Refer to the exhibit, which shows a truncated output of a real-time LDAP debug.
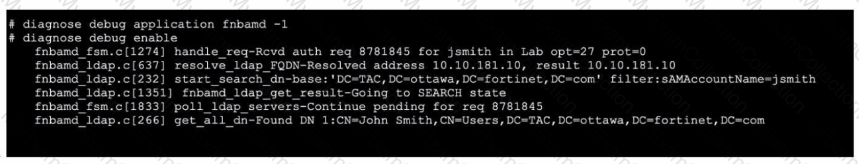
What two conclusions can you draw from the output? (Choose two.)
Refer to the exhibits.
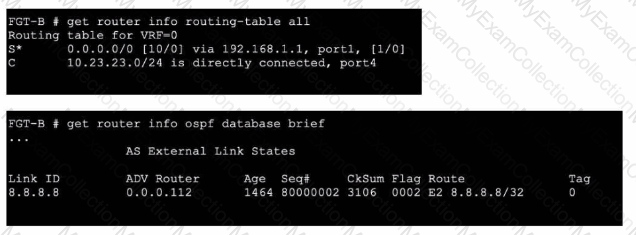
An administrator Is expecting to receive advertised route 8.8.8.8/32 from FGT-A. On FGT-B, they confirm that the route is being advertised and received, however, the route is not being injected into the routing table. What is the most likely cause of this issue?
Exhibit.
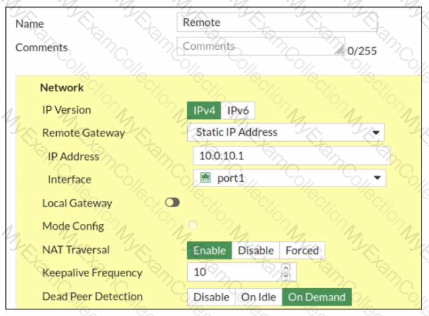
Refer to the exhibit, which contains a screenshot of some phase 1 settings.
The VPN is not up. To diagnose the issue, the administrator enters the following CLI commands on an SSH session on FortiGate:

However, the IKE real-time debug does not show any output. Why?
Refer to the exhibit, which shows the output of a policy route table entry.
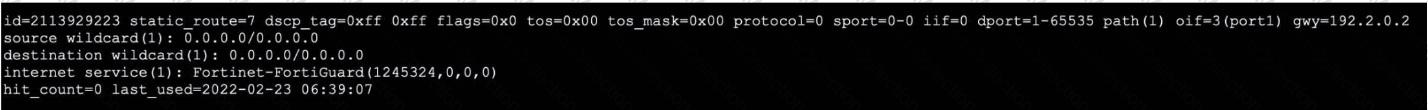
Which type of policy route does the output show?
Exhibit.
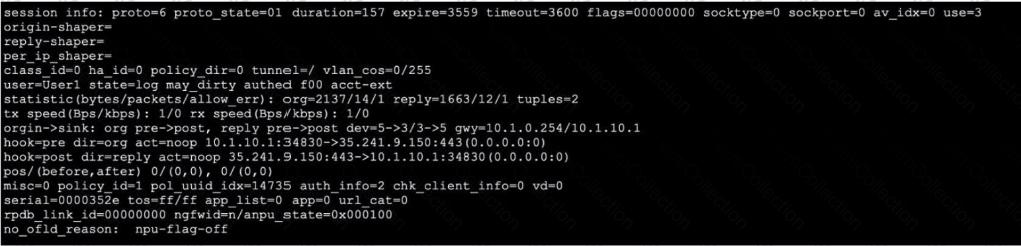
Refer to the exhibit, which shows the output of a session. Which two statements are true? (Choose Iwo.)
In which two slates is a given session categorized as ephemeral? (Choose two.)

