How do you restrict an administrator’s access to a subset of your organization’s ADOMs?
Which item must you configure on FortiAnalyzer to email generated reports automatically?
Which log type does the FortiAnalyzer indicators of compromise feature use to identify infected hosts?
If the primary FortiAnalyzer in an HA cluster fails, how is the new primary elected?
Why should you use an NTP server on FortiAnalyzer and all registered devices that log into FortiAnalyzer?
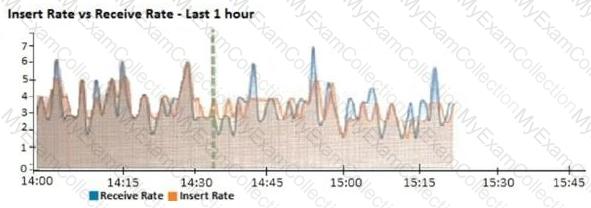
Refer to the exhibit.

Which statement is correct regarding the event displayed?
What can you do on FortiAnalyzer to restrict administrative access from specific locations?
Refer to the exhibit.
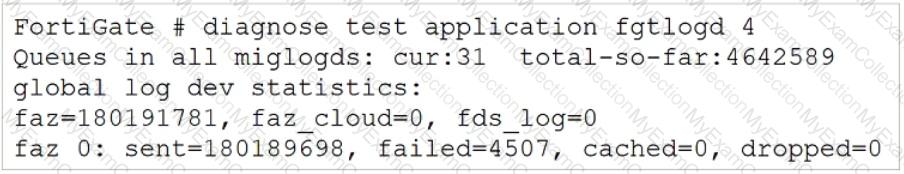
Based on the output, what can you conclude about the FortiAnalyzer logging status?
Which two of the following must you configure on FortiAnalyzer to email a FortiAnalyzer report externally?
(Choose two.)
Which two statement are true regardless initial Logs sync and Log Data Sync for Ha on FortiAnalyzer?
Which statement correctly describes the management extensions available on FortiAnalyzer?
Which two purposes does the auto cache setting on reports serve? (Choose two.)
Which two settings must you configure on FortiAnalyzer to allow non-local administrators to authenticate to FortiAnalyzer with any user account in a single LDAP group? (Choose two.)
Which tabs do not appear when FortiAnalyzer is operating in Collector mode?
Refer to the exhibit.
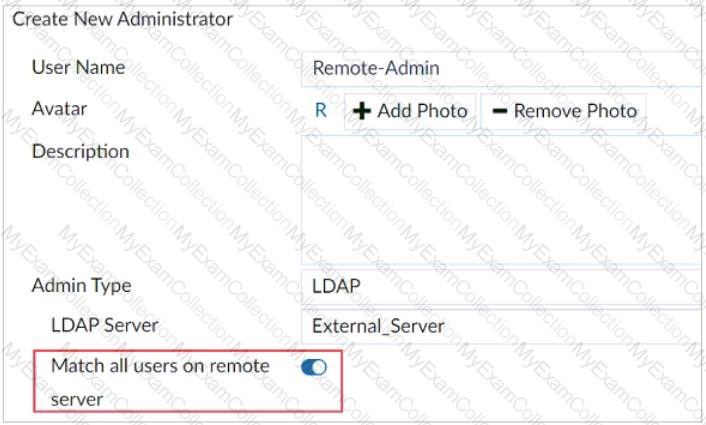
The exhibit shows the creation of a new administrator on FortiAnalyzer.
What are two effects of enabling the choice Match all users on remote server when configuring a new administrator? (Choose two.)
What statements are true regarding FortiAnalyzer 's treatment of high availability (HA) dusters? (Choose two)
Logs are being deleted from one of the ADOMs earlier than the configured setting for archiving in the data
policy.
What is the most likely problem?
What FortiView tool can you use to automatically build a dataset and chart based on a filtered search result?
View the exhibit.
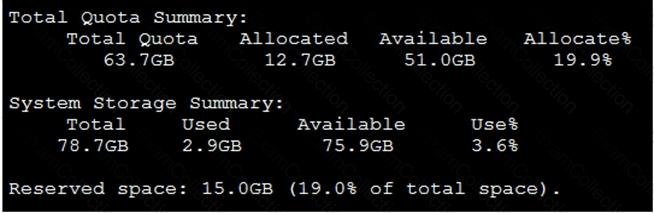
Why is the total quota less than the total system storage?
Refer to the exhibit.
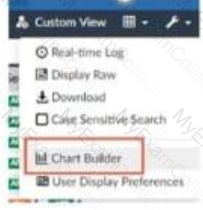
What is the purpose of using the Chart Builder feature on FortiAnalyzer?
You are trying to initiate an authorization request from FortiGate to FortiAnalyzer, but the Security Fabric window does not open when you click Authorize.
Which two reasons can cause this to happen? (Choose two.)
The connection status of a new device on FortiAnalyzer is listed as Unauthorized.
What does that status mean?
What is the best approach to handle a hard disk failure on a FortiAnalyzer that supports hardware RAID?
Refer to the exhibit.
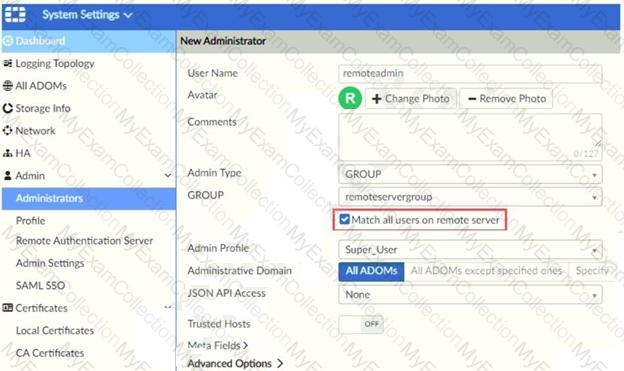
The exhibit shows “remoteservergroup†is an authentication server group with LDAP and RADIUS servers.
Which two statements express the significance of enabling “Match all users on remote server†when configuring a new administrator? (Choose two.)
Which statement is true about sending notifications with incident updates?
An administrator has configured the following settings:
config system fortiview settings
set resolve-ip enable
end
What is the significance of executing this command?
When you perform a system backup, what does the backup configuration contain? (Choose two.)
What is the main purpose of using an NTP server on FortiAnalyzer and all of its registered devices?
Which clause is considered mandatory in SELECT statements used by the FortiAnalyzer to generate reports?
Which two methods can you use to restrict administrative access on FortiAnalyzer? (Choose two.)
In Log View, you can use the Chart Builder feature to build a dataset and chart based on the filtered search results.
Similarly, which feature you can use for FortiView?
Refer to the exhibit.
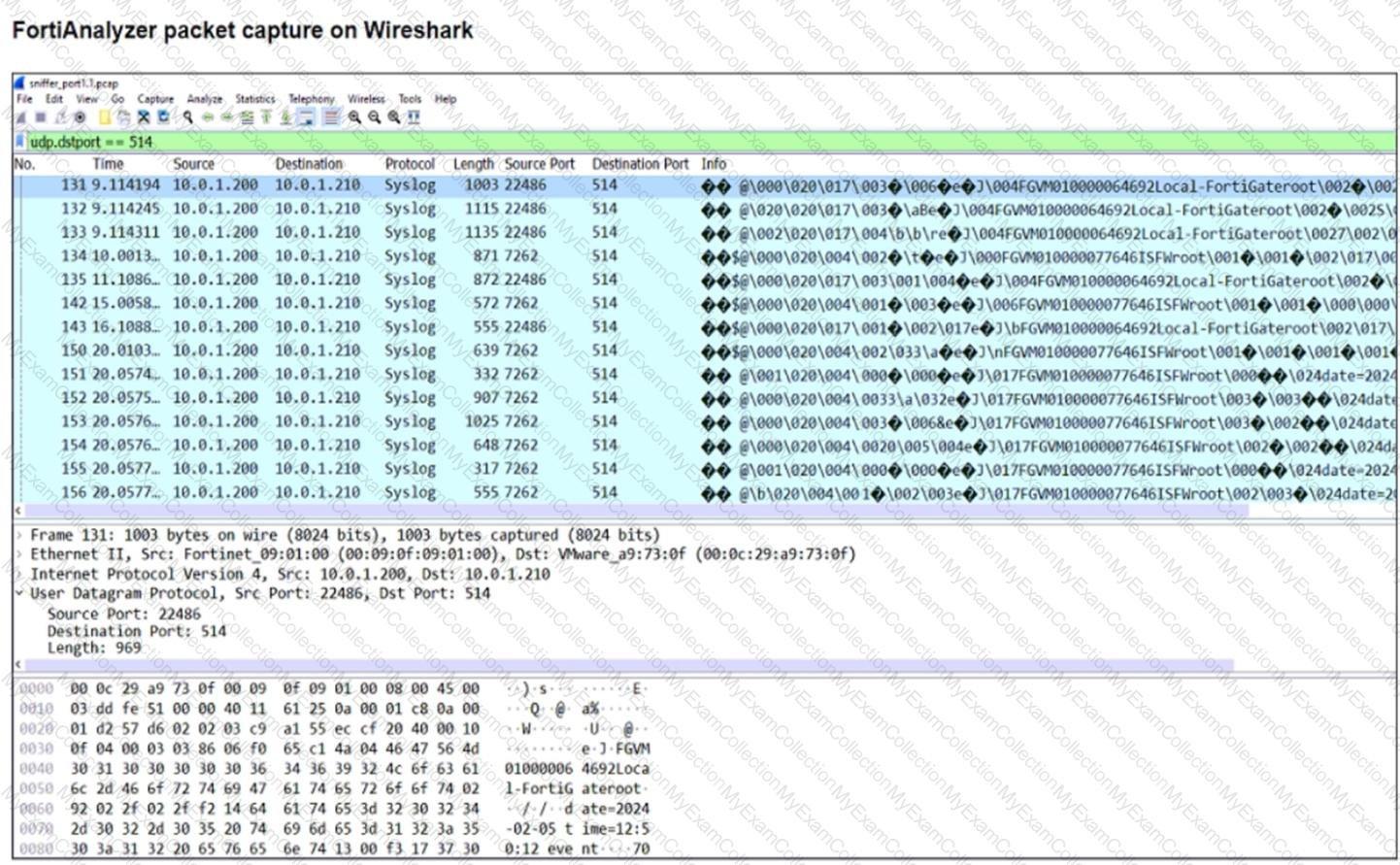
The capture displayed was taken on a FortiAnalyzer.
Why is a single IP address shown as the source for all logs received?
What happens when the IOC breach detection engine on FortiAnalyzer finds web logs that match a blocklisted IP address?
Which statements are correct regarding FortiAnalyzer reports? (Choose two)
Which statements are true regarding securing communications between FortiAnalyzer and FortiGate with SSL? (Choose two.)
FortiAnalyzer reports are dropping analytical data from 15 days ago, even though the data policy setting for
analytics logs is 60 days.
What is the most likely problem?
Which two settings must you configure on FortiAnalyzer to allow non-local administrators to authenticate on FortiAnalyzer with any user account in a single LDAP group? (Choose two.)
You have recently grouped multiple FortiGate devices into a single ADOM. System Settings > Storage Info
shows the quota used.
What does the disk quota refer to?
Refer to the exhibit.
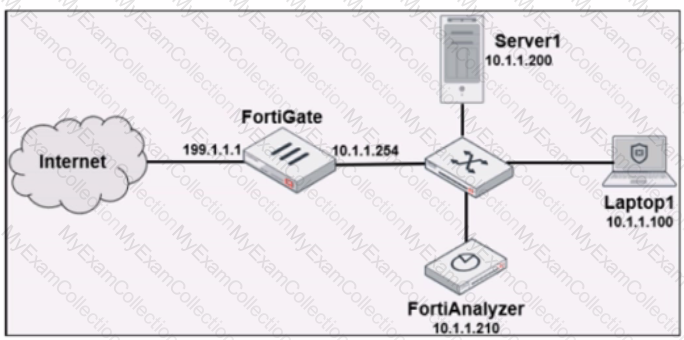
Laptop1 is used by several administrators to manage FortiAnalyzer. You want to configure a generic text filter that matches all login attempts to the web interface generated by any user other than "admin", and coming from Laptop1.
Which filter will achieve the desired result?
Which three RAID configurations provide fault tolerance on FortiAnalyzer? (Choose three.)
What is the best approach to handle a hard disk failure on a FortiAnalyzer that supports hardware RAID?