You work as a Network Administrator for Tech2tech Inc. You have configured a network-based IDS for your company.
You have physically installed sensors at all key positions throughout the network such that they all report to the command console.
What will be the key functions of the sensors in such a physical layout?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following utilities is used to verify the existence of a host in a network?
You work as a Network Administrator for Infonet Inc. The company has a Windows Server 2008 domain-based network. The network has three Windows Server 2008 member servers and 150 Windows Vista client computers. According to the company's security policy, you apply Windows firewall setting to the computers on the network. Now, you are troubleshooting a connectivity problem that might be caused by Windows firewall. What will you do to identify connections that Windows firewall allows or blocks?
Which of the following IDs is used to reassemble the fragments of a datagram at the destination point?
Fill in the blank with the appropriate term.
___________is the practice of monitoring and potentially restricting the flow of information outbound from one network to another
Which of the following command-line utilities is used to show the state of current TCP/IP connections?
Which of the following tools performs comprehensive tests against web servers for multiple items, including over 6100 potentially dangerous files/CGIs?
Andrew works as a System Administrator for NetPerfect Inc. All client computers on the network run on Mac OS X. The Sales Manager of the company complains that his MacBook is not able to boot. Andrew wants to check the booting process. He suspects that an error persists in the bootloader of Mac OS X. Which of the following is the default bootloader on Mac OS X that he should use to resolve the issue?
Mark works as a Network administrator for SecureEnet Inc. His system runs on Mac OS X. He wants to boot his system from the Network Interface Controller (NIC). Which of the following snag keys will Mark use to perform the required function?
Which of the following is a signature-based intrusion detection system (IDS) ?
You work as a Network Administrator for Tech Perfect Inc. The company has a TCP/IP-based routed network. You have recently come to know about the Slammer worm, which attacked computers in 2003 and doubled the number of infected hosts every 9 seconds or so. Slammer infected 75000 hosts in the first 10 minutes of the attack. To mitigate such security threats, you want to configure security tools on the network. Which of the following tools will you use?
The promiscuous mode is a configuration of a network card that makes the card pass all traffic it receives to the central processing unit rather than just packets addressed to it. Which of the following tools works by placing the host system network card into the promiscuous mode?
You are the Network Administrator for a large corporate network. You want to monitor all network traffic on your local network for suspicious activities and receive a notification when a possible attack is in process. Which of the following actions will you take for this?
Which of the following tools is used to detect spam email without checking the content?
You are the Administrator for a Windows 2000 based network that uses DHCP to dynamically assign IP addresses to the clients and DNS servers. You want to ensure that the DNS servers can communicate with another DNS server. Which type of query will you run to achieve this?
Which of the following tools are used to determine the hop counts of an IP packet?
Each correct answer represents a complete solution. Choose two.
Which of the following Web attacks is performed by manipulating codes of programming languages such as SQL, Perl, Java present in the Web pages?
You work as a Network Administrator for Tech Perfect Inc. The office network is configured as an IPv6 network. You have to configure a computer with the IPv6 address, which is equivalent to an IPv4 publicly routable address. Which of the following types of addresses will you choose?
Which of the following OSI layers is responsible for protocol conversion, data encryption/decryption, and data compression?
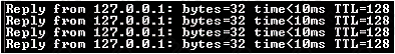
Which of the following utilities produces the output shown in the image below?
Which of the following utilities is used to display the current TCP/IP configuration of a Windows NT computer?
Fill in the blank with the appropriate term.
___________ is a technique used to make sure that incoming packets are actually from the networks that they claim to be from.
You work as a Network Administrator for McRobert Inc. Your company has a TCP/IP-based network. You want to get the protocol statistics and the active TCP/IP network connections of your computer. Which of the following will you use?
You work as a Network Administrator for NetTech Inc. You want to know the local IP address, subnet mask, and default gateway of a NIC in a Windows 98 computer. Which of the following utilities will you use to accomplish this ?
You work as a Network Administrator for Tech Perfect Inc. The company has a TCP/IP-based network.
You have configured a firewall on the network. A filter has been applied to block all the ports. You want to enable sending and receiving of emails on the network. Which of the following ports will you open?
Each correct answer represents a complete solution. Choose two.
Which of the following types of firewall ensures that the packets are part of the established session?
Sandra, an expert computer user, hears five beeps while booting her computer that has AMI BIOS; and after that her computer stops responding. Sandra knows that during booting process POST produces different beep codes for different types of errors. Which of the following errors refers to this POST beep code?
Adam works as a Security Administrator for Umbrella. A project has been assigned to him to test the network security of the company. He created a webpage to discuss the progress of the tests with employees who were interested in following the test. Visitors were allowed to click on a company's icon to mark the progress of the test. Adam successfully embeds a keylogger. He also added some statistics on the webpage. The firewall protects the network well and allows strict Internet access.
How was security compromised and how did the firewall respond?
Which of the following command line tools are available in Helix Live acquisition tool on Windows?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Network Security Administrator for NetPerfect Inc. The company has a Windowsbased network. You are incharge of the data and network security of the company. While performing a threat log analysis, you observe that one of the database administrators is pilfering confidential data. What type of threat is this?
Victor works as a professional Ethical Hacker for SecureNet Inc. He wants to use Steganographic file system method to encrypt and hide some secret information. Which of the following disk spaces will he use to store this secret information?
Each correct answer represents a complete solution. Choose all that apply.
Adam works as a professional Computer Hacking Forensic Investigator. A project has been assigned to him to investigate computer of an unfaithful employee of SecureEnet Inc. Suspect's computer runs on Windows operating system. Which of the following sources will Adam investigate on a Windows host to collect the electronic evidences?
Each correct answer represents a complete solution. Choose all that apply.
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He wants to send malicious data packets in such a manner that one packet fragment overlaps data from a previous fragment so that he can perform IDS evasion on the We-are-secure server and execute malicious data. Which of the following tools can he use to accomplish the task?
Which of the following intrusion detection systems (IDS) monitors network traffic and compares it against an established baseline?
Maria works as the Chief Security Officer for passguide Inc. She wants to send secret messages to the CEO of the company. To secure these messages, she uses a technique of hiding a secret message within an ordinary message. The technique provides 'security through obscurity'. What technique is Maria using?
Which of the following algorithms produces a digital signature which is used to authenticate the bit-stream images?
Which of the following attacks is designed to deduce the brand and/or version of an operating system or application?
Which of the following partitions contains the system files that are used to start the operating system?
Which of the following DOS commands is used to configure network protocols?
Adam works as a Computer Hacking Forensic Investigator in a law firm. He has been assigned with his first project. Adam collected all required evidences and clues. He is now required to write an investigative report to present before court for further prosecution of the case. He needs guidelines to write an investigative report for expressing an opinion. Which of the following are the guidelines to write an investigative report in an efficient way?
Each correct answer represents a complete solution. Choose all that apply.
What is the name of the group of blocks which contains information used by the operating system in Linux system?
Which of the following tools are used to determine the hop counts of an IP packet?
Each correct answer represents a complete solution. Choose two.
Which of the following methods is used by forensic investigators to acquire an image over the network in a secure manner?
Which of the following are the two sub-layers present in Data Link layer of the OSI Reference model?
Which of the following statements are true about an IPv6 network?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following NETSH commands for interface Internet protocol version 4 (IPv4) is used to delete a DNS server or all DNS servers from a list of DNS servers for a specified interface or for all interfaces?
Which of the following commands is used to flush the destination cache for IPv6 interface?
Which of the following wireless network standards operates on the 5 GHz band and transfers data at a rate of 54 Mbps?
Which of the following types of Intrusion detection systems (IDS) is used for port mirroring?
Which of the following NETSH commands for interface Internet protocol version 4 (IPv4) is used to delete a DNS server or all DNS servers from a list of DNS servers for a specified interface or for all interfaces?
Which of the following parts of hard disk in Mac OS X File system stores information related to the files?
Which of the following tools is used to recover data and partitions, and can run on Windows, Linux, SunOS, and Macintosh OS X operating systems?
Which of the following protocols is used to translate IP addresses to Ethernet addresses?
Which of the following Windows Registry key contains the password file of the user?
You work as a Network Administrator for McNeil Inc. The company's Windows 2000-based network is configured with Internet Security and Acceleration (ISA) Server 2000. You configure intrusion detection on the server. Which of the following alerts notifies that repeated attempts to a destination computer are being made and no corresponding ACK (acknowledge) packet is being communicated?
Which of the following ports is used by e-mail clients to send request to connect to the server?
________ is a command-line tool that can check the DNS registration of a domain controller.
Peter works as a System Administrator for TechSoft Inc. The company uses Linux-based systems.
Peter's manager suspects that someone is trying to log in to his computer in his absence. Which of the following commands will Peter run to show the last unsuccessful login attempts, as well as the users who have last logged in to the manager's system?
Each correct answer represents a complete solution. Choose two.
You work as a Network Administrator for McRobert Inc. Your company has a TCP/IP-based network.
You want to know the statistics of each protocol installed on your computer. Which of the following commands will you use?
Mark works as a Network Administrator for Infonet Inc. The company has a Windows 2000 domainbased network. Mark wants to block all NNTP traffic between the network and the Internet. How will he configure the network?
Which of the following partitions contains the system files that are used to start the operating system?
You work as a Network Administrator for PassGuide Inc. The company has deployed an ASA at the network perimeter. Which of the following types of firewall will you use to create two different communications, one between the client and the firewall, and the other between the firewall and the end server?
Andrew, a bachelor student of Faulkner University, creates a gmail account. He uses 'Faulkner' as the password for the gmail account. After a few days, he starts receiving a lot of e-mails stating that his gmail account has been hacked. He also finds that some of his important mails have been deleted by someone. Which of the following methods has the attacker used to crack Andrew's password?
Each correct answer represents a complete solution. Choose all that apply.

