Refer to the exhibit, which shows the endpoint summary information on FortiClient EMS.
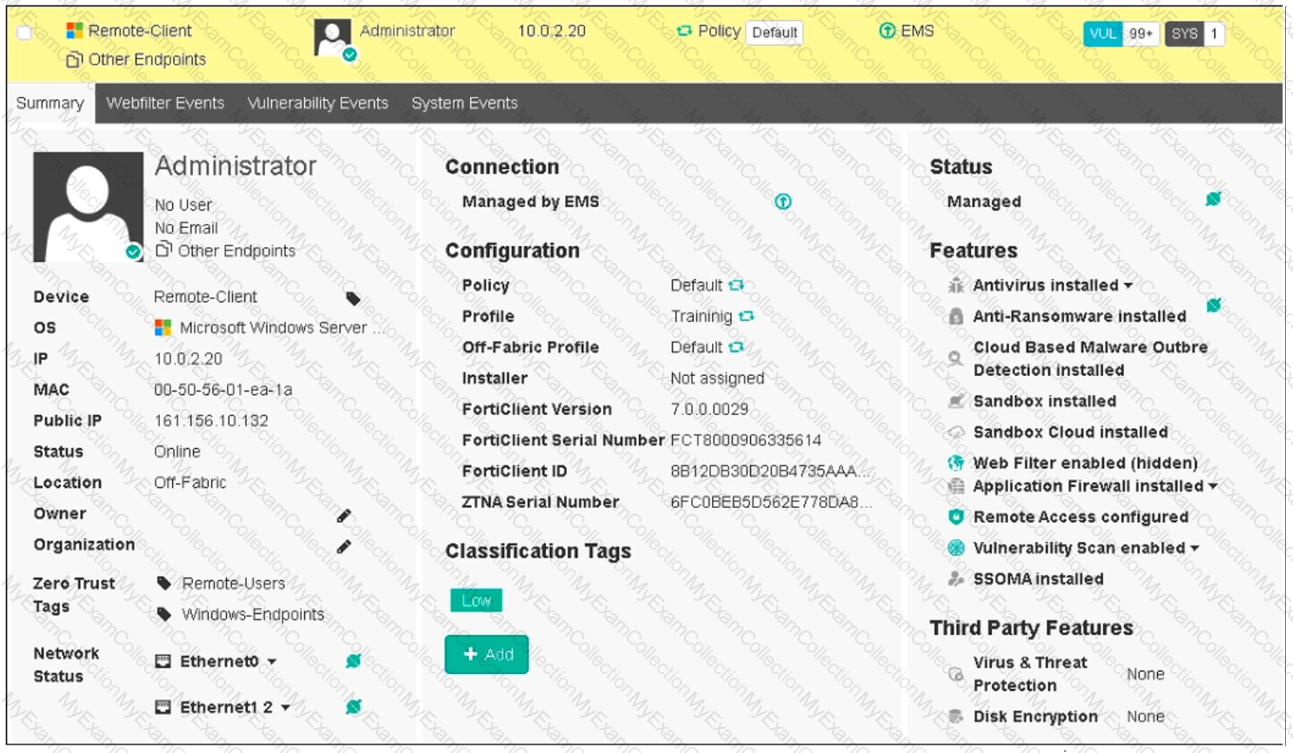
What two conclusions can you make based on the Remote-Client status shown above? (Choose two.)
When site categories are disabled in FortiClient web filter, which feature can be used to protect the endpoint from malicious web access?
Which statement about the FortiClient enterprise management server is true?
An administrator wants to simplify remote access without asking users to provide user credentials Which access control method provides this solution?
Exhibit.
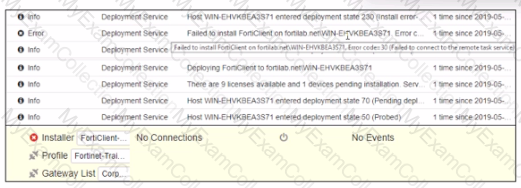
Based on the logs shown in the exhibit, why did FortiClient EMS tail to install FortiClient on the endpoint?
An administrator installs FortiClient on Windows Server.
What is the default behavior of real-time protection control?
Refer to the exhibit.
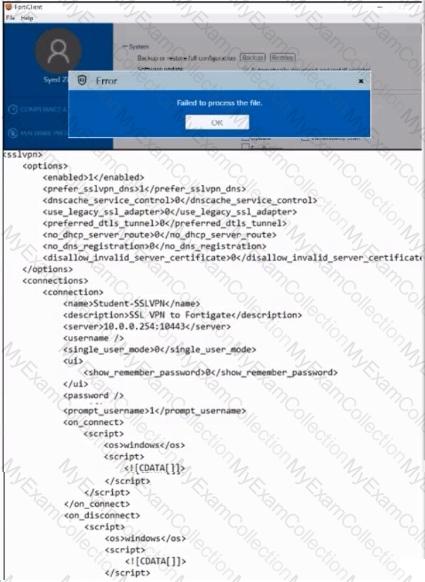
An administrator has restored the modified XML configuration file to FortiClient and sees the error shown in the exhibit.
Based on the XML settings shown in the exhibit, what must the administrator do to resolve the issue with the XML configuration file?
An administrator must add an authentication server on FortiClient EMS in a different security zone that cannot allow a direct connection.
Which solution can provide secure access between FortiClient EMS and the Active Directory server?
Refer to the exhibit.
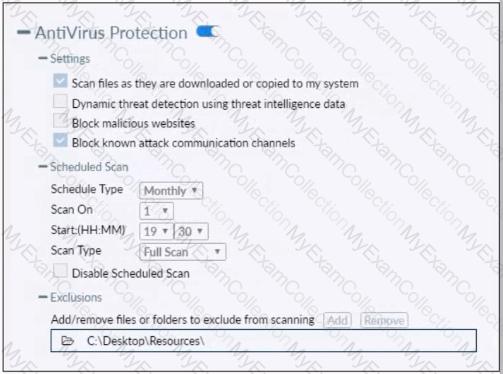
Based on the settings shown in the exhibit which statement about FortiClient behavior is true?
Which statement about FortiClient comprehensive endpoint protection is true?
A new chrome book is connected in a school's network.
Which component can the EMS administrator use to manage the FortiClient web filter extension installed on the Google Chromebook endpoint?

