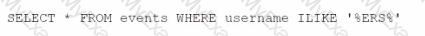Which two (2) options are at the top level when an analyst right-clicks on the Source IP or Destination IP that is associated with an offense at the Offense Summary?
The magnitude rating of an offense in QRadar is calculated based on which values?
Which two (2) types of data can be displayed by default in the Application Overview dashboard?
A mapping of a username to a user’s manager can be stored in a Reference Table and output in a search or a report.
Which mechanism could be used to do this?
What is an effective method to fix an event that is parsed an determined to be unknown or in the wrong QReader category/
A QRadar analyst wants predefined searches, reports, custom rules, and custom properties for HIPAA compliance.
Which option does the QRadar analyst use to look for HIPAA compliance on QRadar?
After analyzing an active offense where many source systems were observed connecting to a specific destination via local-to-local LDAP traffic, an ^lyst discovered that the targeted system is a legitimate LDAP server within the organization.
x avoid confusion in future analyses, how can this type of traffic to the target system be flagged as expected and be excluded from further offense ation?
What is the effect of toggling the Global/Local option to Global in a Custom Rule?
When examining lime fields on Event Information, which one represents the time QRadar received the raw event?
How can an analyst identify the top rules that generated offenses in the previous week and were closed as false positives or tuned?
Which two (2) statements regarding indexed custom event properties are true?
Which two (2) aggregation types are available for the pie chart in the Pulse app?
Which action is performed in Edit Search to create a report from Offense data?
When you create a report, you must choose a chart type for each chart that is included in the report.
Which two (2) chart types can you include in a report?
AQRadar analyst can check the rule coverage of MITRE ATT&CK tactics and techniques by using Use Case Manager.
In the Use Case Manager app, how can a QRadar analyst check the offenses triggered and mapped to MITRE ATT&CK framework?
Select all that apply
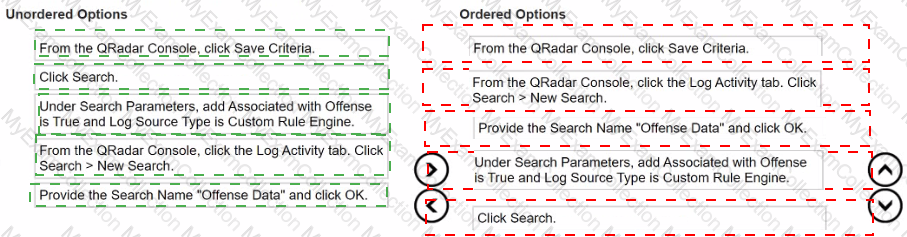
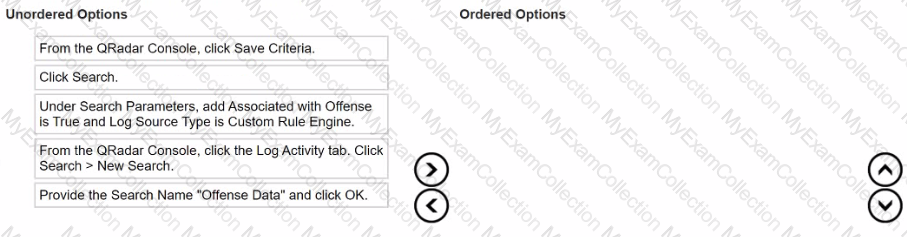
What is the sequence to create and save a new search called "Offense Data" that shows all the CRE events that are associated with offenses?
How does a QRadar analyst get to more information about a MITRE entry in the Use Case Manager?
Which parameter is calculated based on the relevance, severity, and credibility of an offense?
The Use Case Manager app has an option to see MITRE heat map.
Which two (2) factors are responsible for the different colors in MITRE heat map?
On the Reports tab in QRadar. what does the message "Queued (position in the queue)" indicate when generating a report?
Which two (2) are valid options available for configuring the frequency of report execution in the QRadar Report wizard?
Which two (2) options are used to search offense data on the By Networks page?
Several systems were initially reviewed as active offenses, but further analysis revealed that the traffic generated by these source systems is legitimate and should not contribute to offenses.
How can the activity be fine-tuned when multiple source systems are found to be generating the same event and targeting several systems?
During an active offense review, an analyst observed that a single source system generated a significant amount of high-rate traffic for transferring ^bound mail via port 25. The system responsible for this traffic was not authorized to function as a mail server.
lat is the correct action in this situation?