A company’sSIEMis designed to associate the company’sasset inventorywith user events. Given the following report:

Which of thefollowing should asecurity engineer investigate firstas part of alog audit?
A security administrator needs to review the efficacy of the detection rules configured on the SIEM by employing real-world attacker TTPs. Which of the following actions should the security administrator take to accomplish this objective?
A company that uses containers to run its applications is required to identify vulnerabilities on every container image in a private repository The security team needs to be able to quickly evaluate whether to respond to a given vulnerability Which of the following, will allow the security team to achieve the objective with the last effort?
An incident response team is analyzing malware and observes the following:
• Does not execute in a sandbox
• No network loCs
• No publicly known hash match
• No process injection method detected
Which of thefollowing should the team do next to proceed with further analysis?
A company needs to quickly assess whether software deployed across the company's global corporate network contains specific software libraries. Which of the following best enables the company's SOC to respond quickly when such an assessment is required?
A security analyst is reviewingsuspicious log-in activity and sees the following data in the SICM:

Which of the following is the most appropriate action for the analyst to take?
Which of the following includes best practices for validating perimeter firewall configurations?
During a vulnerability assessment, a scan reveals the following finding:
Windows Server 2016 Missing hotfix KB87728 - CVSS 3.1 Score: 8.1 [High] - Affected host 172.16.15.2
Later in the review process, the remediation team marks the finding as a false positive. Which of the following is the best way toavoid this issue on future scans?
Developers have been creating and managing cryptographic material on their personal laptops fix use in production environment. A security engineer needs to initiate a more secure process. Which of thefollowing is the best strategy for the engineer to use?
Engineers are unable to control pumps at Site A from Site B when the SCADA controller at Site A experiences an outage. A security analyst must provide a secure solution that ensures Site A pumps can be controlled by a SCADA controller at Site B if a similar outage occurs again. Which of the following represents the most cost-effective solution?
During a recent audit, a company's systems were assessed- Given the following information:

Which of the following is the best way to reduce the attack surface?
Audit findings indicate several user endpoints are not utilizing full disk encryption During me remediation process, a compliance analyst reviews the testing details for the endpoints and notes the endpoint device configuration does not support full disk encryption Which of the following is the most likely reason me device must be replaced'
A developer needs toimprove the cryptographic strength of a password-storage component in a web application without completely replacing the crypto-module. Which of the following is the most appropriate technique?
An organization is researching the automation capabilities for systems within an OT network. A security analyst wants to assist with creating secure coding practices and would like to learn about the programming languages used on the PLCs. Which of the following programming languages is the most relevant for PLCs?
An organization is deploying a new data lake that will centralize records from several applications. During the design phase, the security architect identifies the following requirements:
• The sensitivity levels of the data is different.
• The data must be accessed through stateless API calls after authentication.
• Different users will have access to different data sets.
Which of the following should the architect implement to best meet these requirements?
The ISAC for the retail industry recently released a report regarding social engineering tactics in which small groups create distractions for employees while other malicious individuals install advanced card skimmers on the payment systems. The Chief Information Security Officer (CISO) thinks that security awareness training, technical control implementations, and governance already in place is adequate to protect from this threat. The board would like to test these controls. Which of the following should the CISO recommend?
A hospital provides tablets to its medical staff to enable them to more quickly access and edit patients' charts. The hospital wants to ensure that if a tablet is identified as lost or stolen and a remote command is issued, the risk of data loss can be mitigated within seconds. The tablets are configured as follows:
• Full disk encryption is enabled.
• "Always On" corporate VPN is enabled.
• eFuse-backed keystore is enabled.
• Wi-Fi 6 is configured with SAE.
• Location services is disabled.
• Application allow list is unconfigured.
Assuming the hospital policy cannot be changed, which of the following is the best way to meet the hospital's objective?
Which of the following are risks associated with vendor lock-in? (Select two).
Source code snippets for two separate malware samples are shown below:
Sample 1:
knockEmDown(String e) {
if(target.isAccessed()) {
target.toShell(e);
System.out.printIn(e.toString());
c2.sendTelemetry(target.hostname.toString + " is " + e.toString());
} else {
target.close();
}
}
Sample 2:
targetSys(address a) {
if(address.islpv4()) {
address.connect(1337);
address.keepAlive("paranoid");
String status = knockEmDown(address.current);
remote.sendC2(address.current + " is " + status);
} else {
throw Exception e;
}
}
Which of the following describes the most important observation about the two samples?
Which of the following best describes the reason PQC preparation is important?
An organization recently implemented a policy that requires all passwords to be rotated every 90 days. An administrator observes a large volume of failed sign-on logs from multiple servers that are often accessed by users. The administrator determines users are disconnecting from the RDP session but not logging off. Which of the following should the administrator do to prevent account lockouts?
While investigating a security event an analyst finds evidence that a user opened an email attachment from an unknown source. Shortly after the user opened the attachment, a group of servers experienced a large amount of network and resource activity. Upon investigating the servers, the analyst discovers the servers were encrypted by ransomware that is demanding payment within 48 hours or all data will be destroyed. The company has no response plans for ransomware. Which of the following is the next step the analyst should take after reporting the incident to the management team?
After a company discovered a zero-day vulnerability in its VPN solution, the company plans to deploy cloud-hosted resources to replace its current on-premises systems. An engineer must find an appropriate solution to facilitate trusted connectivity. Which of the following capabilities is the most relevant?
A company plans to deploy a new online application that provides video training for its customers. As part of the design, the application must be:
• Fast for all users
• Available for users worldwide
• Protected against attacks
Which of the following are the best components the company should use to meet these requirements? (Select two).
Which of the following security risks should be considered as an organization reduces cost and increases availability of services by adopting serverless computing?
A network security architect for an organization with a highly remote workforce implements an always-on VPN to meet business requirements. Which of the following best explains why the architect is using this approach?
While performing threat-hunting functions, an analyst is using the Diamond Model of Intrusion Analysis. The analyst identifies the likely adversary, the infrastructure involved, and the target. Which of the following must the threat hunter document to use the model effectively?

An organization is planning for disaster recovery and continuity of operations.
INSTRUCTIONS
Review the following scenarios and instructions. Match each relevant finding to the affected host.
After associating scenario 3 with the appropriate host(s), click the host to select the appropriate corrective action for that finding.
Each finding may be used more than once.
If at any time you would like to bring back the initial state of the simul-ation, please click the Reset All button.
A global manufacturing company has an internal application mat is critical to making products This application cannot be updated and must Beavailable in the production area A security architect is implementing security for the application. Which of the following best describes the action the architect should take-?
A systems administrator wants to introduce a newly released feature for an internal application. The administrate docs not want to test the feature in the production environment. Which of the following locations is the best place to test the new feature?
A company isolated its OT systems from other areas of the corporate network These systems are required to report usage information over the internet to the vendor Which oi the following b*st reduces the risk of compromise or sabotage' (Select two).
A company that relies on an COL system must keep it operating until a new solution is available Which of the following is the most secure way to meet this goal?
A security analyst is reviewing the following authentication logs:

Which of the following should the analyst do first?
An organization decides to move to a distributed workforce model. Several legacy systems exist on premises and cannot be migrated because of existing compliance requirements. However, all new systems are required to be cloud-based. Which of the following would best ensure network access security?
A company implements an Al model that handles sensitive and personally identifiable information. Which of the following threats is most likely the company's primary concern?
A company developed a new solution that needs to track any changes to the data, and the changes need to be quickly identified. If any changes are attempted without prior approval, multiple events must be triggered, such as:
Raising alerts
Blocking the unapproved changes
Quickly removing access to the data
Which of the following solutions best meets these requirements?
A company wants to perform threat modeling on an internally developed, business-critical application. The Chief Information Security Officer (CISO) is most concerned that the application should maintain 99.999% availability and authorized users should only be able to gain access to data they are explicitly authorized to view. Which of the following threat-modeling frameworks directly addresses the CISO's concerns about this system?
A security analyst is developing a threat model that focuses on attacks associated with the organization's storage products. The products:
• Are used in commercial and government user environments
• Are required to comply with crypto-export requirements
• Include both hardware and software components that are developed by external vendors in Europe and Asia
Which of the following are the most important for the analyst to consider when developing the model? (Select two).
A local government that is investigating a data exfiltration claim was asked to review the fingerprint of the malicious user's actions. An investigator took a forensic image of the VM and downloaded the image to a secured USB drive to share with the government. Which of the following should be taken into consideration during the process of releasing the drive to the government?
An organization is required to
* Respond to internal andexternal inquiries in a timely manner
* Provide transparency.
* Comply with regulatory requirements
The organization has not experienced any reportable breaches but wants to be prepared if a breach occurs in the future. Which of the following is the best way for the organization to prepare?
An analyst reviews a SIEM and generates the following report:

OnlyHOST002is authorized for internet traffic. Which of the following statements is accurate?
A security review revealed that not all of the client proxy traffic is being captured. Which of the following architectural changes best enables the capture of traffic for analysis?
An attacker infiltrated the code base of a hardware manufacturer and inserted malware before the code was compiled. The malicious code is now running at the hardware level across a number of industries and sectors. Which of the following categories best describes this type of vendor risk?
A security architect wants to develop abaseline of security configurations These configurations automatically will be utilized machine is created Which of the following technologies should the security architect deploy to accomplish this goal?
A subcontractor develops safety critical avionics software for a major aircraft manufacturer. After an incident, a third-party investigator recommends the company begin to employ formal methods in the development life cycle. Which of the following findings from the investigation most directly supports the investigator's recommendation?
A company plans to implement a research facility with Intellectual property data that should be protected The following is the security diagram proposed by the security architect

Which of the following security architect models is illustrated by the diagram?
A security engineer is developing a solution to meet the following requirements?
• All endpoints should be able to establish telemetry with a SIEM.
• All endpoints should be able to be integrated into the XDR platform.
• SOC services should be able to monitor the XDR platform
Which of the following should the security engineer implement to meet the requirements?
A security architect must make sure that the least number of services as possible is exposed in order to limit an adversary's ability to access the systems. Which of the following should the architect do first?
A user from the sales department opened a suspicious file attachment. The sales department then contacted the SOC to investigate a number of unresponsive systems, and the team successfully identified the file and the origin of the attack. Which of the following is the next step of the incident response plan?
A security engineer is reviewing the following vulnerability scan report:

Which of the following should the engineer prioritize for remediation?
An audit finding reveals that a legacy platform has not retained loos for more than 30 days The platform has been segmented due to its interoperability with newer technology. As a temporarysolution, the IT department changed the log retention to 120 days. Which of the following should the security engineer do to ensure the logs are being properly retained?
An organization is developing on Al-enabled digital worker to help employees complete common tasks such as template development, editing, research, and scheduling. As part of the Al workload the organization wants to Implement guardrails within the platform. Which of the following should the company do to secure the Al environment?
A company finds logs with modified time stamps when compared to other systems. The security team decides to improve logging and auditing for incident response. Which of the following should the team do to best accomplish this goal?
A company was recently infected by malware. During the root cause analysis, the company determined that several users were installing their own applications. To prevent further compromises, the company has decided it will onlyallow authorized applications to run on its systems. Which of the following should the company implement?
A global organization is reviewing potential vendors to outsource a critical payroll function. Each vendor's plan includes using local resources in multiple regions to ensure compliance with all regulations. The organization's Chief Information Security Officer is conducting a risk assessment on the potential outsourcing vendors' subprocessors. Which of the following best explains the need for this risk assessment?
A senior security engineer flags me following log file snippet as hawing likely facilitated an attacker's lateral movement in a recent breach:

Which of the following solutions, if implemented, would mitigate the nsk of this issue reoccurnnp?
A malware researcher has discovered a credential stealer is looking at a specific memory register to harvest passwords that will be used later for lateral movement in corporate networks. The malware is using TCP 4444 to communicate with other workstations. The lateral movement would be best mitigated by:
A security engineer is assisting a DevOps team that has the following requirements for container images:
Ensure container images are hashed and use version controls.
Ensure container images are up to date and scanned for vulnerabilities.
Which of the following should the security engineer do to meet these requirements?
A security administrator is reviewing the following code snippet from a website component:

A review of the inc.tmp file shows the following:

Which of the following is most likely the reason for inaccuracies?
Which of the following AI concerns is most adequately addressed by input sanitation?
A security analyst wants to use lessons learned from a poor incident response to reduce dwell lime in the future The analyst is using the following data points

Which of the following would the analyst most likely recommend?
A security configure isbuilding a solution to disable weak CBC configuration for remote access connections lo Linux systems. Which of the following should the security engineer modify?
A company is preparing to move a new version of a web application to production. No issues were reported during security scanning or quality assurance in the CI/CD pipeline. Which of the following actions should thecompany take next?
Which of the following best explains the business requirement a healthcare provider fulfills by encrypting patient data at rest?
A security engineer reviews an after action report from a previous security breach and notes a long lag time between detection and containment of a compromised account. The engineer suggests using SOAR to address this concern. Which of the following best explains the engineer's goal?
After remote desktop capabilities were deployed in the environment, various vulnerabilities were noticed.
• Exfiltration of intellectual property
• Unencrypted files
• Weak user passwords
Which of the following is the best way to mitigate these vulnerabilities? (Select two).
A cloud engineer needs to identify appropriate solutions to:
• Provide secure access to internal and external cloud resources.
• Eliminate split-tunnel traffic flows.
•Enable identity and access management capabilities.
Which of the following solutions arc the most appropriate? (Select two).
Which of the following best explains the importance of determining organization risk appetite when operating with a constrained budget?
An organization wants to manage specialized endpoints and needs a solution that provides the ability to
* Centrally manage configurations
* Push policies.
• Remotely wipe devices
• Maintain asset inventory
Which of the following should the organization do to best meet these requirements?
A company recently experienced an incident in which an advanced threat actor was able to shim malicious code against the hardware static of a domain controller The forensic team cryptographically validated that com the underlying firmware of the box and the operating system had not been compromised. However, the attacker was able to exfiltrate information from the server using a steganographic technique within LOAP Which of the following is me b»« way to reduce the risk oi reoccurrence?
Employees use their badges to track the number of hours they work. The badge readers cannot be upgraded due to facility constraints. The software for the badge readers uses a legacy platform and requires connectivity to the enterprise resource planning solution. Which of the following is the best to ensure the security of the badge readers?
A game developer wants to reach new markets and is advised by legal counsel to include specific age-related sign-up requirements. Which of the following best describes the legal counsel's concerns?
Users must accept the terms presented in a captive petal when connecting to a guest network. Recently, users have reported that they are unable to access the Internet after joining the network A network engineer observes the following:
• Users should be redirected to the captive portal.
• The Motive portal runs Tl. S 1 2
• Newer browser versions encounter security errors that cannot be bypassed
• Certain websites cause unexpected re directs
Which of the following mow likely explains this behavior?
Embedded malware has been discovered in a popular PDF reader application and is currently being exploited in the wild. Because the supply chain was compromised, this malware is present in versions 10.0 through 10.3 of the software's official versions. The malware is not present in version 10.4.
Since the details around this malware are still emerging, the Chief Information Security Officer has asked the senior security analyst to collaborate with the IT asset inventory manager to find instances of the installed software in order to begin response activities. The asset inventory manager has asked an analyst to provide a regular expression that will identify the affected versions. The software installation entries are formatted as follows:
Reader 10.0
Reader 10.1
Reader 10.2
Reader 10.3
Reader 10.4
Which of the following regular expression entries will accuratelyidentify all the affected versions?
A systems administrator needs to identify new attacks that could be carried out against the environment. The administrator plans to proactively seek out and observe new attacks. Which of the following is the best way to accomplish this goal?
A security architect wants to configure a mail server so it maintains an updated list of IoCs and blocks known-malicious incoming emails. Which of the following will the security architect most likely need for this task? (Select two)
A global organization wants to manage all endpoint and user telemetry. The organization also needs to differentiate this data based on which office it is correlated to. Which of the following strategies best aligns with this goal?
A Chief Information Security Officer (CISO) is concerned that a company's current data disposal procedures could result in data remanence. The company uses only SSDs. Which of the following would be the most secure way to dispose of the SSDs given the CISO's concern?
A global company’s Chief Financial Officer (CFO) receives a phone call from someone claiming to be the Chief Executive Officer (CEO). The caller claims to be stranded and in desperate need of money. The CFO is suspicious, but the caller’s voice sounds similar to the CEO’s. Which of the following best describes this type of attack?
A user reports application access issues to the help desk. The help desk reviews the logs for the user:

Which of the following is most likely the reason for the issue?
An external threat actor attacks public infrastructure providers. In response to the attack and during follow-up activities, various providers share information obtained during response efforts. After the attack, energy sector companies share their status and response data:
Company
SIEM
UEBA
DLP
ISAC Member
TIP Integration
Time to Detect
Time to Respond
1
Yes
No
Yes
Yes
Yes
10 minutes
20 minutes
2
Yes
Yes
Yes
Yes
No
20 minutes
40 minutes
3
Yes
Yes
No
No
Yes
12 minutes
24 minutes
Which of thefollowing is the most important issue to address to defend against future attacks?
Protected company data was recently exfiltrated. The SOC did not find any indication of a network or outside physical intrusion, and the DLP systems reported no unusual activity. The incident response team determined a text file was encrypted and reviews the following log excerpt:
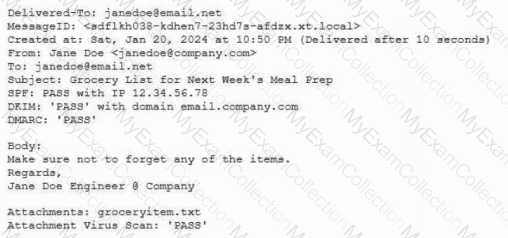
Which of the following is the most appropriate action for the team to take?
A security engineer receives an alert from the SIEM platform indicating a possible malicious action on the internal network. The engineer generates a report that outputs the logs associated with the incident:

Which of the following actions best enables the engineer to investigate further?
During a forensic review of a cybersecurity incident, a security engineer collected a portion of the payload used by an attacker on a comprised web server Given the following portion of the code:

Which of the following best describes this incident?
A threat intelligence company's business objective is to allow customers to integrate data directly to different TIPs through an API. The company would like to address as many of the following objectives as possible:
• Reduce compute spend as much as possible.
• Ensure availability for all users.
• Reduce the potential attack surface.
• Ensure the integrity of the data provided.
Which of the following should the company consider to best meet the objectives?
A company is adopting microservice architecture in order to quickly remediate vulnerabilities and deploy to production. All of the microservices run on the same Linux platform. Significant time was spent updating the base OS before deploying code. Which of the following should the company do to make the process efficient?
Which of the following best describes the challengesassociated with widespread adoption of homomorphic encryption techniques?
A security engineer wants to propose an MDM solution to mitigate certain risks. The MDM solution should meet the following requirements:
• Mobile devices should be disabled if they leave the trusted zone.
• If the mobile device is lost, data is not accessible.
Which of the following options should the security engineer enable on the MDM solution? (Select two).
A security analyst received a report that an internal web page is down after a company-wide update to the web browser Given the following error message:

Which of the following is the b«« way to fix this issue?
A company's help desk is experiencing a large number of calls from the finance department slating access issues to www bank com The security operations center reviewed the following security logs:

Which of the following is most likely the cause of the issue?
An organization wants to create a threat model to identity vulnerabilities in its infrastructure. Which of the following, should be prioritized first?
Due to locality and budget constraints, an organization’s satellite office has a lower bandwidth allocation than other offices. As a result, the local securityinfrastructure staff is assessing architectural options that will help preserve network bandwidth and increase speed to both internal and external resources while not sacrificing threat visibility. Which of the following would be the best option to implement?
A security engineer is developing a solution to meet the following requirements:
• All endpoints should be able to establish telemetry with a SIEM.
• All endpoints should be able to be integrated into the XDR platform.
• SOC services should be able to monitor the XDR platform.
Which of the following should the security engineer implement to meet the requirements? (Select Two.)
Which of the following are the best ways to mitigate the threats that are the highest priority? (Select two).

 A computer screen shot of a diagram Description automatically generated
A computer screen shot of a diagram Description automatically generated A screenshot of a computer error Description automatically generated
A screenshot of a computer error Description automatically generated
