A security analyst for a financial services firm is monitoring blogs and reads about a zero-day vulnerability being exploited by a little-known group of hackers. The analyst wishes to independently validate and corroborate the blog’s posting. Whichof the following sources of information will provide the MOST credible supporting threat intelligence in this situation?
Customers are reporting issues connecting to a company’s Internet server. Which of the following device logs should a technician review in order to help identify the issue?
When investigating a wireless attack, which of the following can be obtained from the DHCP server?
A malicious actor sends a crafted email to the office manager using personal information collected from social media. This type of social engineering attack is known as:
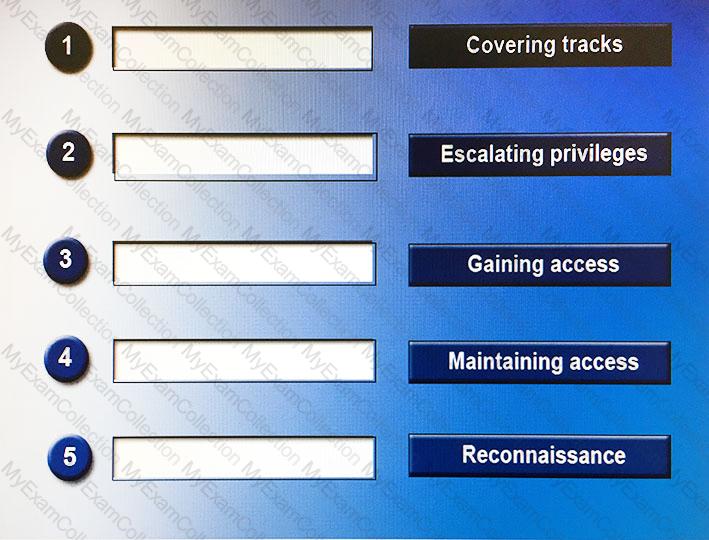
When perpetrating an attack, there are often a number of phases attackers will undertake, sometimes taking place over a long period of time. Place the following phases in the correct chronological order from first (1) to last (5).
A malware analyst has been assigned the task of reverse engineering malicious code. To conduct the analysis safely, which of the following could the analyst implement?
When determining the threats/vulnerabilities to migrate, it is important to identify which are applicable. Which of the following is the FIRST step to determine applicability?
An administrator wants to block Java exploits that were not detected by the organization’s antivirus product. Which of the following mitigation methods should an incident responder perform? (Choose two.)
A security auditor has been asked to analyze event logs to look for signs of suspicious behavior. The company operated on a normal workday schedule (e.g., Monday through Friday, 8 am – 5 pm) and has implemented stringent access control policies (e.g. password complexity, failed login attempts). Which of the following provides the MOST reason for concern?
An attacker has exfiltrated the SAM file from a Windows workstation. Which of the following attacks is MOST likely being perpetrated?
An attacker has decided to attempt a brute force attack on a UNIX server. In order to accomplish this, which of the following steps must be performed?
A network administrator has been asked to configure a new network. It is the company’s policy to segregate network functions using different Virtual LANs (VLANs). On which of the following is this configuration MOST likely to occur?


