A network device has both an SSH port and an SNMP port open. Discovery tries the SSH probe first and it fails. This triggers the SNMP probe, which succeeds. Discovery uses SNMP first for subsequent discoveries on that device.
What discovery functionality allows the above to happen?
What pattern operation allows the transfer of a file from the MID Server to a target?
Which of the below choices are possible options under ACTION ON ALL in the Recommended Actions pane for an Automated Error Messages list within Discovery > Home?
Choose 2 answers
Which of the following executes the osquery commands on agents to gather attribute details from a CI?
Which part of Agent Client Collector must be configured to run osquery commands on a CI?
- Policies
Which of the following choices may be global variables for steps in horizontal discovery patterns? (Choose two.)
Which choice allows the following functionality to occur?
If this value is set to 1000 and a discovery must scan 10,000 IP addresses using a single MID Server, it creates 10 Shazzam probes with each probe scanning 1000 IP addresses.
Which of the following MID Server Parameters cannot be modified through the platform UI?
Hardware Models can have a one-to-many relationship with the following:
(Choose three.)
What would you see in the Discovery pattern log that you would not see in the ECC Queue?
Which of the following can be used in the Debug Identification Section in Debug Mode for an infrastructure pattern? (Choose two.)
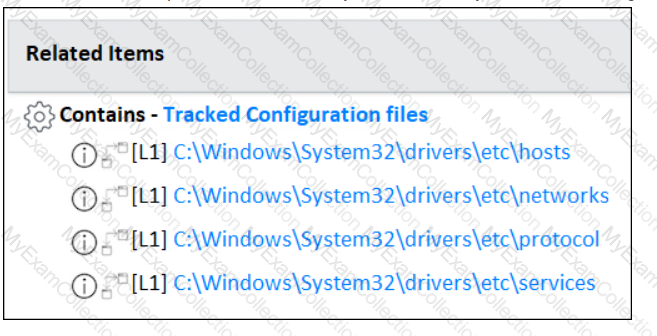
Which of the below choices are benefits of Tracked Configuration Files? (Choose two.)
When configuring the MID Server Service Settings, which of the following is not a valid MID Server name?
Which of the following must be configured to allow a MID Server to access servers using WinRM?
Using the SNMP Query operation on a pattern for a custom device query, it is best practice to do what?
From the Discovery Status record, which of the following does a Device record contain?
Discovery finds and maps dependencies for the following types of storage devices. (Choose three.)
Which metrics comprise the Completeness KPI for CMDB Health? (Choose two.)
Which of the following fields are editable from a Merge Table pattern operation?
Choose 3 answers
For a pattern operation, which of the below choices could be a valid replacement for <_>? (Choose three.)
$IfTable<_>.InstanceID
In a discovery pattern, which types are available with CI Attributes in the Pattern Designer? (Choose two.)
Which choice best represents how to modify the functionality shown in this image?
Which of the following properties define the maximum overall size for the returned payload that comes from patterns?

