Copies of checks that have been included in Agent Client Collector policies are known as what?
The additional information field is a JSON string that gives more information about an event. An example of a supported JSON string is:
What does Operational Intelligence proactively identify before they cause service outages?
If the Message Key is not populated, the default value is created from which fields?
Which step in the event rule configuration process enables you to ignore events and prevent alert generation?
If more than one event rule applies to a particular event or metric, which of the event rules will run based upon the Order of execution number?
When performing CI Binding, what fields does Event Management match to the Node?
What is one of the main benefits of using Event Management and Operational Intelligence?
If a Message Key is not provided, which fields are concatenated to make our own?
What Event Management module allows for configuration of automatic task creation?
Within the ServiceNow IT Operations Management solution set, which statement most accurately describes what Event Management is?
If more than one alert management rule applies to a particular alert which of the rules will run based upon the Order of execution field?
In the event table, which field maps the external attributes from the target system?
What applications are included in the ITOM Health solution?
Choose 3 answers
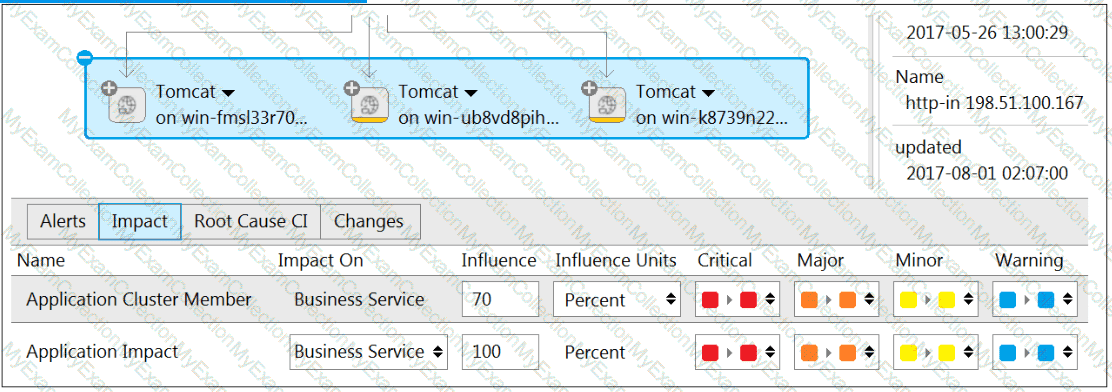
Given the following Impact settings and Alerts in a three node cluster that makes up the components of a Business Service, what is the overall service health of this Business Service?
Which is a correct regex expression to capture only the server's hostname (webserver3) in "The server webserver3.domain.com is down."?
Based on the information shown, which of the following three alerts should be processed first?
MID Servers provide important functions in your ITOM Health deployment.
What does MID stand for?
For an incoming event with a matching message key, what allows an existing alert to be automatically closed?
What makes all ServiceNow metrics, tasks, services, configuration items, assets, people, locations, and information a single system of record for IT and business processes?
In default configuration using baseline connectors, how often is event data collected from event sources?
The ServiceNow standard and shared set of service-related definitions that enable and support true service level reporting is known as what?
What is the primary function of enrich automation in Service Operations Workspace?

