What happens to events that the collector receives when there is a WAN link failure between the collector and the supervisor?
A service provider purchased a 500-EPS license and configured a new collector with 100 EPS for customer A, and another collector with 200 EPS for customer B.
How much is in the remaining EPS pool for future customers and for MSSP itself?
Refer to the exhibit.
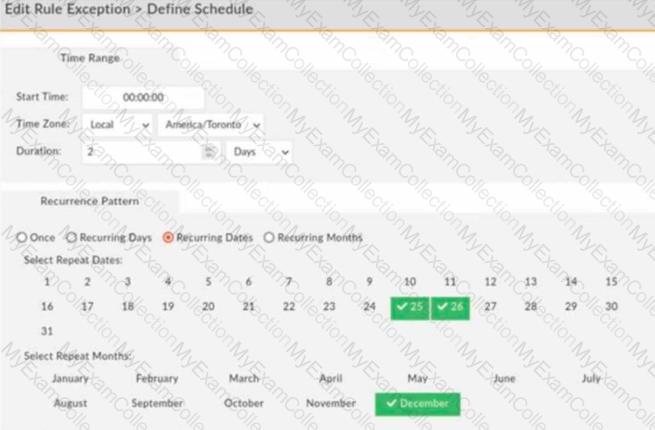
An administrator applies the rule exception shown in the exhibit.
How does this configuration impact the incident generation for that rule?
Why can collectorsnotbe defined before the worker upload address is set on the supervisor?
Why do collectors communicate with the Supervisor after registration? (Choose two.)
Refer to the exhibit.

Which workers are assigned tasks for the query ID13127? (Choose two.)
FortiSIEM provides all rules with the ability to automatically change an active incident status to auto-cleared, based on an extra set of defined criteria.
Why would you configure FortiSIEM to automatically change an active incident status to auto-cleared?
In a customer network that includes a collector, which device performs device discoveries?
Refer to the exhibit.
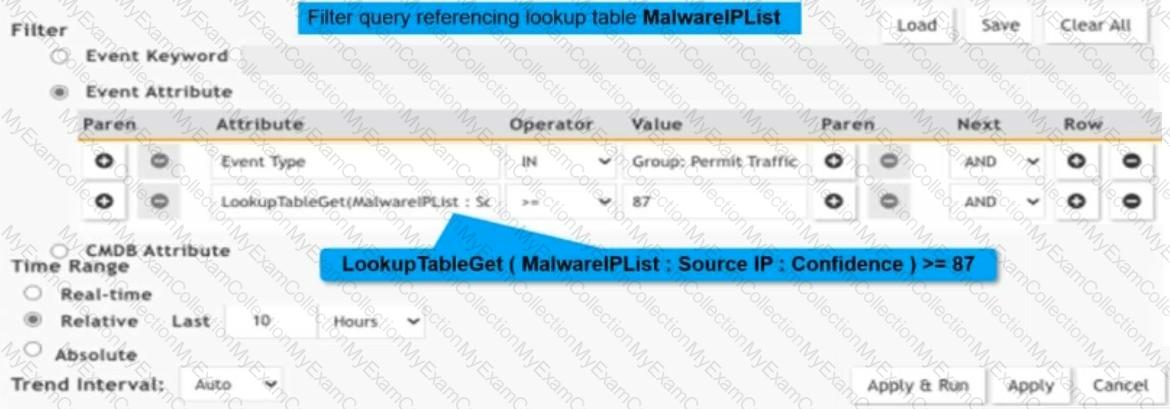
Consider a custom lookup tableMalwareIPList. An analyst constructed an analytic query to reference theMalwareIPListlookup table.
What is the outcome of the analytic query?
 If aworker node fails, thecollector can temporarily store event logsand then forward them to the Supervisor.
If aworker node fails, thecollector can temporarily store event logsand then forward them to the Supervisor. This ensuresevent continuityeven during infrastructure issues.
This ensuresevent continuityeven during infrastructure issues. Thecollector sends health reportsto theSupervisor, including resource usage, connectivity status, and operational logs.
Thecollector sends health reportsto theSupervisor, including resource usage, connectivity status, and operational logs. This helps FortiSIEM trackcollector uptime and performance.
This helps FortiSIEM trackcollector uptime and performance. The output doesnotshow any subdirectories or task files (13127t0,13127t1, etc.), meaningWorker1 is not assigned any tasks.
The output doesnotshow any subdirectories or task files (13127t0,13127t1, etc.), meaningWorker1 is not assigned any tasks. The output showsone task (13127t1)under/querywkr/active/13127*.
The output showsone task (13127t1)under/querywkr/active/13127*. The workerhas only one assigned task, not two, so optionsC and D are incorrect.
The workerhas only one assigned task, not two, so optionsC and D are incorrect. The output showstwo tasks (13127t0and13127t1), indicating that Worker3 is processingtwo tasksfor query ID 13127.
The output showstwo tasks (13127t0and13127t1), indicating that Worker3 is processingtwo tasksfor query ID 13127.
