network. The company's management has decided to provide laptops to its sales team members. These laptops are equipped with smart card readers. The laptops will be configured as wireless network clients. You are required to accomplish the following tasks:
ï¬ï€ The wireless network communication should be secured.
ï¬ï€ The laptop users should be able to use smart cards for getting authenticated.
In order to accomplish the tasks, you take the following steps:
ï¬ï€ Configure 802.1x and WEP for the wireless connections.
ï¬ï€ Configure the PEAP-MS-CHAP v2 protocol for authentication
What will happen after you have taken these steps?
The Incident handling process implemented in an enterprise is responsible to deal with all the incidents regarding the enterprise. Which of the following procedures will be involved by the preparation phase of the Incident handling process?
Which of the following refers to the process of verifying the identity of a person, network host, or system process?
Which of the following attacks is any form of cryptanalysis where the attacker can observe the operation of a cipher under several different keys whose values are initially unknown, but where some mathematical relationship connecting the keys is known to the attacker?
You check the logs on several clients and find that there is traffic coming in on an odd port (port 1872). All clients have the Windows XP firewall turned on. What should you do to block this unwanted traffic?

