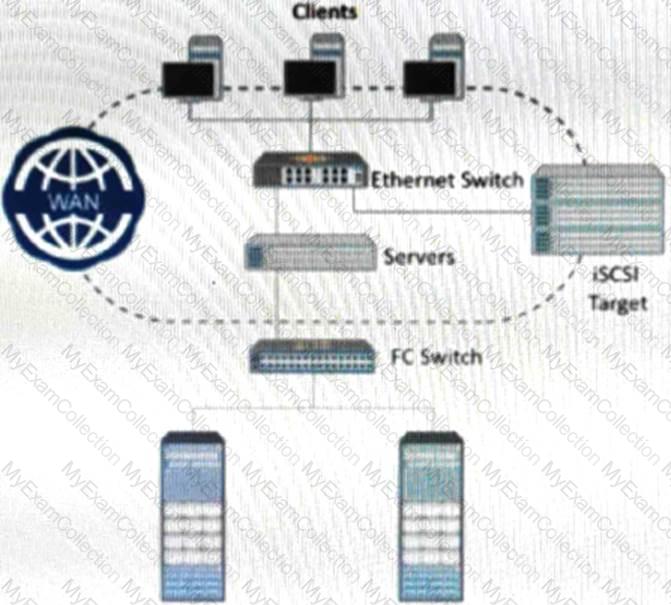
An Ethernet switch has eight ports and all ports must be operational for 24Â hours from Monday through Friday. However, failures of Port 6 occur within the week as follows:
Tuesday = 6Â AM to 8Â AM
Thursday = 5Â PM to 10Â PM
Friday = 7Â AM to 9Â AM
What is the MTBF of Port 6?
What is the functionality of the application server in a Mobile Device Management?
Why is it important for organizations to implement a multi-site remote replication solution?
Which Dell EMC product is a software-defined storage platform that abstracts, pools, and automates a data center’s physical storage infrastructure?
What is an advantage of performing incremental backups compared to cumulative backups for the same data?
Which file system provides a streaming interface using the MapReduce framework?
Refer to the Exhibit:
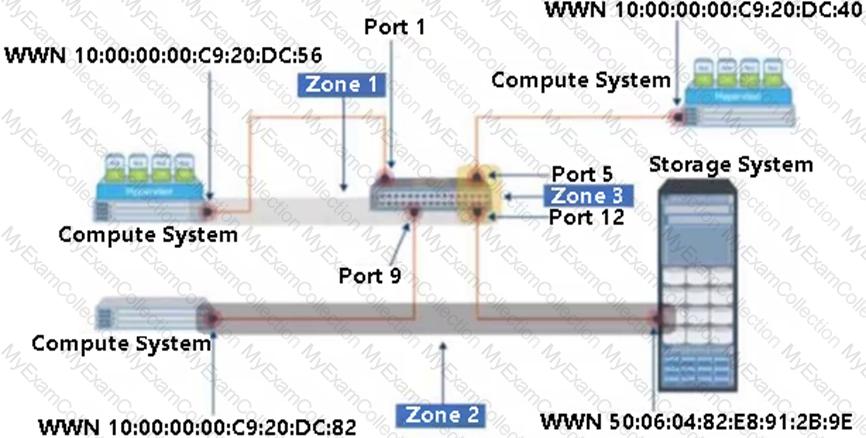
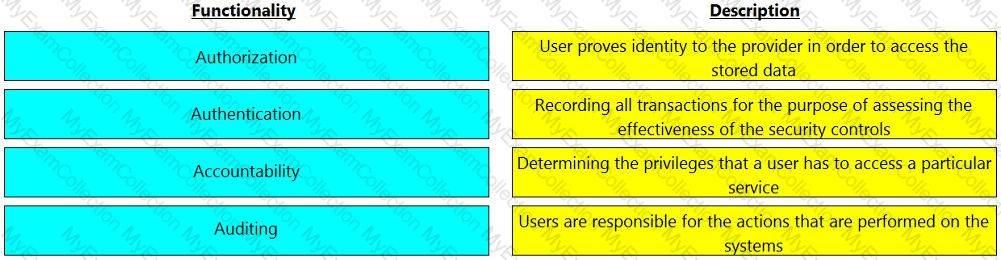
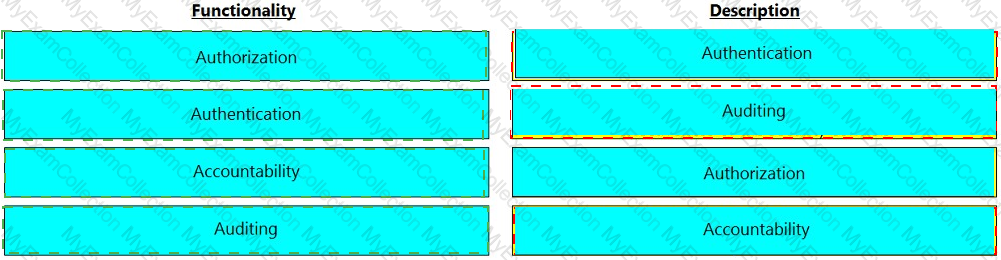
Select the option that represents the three Zone Types for each of the labeled zones.
Which layer of modern data center architecture specifies the measures that help an organization mitigate downtime impact due to planned and unplanned outages?
What is true about scale-out NAS storage architecture? (First Choose Correct option and give detailed explanation delltechnologies.com)
What is a benefit of including a Defense-in-depth strategy as part of the data center security strategy?
What kind of ML explicitly requires splitting the data into training and testing datasets before running an algorithm against that data?
An IT organization wants to deploy four FC switches for compute and storage system connectivity. To meet performance requirements, a maximum of one active ISL and redundant ISLs for their compute to storage traffic.
Which FC SAN topology should be recommended?
Which loT architecture component provides the connection to monitor and control user devices? (First Choose Correct option and give detailed explanation delltechnologies.com)
A company is using an intrusion detection and prevention system (IDPS) to scan and analyze intrusion events.
Which IDPS technique uses a database that contains known attack patterns?
An organization wants to prevent incidents which share common symptoms or root causes from reoccurring. They also want to minimize the adverse impact of incidents that cannot be prevented.
Which management function addresses the organization's requirements?
Which interface does an SCM device use to connect to intelligent storage system controllers?
Which type of machine learning algorithm produces results using a reward and feedback mechanism?
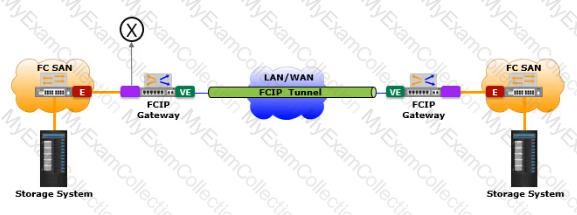
Based on the exhibit, what does the "X" represent in the FCIP tunnel configuration?
Which infrastructure building process allows organizations to repurpose existing infrastructure components and provides cost benefits?
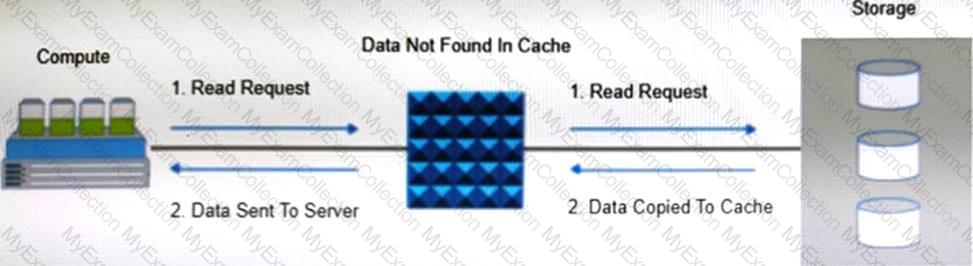
What is an advantage of deploying intelligent storage systems in the data center?
What type of technology is used in SSD devices to provide non-volatile data storage?
In an SDS environment, which protocol supports the resource-oriented architecture for the development of scalable and lightweight web applications while adhering to a set of constraints?
What type of backup method allows a client to be installed in a VM that sends the data to the backup device?
What set of components are part of a block-based storage array controller?
What is a benefit of using a purpose-build NAS solution vs general purpose file servers?
What functionality does the control layer provide in a software-defined networking architecture?
Which storage management function ensures that the services and service levels are delivered per SLAs?
Refer to the Exhibit:
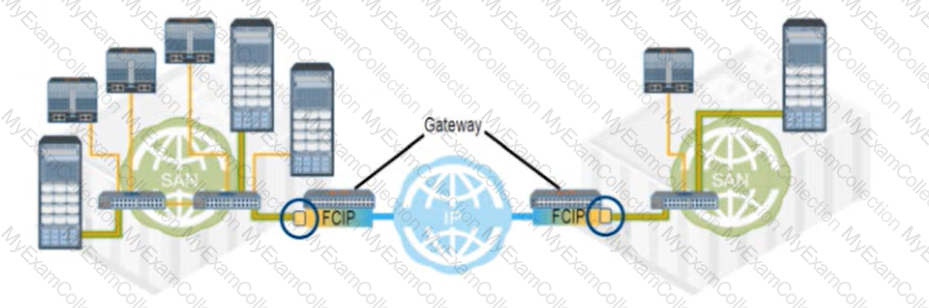
What type of FC port connects each FCIP gateway to each FC SAN?
The Ethernet switch has eight ports and all ports must be operational for 24 hours, from Monday through Friday. However, a failure of Port 4 occurs as follows:
Monday = 8 PM to 11 PM -
Wednesday = 7 PM to 10 PM -
Thursday = 6 AM to 12 PM -
What is the MTTR of Port 4?
Which plane of the SDDC architecture provides a CLI and GUI for IT to administrator the infrastructure and to configure policies? (Choose Correct Answer from Associate - Information Storage and Management version 5 Manual from dellemc.com and give explanation)
Which product enables employees to enroll their mobile devices in an enterprise environment and ensures secure access from the devices to the enterprise resources?
An organization is planning to secure the connection between the data center and cloud while performing data backup and replication.
Which security control mechanism will help organization to achieve the desired security?
A host sends one write /O to the RAID 1 array.
How many writes does it take for the array to store the data?
Which type of data protection is used to move primary data to lower cost storage and helps to enforce compliance requirement?