Which statement about the FortiSOAR management extension is correct?
It requires a FortiManager configured to manage FortiGate.
It runs as a docker container on FortiAnalyzer.
It requires a dedicated FortiSOAR device or VM.
It does not include a limited trial by default.
Answer:
Explanation:
The FortiSOAR management extension is designed as an independent security orchestration, automation, and response (SOAR) solution that integrates with other Fortinet products but requires its own dedicated device or virtual machine (VM) environment. FortiSOAR is not natively integrated as a container or service within FortiAnalyzer or FortiManager, and it operates separately to manage complex security workflows and incident responses across various platforms.
Let’s examine each option to determine the correct answer:
Option A: It requires a FortiManager configured to manage FortiGate
This is incorrect. FortiSOAR operates independently of FortiManager. While FortiSOAR can receive input or data from FortiGate (often managed by FortiManager), it does not require FortiManager to be part of its setup.
Option B: It runs as a docker container on FortiAnalyzer
This is incorrect. FortiSOAR does not run as a container within FortiAnalyzer. It requires its own dedicated environment, either as a physical device or a virtual machine, due to the resource requirements and specialized functions it performs.
Option C: It requires a dedicated FortiSOAR device or VM
This is correct. FortiSOAR is deployed as a standalone device or VM, which enables it to handle the intensive processing needed for orchestrating security operations, integrating with third-party tools, and automating responses across an organization’s security infrastructure.
Option D: It does not include a limited trial by default
This is incorrect. FortiSOAR installations may come with trial options or demos in specific scenarios, especially for evaluation purposes. This depends on licensing and deployment policies.
Which two statements regarding FortiAnalyzer operating modes are true? (Choose two.)
When running in collector mode, FortiAnalyzer can forward logs to a syslog server.
FortiAnalyzer runs in collector mode by default unless it is configured for HA.
You can create and edit reports when FortiAnalyzer is running in collector mode.
A topology with FortiAnalyzeer devices running in both modes can improve their performance.
Answer:
Explanation:
FortiAnalyzer has two primary operating modes: Analyzer mode and Collector mode. Each mode serves specific purposes and has distinct capabilities.
Option A - Forwarding Logs to a Syslog Server in Collector Mode:
In Collector mode, FortiAnalyzer collects logs from Fortinet devices but does not process or analyze them. Instead, it forwards the logs to other FortiAnalyzer units in Analyzer mode or to specific storage locations. However, forwarding logs to a syslog server is not a function of Collector mode. Logs are generally stored or sent to other FortiAnalyzer devices.
Conclusion: Incorrect.
Option B - Default Mode is Collector Mode Unless Configured for HA:
When a FortiAnalyzer is initially set up, it runs in Collector mode by default unless it is configured as part of a High Availability (HA) setup, which would set it to Analyzer mode. Collector mode prioritizes log collection and storage rather than analysis, offloading analysis to other devices in the network.
Conclusion: Correct.
Option C - Report Creation and Editing in Collector Mode:
In Collector mode, FortiAnalyzer does not have the capability to create or edit reports. This mode is focused solely on log collection and forwarding, with analysis and report generation left to FortiAnalyzer units operating in Analyzer mode.
Conclusion: Incorrect.
Option D - Performance Improvement with Both Modes in Topology:
Deploying FortiAnalyzer devices in both Collector and Analyzer modes in a network topology can enhance performance. Collector mode devices handle log collection, reducing the workload on Analyzer mode devices, which focus on log processing, analysis, and reporting. This separation of tasks can optimize resource usage and improve the overall efficiency of log management.
Conclusion: Correct.
Conclusion:
Correct Answer: B. FortiAnalyzer runs in collector mode by default unless it is configured for HA and D. A topology with FortiAnalyzer devices running in both modes can improve their performance.
These answers correctly describe the functionality and default configuration of FortiAnalyzer operating modes, along with how a mixed-mode topology can enhance performance.
Which FortiAnalyzer feature allows you to use a proactive approach when managing your network security?
FortiView Monitor
Outbreak alert services
Incidents dashboard
Threat hunting
Answer:
Explanation:
FortiAnalyzer offers several features for monitoring, alerting, and incident management, each serving different purposes. Let's examine each option to determine which one best supports a proactive security approach.
Option A - FortiView Monitor:
FortiView is a visualization tool that provides real-time and historical insights into network traffic, threats, and logs. While it gives visibility into network activity, it is generally more reactive than proactive, as it relies on existing log data and incidents.
Conclusion: Incorrect.
Option B - Outbreak Alert Services:
Outbreak Alert Services in FortiAnalyzer notify administrators of emerging threats and outbreaks based on FortiGuard intelligence. This is beneficial for awareness of potential threats but does not offer a hands-on, investigative approach. It’s more of a notification service rather than an active, proactive investigation tool.
Conclusion: Incorrect.
Option C - Incidents Dashboard:
The Incidents Dashboard provides a summary of incidents and current security statuses within the network. While it assists with ongoing incident response, it is used to manage and track existing incidents rather than proactively identifying new threats.
Conclusion: Incorrect.
Option D - Threat Hunting:
Threat Hunting in FortiAnalyzer enables security analysts to actively search for hidden threats or malicious activities within the network by leveraging historical data, analytics, and intelligence. This is a proactive approach as it allows analysts to seek out threats before they escalate into incidents.
Conclusion: Correct.
Conclusion:
Correct Answer: D. Threat hunting
Threat hunting is the most proactive feature among the options, as it involves actively searching for threats within the network rather than reacting to already detected incidents.
Which statement about the FortiSIEM management extension is correct?
It allows you to manage the entire life cycle of a threat or breach.
It can be installed as a dedicated VM.
Its use of the available disk space is capped at 50%.
It requires a licensed FortiSIEM supervisor.
Answer:
You discover that a few reports are taking a long tine lo generate. Which two steps can you Like to troubleshoot? (Choose two.)
Remove old reports from the hcache
Enable auto-cache and run the reports again
Increase the ADOM reports quota
Review report diagnostics
Answer:
As part of your analysis, you discover that a Medium severity level incident is fully remediated.
You change the incident status to Closed:Remediated.
Which statement about your update is true?
The incident can no longer be deleted.
The corresponding event will be marked as Mitigated.
The incident dashboard will be updated.
The incident severity will be lowered.
Answer:
Exhibit.
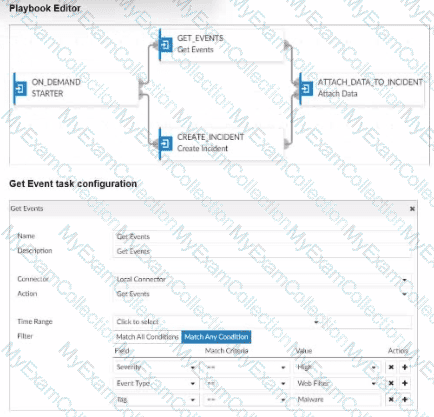
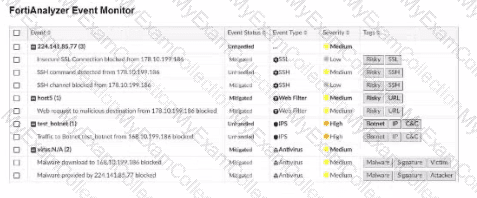
Assume these are all the events that exist on the FortiAnalyzer device.
How many events will be added to the incident created after running this playbook?
Eleven events will be added.
Seven events will be added
No events will be added.
Four events will be added.
Answer:
Explanation:
In the exhibit, we see a playbook in FortiAnalyzer designed to retrieve events based on specific criteria, create an incident, and attach relevant data to that incident. The "Get Event" task configuration specifies filters to match any of the following conditions:
Severity = High
Event Type = Web Filter
Tag = Malware
Analysis of Events:
In the FortiAnalyzer Event Monitor list:
We need to identify events that meet any one of the specified conditions (since the filter is set to "Match Any Condition").
Events Matching Criteria:
Severity = High:
There are two events with "High" severity, both with the "Event Type" IPS.
Event Type = Web Filter:
There are two events with the "Event Type" Web Filter. One has a "Medium" severity, and the other has a "Low" severity.
Tag = Malware:
There are two events tagged with "Malware," both with the "Event Type" Antivirus and "Medium" severity.
After filtering based on these criteria, there are four distinct events:
Two from the "Severity = High" filter.
One from the "Event Type = Web Filter" filter.
One from the "Tag = Malware" filter.
Conclusion:
Correct Answer: D. Four events will be added.
This answer matches the conditions set in the playbook filter configuration and the events listed in the Event Monitor.
Which log will generate an event with the status Unhandled?
An AV log with action=quarantine.
An IPS log with action=pass.
A WebFilter log will action=dropped.
An AppControl log with action=blocked.
Answer:
Explanation:
In FortiOS 7.4.1 and FortiAnalyzer 7.4.1, the "Unhandled" status in logs typically signifies that the FortiGate encountered a security event but did not take any specific action to block or alter it. This usually occurs in the context of Intrusion Prevention System (IPS) logs.
IPS logs with action=pass: When the IPS engine inspects traffic and determines that it does not match any known attack signatures or violate any configured policies, it assigns the action "pass". Since no action is taken to block or modify this traffic, the status is logged as "Unhandled."
Let's look at why the other options are incorrect:
An AV log with action=quarantine: Antivirus (AV) logs with the action "quarantine" indicate that a file was detected as malicious and moved to quarantine. This is a definitive action, so the status wouldn't be "Unhandled."
A WebFilter log will action=dropped: WebFilter logs with the action "dropped" indicate that web traffic was blocked according to the configured web filtering policies. Again, this is a specific action taken, not an "Unhandled" event.
An AppControl log with action=blocked: Application Control logs with the action "blocked" mean that an application was denied access based on the defined application control rules. This is also a clear action, not "Unhandled."
Which two methods can you use to send notifications when an event occurs that matches a configured event handler? (Choose two.)
Send Alert through Fabric Connectors
Send SNMP trap
Send SMS notification
Send Alert through FortiSIEM MEA
Answer:
Explanation:
In FortiAnalyzer, event handlers can be configured to trigger specific notifications when an event matches defined criteria. These notifications are designed to alert administrators in real time about critical events.
Option B - Send SNMP Trap:
FortiAnalyzer supports sending SNMP traps as one of the notification methods when an event matches an event handler. This allows integration with SNMP-enabled network management systems, which can then trigger further alerts or actions based on the trap received.
Conclusion: Correct.
Option C - Send SMS Notification:
FortiAnalyzer also supports SMS notifications, enabling alerts to be sent via SMS to predefined recipients. This method is useful for administrators who require immediate alerts but may not have access to email or other notification systems at all times.
Conclusion: Correct.
Option A - Send Alert through Fabric Connectors:
While Fabric Connectors allow FortiAnalyzer to interact with other parts of the Security Fabric, they are primarily used for data sharing and automation rather than directly for sending alerts or notifications.
Conclusion: Incorrect.
Option D - Send Alert through FortiSIEM MEA:
FortiSIEM integration allows for data sharing and further analysis within the Fortinet ecosystem, but it does not directly act as a notification method from FortiAnalyzer itself.
Conclusion: Incorrect.
Conclusion:
Correct Answer: B. Send SNMP trap and C. Send SMS notification
These options represent valid notification methods for FortiAnalyzer’s event handler configuration.
Refer to Exhibit:

What does the data point at 21:20 indicate?
FortiAnalyzer is indexing logs faster than logs are being received.
The fortilogd daemon is ahead in indexing by one log.
The SQL database requires a rebuild because of high receive lag.
FortiAnalyzer is temporarily buffering received logs so older logs can be indexed first.
Answer:
Explanation:
The exhibit shows a graph that tracks two metrics over time: Receive Rate and Insert Rate. These two rates are crucial for understanding the log processing behavior in FortiAnalyzer.
Understanding Receive Rate and Insert Rate:
Receive Rate: This is the rate at which FortiAnalyzer is receiving logs from connected devices.
Insert Rate: This is the rate at which FortiAnalyzer is indexing (inserting) logs into its database for storage and analysis.
Data Point at 21:20:
At 21:20, the Insert Rate line is above the Receive Rate line, indicating that FortiAnalyzer is inserting logs into its database at a faster rate than it is receiving them. This situation suggests that FortiAnalyzer is able to keep up with the incoming logs and is possibly processing a backlog or temporarily received logs faster than new logs are coming in.
Option Analysis:
Option A - FortiAnalyzer is Indexing Logs Faster Than Logs are Being Received: This accurately describes the scenario at 21:20, where the Insert Rate exceeds the Receive Rate. This indicates that FortiAnalyzer is handling logs efficiently at that moment, with no backlog in processing.
Option B - The fortilogd Daemon is Ahead in Indexing by One Log: The data does not provide specific information about the fortilogd daemon’s log count, only the rates. This option is incorrect.
Option C - SQL Database Requires a Rebuild: High receive lag would imply a backlog in receiving and indexing logs, typically visible if the Receive Rate were significantly above the Insert Rate, which is not the case here.
Option D - FortiAnalyzer is Temporarily Buffering Logs to Index Older Logs First: There is no indication of buffering in this scenario. Buffering would usually occur if the Receive Rate were higher than the Insert Rate, indicating that FortiAnalyzer is storing logs temporarily due to indexing lag.
Conclusion:
Correct Answer: A. FortiAnalyzer is indexing logs faster than logs are being received.
The graph at 21:20 shows a higher Insert Rate than Receive Rate, indicating efficient log processing by FortiAnalyzer.
A playbook contains five tasks in total. An administrator runs the playbook and four out of five tasks finish successfully, but one task fails.
What will be the status of the playbook after it is run?
Attention required
Upstream_failed
Failed
Success
Answer:
Explanation:
In FortiAnalyzer, when a playbook is run, each task’s status impacts the overall playbook status. Here’s what happens based on task outcomes:
Status When All Tasks Succeed:
If all tasks finish successfully, the playbook status is marked as Success.
Status When Some Tasks Fail:
If one or more tasks in the playbook fail, but others succeed, the playbook status generally changes to Attention required. This status indicates that the playbook completed execution but requires review due to one or more tasks failing.
This is different from a complete Failed status, which is used if the playbook cannot proceed due to a critical error in an early task, often one that upstream tasks depend on.
Option Analysis:
A. Attention required: This is correct as the playbook has completed, but with partial success and a task requiring review.
B. Upstream_failed: This status is used if a task cannot run because a prerequisite or "upstream" task failed. Since four out of five tasks completed, this is not the case here.
C. Failed: This status would imply that the playbook completely failed, which does not match the scenario where only one task out of five failed.
D. Success: This status would apply if all tasks had completed successfully, which is not the case here.
Conclusion:
Correct Answer: A. Attention required
The playbook status reflects that it completed, but an error occurred in one of the tasks, prompting the administrator to review the failed task.
Exhibit.

A fortiAnalyzer analyst is customizing a SQL query to use in a report.
Which SQL query should the analyst run to get the expected results?
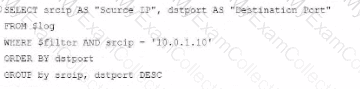
A)
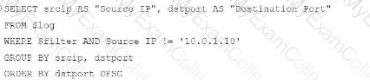
B)
C)

D)
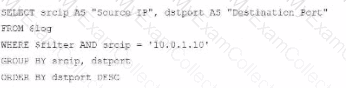
Option A
Option B
Option C
Option D
Answer:
Explanation:
The requirement here is to construct a SQL query that retrieves logs with specific fields, namely "Source IP" and "Destination Port," for entries where the source IP address matches 10.0.1.10. The correct syntax is essential for selecting, filtering, ordering, and grouping the results as shown in the expected outcome.
Analysis of the Options:
Option A Explanation:
SELECT srcip AS "Source IP", dstport AS "Destination Port": This syntax selects srcip and dstport, renaming them to "Source IP" and "Destination Port" respectively in the output.
FROM $log: Specifies the log table as the data source.
WHERE $filter AND srcip = '10.0.1.10': This line filters logs to only include entries with srcip equal to 10.0.1.10.
ORDER BY dstport DESC: Orders the results in descending order by dstport.
GROUP BY srcip, dstport: Groups results by srcip and dstport, which is valid SQL syntax.
This option meets all the requirements to get the expected results accurately.
Option B Explanation:
WHERE $filter AND Source IP != '10.0.1.10': Uses != instead of =. This would exclude logs from the specified IP 10.0.1.10, which is contrary to the expected result.
Option C Explanation:
The ORDER BY clause appears before the FROM clause, which is incorrect syntax. SQL requires the FROM clause to follow the SELECT clause directly.
Option D Explanation:
The GROUP BY clause should follow the FROM clause. However, here, it’s located after WHERE, making it syntactically incorrect.
Conclusion:
Correct Answer: A. Option A
This option aligns perfectly with standard SQL syntax and filters correctly for srcip = '10.0.1.10', while ordering and grouping as required.
Exhibit.
What is the purpose of using the Chart Builder feature On FortiAnalyzer?
To build a chart automatically based on the top 100 log entries
To add charts directly to generate reports in the current ADOM.
To add a new chart under FortiView to be used in new reports
To build a dataset and chart based on the filtered search results

