An organization wants to block all video and audio application traffic but grant access to videos from CNN Which application override action must you configure in the Application Control with Inline-CASB?
Which two components are part of onboarding a secure web gateway (SWG) endpoint? (Choose two)
To complete their day-to-day operations, remote users require access to a TCP-based application that is hosted on a private web server. Which FortiSASE deployment use case provides the most efficient and secure method for meeting the remote users' requirements?
Refer to the exhibits.
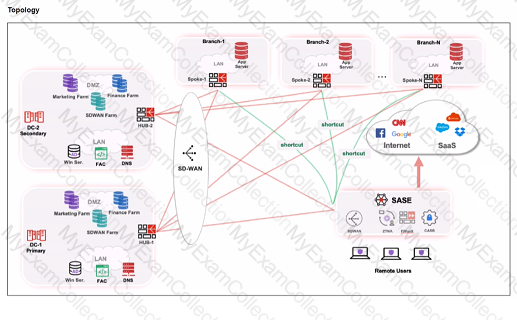
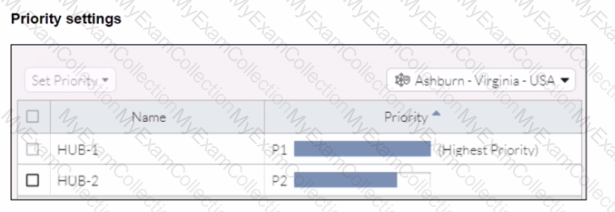
When remote users connected to FortiSASE require access to internal resources on Branch-2. how will traffic be routed?
Which FortiSASE feature ensures least-privileged user access to all applications?
When viewing the daily summary report generated by FortiSASE, the administrator notices that the report contains very little data.
What is a possible explanation for this almost empty report?
Refer to the exhibit.
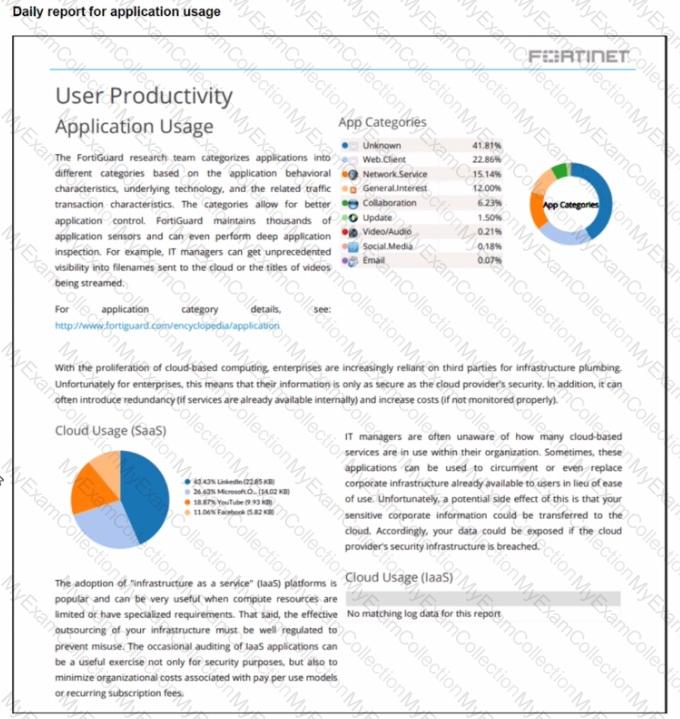
The daily report for application usage shows an unusually high number of unknown applications by category.
What are two possible explanations for this? (Choose two.)
Which role does FortiSASE play in supporting zero trust network access (ZTNA) principles9
Which secure internet access (SIA) use case minimizes individual workstation or device setup, because you do not need to install FortiClient on endpoints or configure explicit web proxy settings on web browser-based end points?

