Which of the following is of most concern when attempting to root an Android device such as Google Glass
when conducting a forensic acquisition?
In 2015, Apple’s iTunes store was found to be hosting several malicious applications that were infected as a result of hacked version of the developer toolkit used to create applications. Which Apple developer suite was targeted?
The files pictured below from a BlackBerry OS10 file system have a unique file extension.
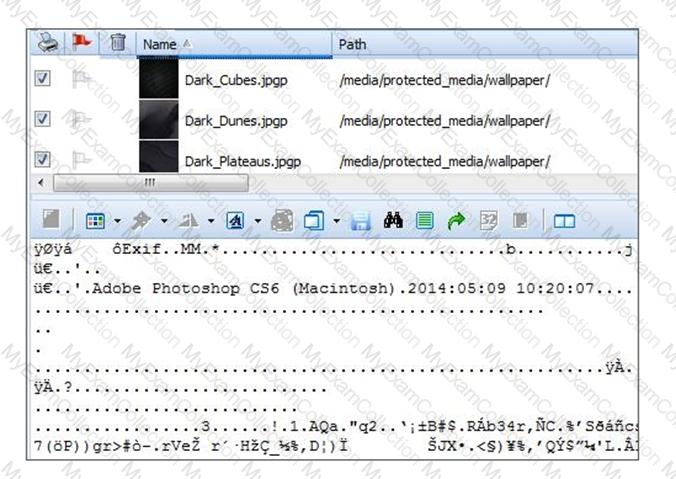
What can be concluded about these files?
While analysis in BlackBerry application list it appears that no third-party applications were installed on the device. Which other file may provide you with additional information on applications that were accessed with the handset?
Which of the following operating systems are used by Blackberry 10 and found in some vehicles and medical
devices?
Exhibit:
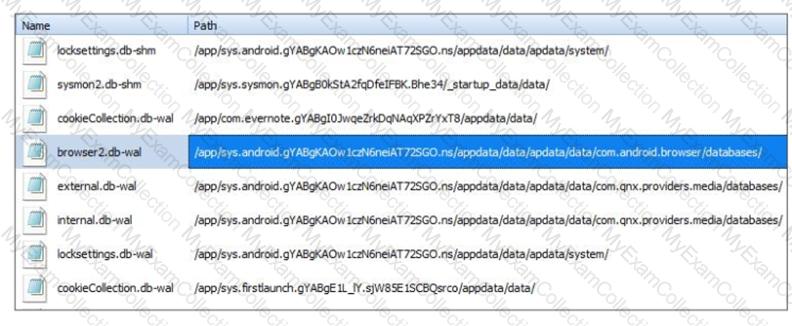
Where can an analyst find data to provide additional artifacts to support the evidence in the highlighted file?
Physical Analyzer provides a function to narrow down a search based on a timestamp, a type, a party or date.
What is the name of this advanced searching capability?
An analyst is investigating files on a Nokia S60 Symbian device and looking for data that would contain
possible cell tower locations, date and time stamps, phone numbers and/or references to files saved on the device. Which of the follow files would contain user data that was created and stored on the device that meet this criteria?