Which of the following can be enabled on a Linux based system in order to make it more difficult for an attacker to execute malicious code after launching a buffer overflow attack?
An organization has implemented a policy to continually detect and remove malware from its network. Which of the following is a detective control needed for this?
What is the first step suggested before implementing any single CIS Control?
How often should the security awareness program be communicated to employees?
Janice is auditing the perimeter of the network at Sugar Water InC. According to documentation, external SMTP traffic is only allowed to and from 10.10.10.25. Which of the following actions would demonstrate the rules are configured incorrectly?
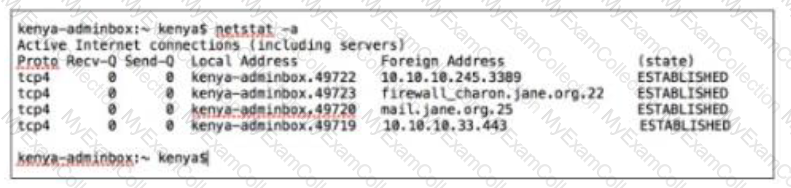
Kenya is a system administrator for SANS. Per the recommendations of the CIS Controls she has a dedicated host (kenya- adminbox / 10.10.10.10) for any administrative tasks. She logs into the dedicated host with her domain admin credentials. Which of the following connections should not exist from kenya-adminbox?
As part of a scheduled network discovery scan, what function should the automated scanning tool perform?
Which of the following is necessary for implementing and automating the Continuous Vulnerability Assessment and Remediation CIS Control?
An organization has created a policy that allows software from an approved list of applications to be installed on workstations. Programs not on the list should not be installed. How can the organization best monitor compliance with the policy?

