Which command will display the following output?
show mac-address-table
show cdp neighbor
show inventory
show ip interface
Answer:
Explanation:
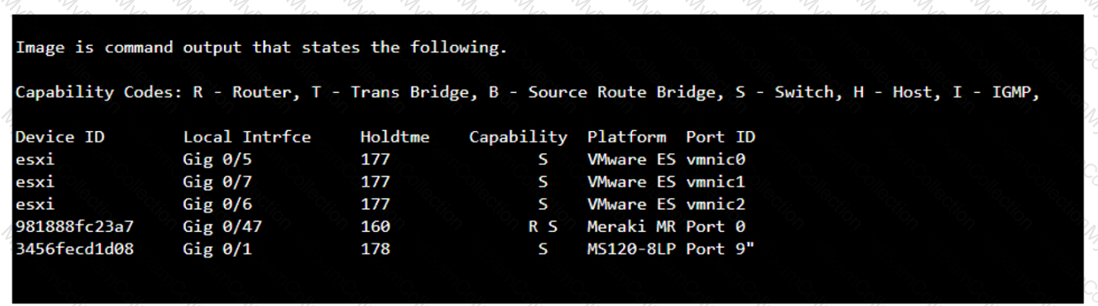
The command that will display the output provided, which includes capability codes, local interface details, device IDs, hold times, and platform port ID capabilities, is the show cdp neighbor command. This command is used in Cisco devices to display current information about neighboring devices detected by Cisco Discovery Protocol (CDP), which includes details such as the interface through which the neighbor is connected, the type of device, and the port ID of the device1.
References :=
•Cisco - show cdp neighbors
The provided output is from the Cisco Discovery Protocol (CDP) neighbor table. The show cdp neighbor command displays information about directly connected Cisco devices, including Device ID, Local Interface, Holdtime, Capability, Platform, and Port ID.
•A. show mac-address-table: Displays the MAC address table on the switch.
•C. show inventory: Displays information about the hardware inventory of the device.
•D. show ip interface: Displays IP interface status and configuration.
Thus, the correct answer is B. show cdp neighbor.
References :=
•Cisco CDP Neighbor Command
•Understanding CDP
Move each cloud computing service model from the list on the left to the correct example on the right
Note: You will receive partial credit for each correct answer.

Answer:

Explanation:
Three virtual machines are connected by a virtual network in the cloud.
Model: IaaS (Infrastructure as a Service)
Explanation: IaaS provides virtualized computing resources over the internet, including virtual machines, storage, and networks.
Users access a web-based graphics design application in the cloud for a monthly fee.
Model: SaaS (Software as a Service)
Explanation: SaaS delivers software applications over the internet, typically on a subscription basis, accessible via a web browser.
A company develops applications using cloud-based resources and tools.
Model: PaaS (Platform as a Service)
Explanation: PaaS provides a platform allowing customers to develop, run, and manage applications without dealing with the infrastructure.
IaaS (Infrastructure as a Service): Provides virtualized hardware resources that customers can use to build their own computing environments.
PaaS (Platform as a Service): Offers a platform with tools and services to develop, test, and deploy applications.
SaaS (Software as a Service): Delivers fully functional applications over the internet that users can access and use without managing the underlying infrastructure.
References:
Cloud Service Models: Understanding IaaS, PaaS, SaaS
NIST Definition of Cloud Computing:NIST Cloud Computing
Which information is included in the header of a UDP segment?
IP addresses
Sequence numbers
Port numbers
MAC addresses
Answer:
Explanation:
The header of a UDP (User Datagram Protocol) segment includesport numbers. Specifically, it contains the source port number and the destination port number, which are used to identify the sending and receiving applications. UDP headers do not include IP addresses or MAC addresses, as those are part of the IP and Ethernet frame headers, respectively.Additionally, UDP does not use sequence numbers, which are a feature of TCP (Transmission Control Protocol) for ensuring reliable delivery of data segments1.
References:=
Segmentation Explained with TCP and UDP Header
User Datagram Protocol (UDP) - GeeksforGeeks
Which three fields are used in a UDP segment header
=========================
UDP Header: The header of a UDP segment includes the following key fields:
Source Port: The port number of the sending application.
Destination Port: The port number of the receiving application.
Length: The length of the UDP header and data.
Checksum: Used for error-checking the header and data.
IP Addresses: These are included in the IP header, not the UDP header.
Sequence Numbers: These are part of the TCP header, not UDP.
MAC Addresses: These are part of the Ethernet frame header and are not included in the UDP header.
References:
RFC 768 - User Datagram Protocol: RFC 768
Cisco Guide on UDP: Cisco UDP Guide
Which address is included in the 192.168.200.0/24 network?
192.168.199.13
192.168.200.13
192.168.201.13
192.168.1.13
Answer:
Explanation:
•192.168.200.0/24 Network: This subnet includes all addresses from 192.168.200.0 to 192.168.200.255. The /24 indicates a subnet mask of 255.255.255.0, which allows for 256 addresses.
•192.168.199.13: This address is in the 192.168.199.0/24 subnet, not the 192.168.200.0/24 subnet.
•192.168.200.13: This address is within the 192.168.200.0/24 subnet.
•192.168.201.13: This address is in the 192.168.201.0/24 subnet, not the 192.168.200.0/24subnet.
•192.168.1.13: This address is in the 192.168.1.0/24 subnet, not the 192.168.200.0/24 subnet.
References:
•Subnetting Guide: Subnetting Basics
Which protocol allows you to securely upload files to another computer on the internet?
SFTP
ICMP
NTP
HTTP
Answer:
Explanation:
SFTP, or Secure File Transfer Protocol, is a protocol that allows for secure file transfer capabilities between networked hosts. It is a secure extension of the File Transfer Protocol (FTP). SFTP encrypts both commands and data, preventing passwords and sensitive information from being transmitted openly over the network. It is typically used for secure file transfers over the internet and is built on the Secure Shell (SSH) protocol1.
References :=
•What Is SFTP? (Secure File Transfer Protocol)
•How to Use SFTP to Safely Transfer Files: A Step-by-Step Guide
•Secure File Transfers: Best Practices, Protocols And Tools
The Secure File Transfer Protocol (SFTP) is a secure version of the File Transfer Protocol (FTP) that uses SSH (Secure Shell) to encrypt all commands and data. This ensures that sensitive information, such as usernames, passwords, and files being transferred, are securely transmitted over the network.
•ICMP (Internet Control Message Protocol) is used for network diagnostics and is not designed for file transfer.
•NTP (Network Time Protocol) is used to synchronize clocks between computer systems and is not related to file transfer.
•HTTP (HyperText Transfer Protocol) is used for transmitting web pages over the internet and does not inherently provide secure file transfer capabilities.
Thus, the correct protocol that allows secure uploading of files to another computer on the internet is SFTP.
References :=
•Cisco Learning Network
•SFTP Overview (Cisco)
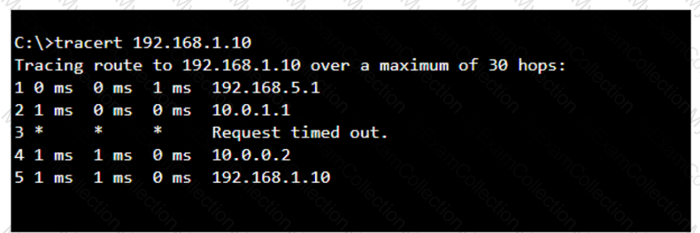
A user reports that a company website is not available. The help desk technician issues a tracert command to determine if the server hosting the website is reachable over the network. The output of the command is shown as follows:
What can you tell from the command output?
The router at hop 3 is not forwarding packets to the IP address 192.168.1.10.
The server address 192.168.1.10 is being blocked by a firewall on the router at hop 3.
The server with the address 192.168.1.10 is reachable over the network.
Requests to the web server at 192.168.1.10 are being delayed and time out.
Answer:
Explanation:
The tracert command output shows the path taken to reach the destination IP address, 192.168.1.10. The command output indicates:
•Hops 1 and 2 are successfully reached.
•Hop 3 times out, meaning the router at hop 3 did not respond to the tracert request. However, this does not necessarily indicate a problem with forwarding packets, as some routers may be configured to block or not respond to ICMP requests.
•Hops 4 and 5 are successfully reached, with hop 5 being the destination IP 192.168.1.10, indicating that the server is reachable.
Thus, the correct answer is C. The server with the address 192.168.1.10 is reachable over the network.
References :=
•Cisco Traceroute Command
•Understanding Traceroute
The tracert command output indicates that the server with the address 192.168.1.10 is reachable over the network. The asterisk (*) at hop 3 suggests that the probe sent to that hop did not return a response, which could be due to a variety of reasons such as a firewall blocking ICMP packets or the router at that hop being configured not to respond to ICMP requests. However, since the subsequent hops (4 and 5) are showing response times, it means that the packets are indeed getting through and the server is reachable12.
References :=
•How to Use Traceroute Command to Read Its Results
•How to Use the Tracert Command in Windows
A host is given the IP address 172.16.100.25 and the subnet mask 255.255.252.0.
What is the CIDR notation for this address?
172.16.100.25 /23
172.16.100.25 /20
172.16.100.25 /21
172.16.100.25 /22
Answer:
Explanation:
The CIDR (Classless Inter-Domain Routing) notation for the subnet mask 255.255.252.0 is /22. This notation indicates that the first 22 bits of the IP address are used for network identification, and the remaining bits are used for host addresses within the network1.
References :=
•Subnet Cheat Sheet – 24 Subnet Mask, 30, 26, 27, 29, and other IP Address CIDR Network References
=========================
•Subnet Mask to CIDR Notation: The given subnet mask is 255.255.252.0. To convert this to CIDR notation:
•Convert the subnet mask to binary: 11111111.11111111.11111100.00000000
•Count the number of consecutive 1s in the binary form: There are 22 ones.
•Therefore, the CIDR notation is /22.
References:
•Understanding Subnetting and CIDR: Cisco CIDR Guide
For each statement about bandwidth and throughput, select True or False.
Note: You will receive partial credit for each correct selection.
Answer:
Explanation:
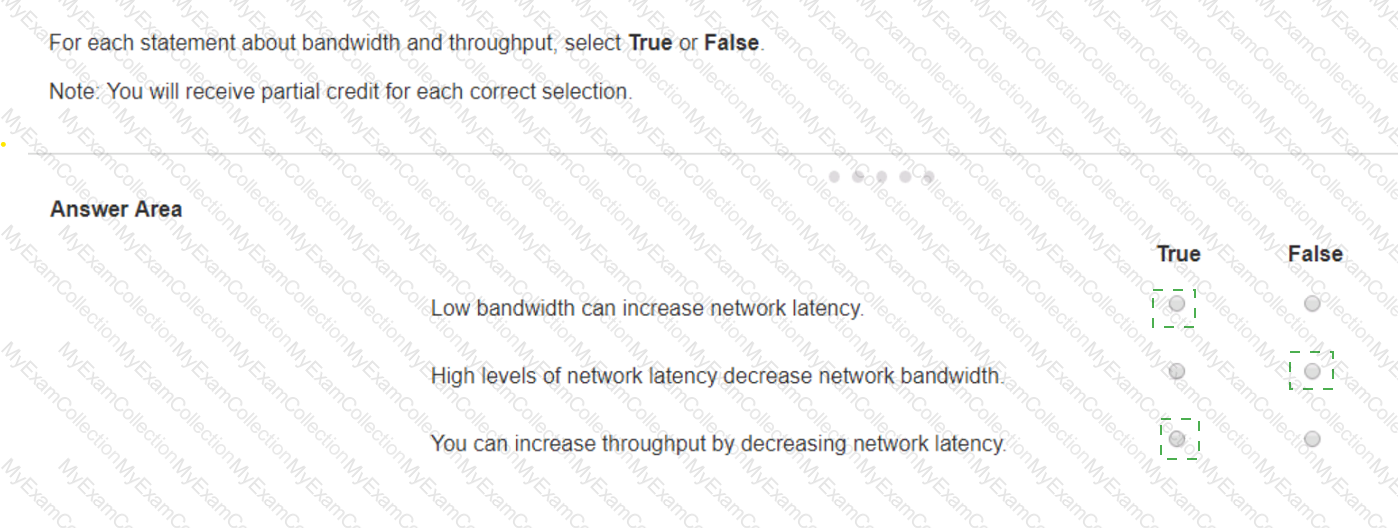
Statement 1: Low bandwidth can increase network latency.
True: Low bandwidth can result in increased network latency because the network may become congested, leading to delays in data transmission.
Statement 2: High levels of network latency decrease network bandwidth.
False: High levels of network latency do not decrease the available network bandwidth, but they do affect the perceived performance and throughput of the network.
Statement 3: You can increase throughput by decreasing network latency.
True: Decreasing network latency can increase throughput because data can be transmitted more quickly and efficiently without delays.
Bandwidth vs. Latency: Bandwidth refers to the maximum rate at which data can be transferred over a network path. Latency is the time it takes for a data packet to travel from the source to the destination.
Low bandwidth can cause network congestion, which can increase latency as packets wait to be transmitted.
High latency does not reduce the actual bandwidth but can affect the overall performance and efficiency of data transmission.
Reducing latency can lead to higher throughput because the network can handle more data in a given period without delays.
References:
Network Performance Metrics: Cisco Network Performance
Understanding Bandwidth and Latency: Bandwidth vs. Latency
Move each protocol from the list on the left to its correct example on the right.
Answer:
Explanation:
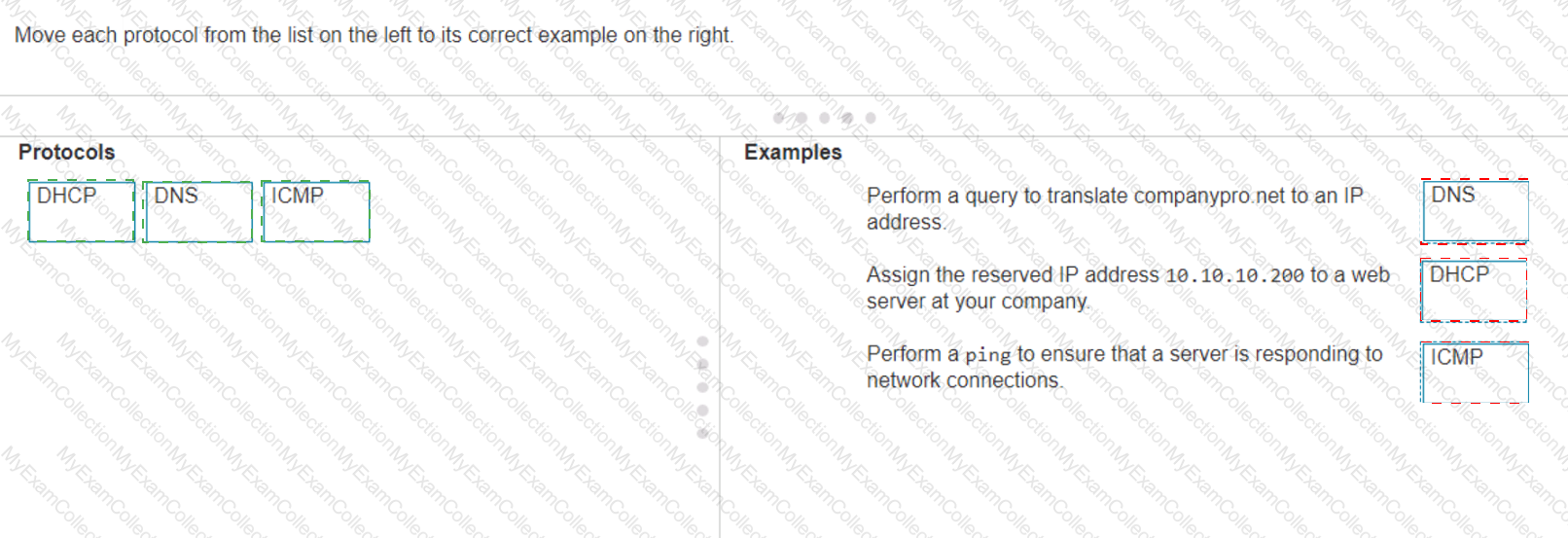
The correct matching of the protocols to their examples is as follows:
DHCP: Assign the reserved IP address 10.10.10.200 to a web server at your company.
DNS: Perform a query to translate companypro.net to an IP address.
ICMP: Perform a ping to ensure that a server is responding to network connections.
Here’s how each protocol corresponds to its example:
DHCP (Dynamic Host Configuration Protocol)is used to assign IP addresses to devices on a network. In this case, DHCP would be used to assign the reserved IP address 10.10.10.200 to a web server.
DNS (Domain Name System)is used to translate domain names into IP addresses. Therefore, to translate companypro.net to an IP address, DNS would be utilized.
ICMP (Internet Control Message Protocol)is used for sending error messages and operational information indicating success or failure when communicating with another IP address. An example of this is using the ping command to check if a server is responding to network connections.
These protocols are essential for the smooth operation of networks and the internet.
Perform a query to translate companypro.net to an IP address.
DNS (Domain Name System): DNS is used to resolve domain names to IP addresses.
Assign the reserved IP address 10.10.10.200 to a web server at your company.
DHCP (Dynamic Host Configuration Protocol): DHCP is used to assign IP addresses to devices on a network.
Perform a ping to ensure that a server is responding to network connections.
ICMP (Internet Control Message Protocol): ICMP is used by network devices to send error messages and operational information, and it is the protocol used by the ping command.
DNS (Domain Name System): DNS translates human-friendly domain names like "companypro.net" into IP addresses that computers use to identify each other on the network.
DHCP (Dynamic Host Configuration Protocol): DHCP automatically assigns IP addresses to devices on a network, ensuring that no two devices have the same IP address.
ICMP (Internet Control Message Protocol): ICMP is used for diagnostic or control purposes, and the ping command uses ICMP to test the reachability of a host on an IP network.
References:
DNS Basics: What is DNS?
DHCP Overview: What is DHCP?
ICMP and Ping: Understanding ICMP

