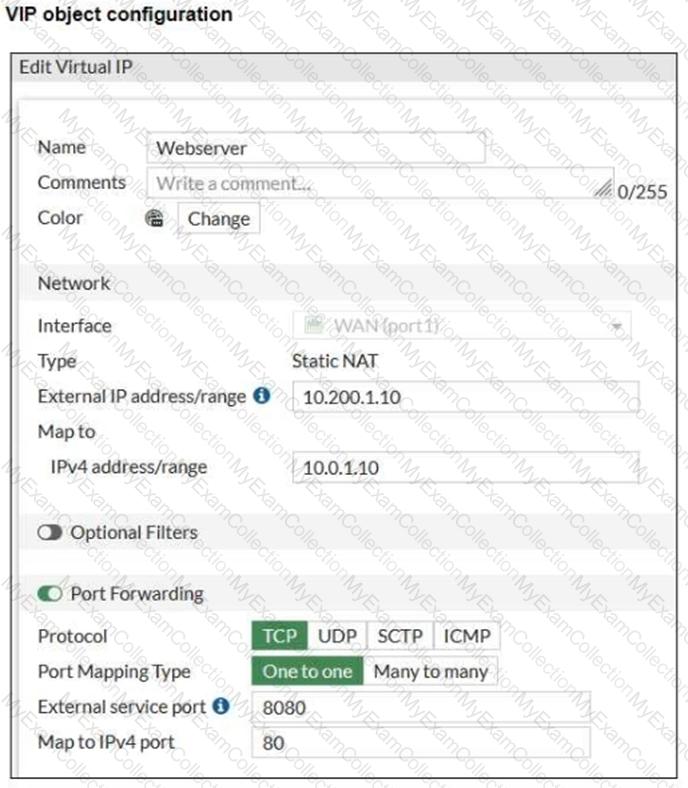
Refer to the exhibits, which show a diagram of a FortiGate device connected to the network. VIP object configuration, and the firewall policy configuration.
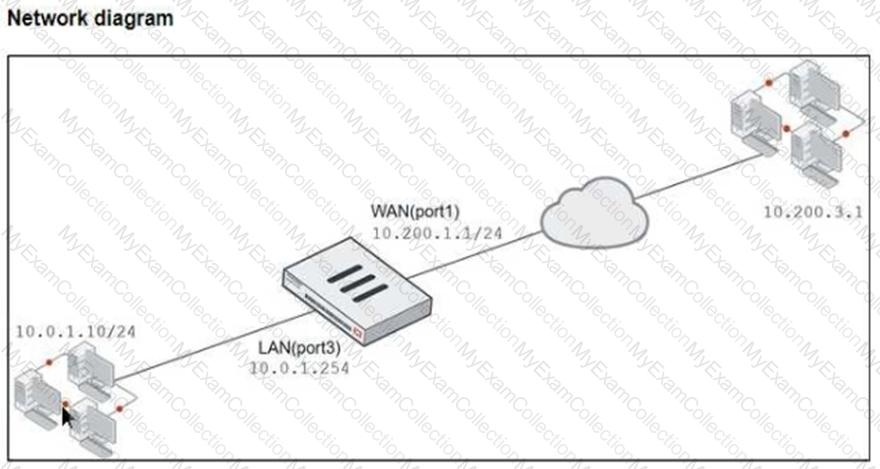

The WAN (port1) interface has the IP address 10.200.1.1/24. The LAN (port3) interface has the IP address 10.0.1.254/24.
If the host 10.200.3.1 sends a TCP SYN packet on port 8080 to 10.200.1.10, what will the source address, destination address, and destination port of the packet be at the time FortiGate forwards the packet to the destination?
An administrator configured a FortiGate to act as a collector for agentless polling mode.
What must the administrator add to the FortiGate device to retrieve AD user group information?
An administrator has configured a strict RPF check on FortiGate.
How does strict RPF check work?
An administrator configures FortiGuard servers as DNS servers on FortiGate using default settings.
What is true about the DNS connection to a FortiGuard server?
Which three strategies are valid SD-WAN rule strategies for member selection? (Choose three.)
A network administrator has configured an SSL/SSH inspection profile defined for full SSL inspection and set with a private CA certificate. The firewall policy that allows the traffic uses this profile for SSL inspection and performs web filtering. When visiting any HTTPS websites, the browser reports certificate warning errors.
What is the reason for the certificate warning errors?
Refer to the exhibit.
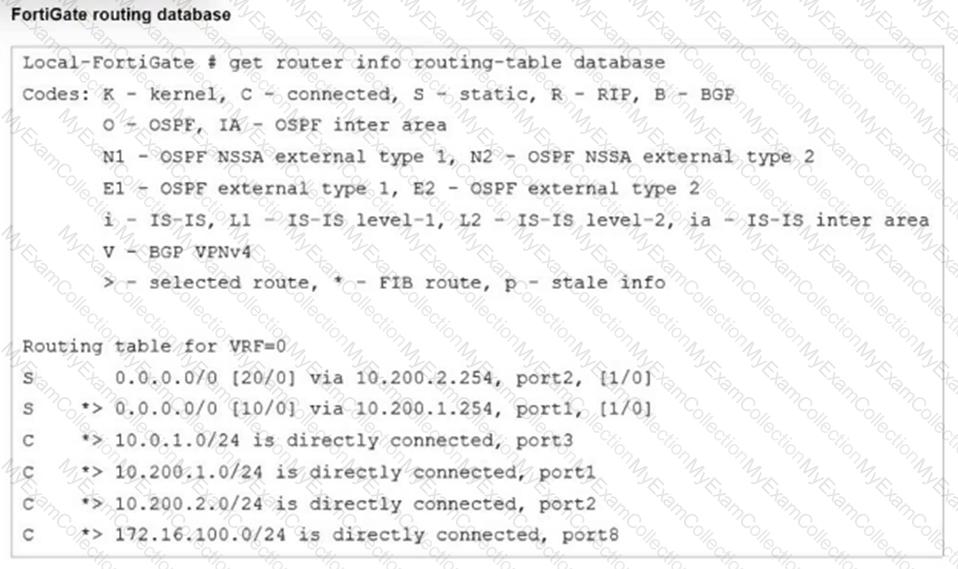
Which two statements are true about the routing entries in this database table? (Choose two.)
Refer to the exhibits.
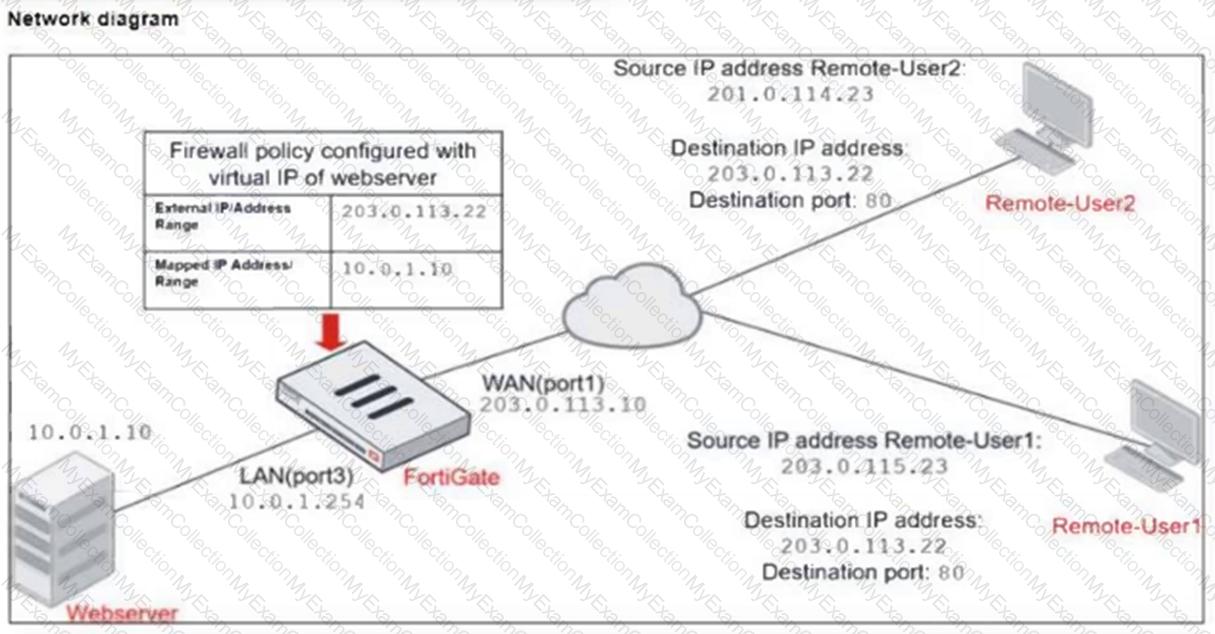
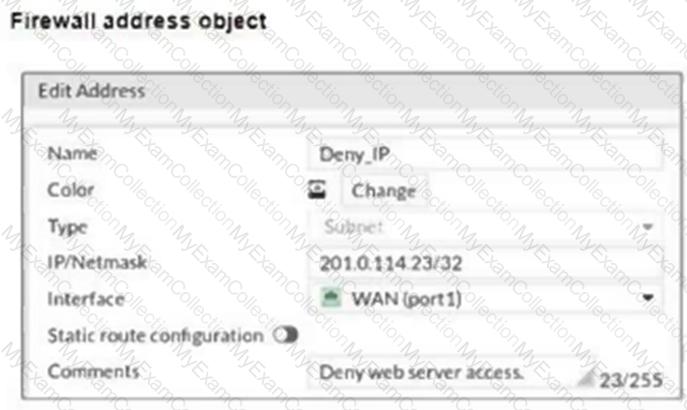
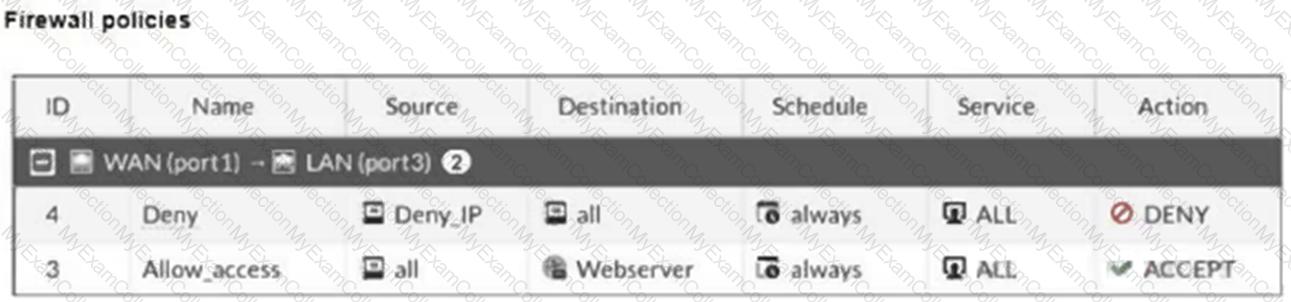
The exhibits show a diagram of a FortiGate device connected to the network, and the firewall configuration.
An administrator created a Deny policy with default settings to deny Webserver access for Remote-User2.
The policy should work such that Remote-User1 must be able to access the Webserver while preventing Remote-User2 from accessing the Webserver.
Which two configuration changes can the administrator make to the policy to deny Webserver access for Remote-User2? (Choose two.)
Which two statements are correct when FortiGate enters conserve mode? (Choose two.)
Which three statements explain a flow-based antivirus profile? (Choose three.)
Refer to the exhibits, which show the system performance output and the default configuration of high memory usage thresholds in a FortiGate.
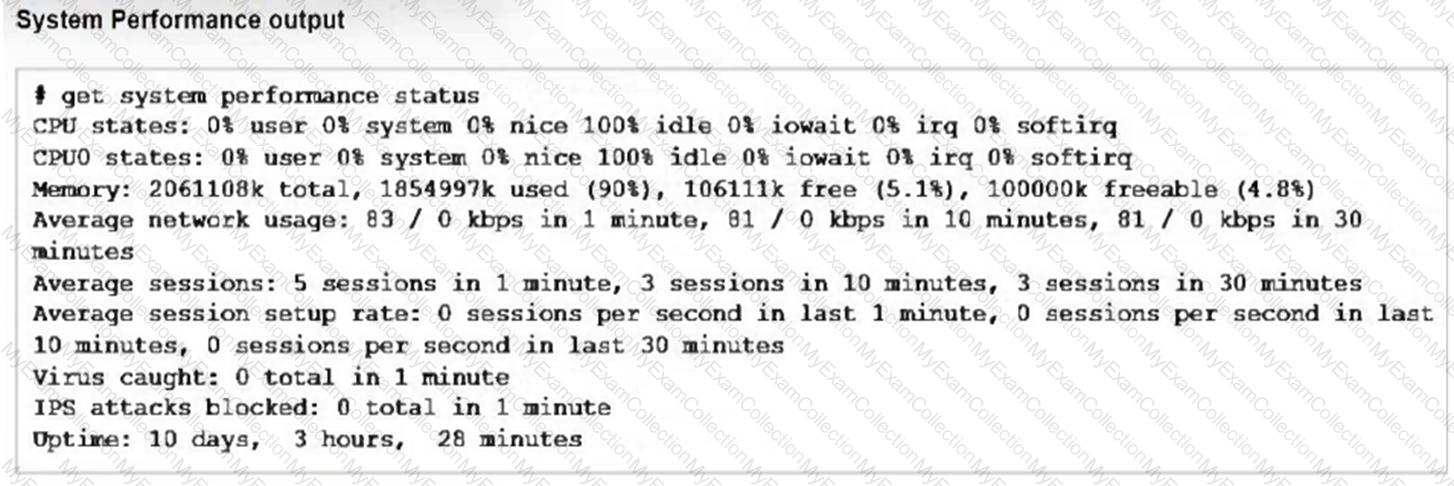
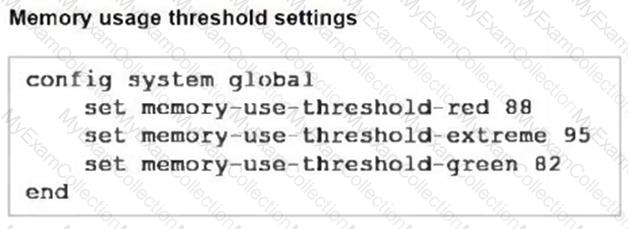
Based on the system performance output, what can be the two possible outcomes? (Choose two.)
Refer to the exhibit, which shows the IPS sensor configuration.
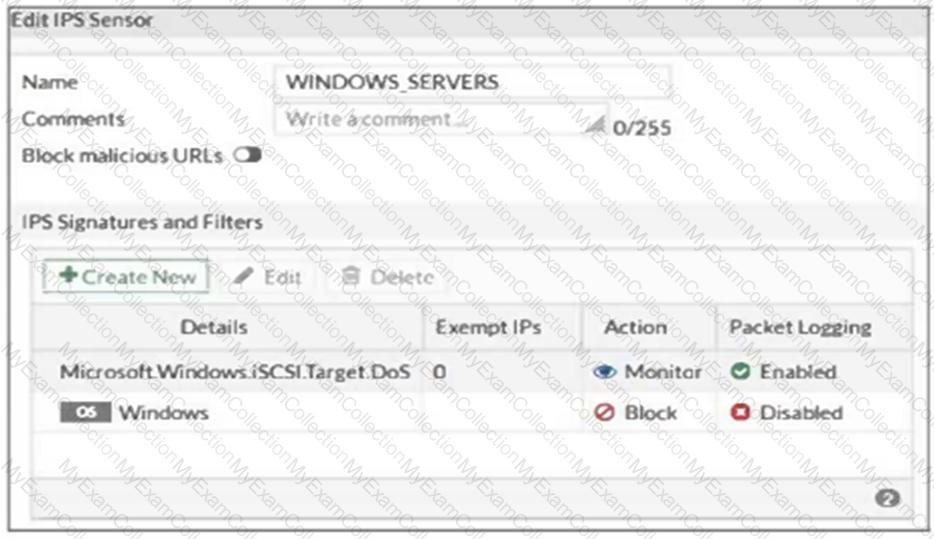
If traffic matches this IPS sensor, which two actions is the sensor expected to take? (Choose two.)
Refer to the exhibit showing a debug flow output.
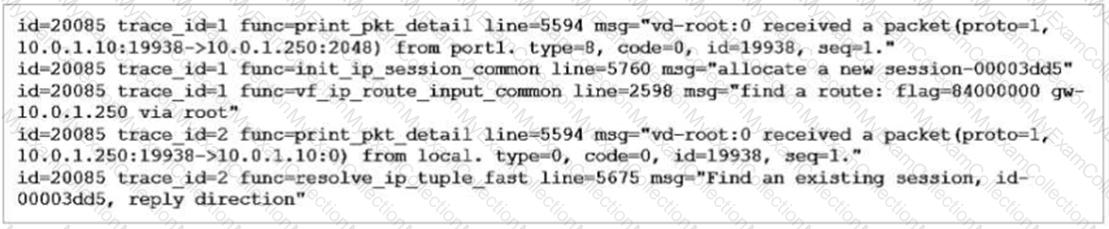
What two conclusions can you make from the debug flow output? (Choose two.)
Which three CLI commands, can you use to troubleshoot Layer 3 issues if the issue is in neither the physical layer nor the link layer? (Choose three.)
Refer to the exhibit.
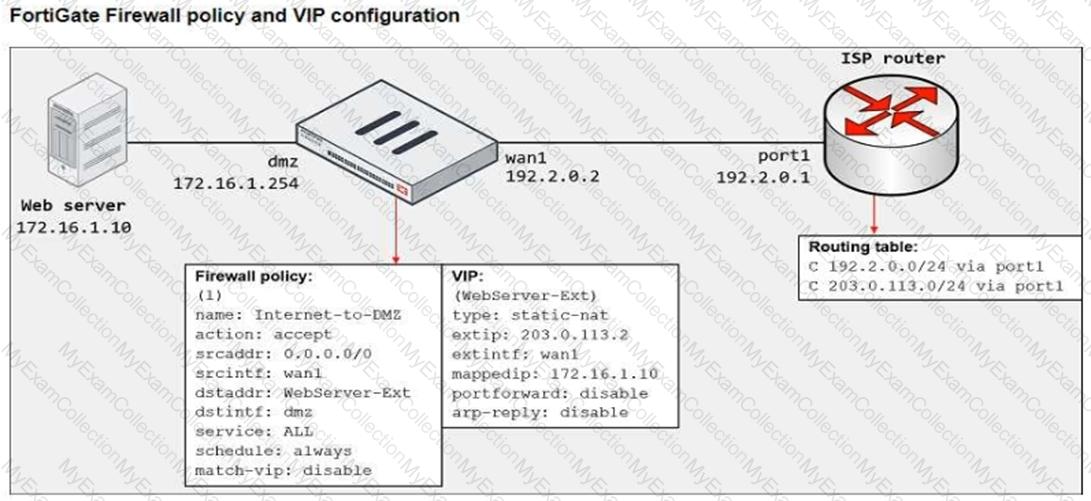
The exhibit shows a diagram of a FortiGate device connected to the network, the firewall policy and VIP configuration on the FortiGate device, and the routing table on the ISP router.
When the administrator tries to access the web server public address (203.0.113.2) from the internet, the connection times out. At the same time the administrator runs a sniffer on FortiGate to capture incoming web traffic to the server and does not see any output.
Based on the information shown in the exhibit, what configuration change must the administrator make to fix the connectivity issue?
When FortiGate performs SSL/SSH full inspection, you can decide how it should react when it detects an invalid certificate.
Which three actions are valid actions that FortiGate can perform when it detects an invalid certificate? (Choose three.)
Refer to the exhibit.
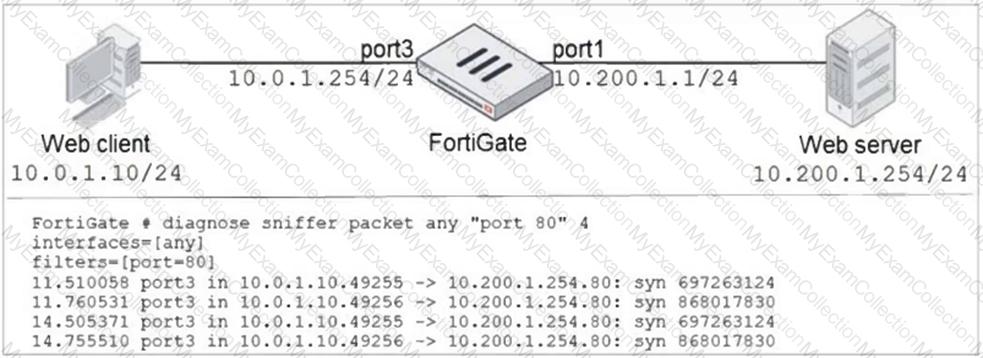
In the network shown in the exhibit, the web client cannot connect to the HTTP web server. The administrator runs the FortiGate built-in sniffer and gets the output shown in the exhibit.
What should the administrator do next, to troubleshoot the problem?
An administrator has configured the following settings:
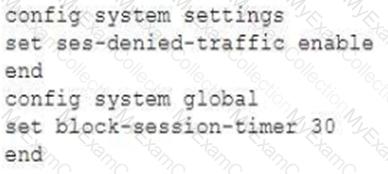
What are the two results of this configuration? (Choose two.)
Which two pieces of information are synchronized between FortiGate HA members? (Choose two.)
FortiGuard categories can be overridden and defined in different categories. To create a web rating override for the example.com home page the override must be configured using a specific syntax.
Which two syntaxes are correct to configure a web rating override for the home page? (Choose two.)
Refer to the exhibit to view the firewall policy.
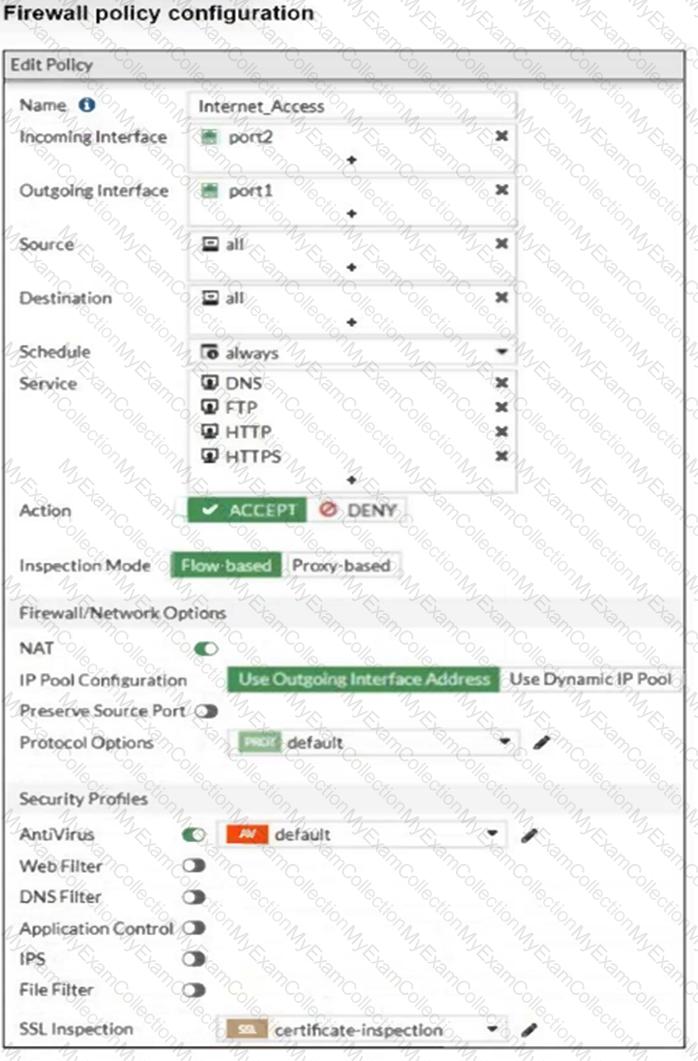
Why would the firewall policy not block a well-known virus, for example eicar?
Refer to the exhibit.
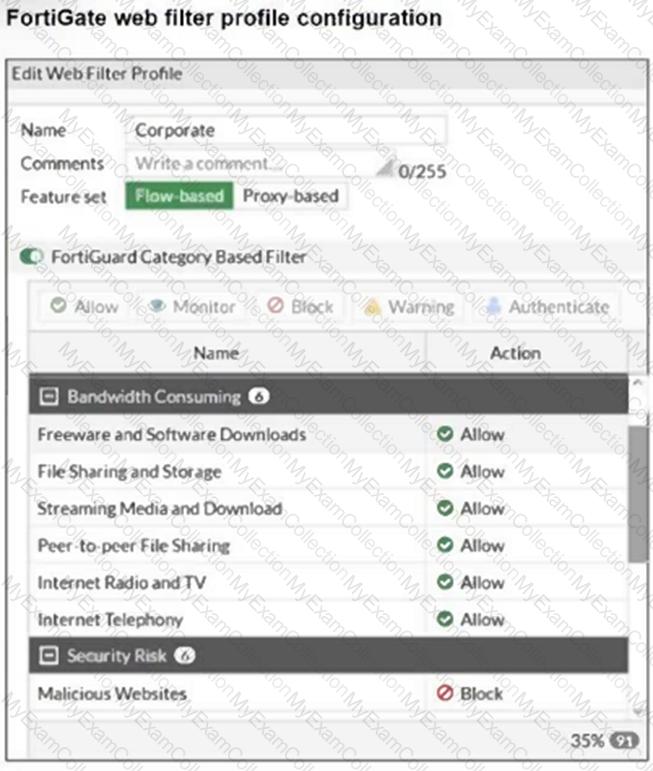
The exhibit shows the FortiGuard Category Based Filter section of a corporate web filter profile.
An administrator must block access to download.com, which belongs to the Freeware and Software Downloads category. The administrator must also allow other websites in the same category.
What are two solutions for satisfying the requirement? (Choose two.)
A network administrator enabled antivirus and selected an SSL inspection profile on a firewall policy.
When downloading an EICAR test file through HTTP, FortiGate detects the virus and blocks the file. When downloading the same file through HTTPS, FortiGate does not detect the
and does not block the file allowing it to be downloaded.
The administrator confirms that the traffic matches the configured firewall policy.
What are two reasons for the failed virus detection by FortiGate? (Choose two.)

