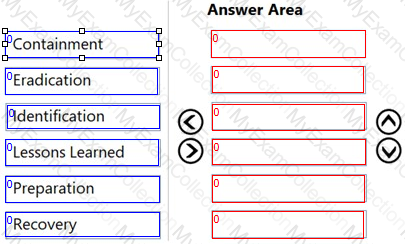
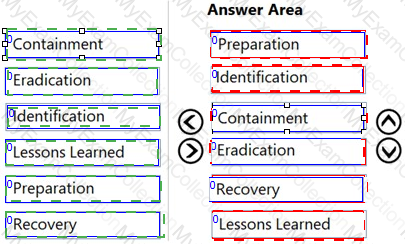
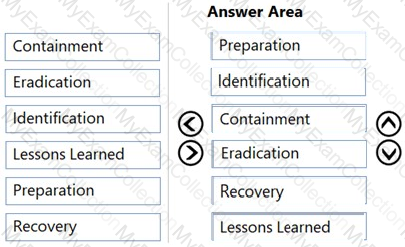
Which of the following digital forensic goals is being provided with hashing and time-stamping of the electronic evidence?
A network administrator has determined that network performance has degraded due to excessive use of
social media and Internet streaming services. Which of the following would be effective for limiting access to these types of services, without completely restricting access to a site?
An incident responder discovers that the CEO logged in from their New York City office and then logged in from a location in Beijing an hour later. The incident responder suspects that the CEO’s account has been
compromised. Which of the following anomalies MOST likely contributed to the incident responder’s suspicion?
Which of the following is considered a weakness or gap in a security program that can be exploited to gain unauthorized access?
When reviewing log files from a recent incident, the response team discovers that most of the network-based indicators are IP-based. It would be helpful to the response team if they could resolve those IP-based indicators to hostnames. Which of the following is BEST suited for this task?
Which of the following enables security personnel to have the BEST security incident recovery practices?
Which answer option is a tactic of social engineering in which an attacker engages in an attack performed by phone?
What is the BEST process to identify the vendors that will ensure protection and compliance with security and privacy laws?
Which are successful Disaster Recovery Plan best practices options to be considered? (Choose three.)
A Windows system administrator has received notification from a security analyst regarding new malware that executes under the process name of “armageddon.exe†along with a request to audit all department workstations for its presence. In the absence of GUI-based tools, what command could the administrator execute to complete this task?
Which of the following are common areas of vulnerabilities in a network switch? (Choose two.)
Which standard was implemented in the United States to protect the privacy of patient medical information through restricted access to medical records and regulations for sharing medical records?
A security analyst needs to capture network traffic from a compromised Mac host. They attempt to execute the tcpdump command using their general user account but continually receive an "Operation Not Permitted" error.
Use of which of the following commands will allow the analyst to capture traffic using tcpdump successfully?
A user receives an email about an unfamiliar bank transaction, which includes a link. When clicked, the link redirects the user to a web page that looks exactly like their bank’s website and asks them to log in with their username and password. Which type of attack is this?
In a Linux operating system, what kind of information does a /var/log/daemon.log file contain?
An attacker intercepts a hash and compares it to pre-computed hashes to crack a password. Which of the following methods has been used?
It was recently discovered that many of an organization’s servers were running unauthorized cryptocurrency mining software. Which of the following assets were being targeted in this attack? (Choose two.)
Which two answer options correctly highlight the difference between static and dynamic binary analysis techniques? (Choose two.)
A secretary receives an email from a friend with a picture of a kitten in it. The secretary forwards it to the
~COMPANYWIDE mailing list and, shortly thereafter, users across the company receive the following message:
“You seem tense. Take a deep breath and relax!â€
The incident response team is activated and opens the picture in a virtual machine to test it. After a short analysis, the following code is found in C:
\Temp\chill.exe:Powershell.exe –Command “do {(for /L %i in (2,1,254) do shutdown /r /m Error! Hyperlink reference not valid.> /f /t / 0 (/c “You seem tense. Take a deep breath and relax!â€);Start-Sleep –s 900) } while(1)â€
Which of the following BEST represents what the attacker was trying to accomplish?
Which of the following are legally compliant forensics applications that will detect an alternative data stream (ADS) or a file with an incorrect file extension? (Choose two.)
Tcpdump is a tool that can be used to detect which of the following indicators of compromise?
A computer forensics analyst suspects that some of the pictures recovered from the suspect's hard drive may contain metadata pertinent to the criminal investigation. Which of the following tools is BEST suited to retrieving any available metadata?
A system administrator identifies unusual network traffic from outside the local network. Which of the following
is the BEST method for mitigating the threat?
According to company policy, all accounts with administrator privileges should have suffix _ja. While reviewing Windows workstation configurations, a security administrator discovers an account without the suffix in the administrator’s group. Which of the following actions should the security administrator take?
Network infrastructure has been scanned and the identified issues have been remediated. What is the next step in the vulnerability assessment process?
A web server is under a denial of service (DoS) attack. The administrator reviews logs and creates an access control list (ACL) to stop the attack. Which of the following technologies could perform these steps automatically in the future?
What describes the BEST approach for developing a plan to continuously assess and track vulnerabilities on all organizational assets and infrastructure in order to remediate and minimize the opportunity for attacks?
Which of the following would MOST likely make a Windows workstation on a corporate network vulnerable to remote exploitation?
Which of the following regulations is most applicable to a public utility provider operating in the United States?
Which of the following backup strategies will result in the shortest backup time during weekdays and use the least amount of storage space but incur the longest restore time?
Which of the following types of attackers would be MOST likely to use multiple zero-day exploits executed against high-value, well-defended targets for the purposes of espionage and sabotage?
To minimize vulnerability, which steps should an organization take before deploying a new Internet of Things (IoT) device? (Choose two.)
What are the two most appropriate binary analysis techniques to use in digital forensics analysis? (Choose two.)
The Key Reinstallation Attack (KRACK) vulnerability is specific to which types of devices? (Choose two.)
As part of an organization’s regular maintenance activities, a security engineer visits the Internet Storm Center advisory page to obtain the latest list of blacklisted host/network addresses. The security engineer does this to perform which of the following activities?
While reviewing some audit logs, an analyst has identified consistent modifications to the sshd_config file for an organization’s server. The analyst would like to investigate and compare contents of the current file with
archived versions of files that are saved weekly. Which of the following tools will be MOST effective during the investigation?
An organization that recently suffered a ransomware attack found that its backups were faulty. Which of the following steps could BEST ensure reliable backups in the future?
An employee discovered the default credentials in DB servers, which were found by using a word list of commonly used and default passwords in Hydra, the tool behind the Brute functionality. The use of the word list in Hydra is an example of what type of password cracking?
A company has noticed a trend of attackers gaining access to corporate mailboxes. Which of the following
would be the BEST action to take to plan for this kind of attack in the future?
During which of the following attack phases might a request sent to port 1433 over a whole company network be seen within a log?
After a security breach, a security consultant is hired to perform a vulnerability assessment for a company’s web application. Which of the following tools would the consultant use?
When tracing an attack to the point of origin, which of the following items is critical data to map layer 2 switching?
Which of the following could be useful to an organization that wants to test its incident response procedures without risking any system downtime?
An incident responder has collected network capture logs in a text file, separated by five or more data fields.
Which of the following is the BEST command to use if the responder would like to print the file (to terminal/ screen) in numerical order?
Which of the following is an automated password cracking technique that uses a combination of uppercase and lowercase letters, 0-9 numbers, and special characters?
During an audit, an organization's ability to establish key performance indicators for its service hosting solution is discovered to be weak. What could be the cause of this?